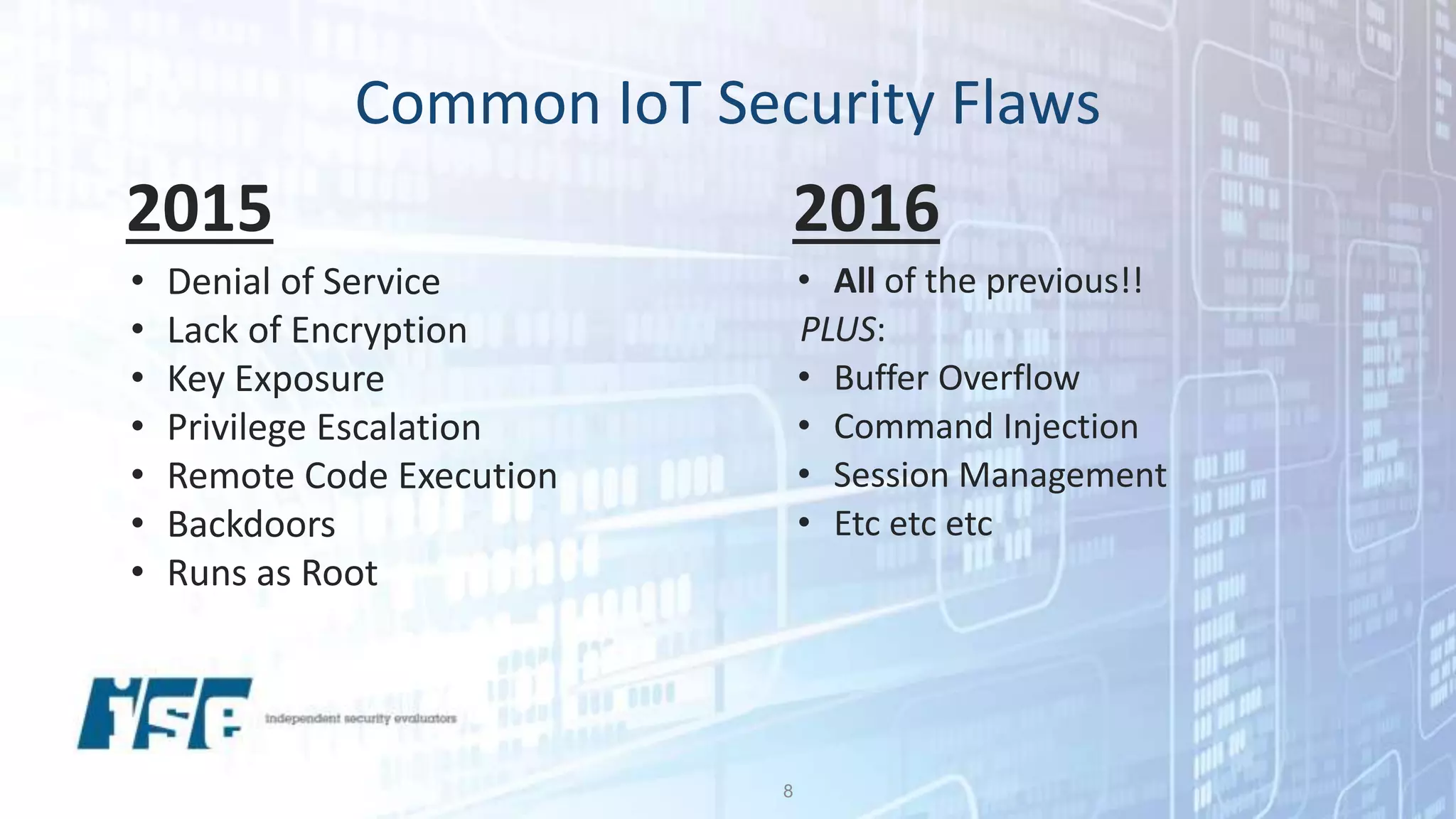
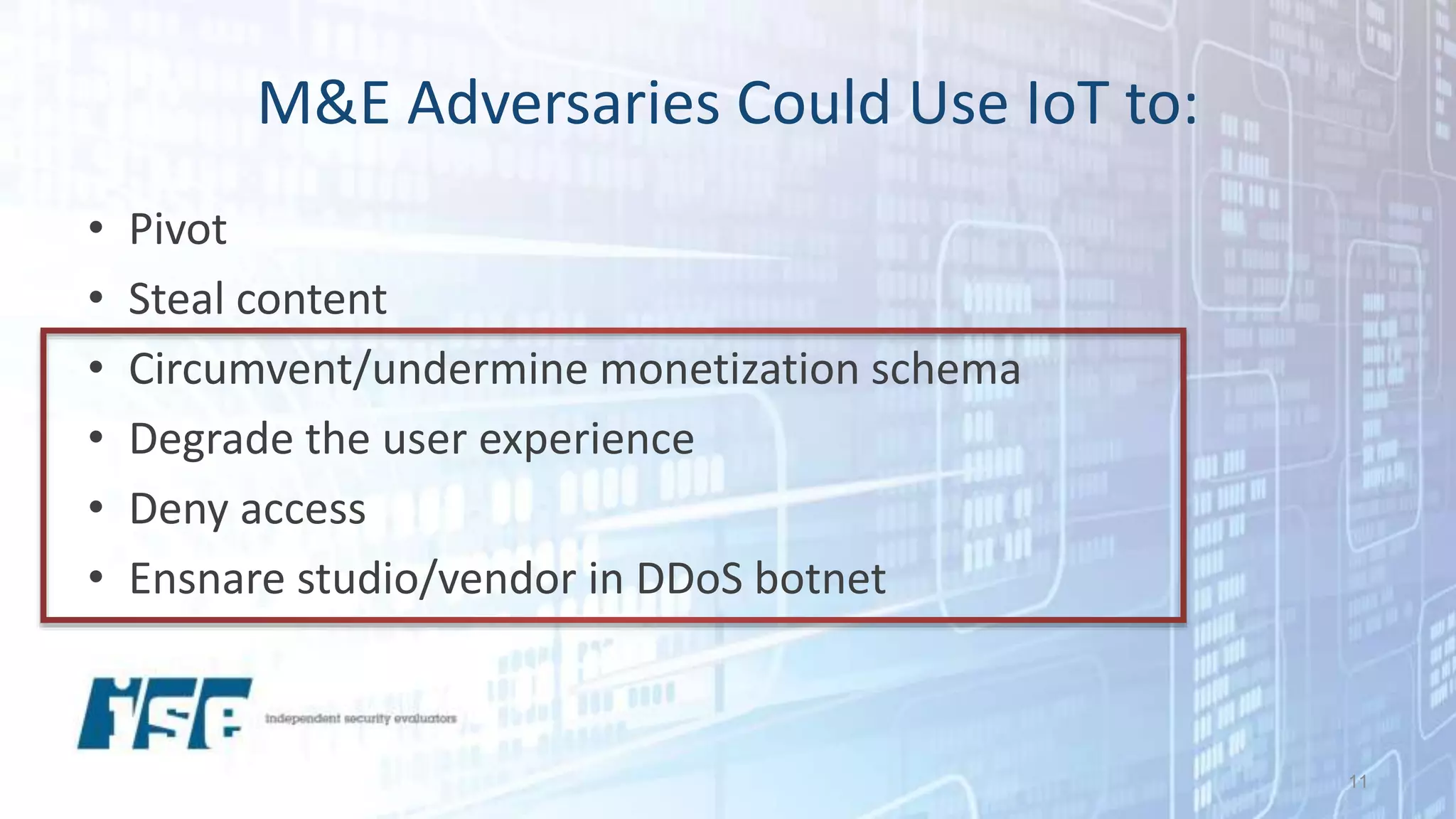
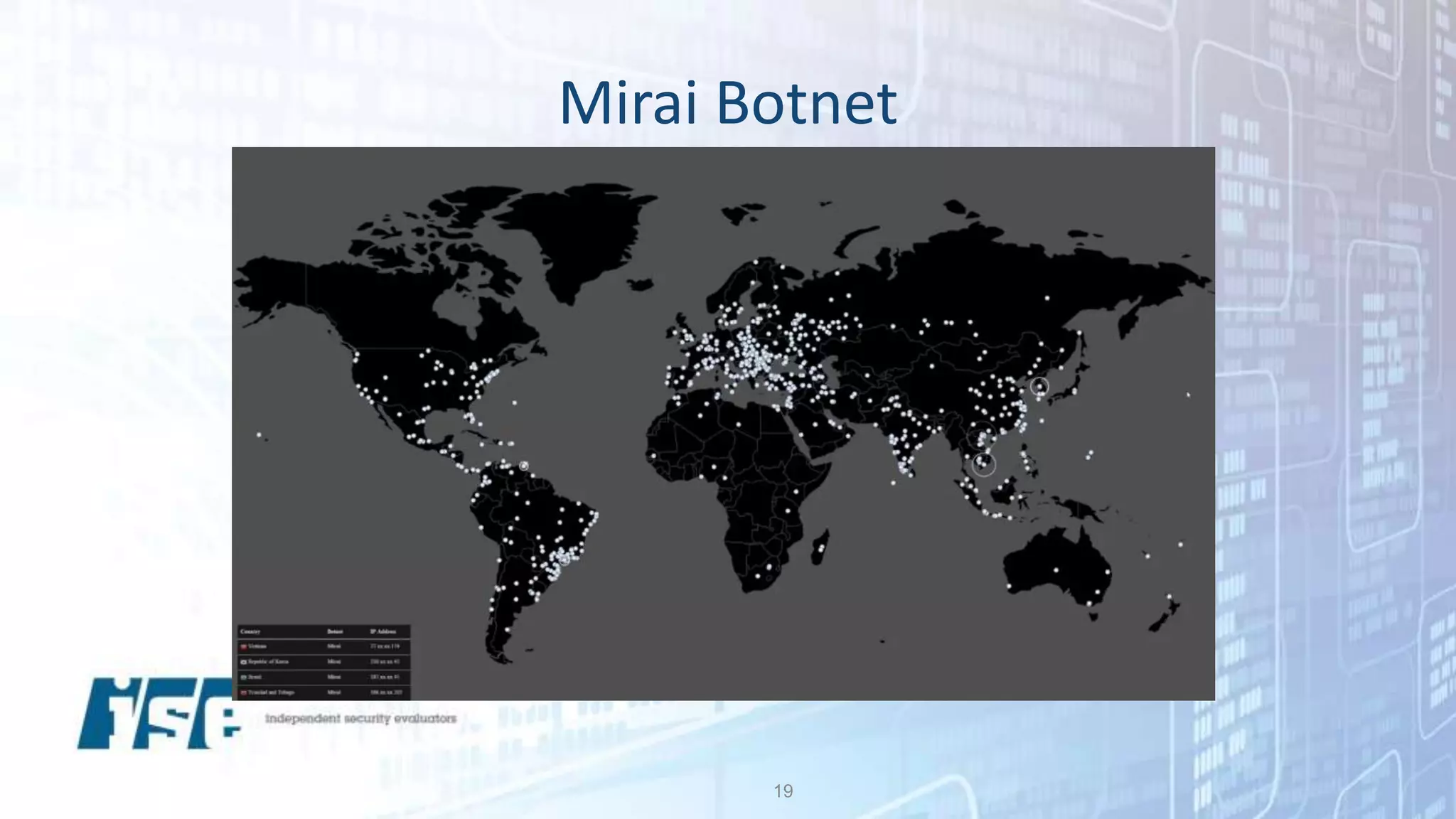
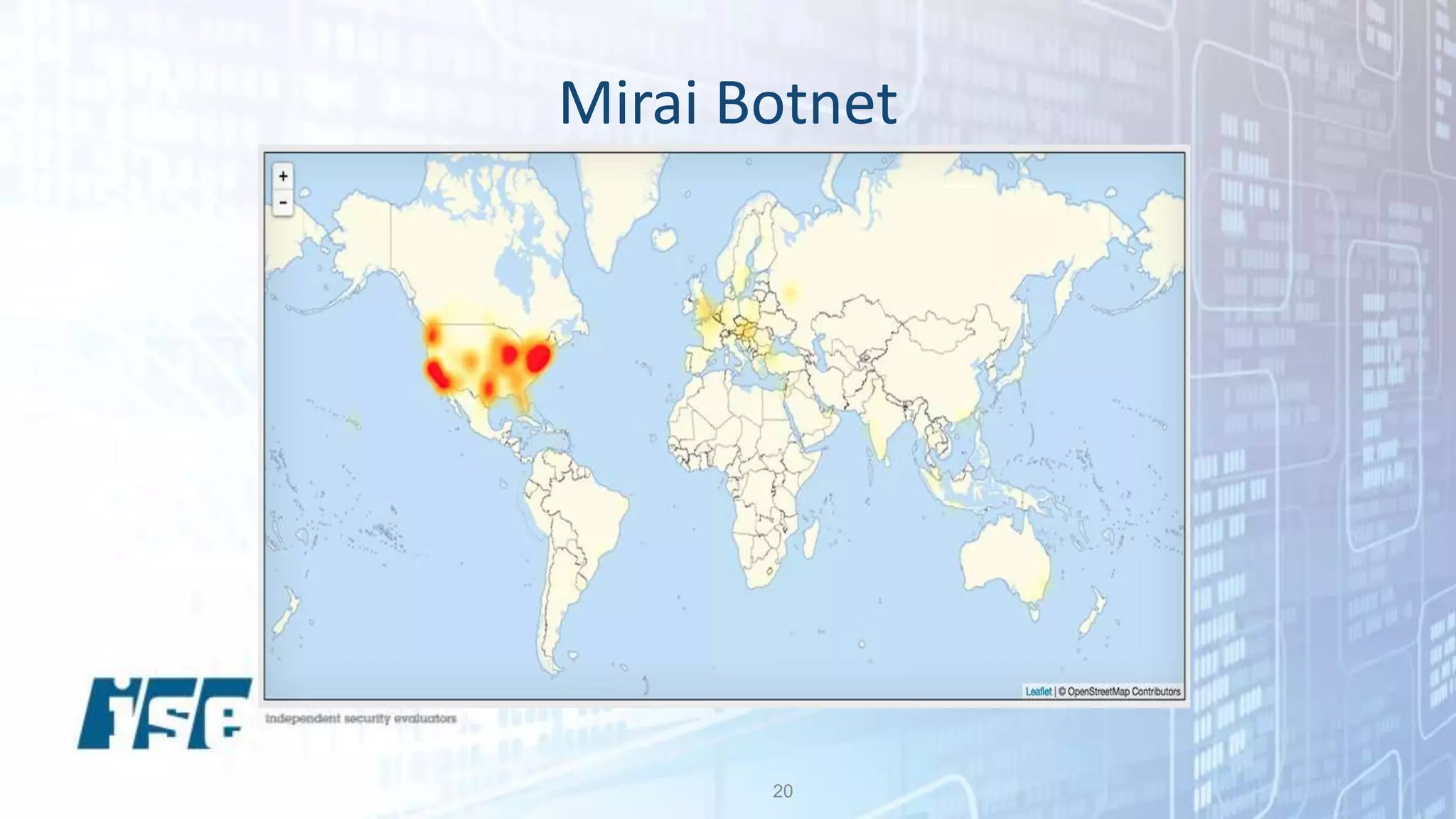
The document discusses security vulnerabilities in IoT devices, highlighting significant common flaws identified from IoT Village, including denial of service and remote code execution. It emphasizes the threat posed by the Mirai botnet and outlines recommendations for both manufacturers and users to mitigate these risks, such as threat modeling and reducing attack surfaces. The author, Ted Harrington, suggests leveraging security assessments to improve protection against these threats.