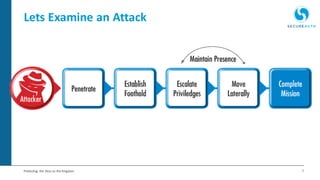
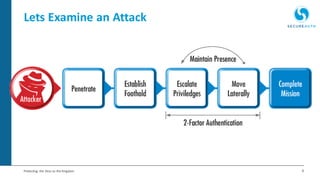
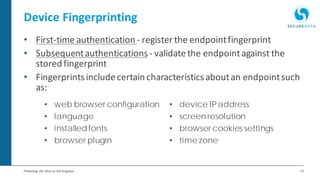
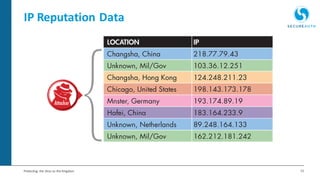
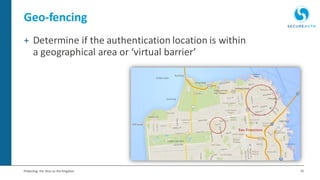
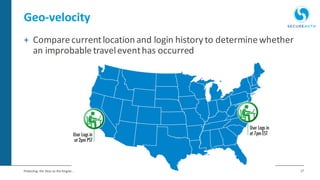
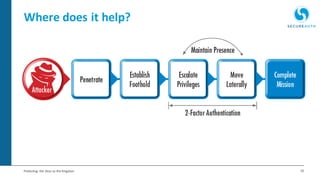
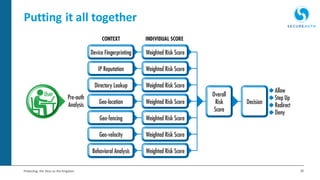
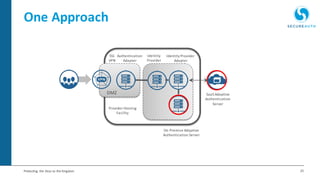
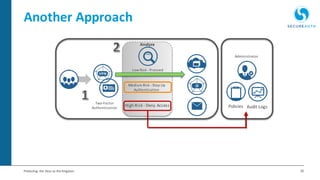
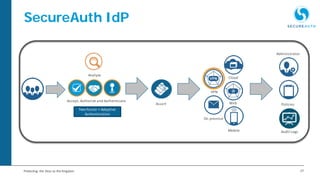
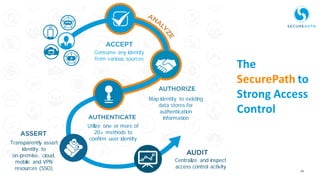
The document discusses the importance of adaptive authentication for VPNs as a response to inadequate traditional security measures, emphasizing that passwords alone are insufficient for protecting sensitive data. It outlines various techniques for adaptive authentication, including device fingerprinting and behavioral analysis, which collectively enhance identity verification while maintaining user experience. The need for real-time analysis of login attempts is highlighted to safeguard against lateral movements of attackers within networks.