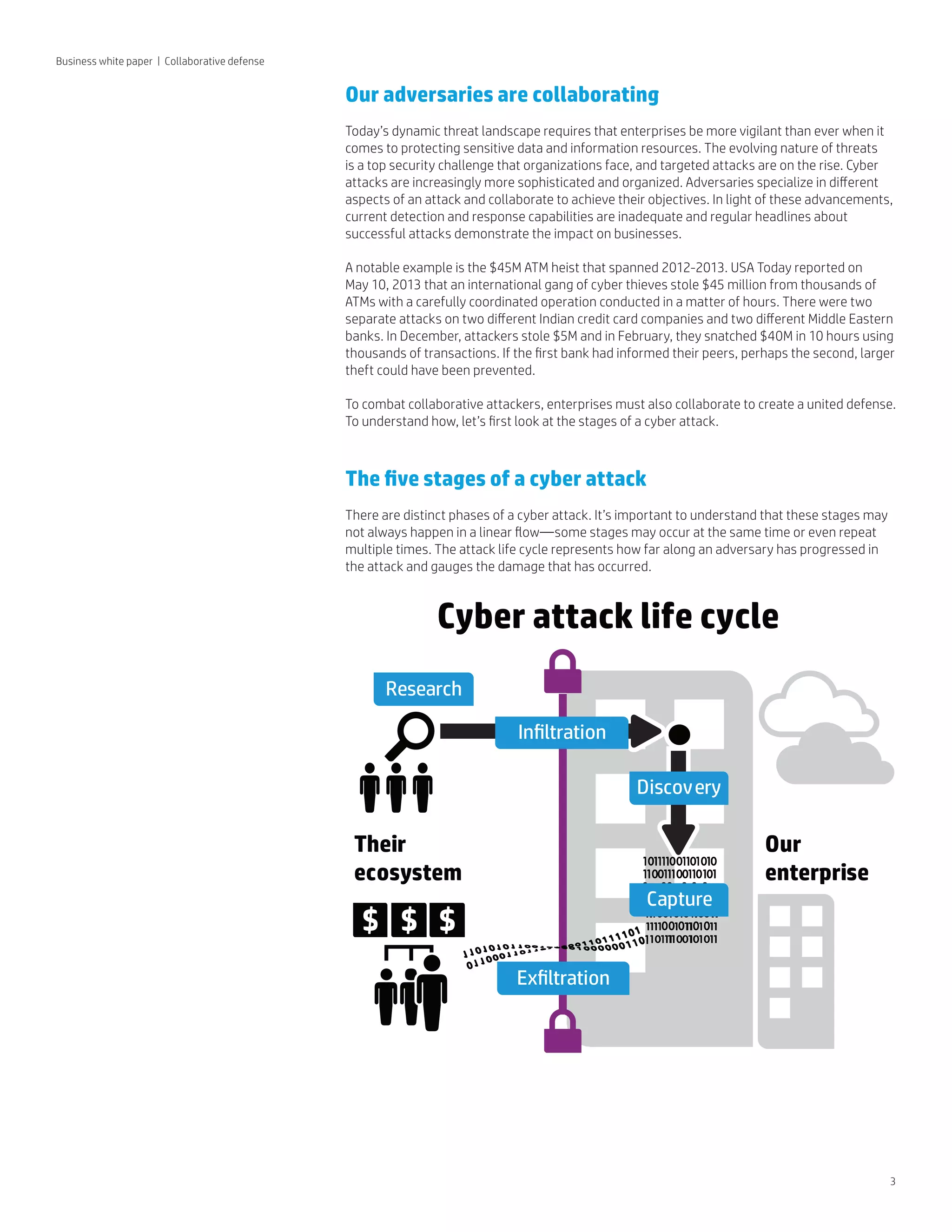
This document discusses the need for collaboration in cyber defense against increasingly sophisticated and organized cyber attacks. It notes that adversaries now specialize and collaborate in different attack phases. The five phases of a cyber attack are outlined as research, infiltration, discovery, capture, and exfiltration. It argues that to effectively counter collaborative adversaries, enterprises must also collaborate by sharing security intelligence in a timely, secure, and confidential manner. Examples of information sharing organizations and challenges to collaboration are provided. It concludes that no practical technology currently enables automated, bi-directional security data sharing at scale.