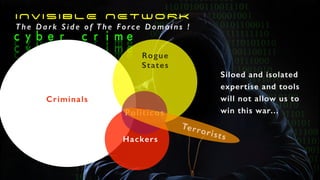
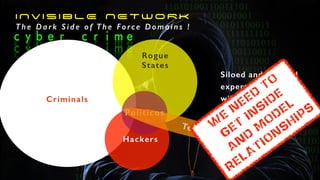
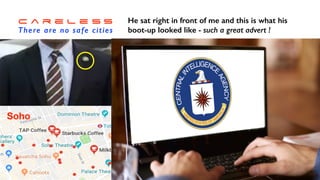
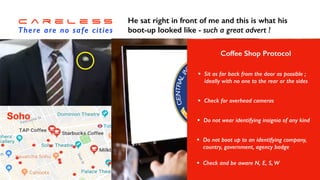
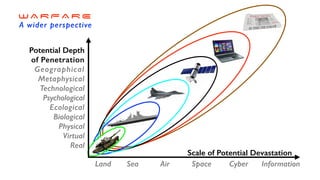
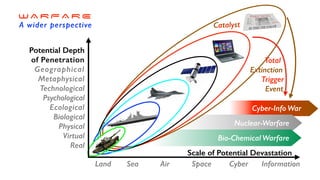
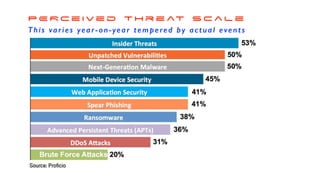
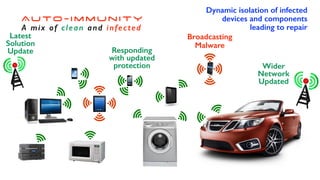
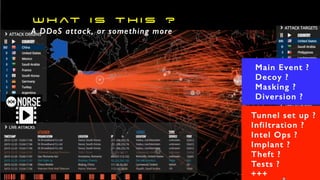
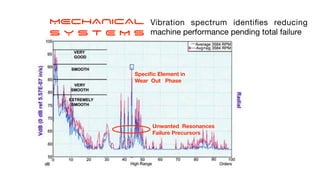
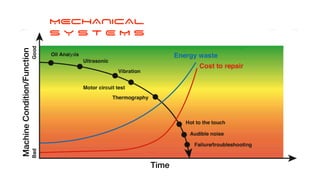
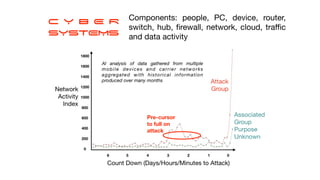
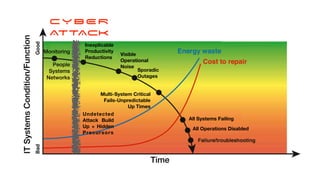
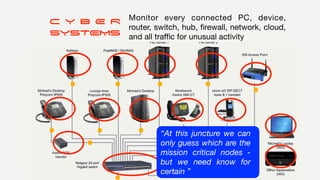
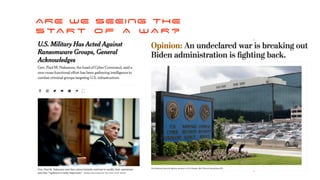
The document discusses the significant challenges posed by cyber criminals and the need for a paradigm shift in cybersecurity strategies. It emphasizes that understanding the enemy, being proactive, and integrating security from day one are crucial for effective defense against invisible network criminals. Additionally, the document highlights the importance of collaborating and sharing information to combat escalating cyber threats.