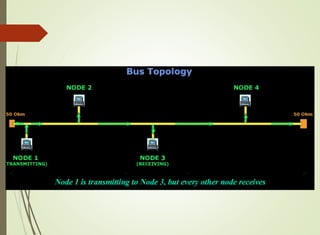
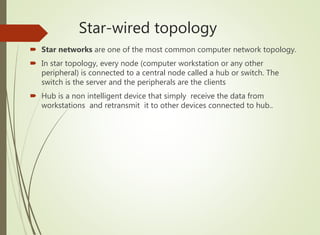
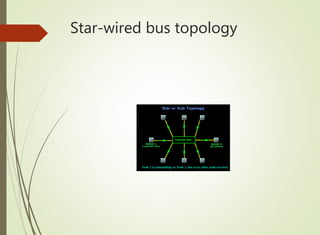
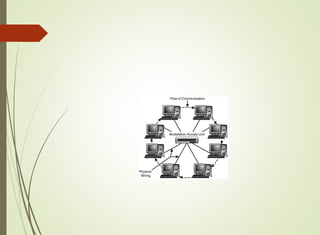
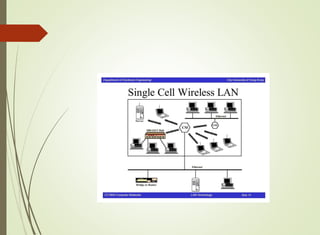
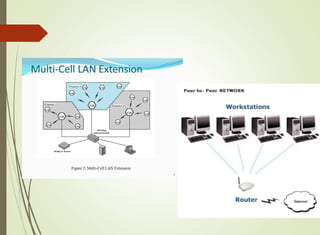
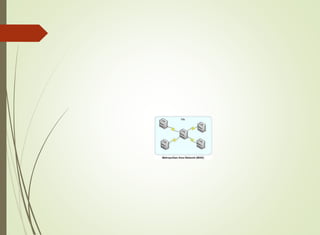
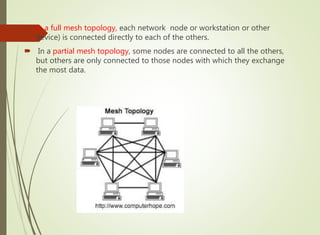
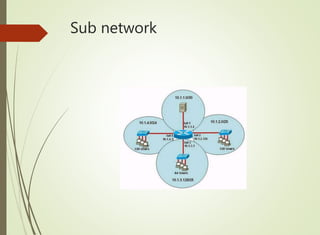
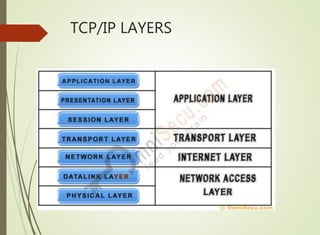
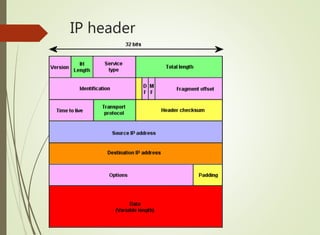
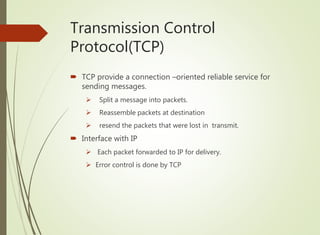
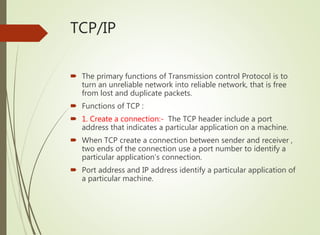
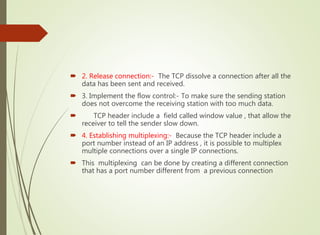
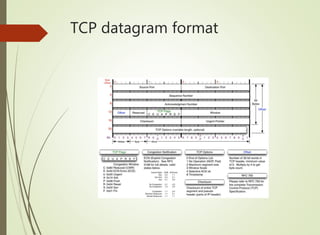
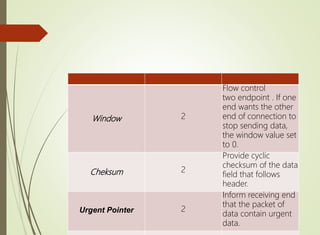
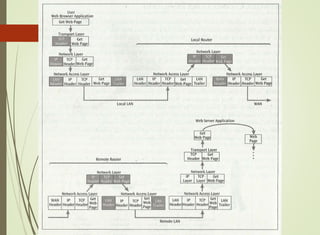
The document discusses local area networks (LANs). It defines a LAN as a network that interconnects data communication devices within a small geographic area and broadcasts data at high transfer rates. Examples of connected devices include PCs, workstations, and printers. Common LAN topologies discussed include bus, star, ring, and wireless configurations. The document also covers the roles and components of TCP/IP networking layers.