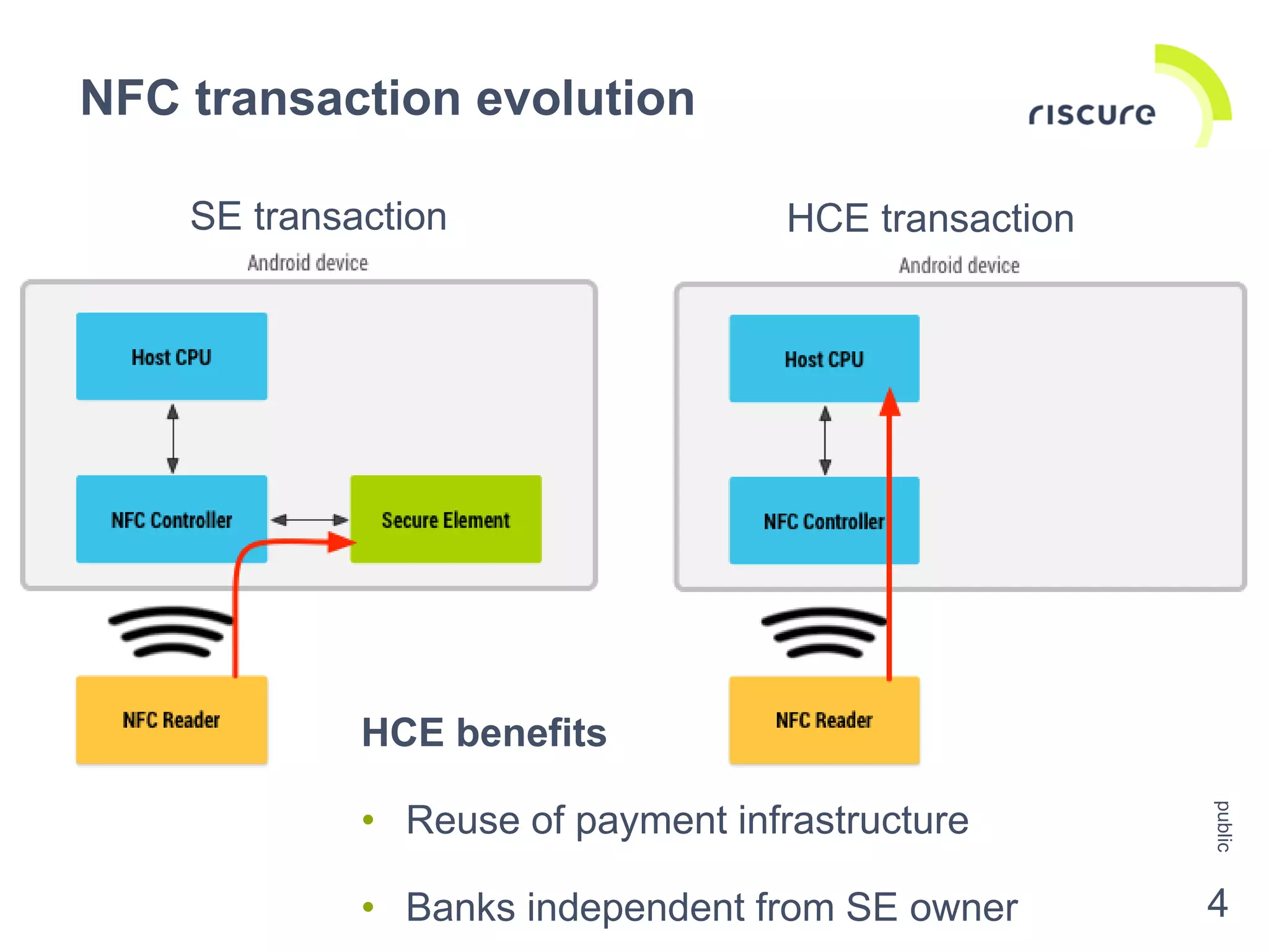
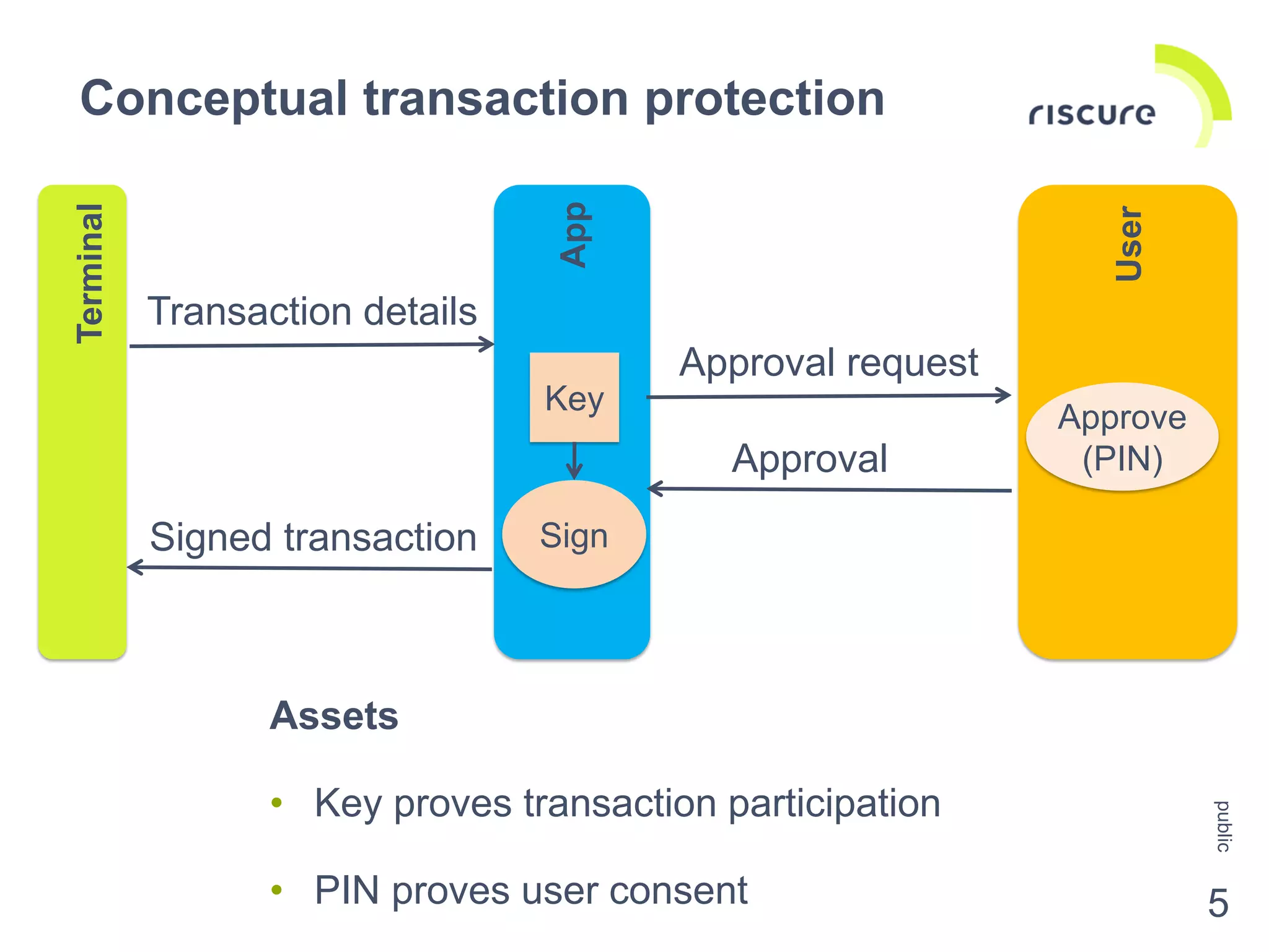
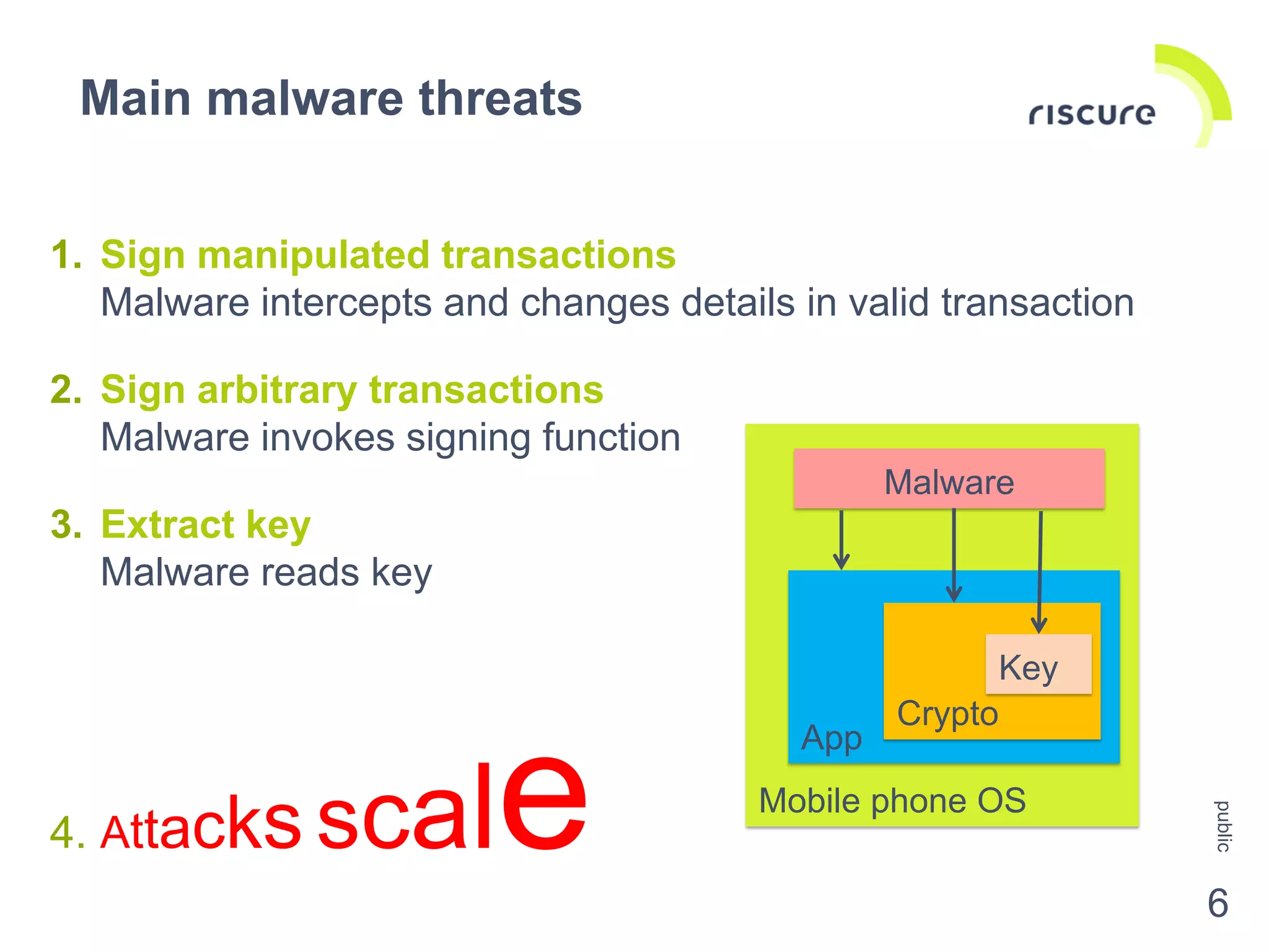
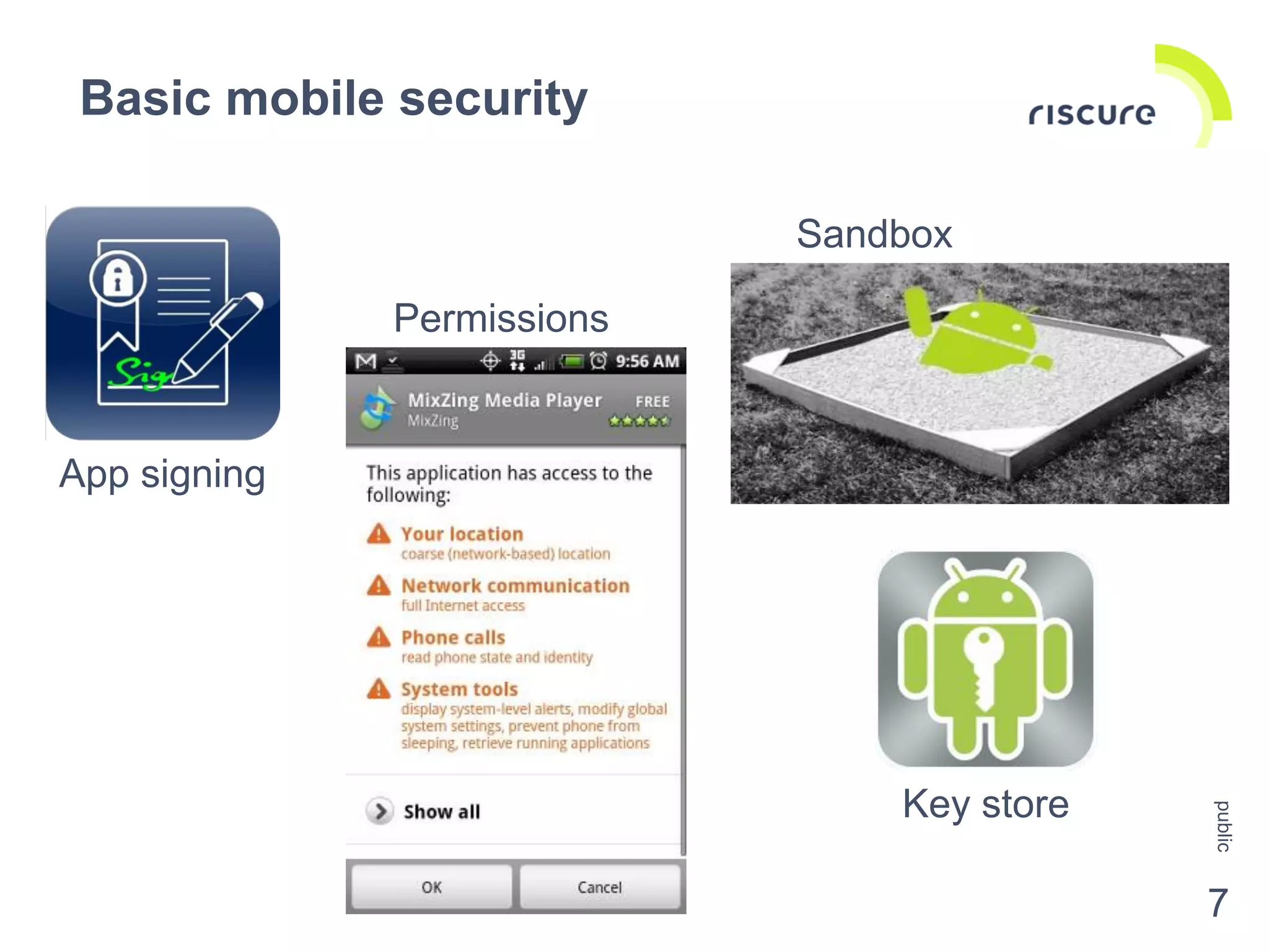
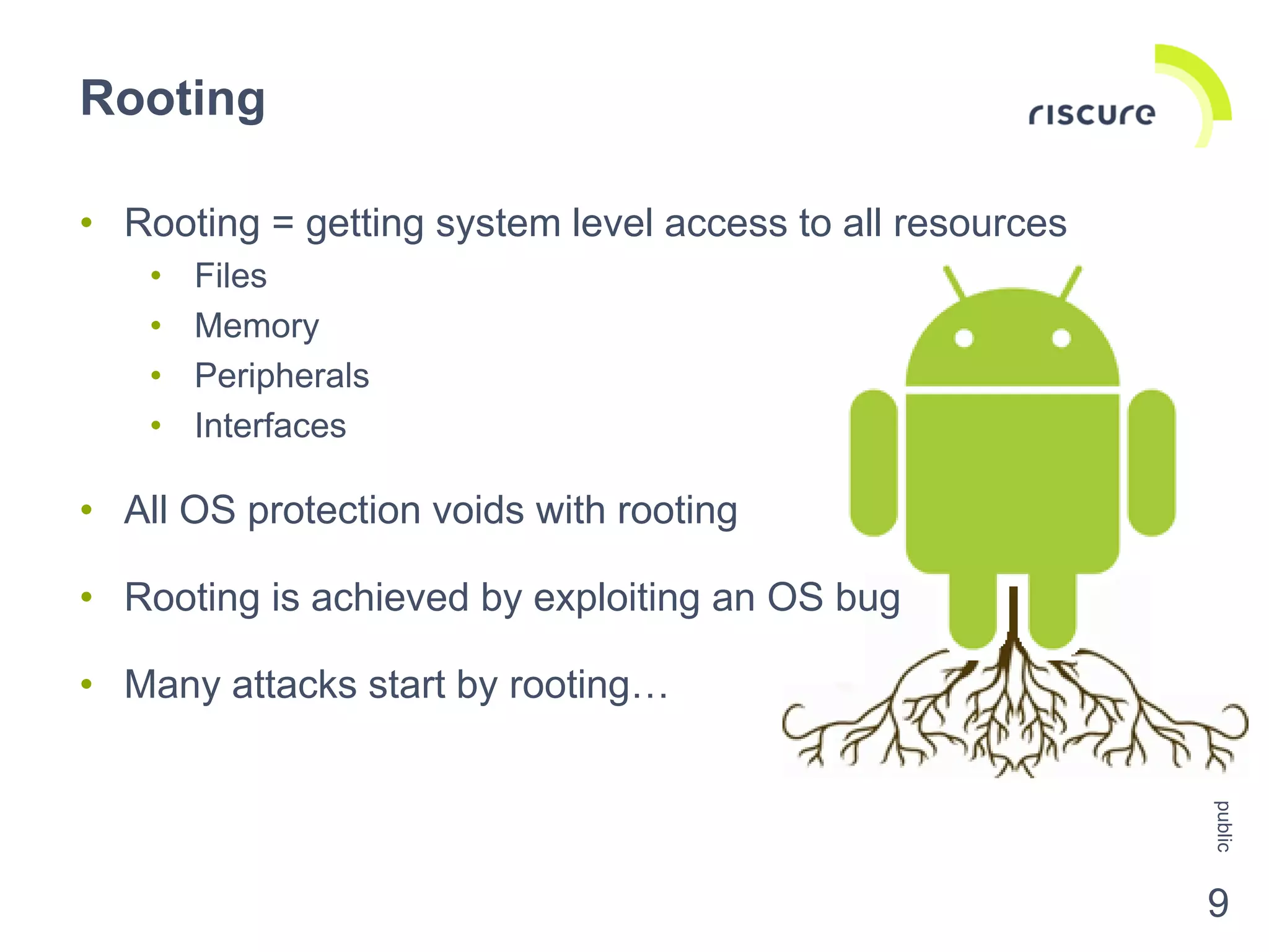
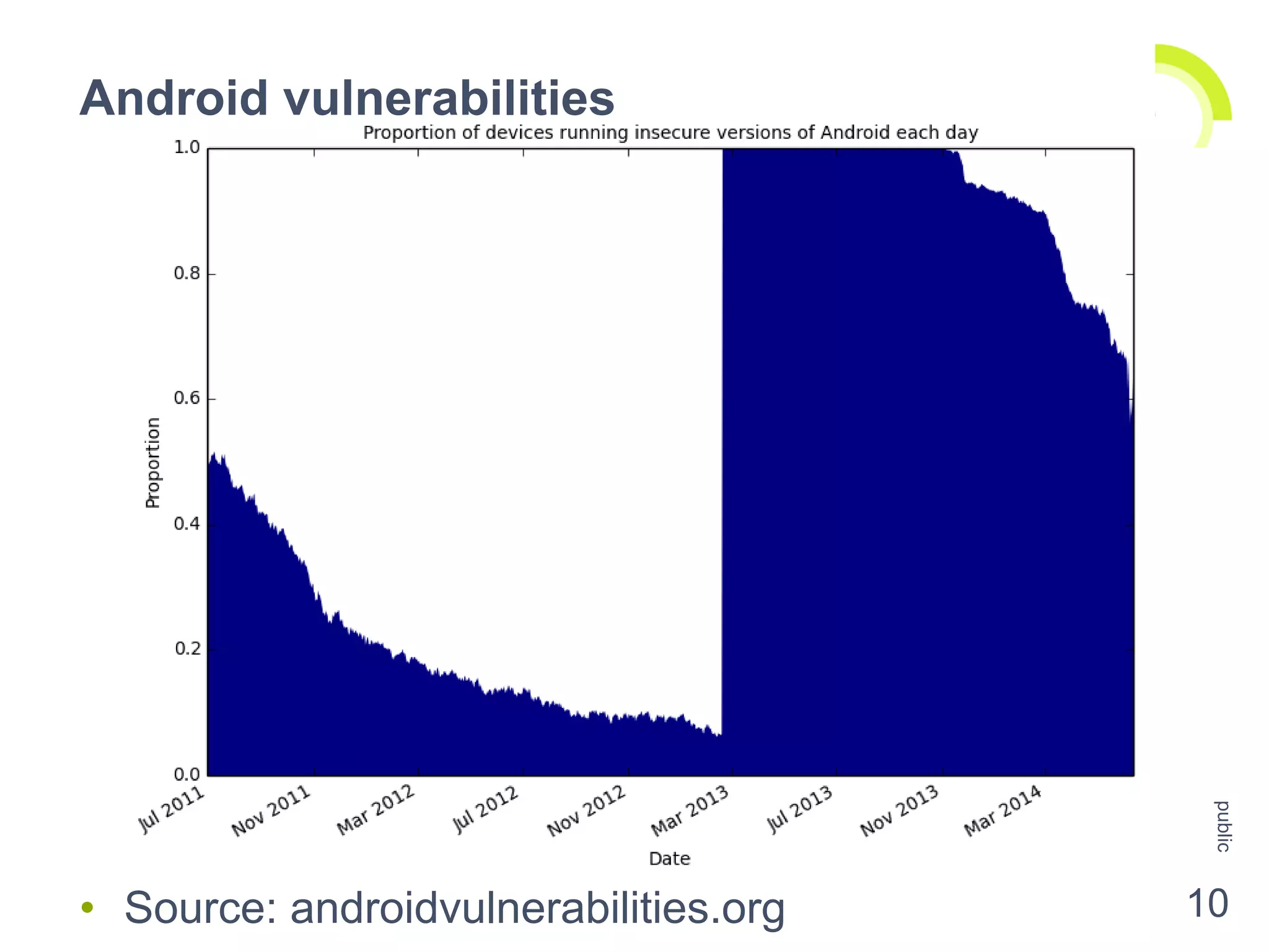
The document discusses the security challenges and risks associated with Host Card Emulation (HCE) in mobile payment applications, emphasizing the need for security measures that surpass traditional mag-stripe technology. It highlights the evolution of transaction security, various types of malware threats, and the importance of rigorous evaluation and mitigation strategies. Riscure offers security certification services to help identify and address vulnerabilities in mobile applications.