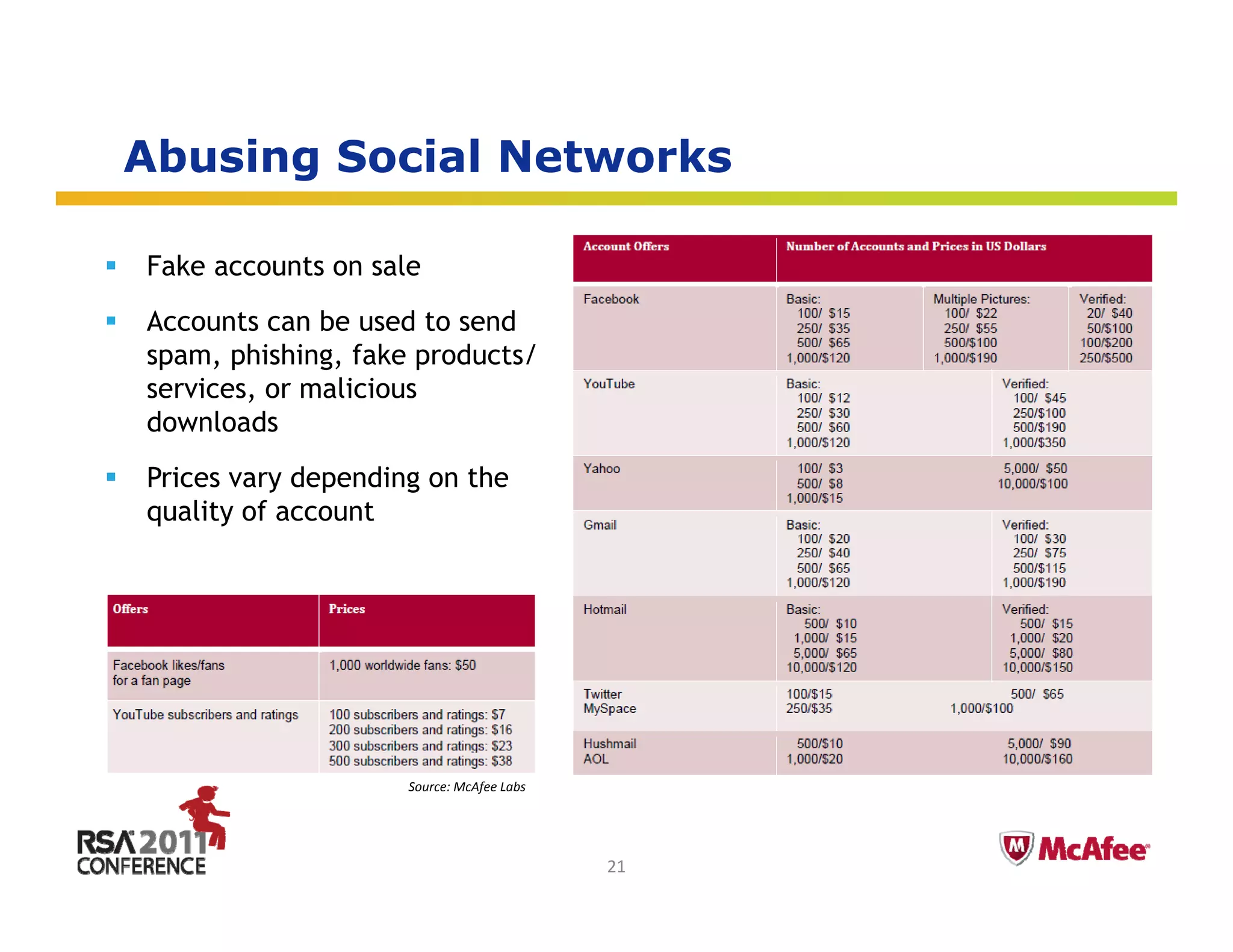
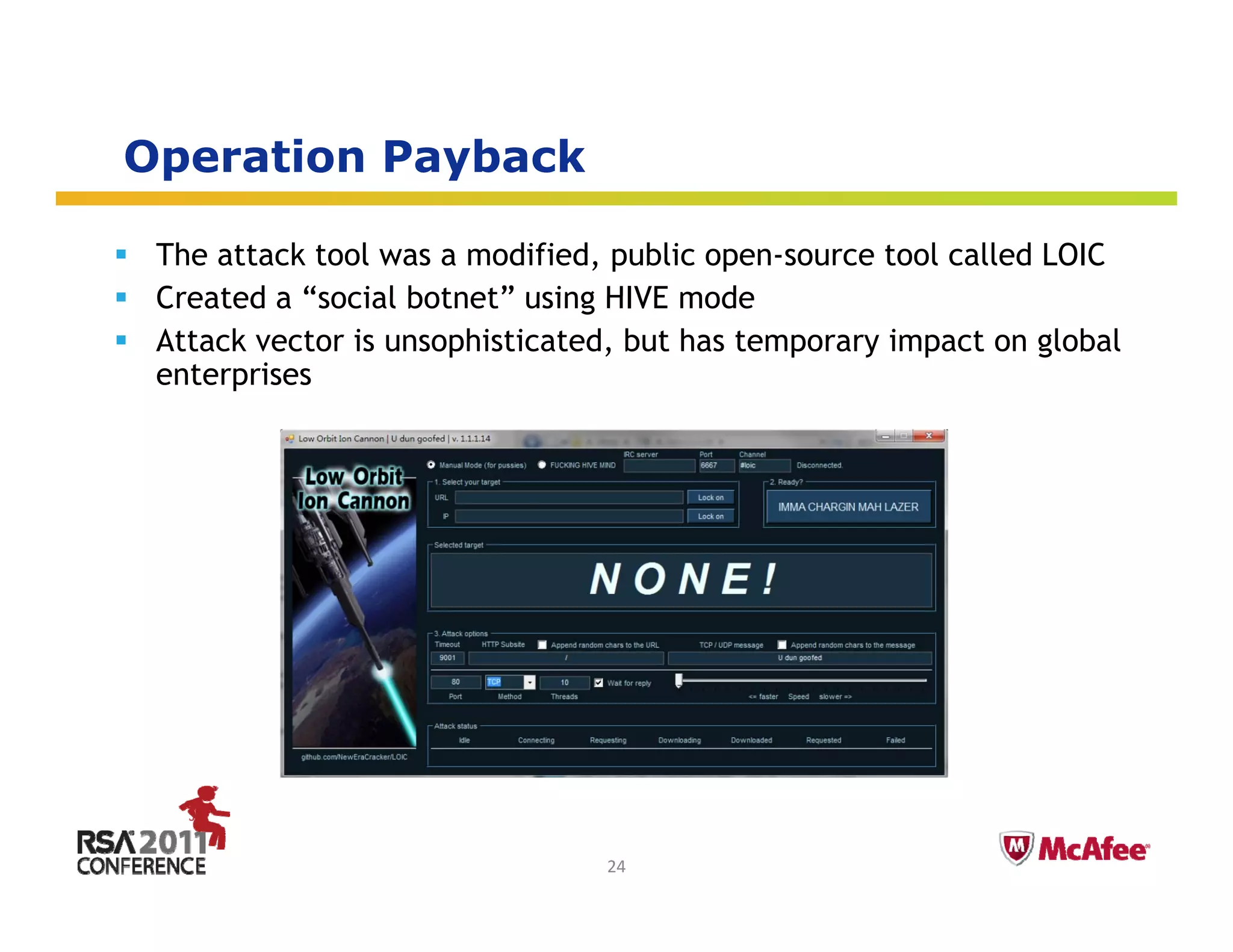
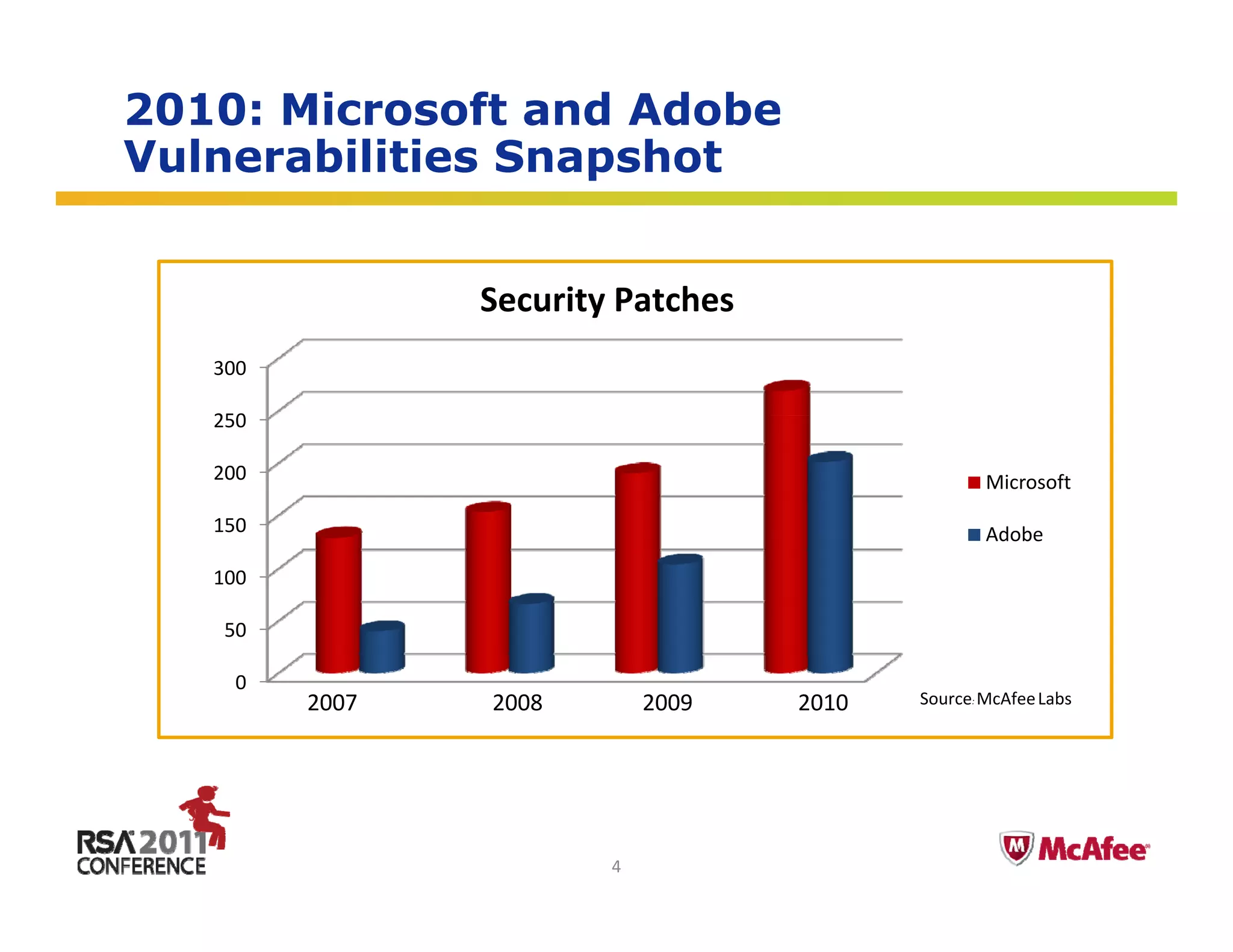
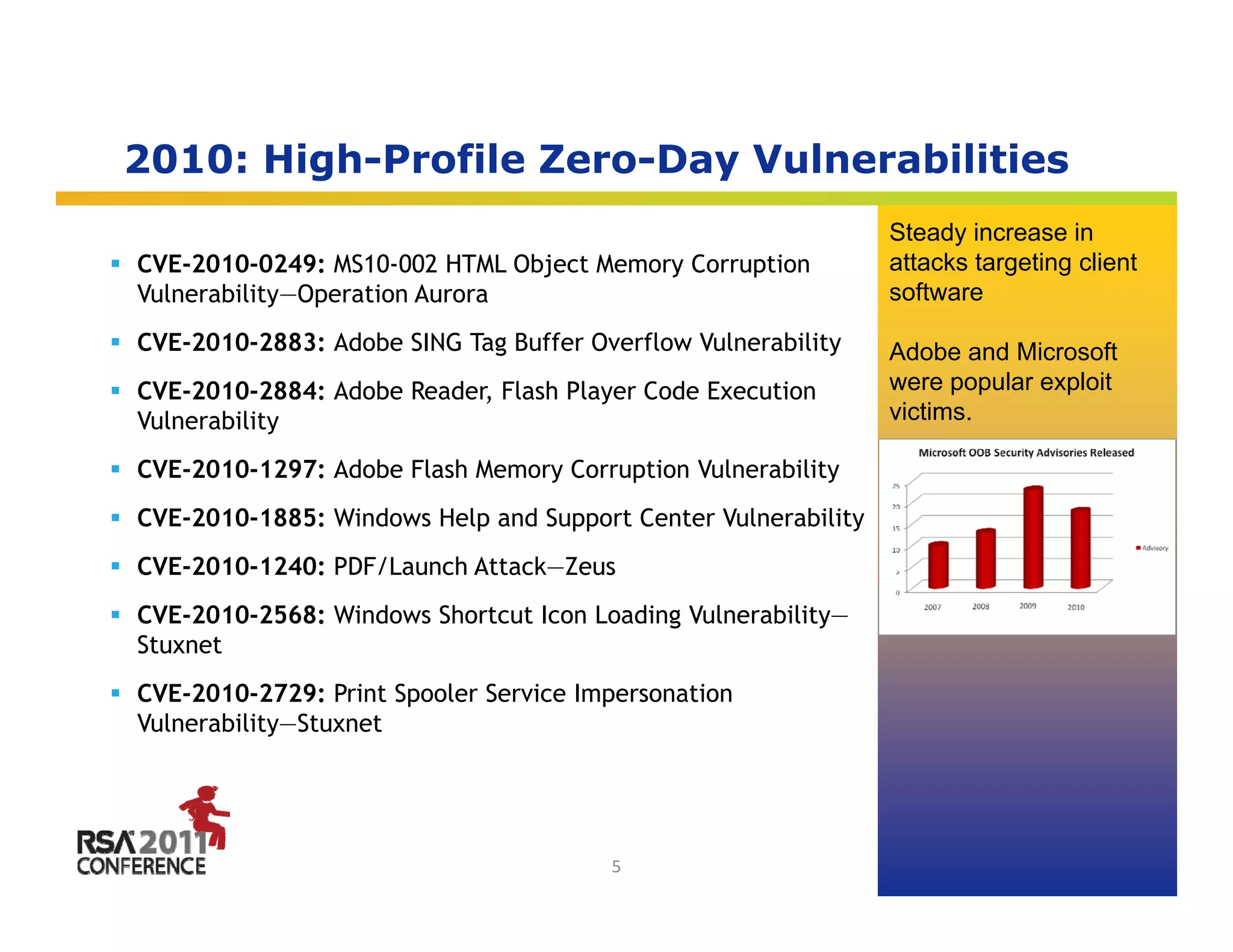
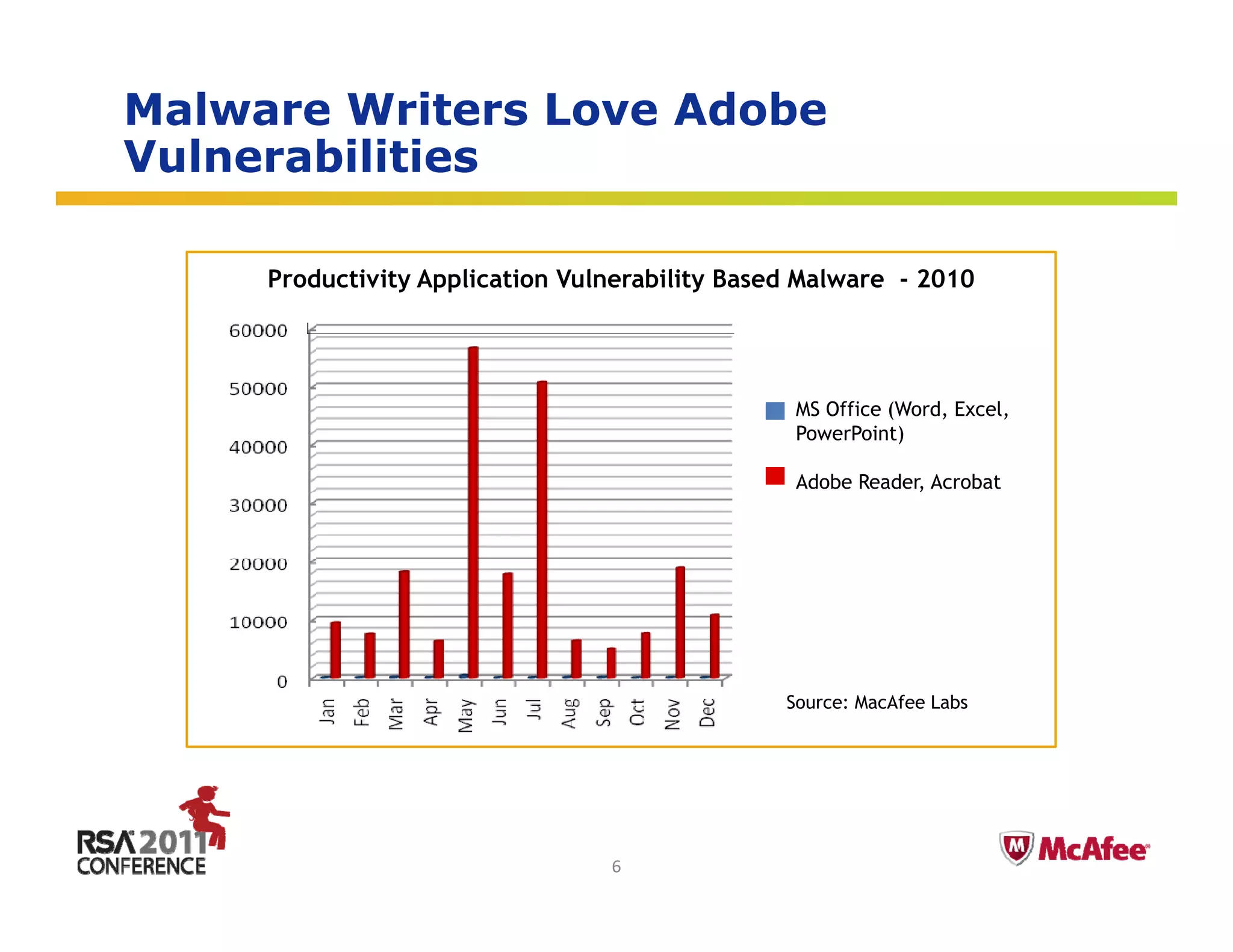
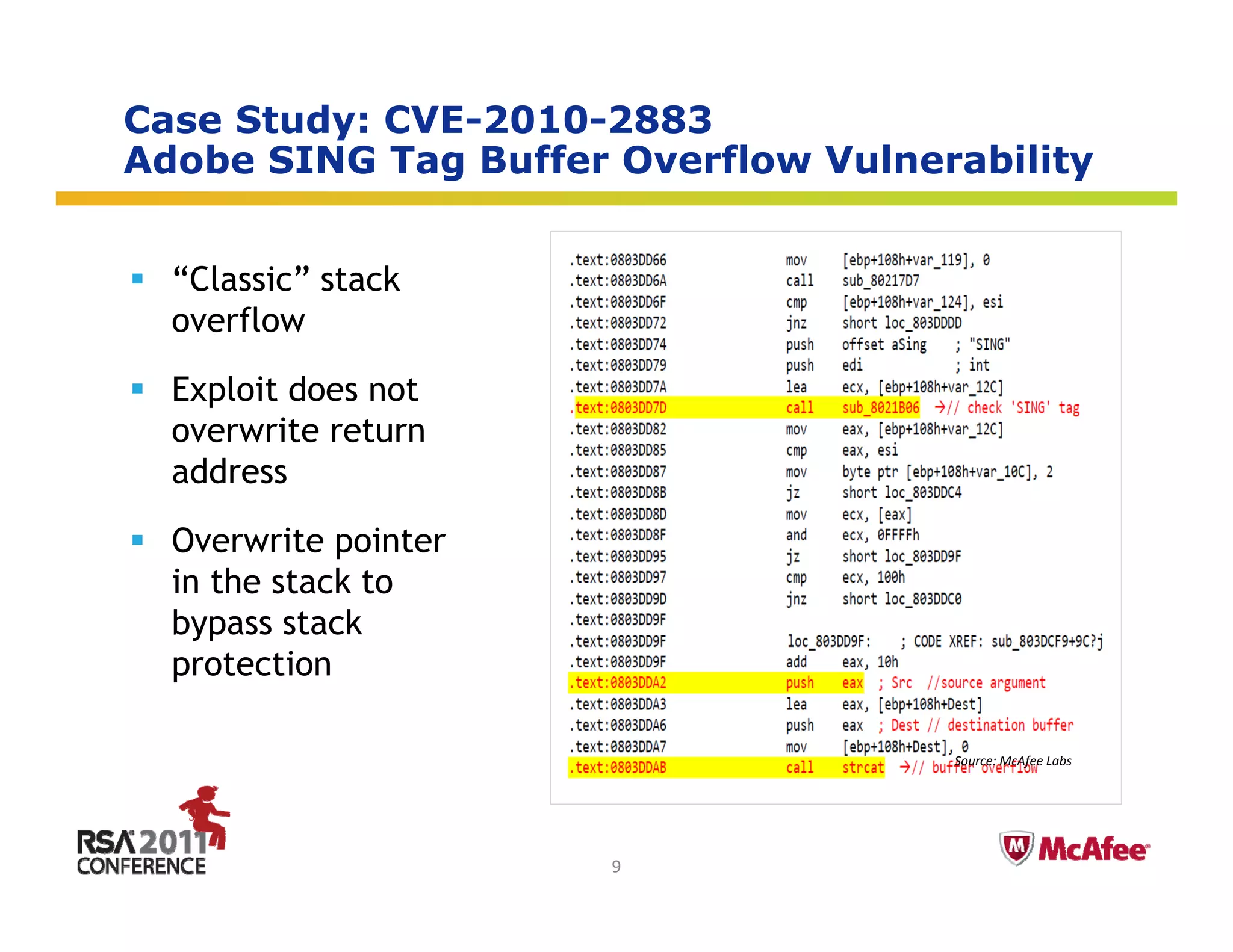
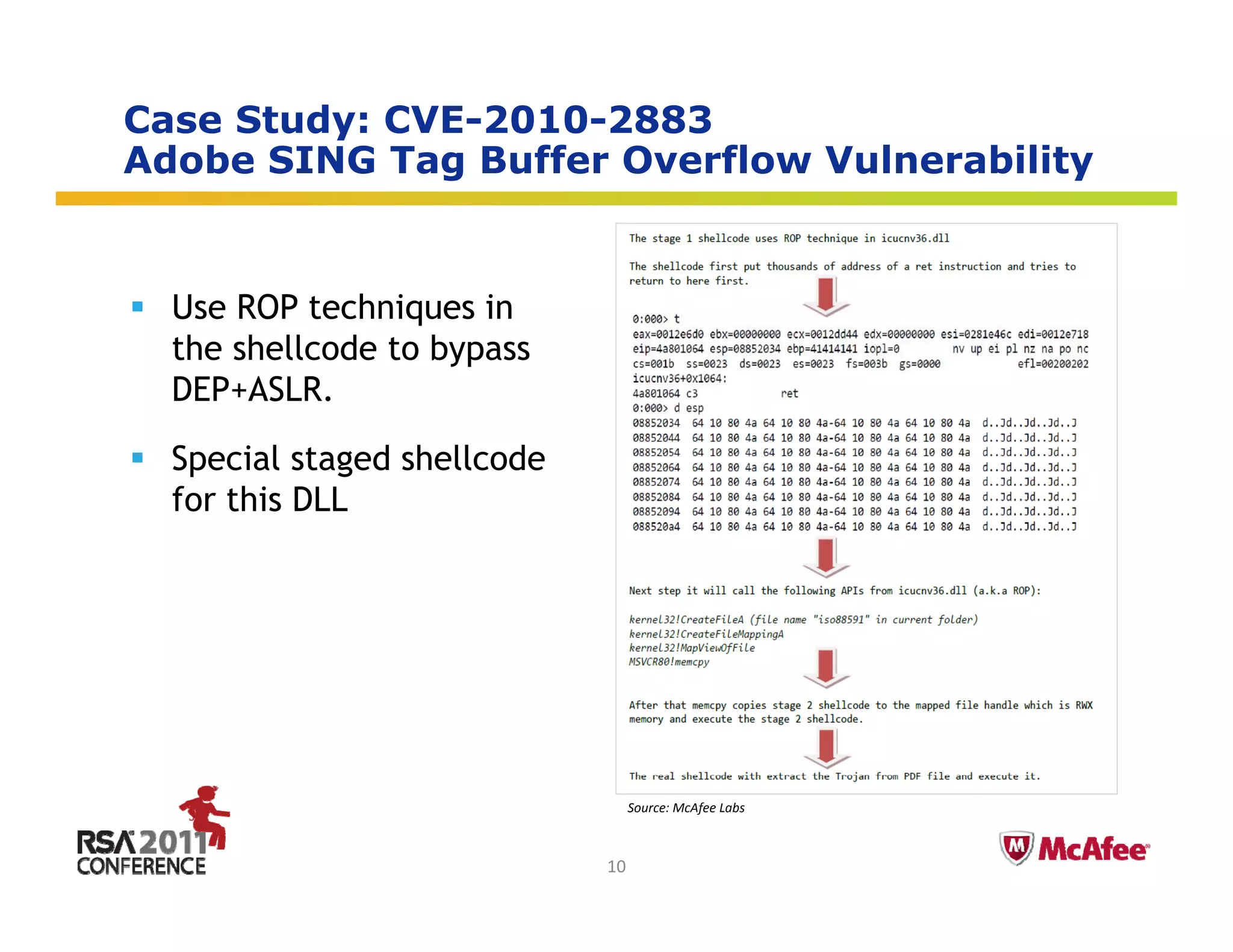
The document discusses the evolving threat landscape in 2010. It covers several topics: (1) vulnerabilities and exploitation increased in 2010, with Microsoft and Adobe products being frequently targeted; (2) targeted attacks like Operation Aurora exploited zero-day vulnerabilities to infiltrate major companies; (3) cybercrime expanded through exploiting social networks to send spam and distribute malware. The document analyzes these trends through specific case studies and statistics from McAfee Labs.



![DEP+ASLR=Peace of Mind!
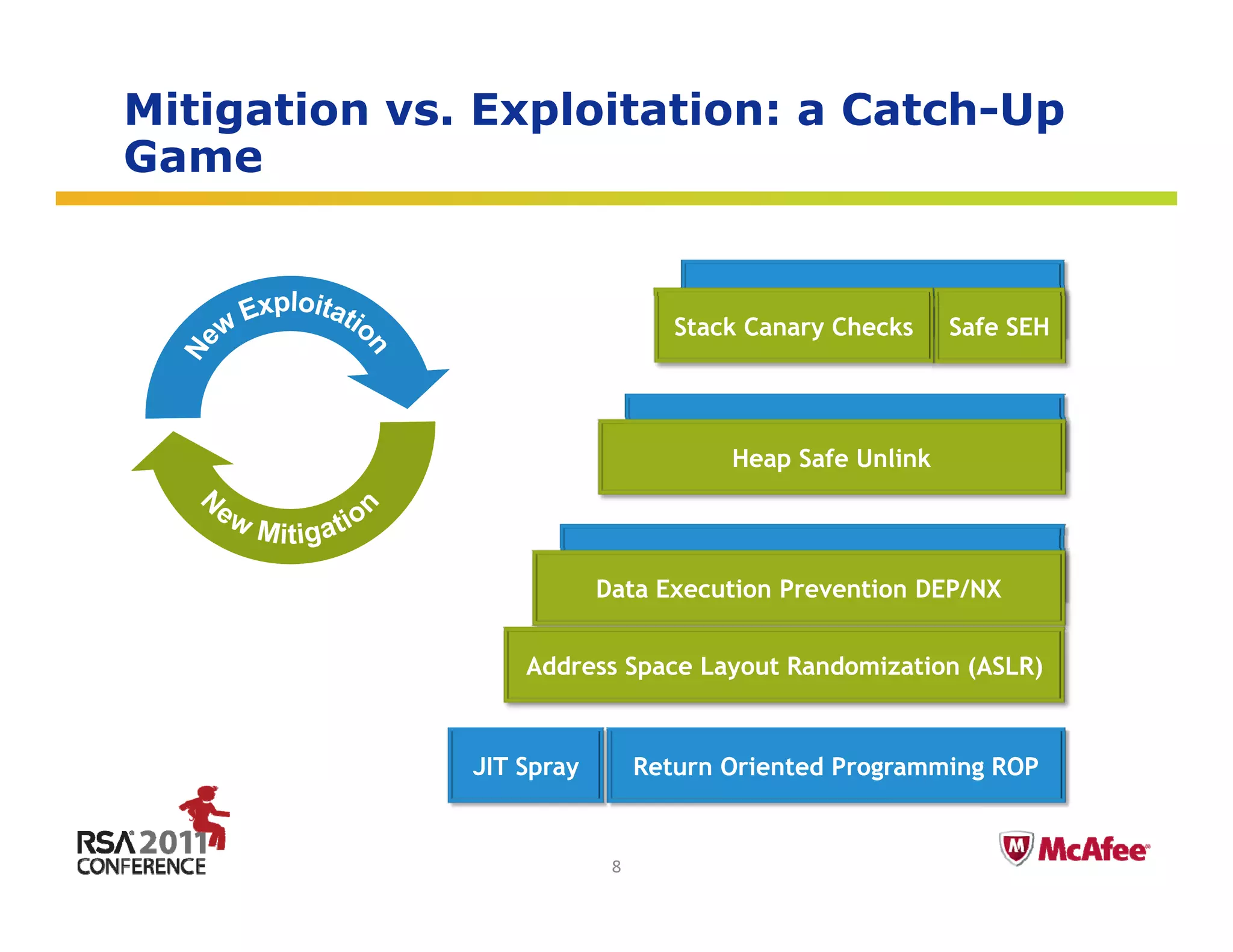
Exploitation
Vulnerability
y
technique
Adobe Products Authplay.dll Code Execution [CVE-2010-3654 ] ROP Shellcode
ROP Shellcode
Adobe Products Authplay dll Code Execution [CVE-2010-2884]
Authplay.dll
Adobe Flash Player, Reader, and Acrobat 'authplay.dll‘ [CVE-2010-1297] ROP Shellcode
Adobe Reader and Acrobat XFA TIFF Support Code Execution
ROP Shellcode
Vulnerability [CVE-2010-0188]
Adobe Reader 'CoolType.dll' TTF Font Vulnerability [CVE-2010-2883] ROP Shellcode
Adobe Reader and Acrobat 'newplayer()' JavaScript Method Vulnerability ROP Shellcode
[CVE-2009-4324]
Insert presenter logo
here on slide master.
See hidden slide 2 for
11 directions](https://image.slidesharecdn.com/ht2-106rsa-111007011703-phpapp01/75/Evolving-Threat-Landscape-11-2048.jpg)