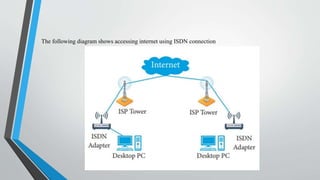
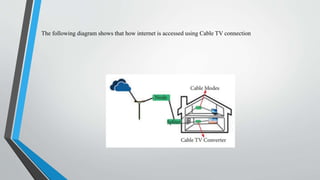
The document outlines the hardware and software requirements for internet connectivity, describing different connection methods including dial-up, DSL, ISDN, cable, satellite, and wireless. It also discusses the evolution of the internet and the importance of user authentication methods, such as passwords, multi-factor authentication, biometric authentication, and token-based systems. The conclusion emphasizes the need for businesses to adopt advanced authentication technologies to enhance user experience and improve security against data breaches.