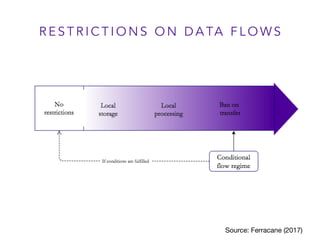
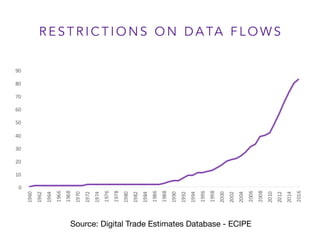
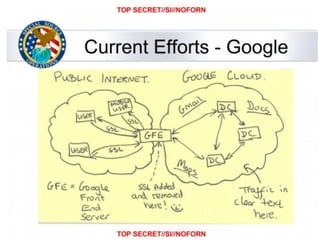
This document outlines a presentation on data flows and national security given by Martina Ferracane. It discusses how restrictions on data flows relate to the GATS security exception and assesses how data flows impact national security concerns like cyber espionage, attacks on critical infrastructure, and terrorist threats. The presentation concludes that determining whether data flow restrictions are justified requires analyzing each case based on the security threat picture and alternative technological options.