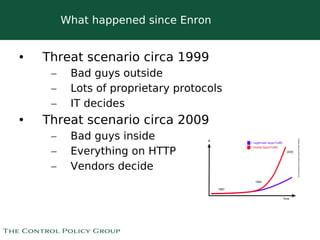
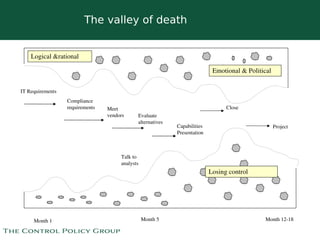
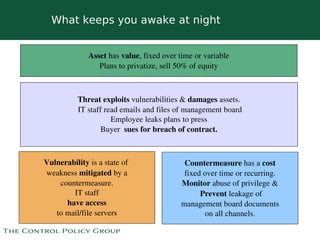
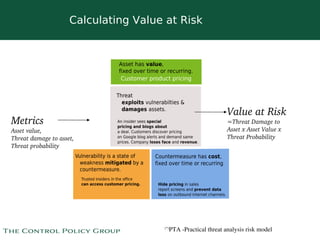
The document discusses strategies for selling data security solutions to CEOs, highlighting the importance of understanding data security, the evolution of threats, and the need for a strong sales strategy. It emphasizes building business pain and securing sponsorship from top executives to drive the adoption of data security measures. The content also suggests ways to calculate the value at risk and address vulnerabilities within organizations.