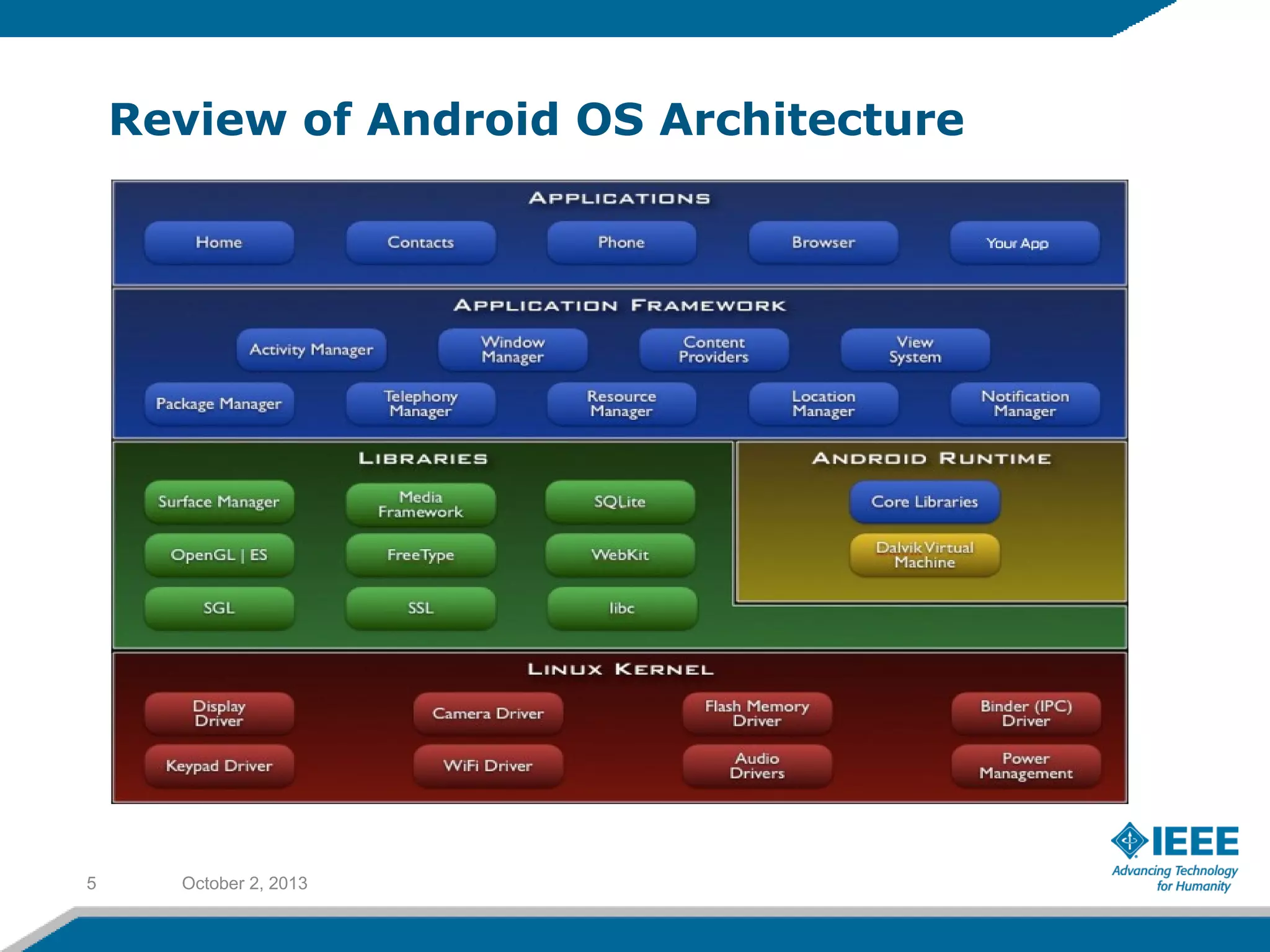
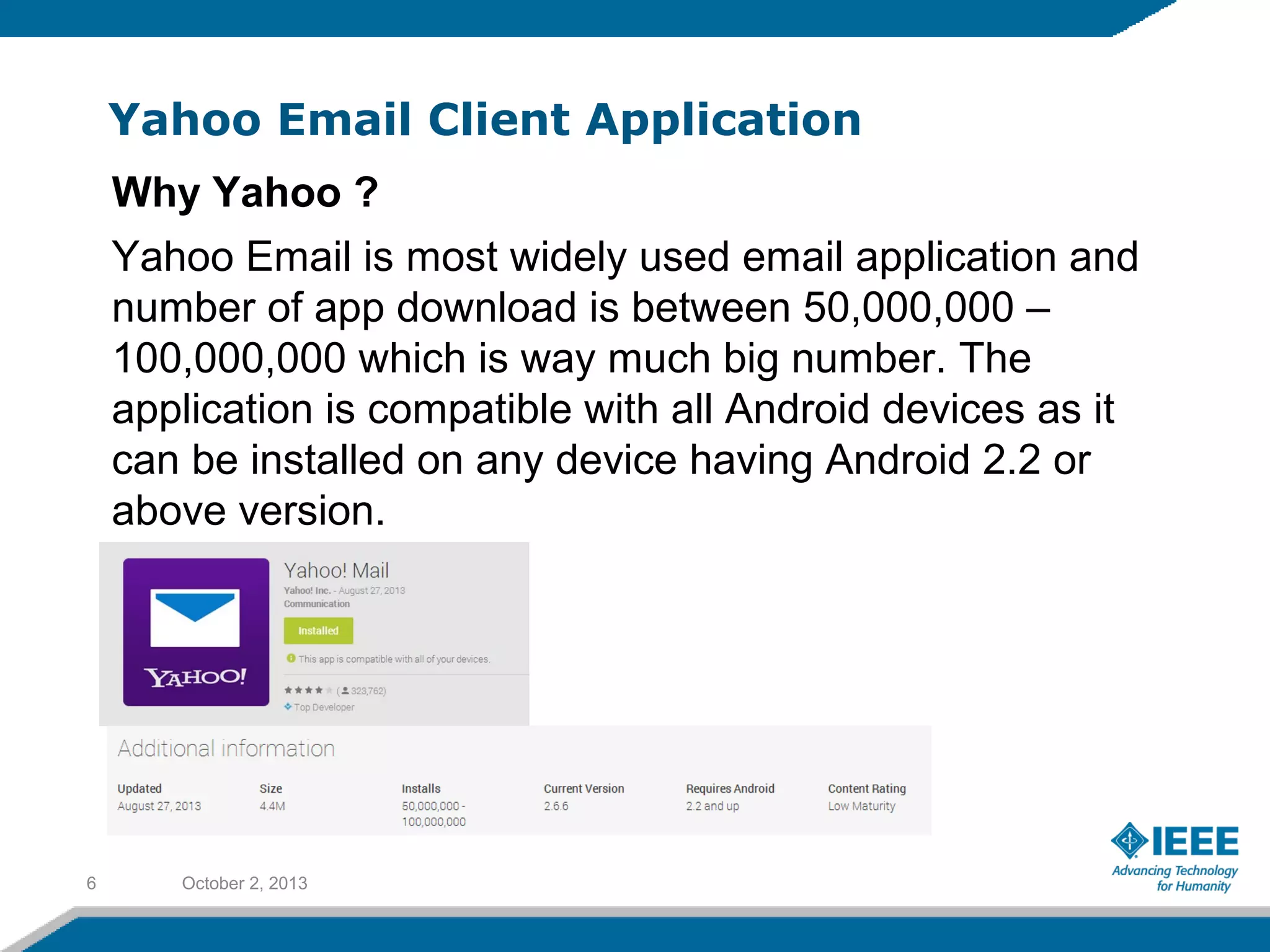
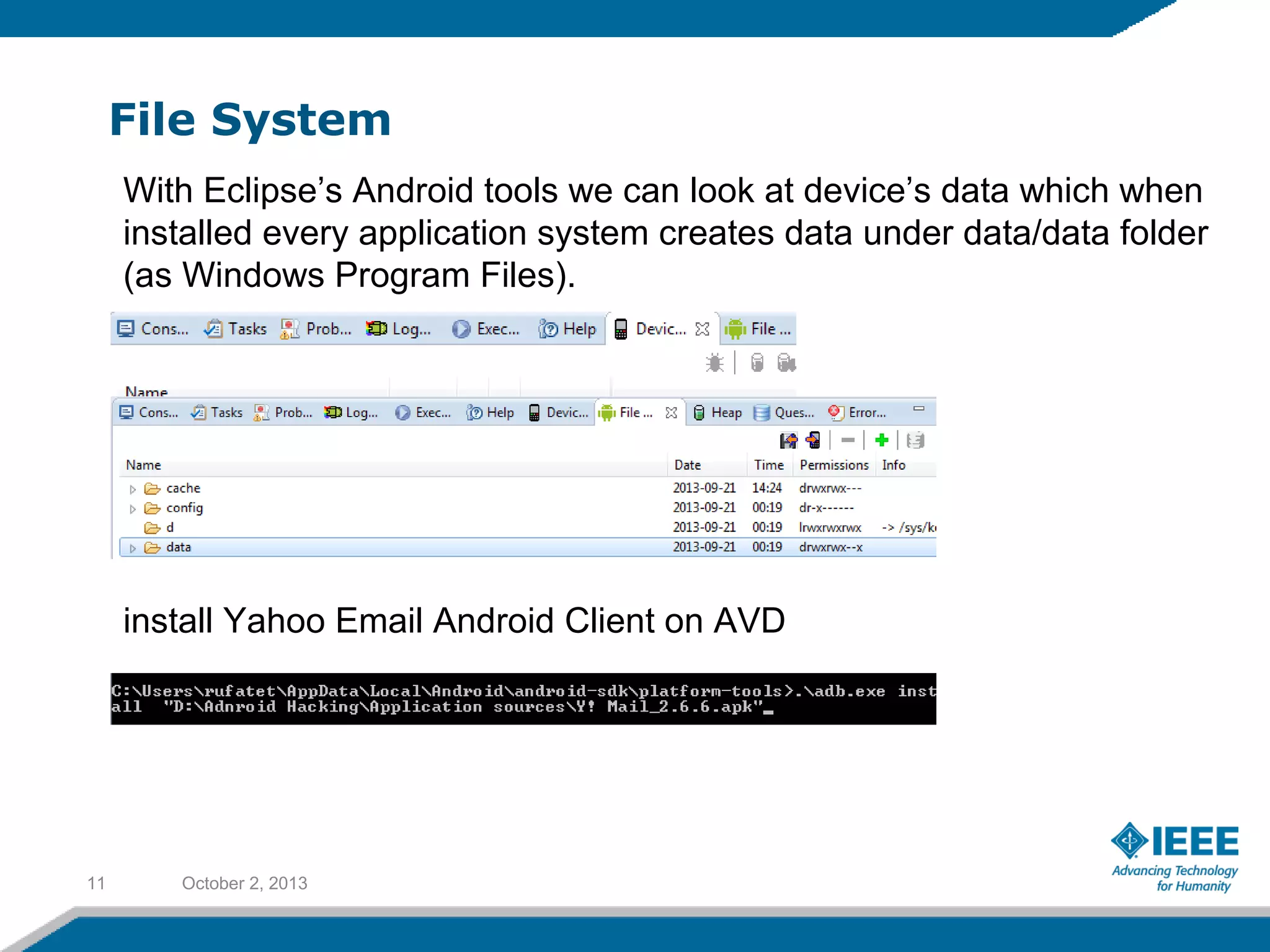
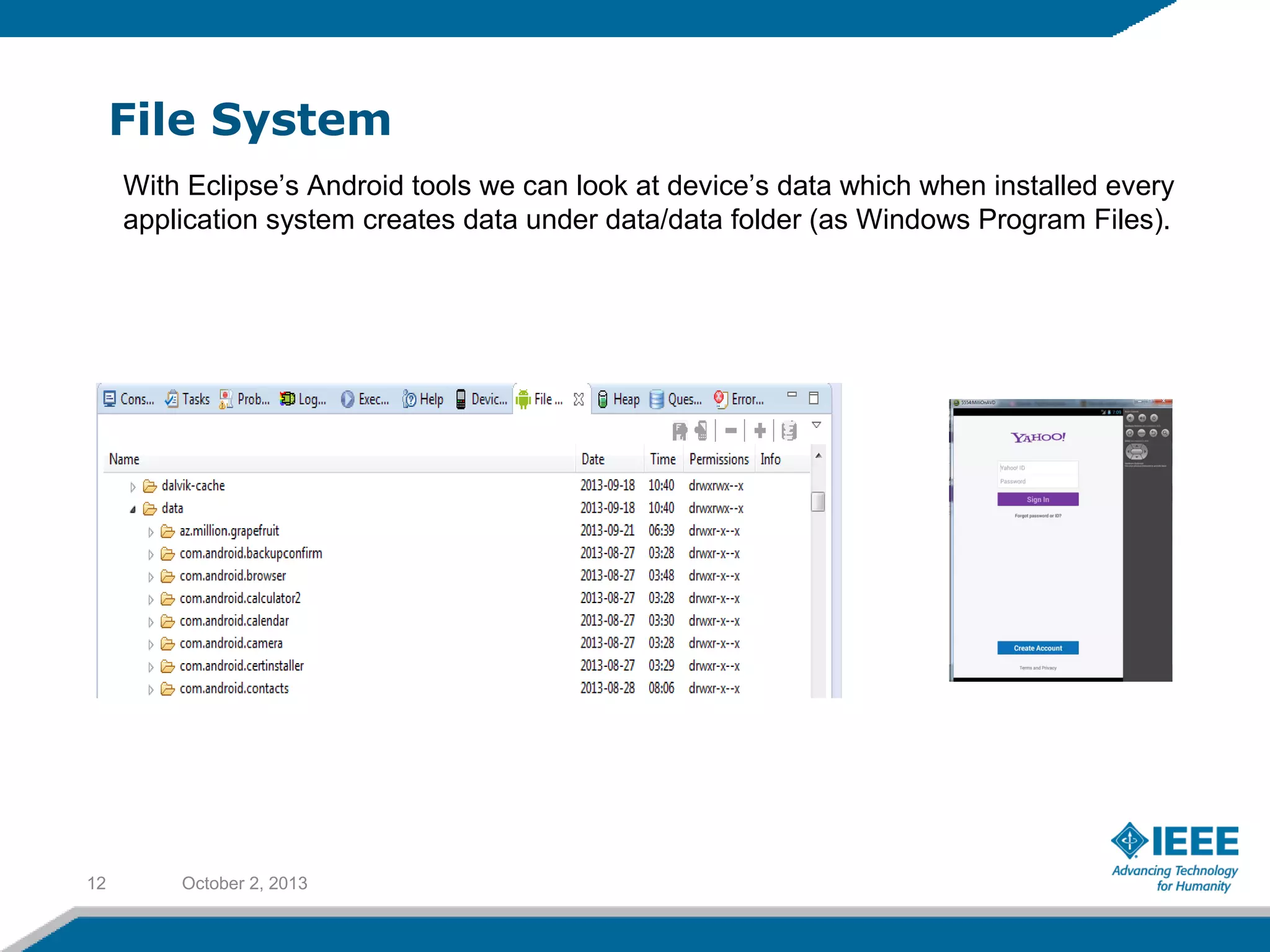
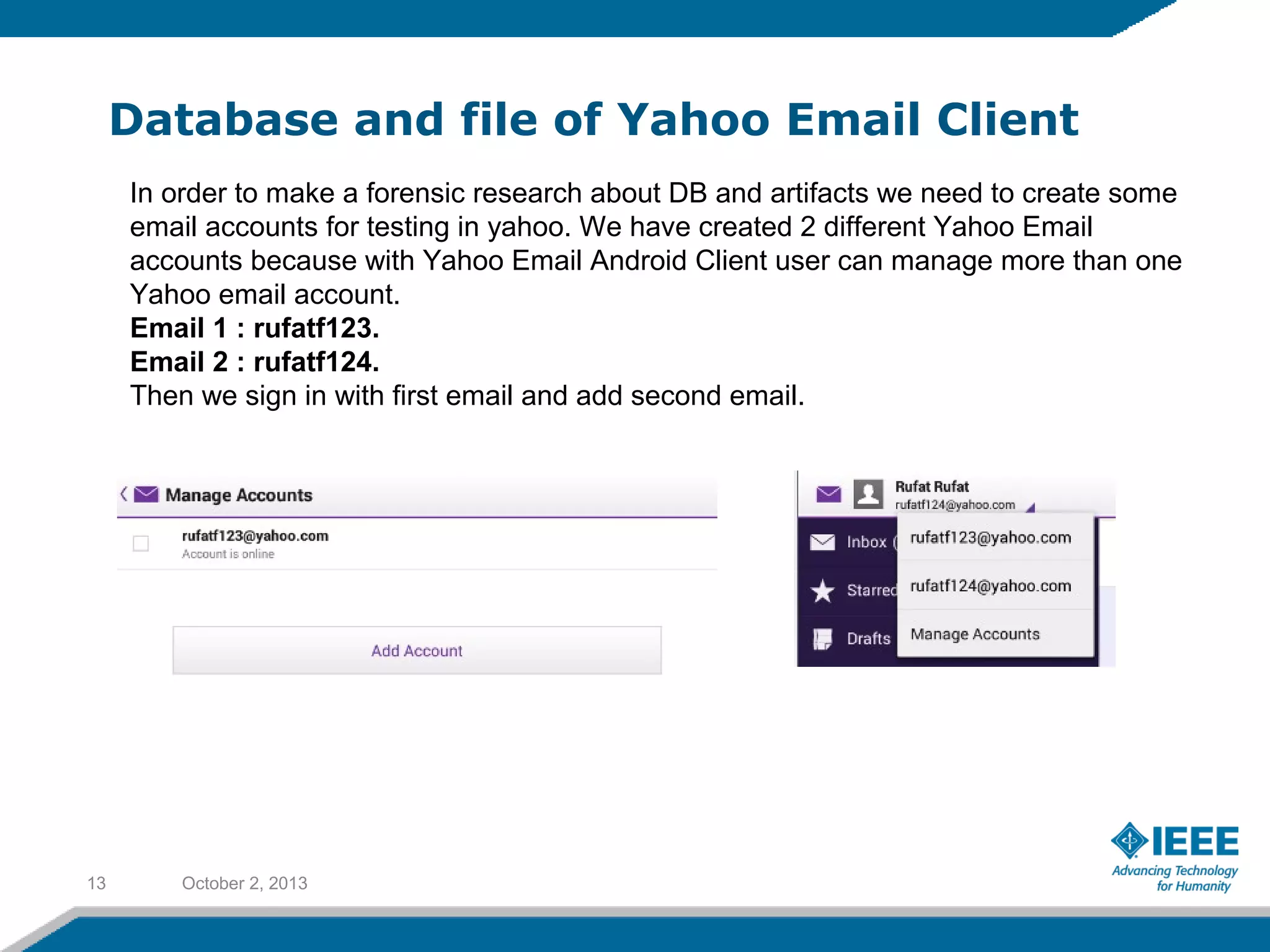
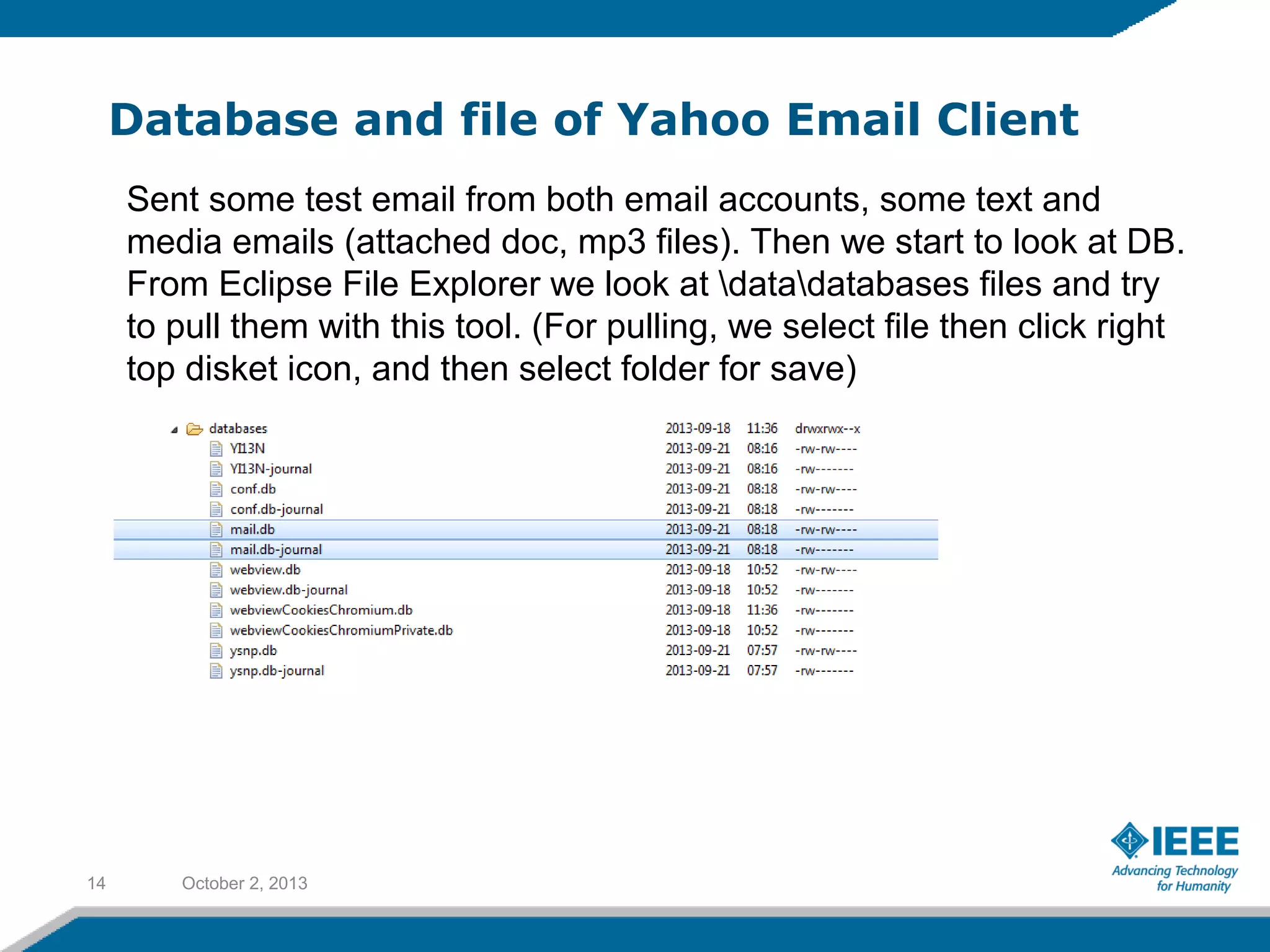
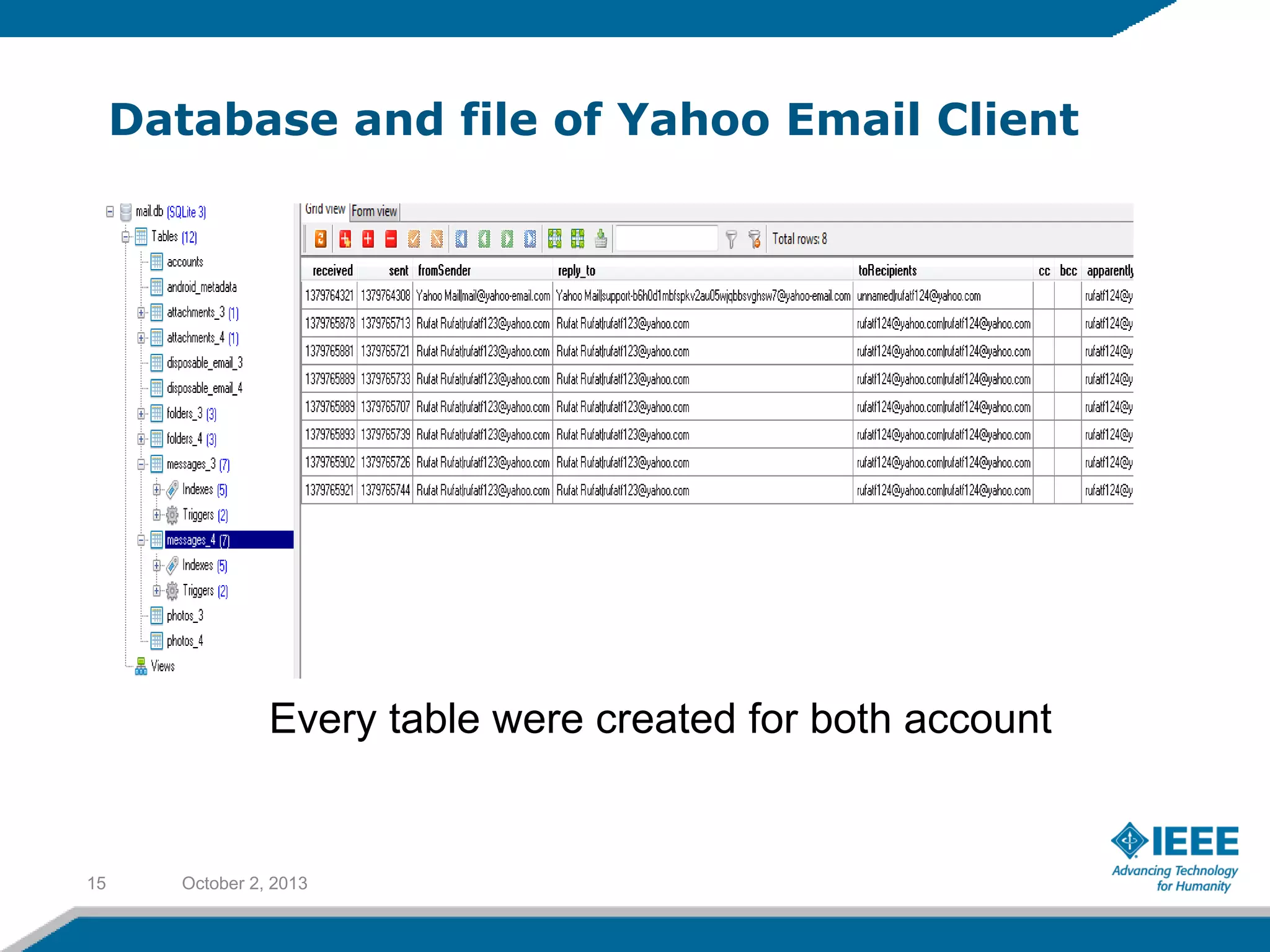
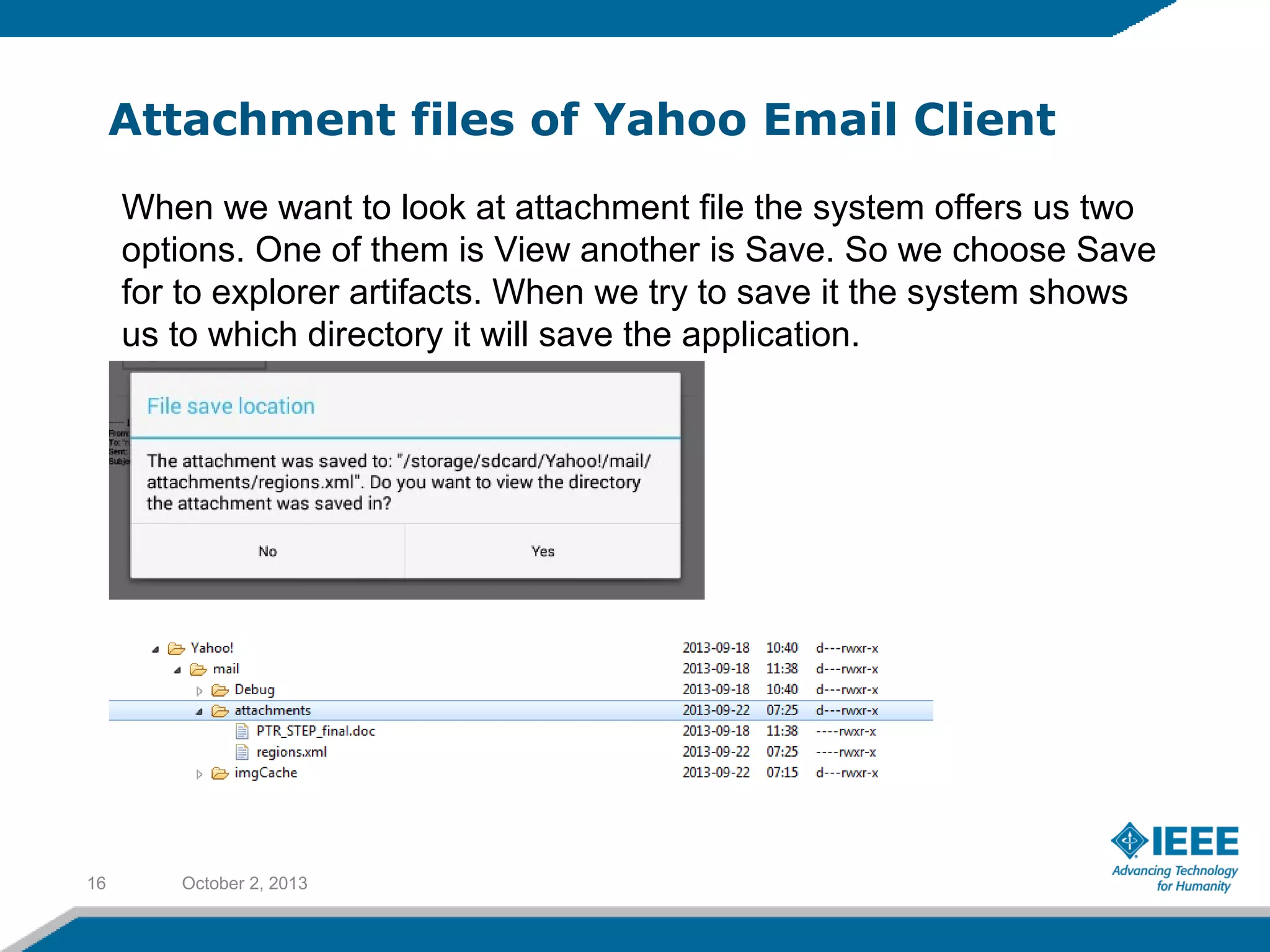
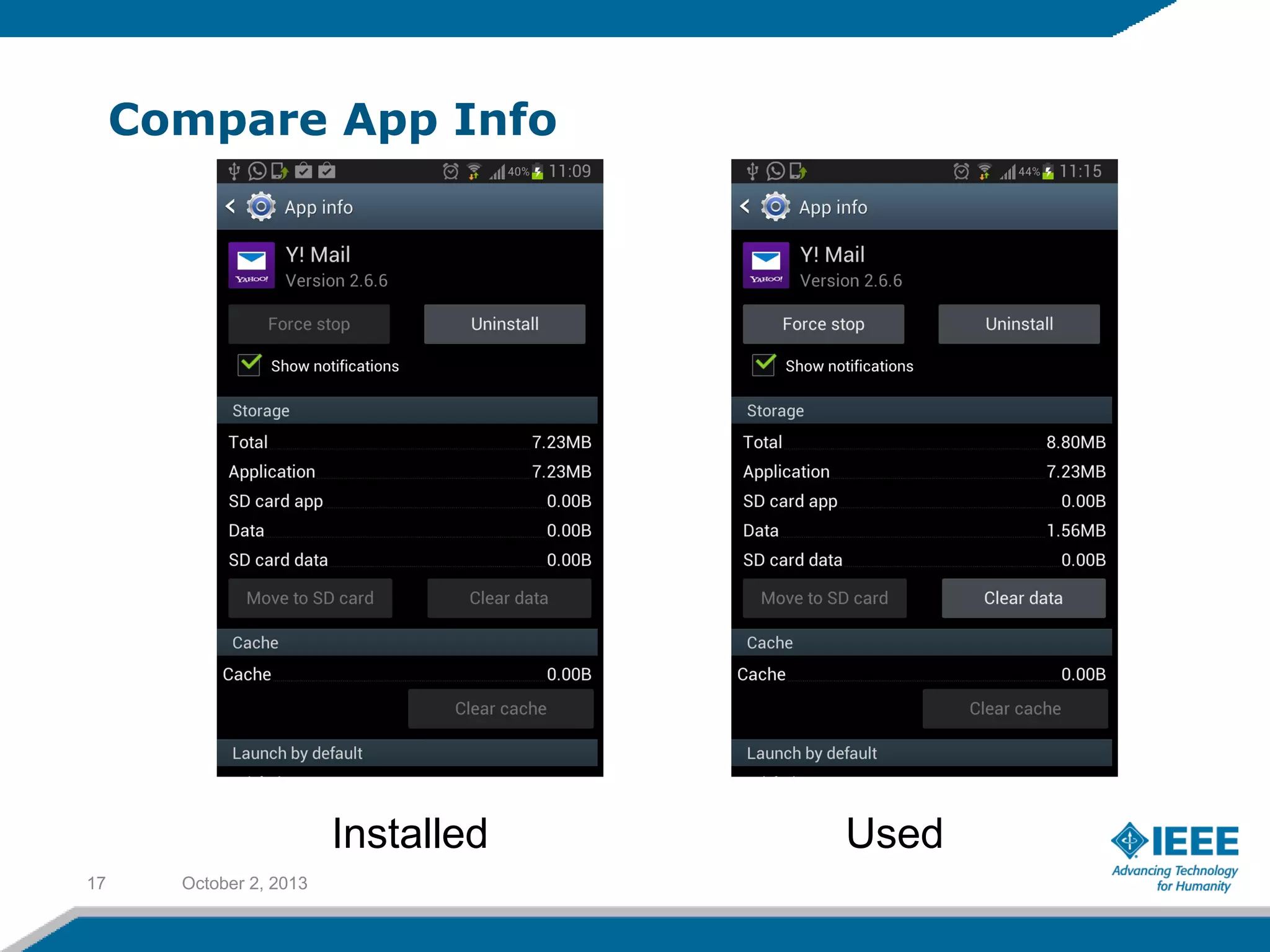
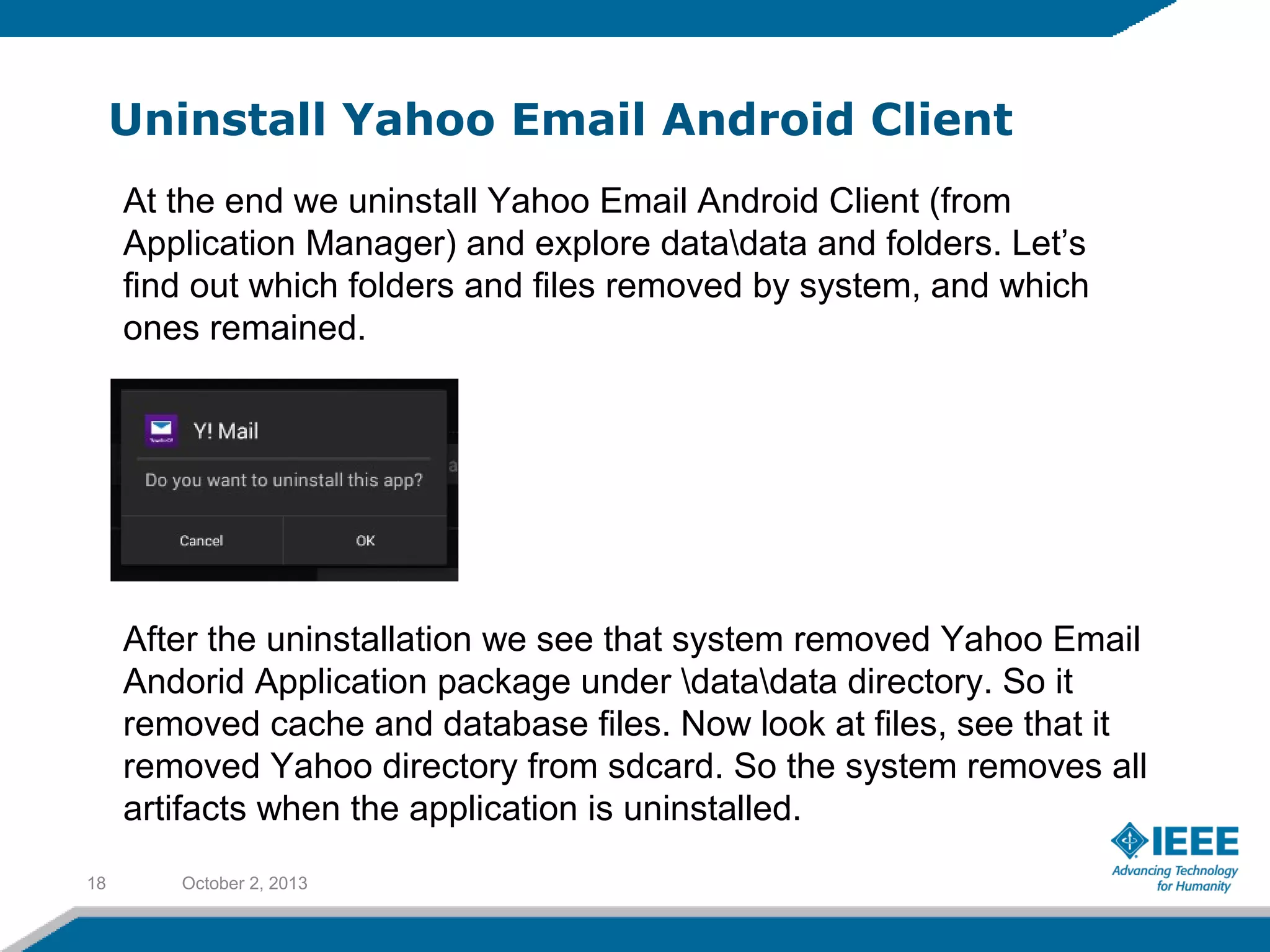
Rufat Babakishiyev will give a presentation on reverse engineering an Android application. The presentation will include an overview of reverse engineering and forensic research, a review of the Android OS architecture, an analysis of the Yahoo email client application, decompiling the application files and database, examining application artifacts after installation and uninstallation, and security best practices. The goal is to understand how the application stores and manages data and identify artifacts left behind after uninstall.



![Bibliography
October 2, 201321
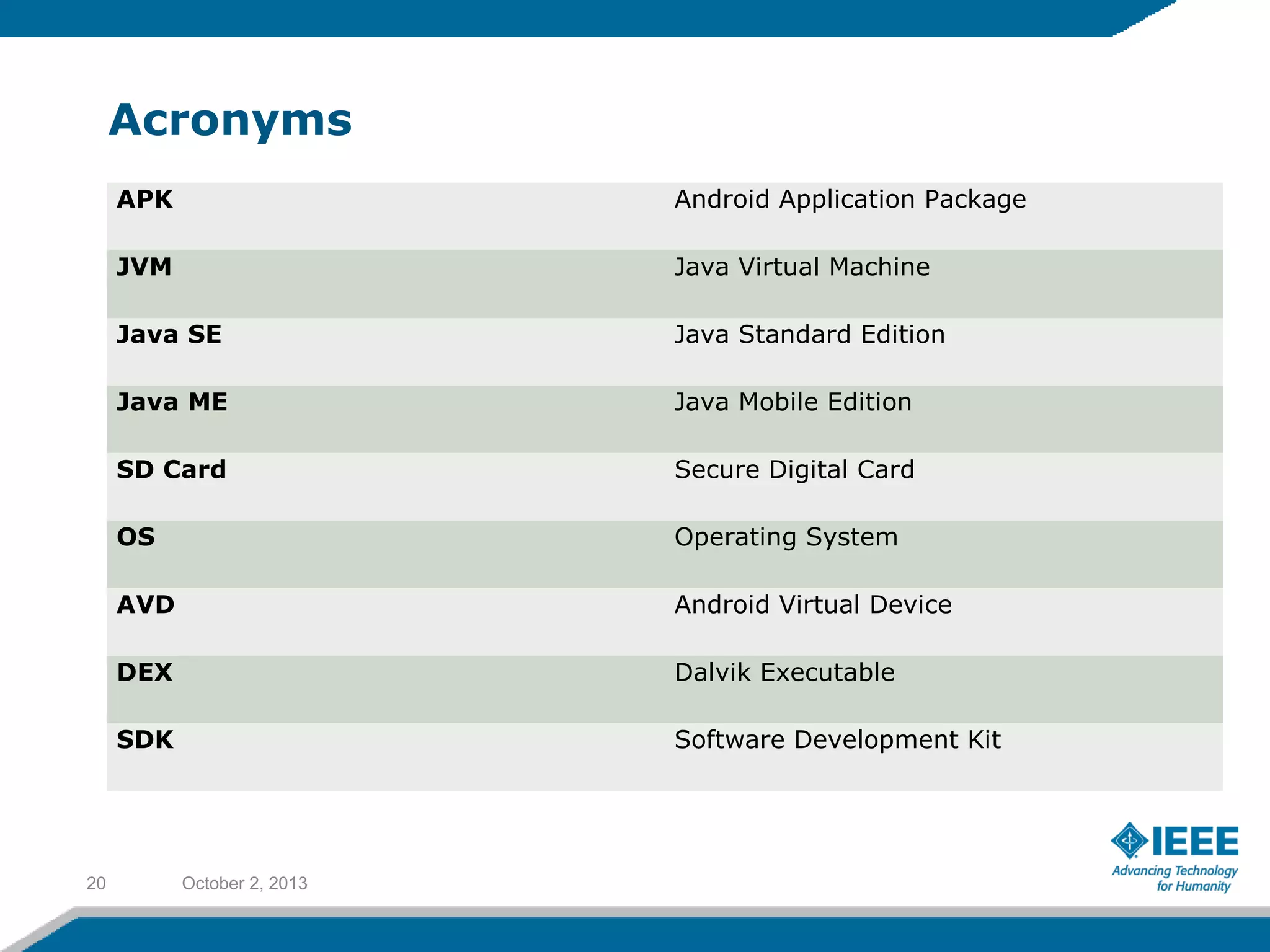
References
[1] Android OS - is a Linux-based operating system designed primarily for touchscreen
mobile devices such as smartphones and tablet computers.
http://en.wikipedia.org/wiki/Android_(operating_system)
Official web site : http://www.android.com/ and most used sub site
http://developer.android.com/index.html
[2] Android Architecture – The Key Concepts
http://www.android-app-market.com/android-architecture.html
[3] Reverse Engineering
http://searchcio-midmarket.techtarget.com/definition/reverse-engineering
[4] android apk tool
https://code.google.com/p/android-apktool/
[5] dex2jar
https://code.google.com/p/dex2jar/
[6] DJ-GUI
https://code.google.com/p/innlab/downloads/detail?name=jd-gui-
0.3.3.windows.zip&can=2&q=
[7] Google Play
For downloads applications. Yahoo and ES File Explorer
https://play.google.com/store](https://image.slidesharecdn.com/ieee-template-ppt-131002054617-phpapp01/75/IEEE-Day-2013-Reverse-Engineering-an-Android-Application-21-2048.jpg)
![Bibliography
October 2, 201322
References
[8] Techopedia.com
http://www.techopedia.com/definition/3868/reverse-engineering
[9] ES File Explorer
https://play.google.com/store/apps/details?id=com.estrongs.android.pop](https://image.slidesharecdn.com/ieee-template-ppt-131002054617-phpapp01/75/IEEE-Day-2013-Reverse-Engineering-an-Android-Application-22-2048.jpg)
