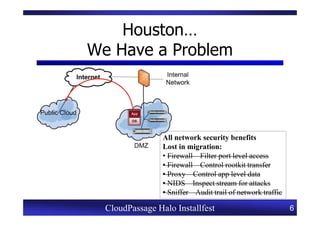
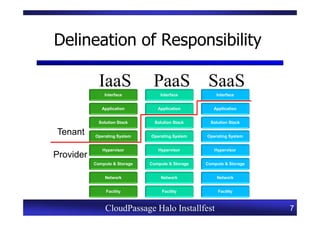
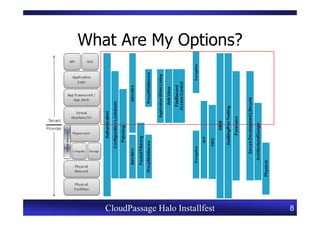
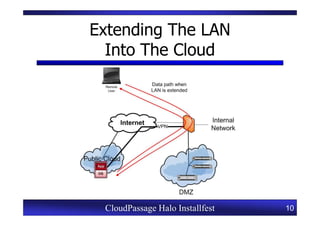
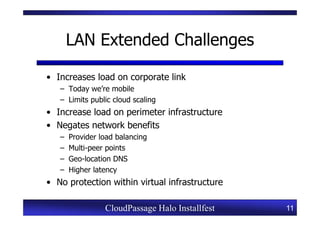
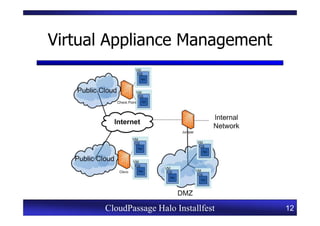
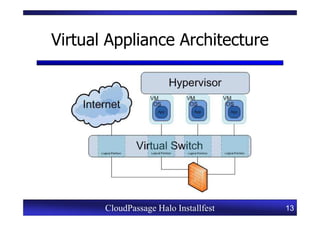
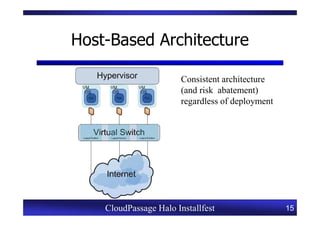
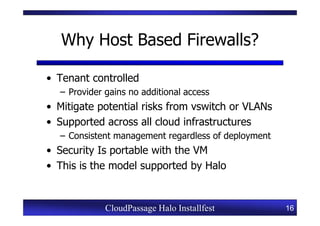
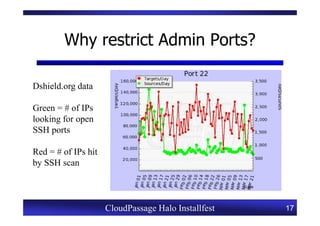
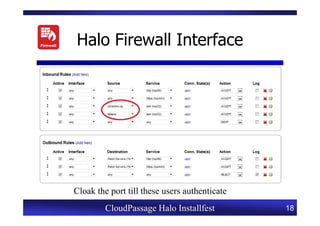
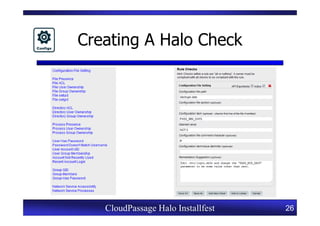
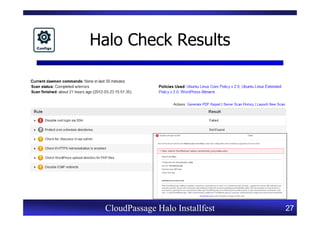
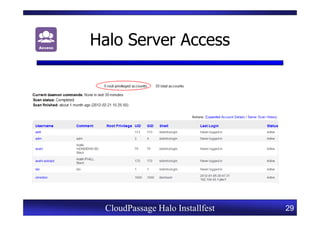
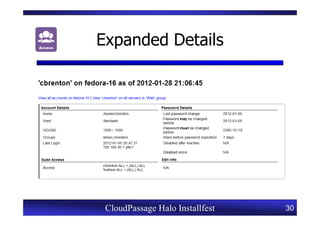
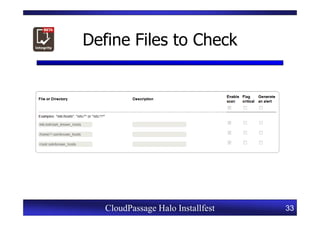
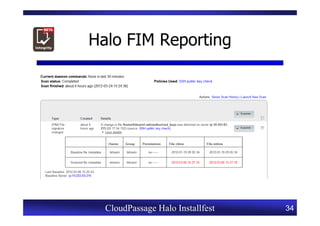
This document provides an overview of a CloudPassage Halo installfest event. It discusses security issues with infrastructure as a service (IaaS) cloud computing models including lack of firewall control, vulnerability management challenges, and difficulty detecting intrusions. It introduces CloudPassage Halo as a host-based security solution that can address these issues by providing firewall rules, vulnerability scanning, configuration monitoring, and event detection across virtual machines. The installfest will guide participants on installing and using CloudPassage Halo to gain security visibility and control over their cloud infrastructure.