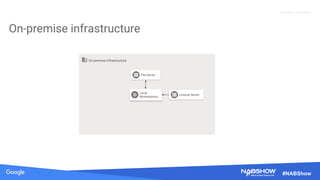
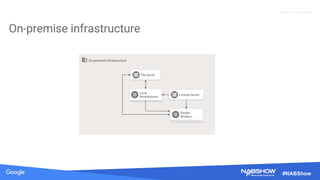
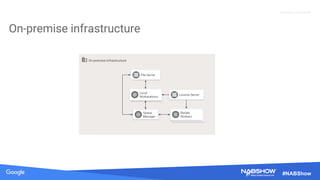
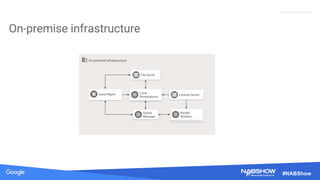
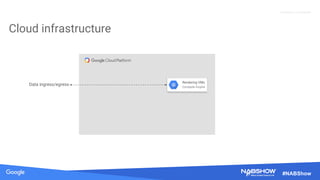
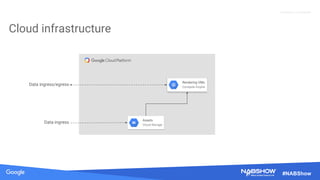
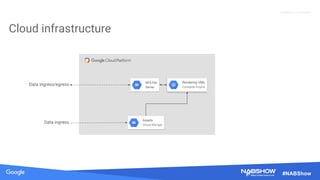
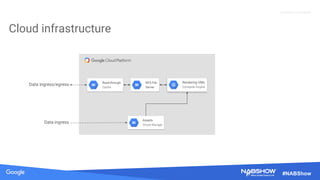
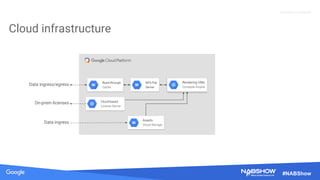
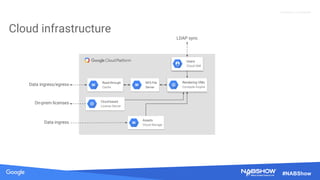
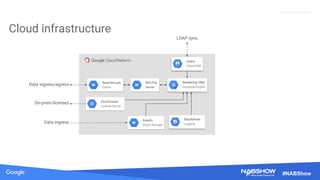
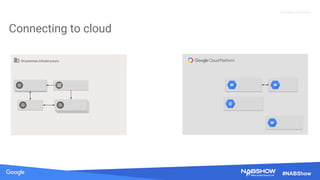
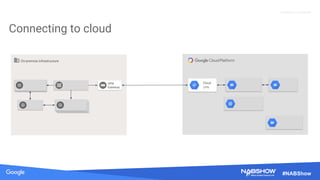
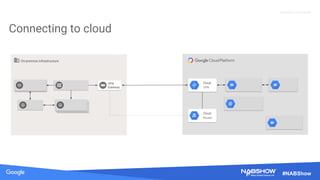
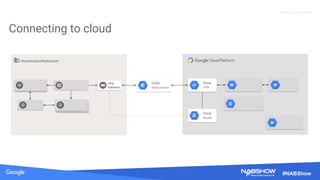
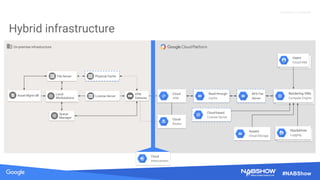
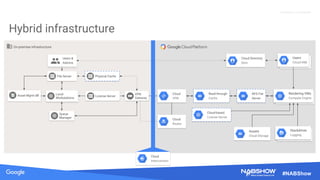
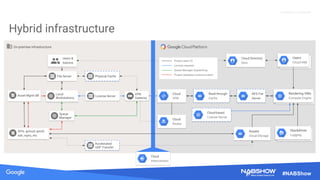
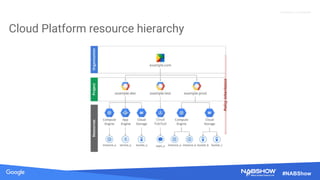
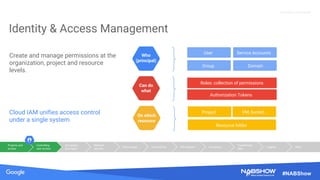
The document provides an overview of securing content in cloud infrastructures, comparing on-premises and cloud setups. It emphasizes the importance of security measures such as identity and access management, encryption, and network security, as well as strategies for connecting hybrid infrastructures. Best practices for enterprise organizations, including securing connections and data transfer methods, are also discussed.