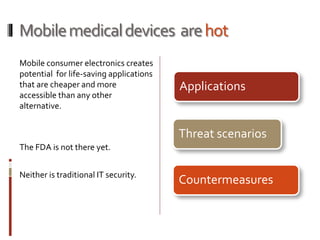
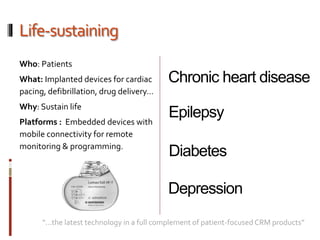
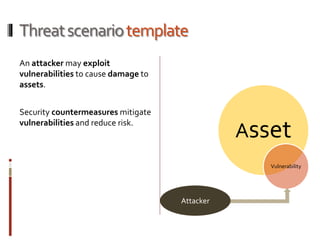
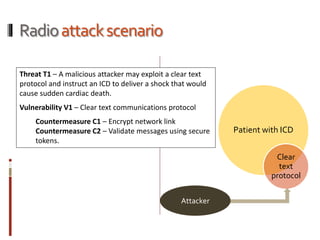
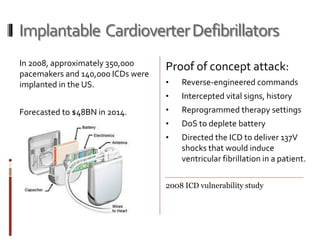
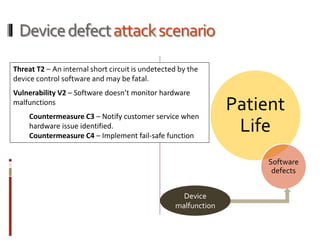
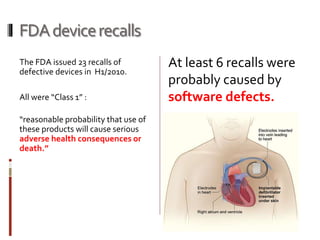
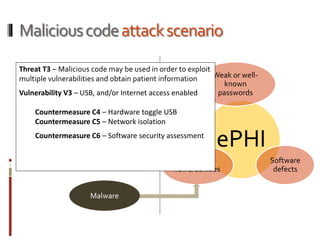
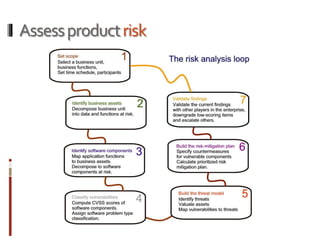
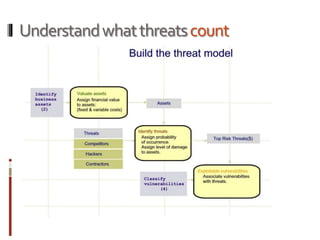
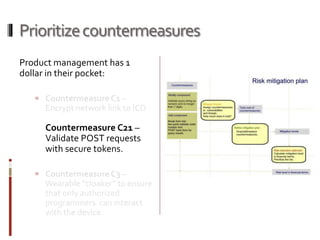
The Mob Sec Mobile Security Conference focused on the growing threat of vulnerabilities in mobile medical devices and the need for robust security frameworks. Discussions included various threat scenarios, such as malicious attacks on implantable cardioverter defibrillators, and the FDA's regulatory challenges. Countermeasures proposed involve encryption, fail-safe functions, and increased transparency to improve safety and revenue for medical device manufacturers.