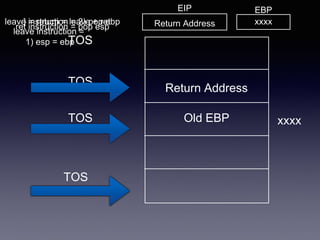
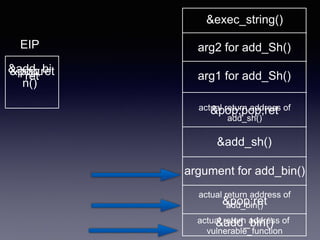
Return-Oriented Programming (ROP) is a technique used to control the instruction pointer (EIP) through a series of return addresses on the stack, allowing attackers to bypass security measures like ASLR and execute arbitrary code. The process involves carefully structuring function calls and utilizing 'gadgets'—short sequences of code ending in a return instruction—to achieve desired outcomes while navigating around executable space restrictions. This method is relevant in various applications such as exploits, jailbreaks, and rooting devices.