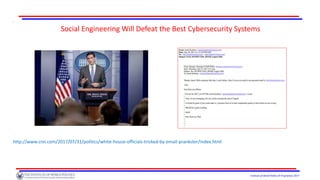
The document discusses the challenges facing the cyber insurance market, noting its immaturity and the inadequacy of coverage provided to organizations, which may lead to financial crises. Although a robust cyber insurance market could promote preventative measures against cyber threats, many organizations remain under-insured and face high risks from potential cyber attacks. The document also highlights the systemic risks associated with cyber events and the role of governmental intervention in the industry's future.





![Institute of World Politics © Proprietary 2017
Are Cybersecurity Efforts Ultimately Futile?
Exhibit 1: Not Necessarily: Consider the [Not]Petya Wiper Attack:
“
“Cyberattack Hits Ukraine Then Spreads Internationally,” New York Times, June 27, 2017.](https://image.slidesharecdn.com/ci2cyberinsurancepresentation-180519014602/85/Ci2-cyber-insurance-presentation-9-320.jpg)
![Institute of World Politics © Proprietary 2017
The Recent Wanna Cry & [Not]Petya Cyber-Attacks
These viruses were propagated without human intervention, but they are not regarded as
very sophisticated. Estimated to have caused harm in the low billions of dollars, almost all
of which will not be covered by insurance.
Whereas Wanna Cry ransomware was designed for financial gain, NotPetya seems to have
been politically driven (attributed by UK and US to Russia( – seeking to maximize harm.
Initial attacks against Ukrainian state bodies, it spread to DLA Piper (a U.S. firm), FedEx
(U.S. delivery service company), MAERSK (Danish-based shipping company), Merck (U.S,
pharmaceutical company), Rosneft (Russian oil company), and many others.
Good cyber-hygiene practices could have prevented infection. Only a minority of the
victims carried stand-alone cyber insurance. But the common exclusions for failing to
install patches, nation-state attackers, or otherwise failing to follow good cybersecurity
practices are likely to prevent recoveries from insurers.](https://image.slidesharecdn.com/ci2cyberinsurancepresentation-180519014602/85/Ci2-cyber-insurance-presentation-10-320.jpg)