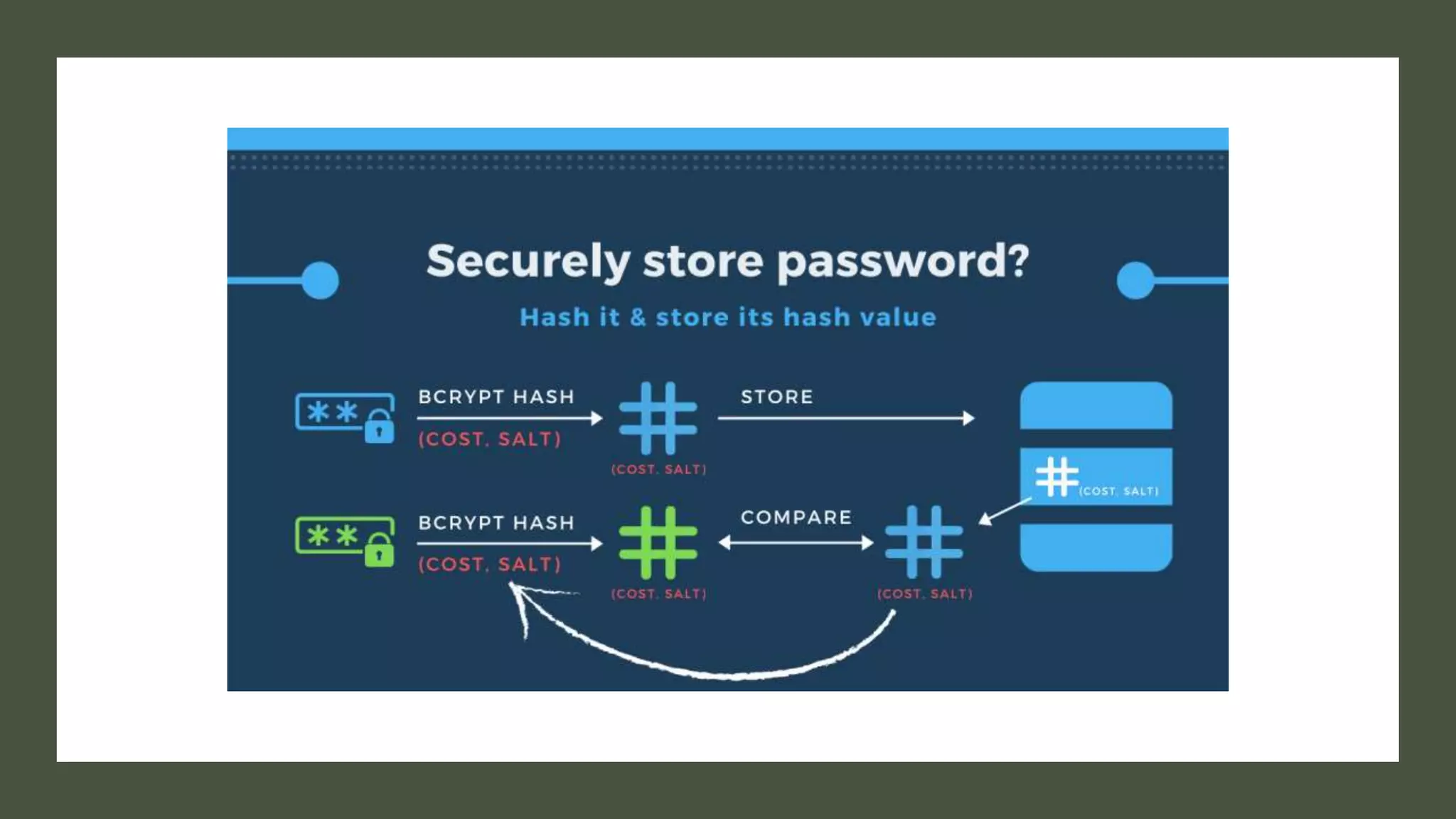
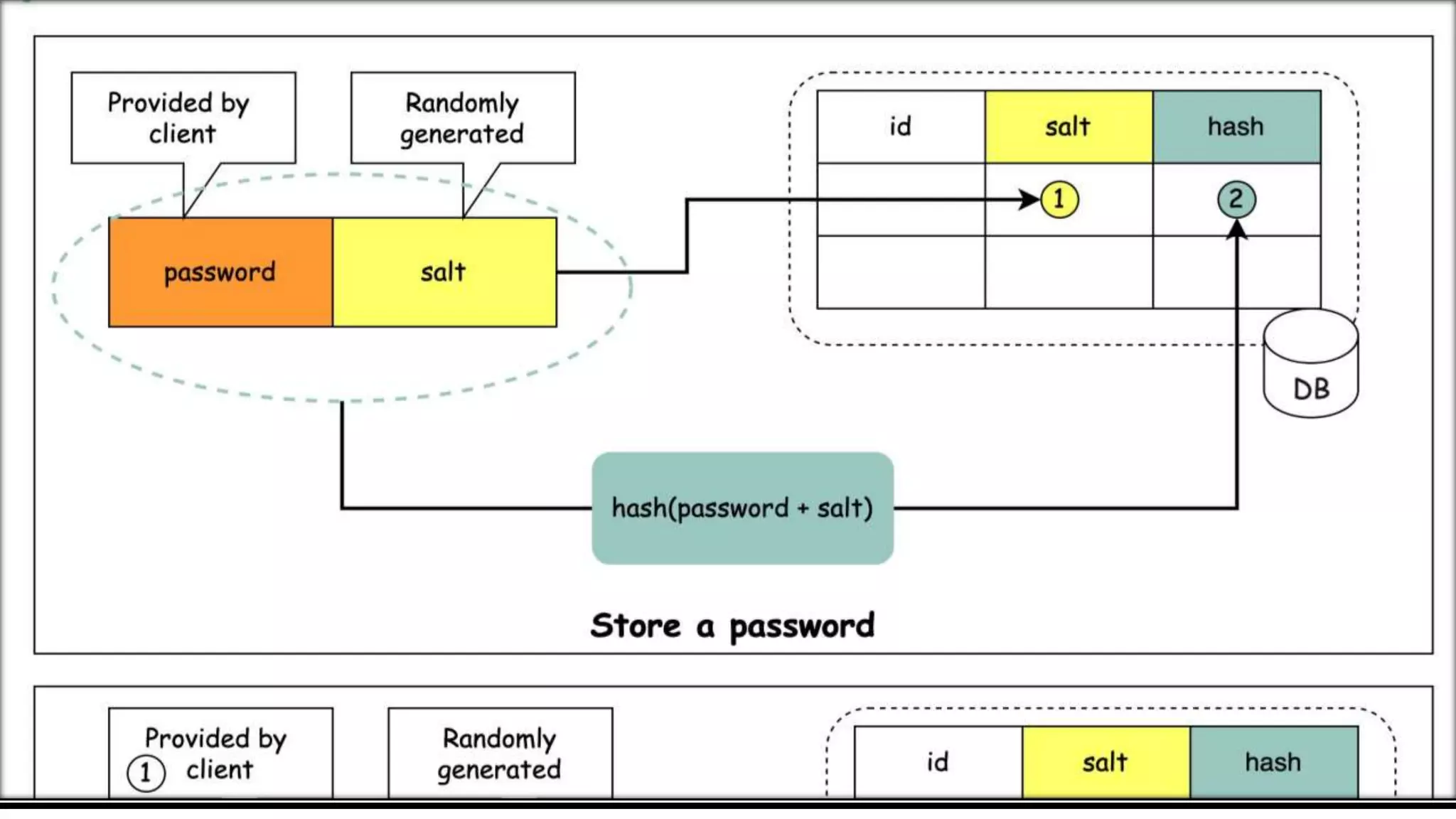
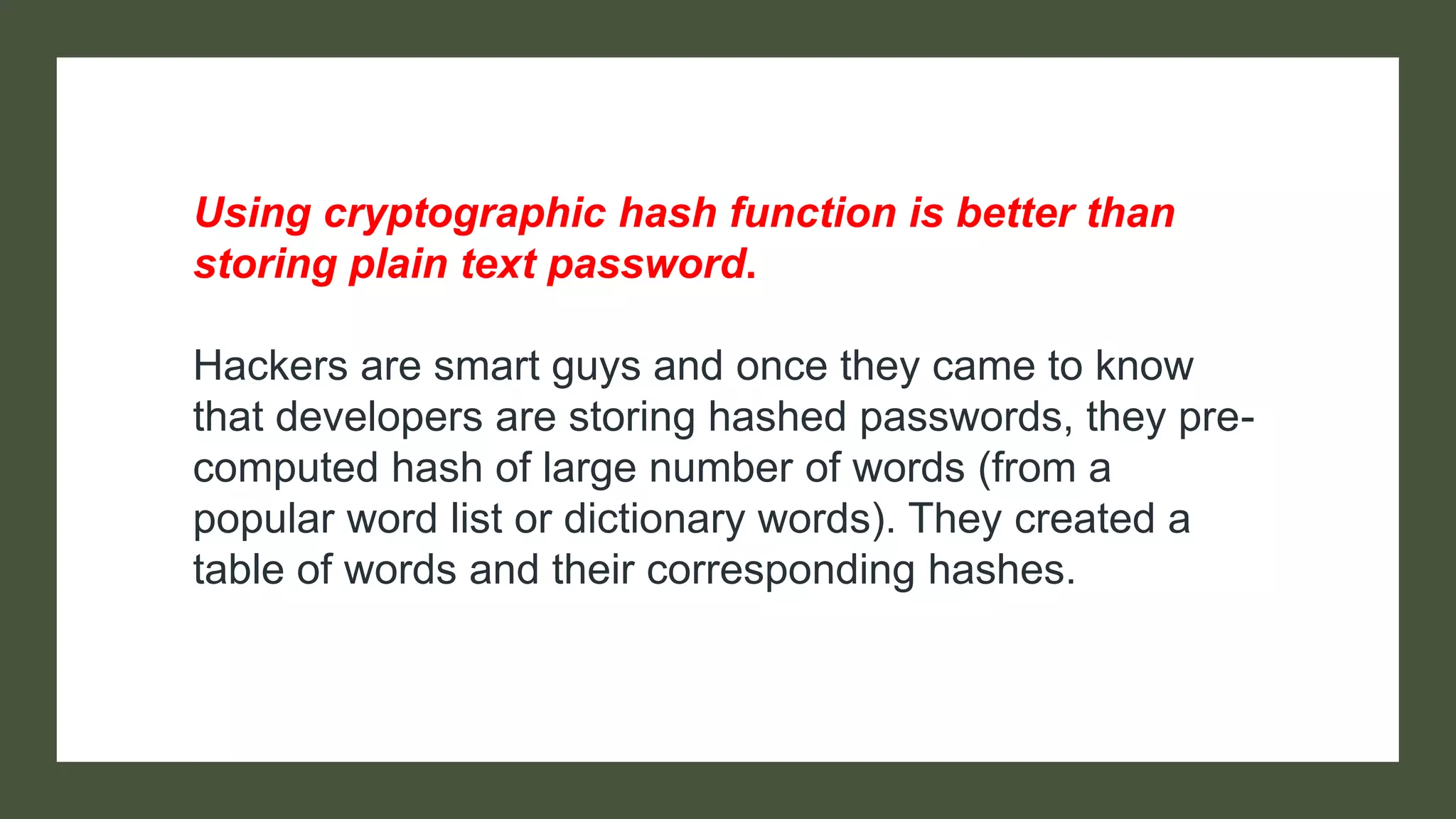
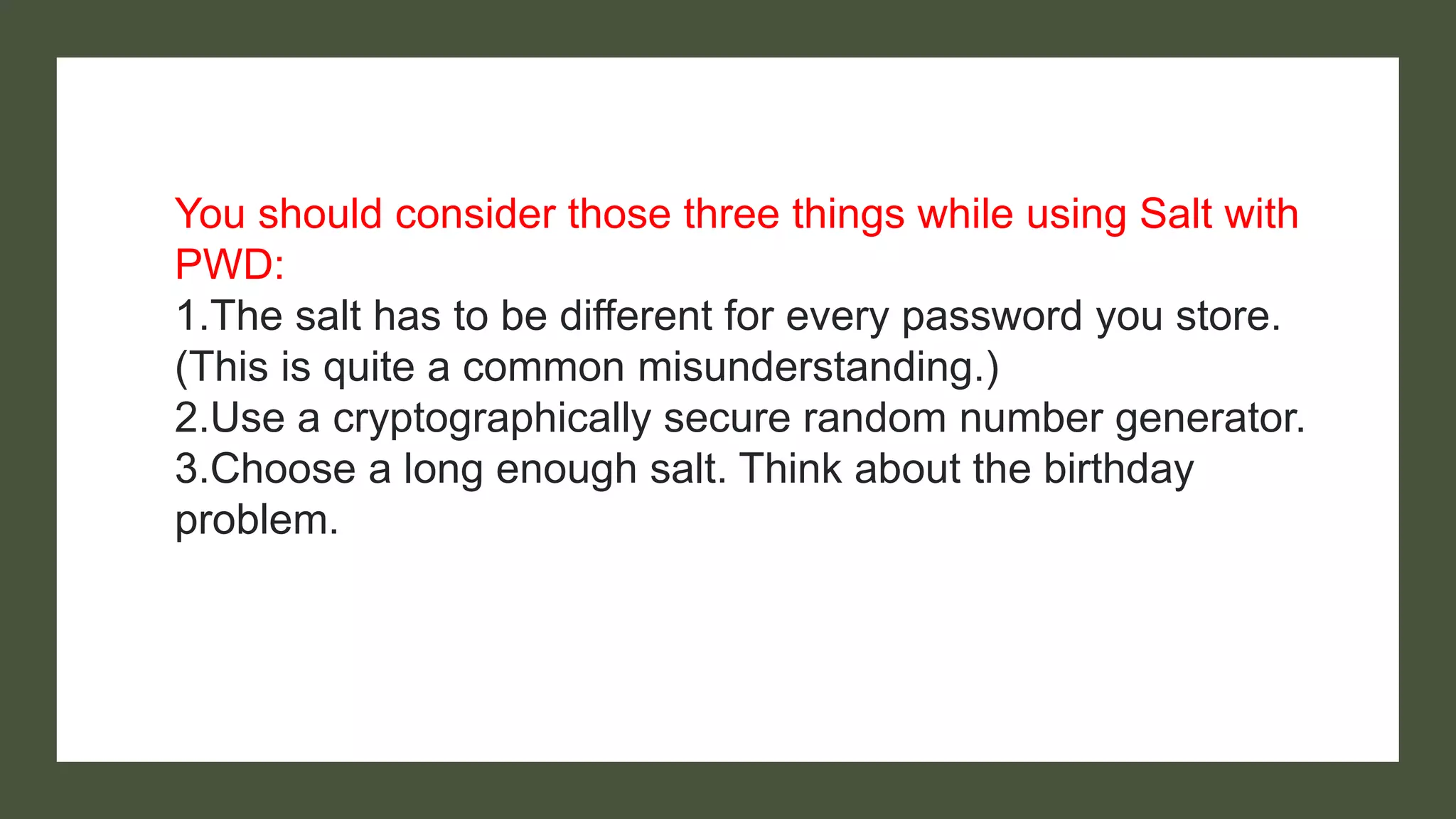
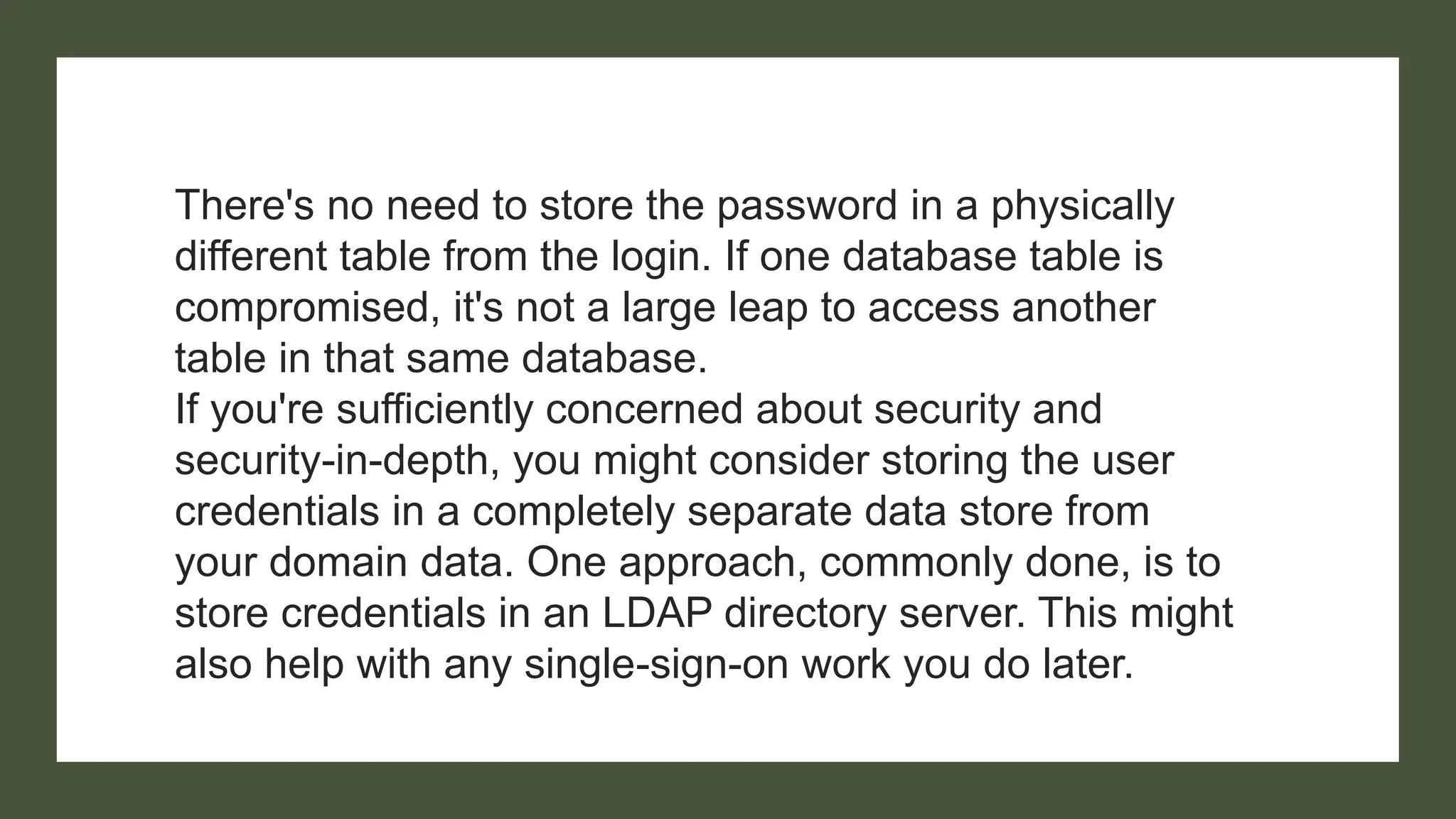
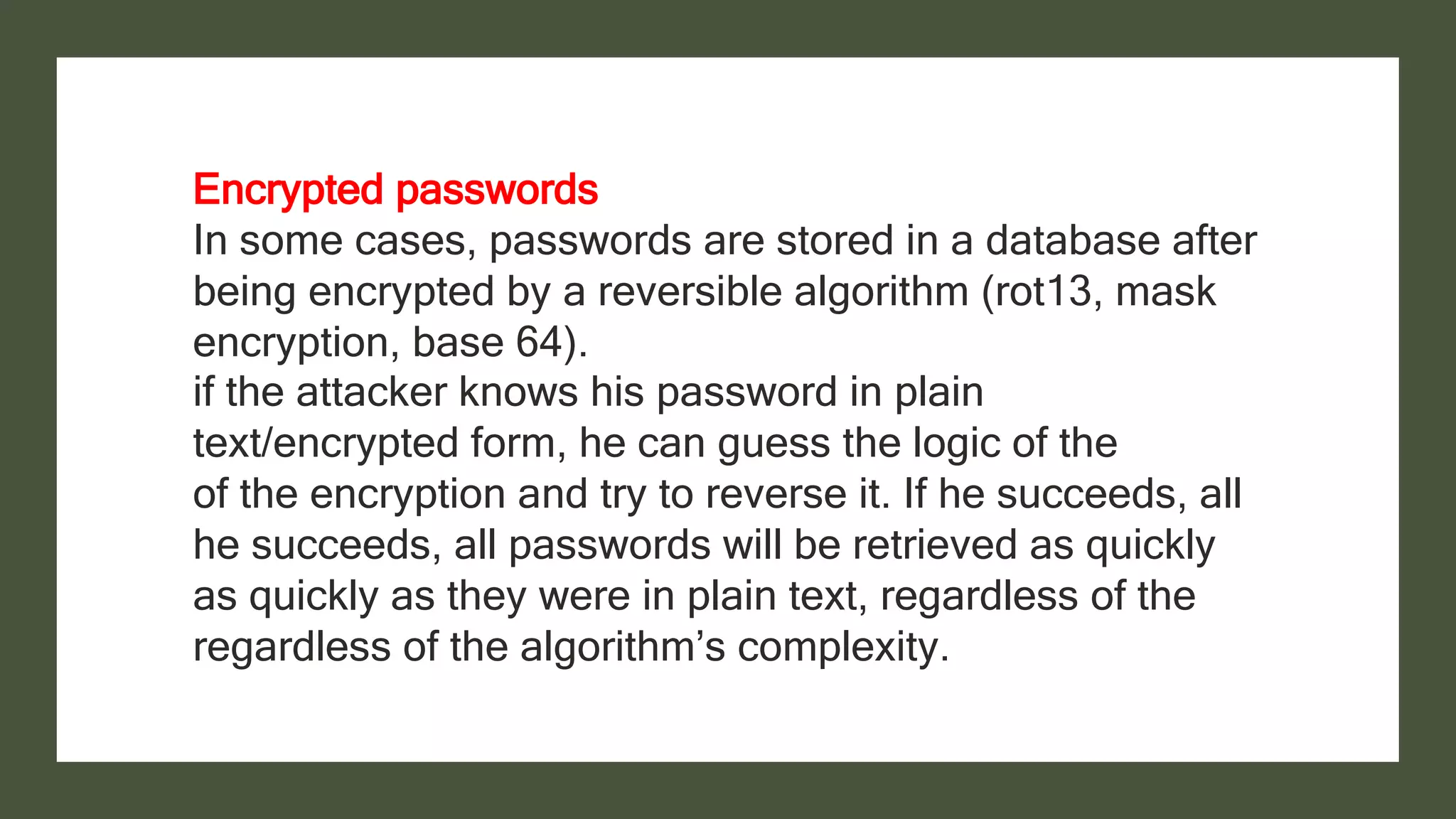
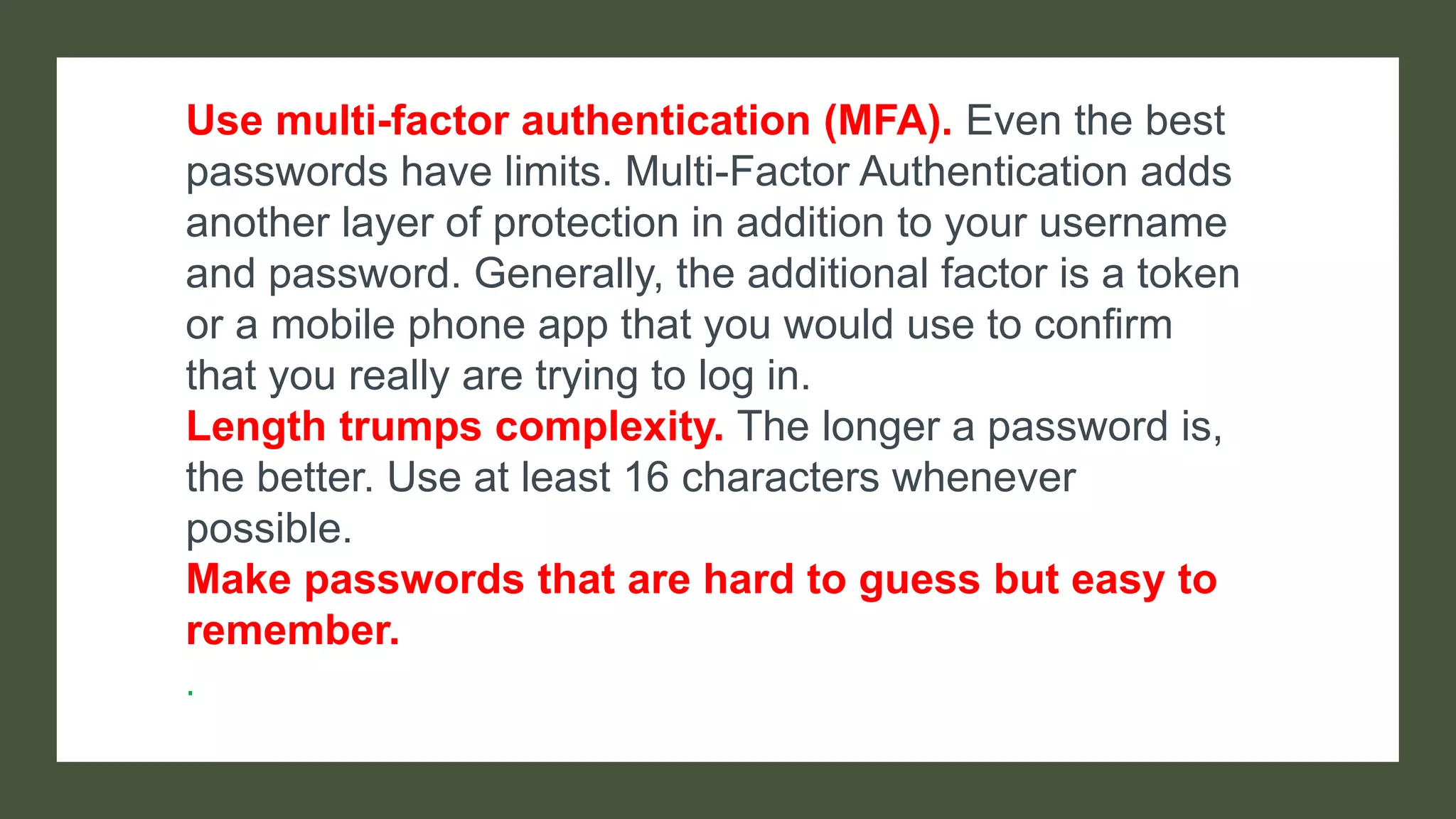
Bcrypt is a hashing function that hashes passwords with a salt and cost parameter to encrypt passwords stored in a database. The salt is randomly generated for each password, meaning the same password will hash to different values. Both the salt and cost are stored with the hashed password. Hackers may pre-compute hashes from word lists to crack hashed passwords, so proper salting is important.