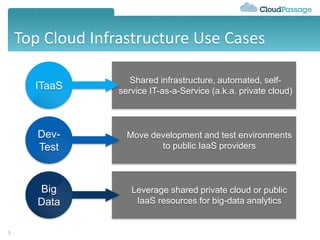
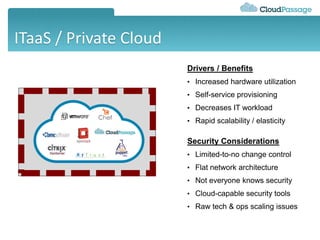
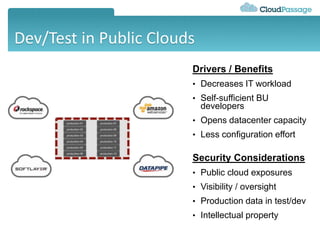
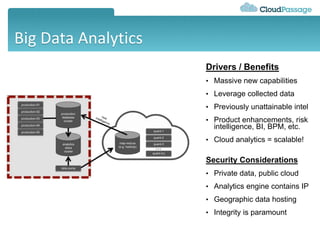
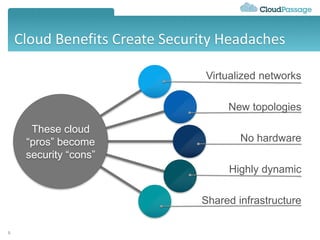
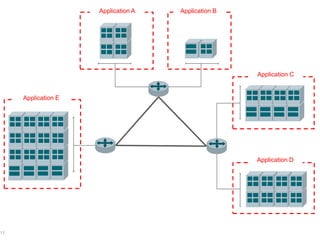
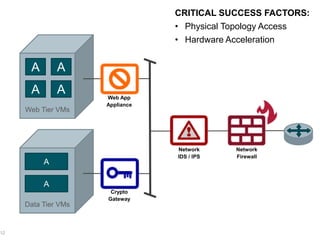
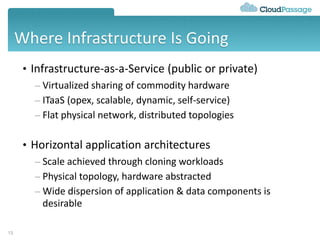
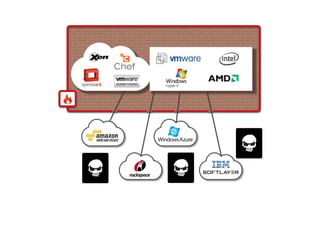
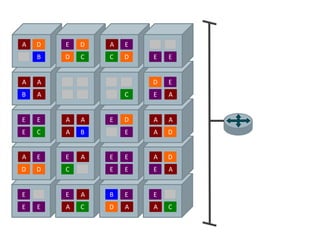
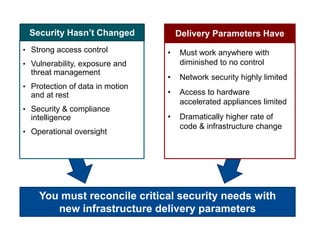
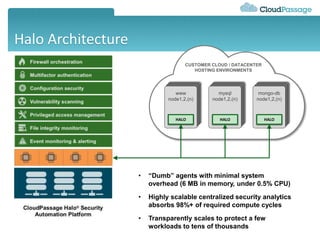
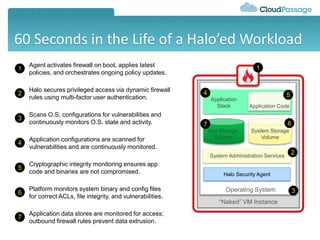
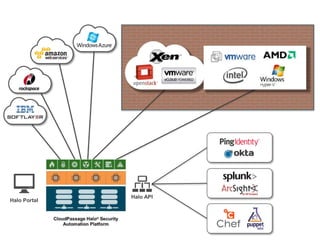
This document discusses security challenges for enterprise cloud infrastructure and different approaches to addressing them. It summarizes common cloud use cases like ITaaS, development/testing in public clouds, and big data analytics. It then outlines challenges like virtualized networks and lack of hardware controls. Next-generation approaches like virtual appliances, in-hypervisor controls, and workload-based security are presented along with pros and cons. The document focuses on CloudPassage's workload-based security agent Halo, which provides automated security and compliance controls that scale across cloud environments.