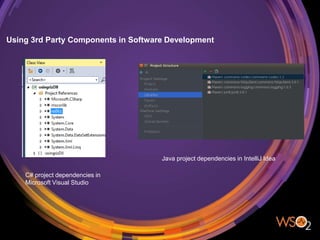
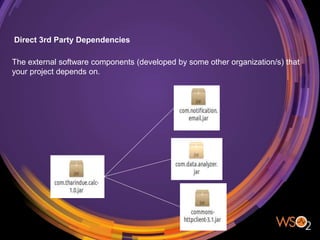
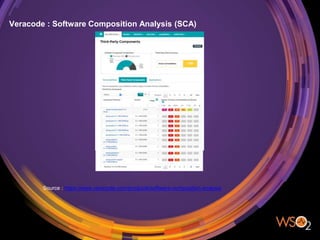
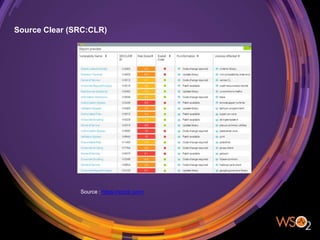
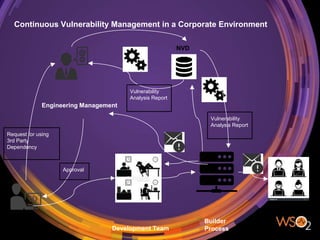
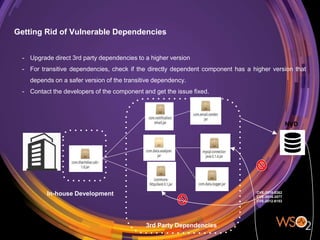
The document discusses the management of security in third-party software dependencies, explaining concepts such as direct and transitive dependencies, and known vulnerabilities. It emphasizes the importance of using tools like the National Vulnerability Database and OWASP Dependency Check to identify and address vulnerabilities in external components. Finally, it outlines a systematic approach for vulnerability management, including identification, analysis, and resolution of dependencies with known issues.