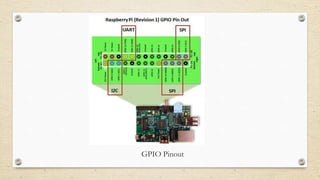
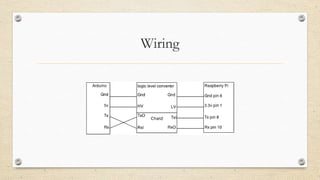
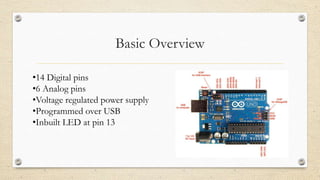
This document provides an introduction to hardware hacking using Raspberry Pi and Arduino. It discusses why hardware hacking is interesting and rewarding as it allows interacting with the physical world. It then provides tutorials on basic projects like blinking an LED using Raspberry Pi and Arduino to illustrate hardware interfacing concepts. These include using GPIO pins on Raspberry Pi and digital pins on Arduino boards. The document encourages exploring additional capabilities like I2C, SPI and serial communication. It also introduces Arduino shields and provides examples of infrared communication and emulating human interface devices.