The document discusses genetic algorithms (GAs), which are search techniques that utilize principles of natural selection for problem-solving in various domains. It outlines the foundational concepts of GAs, including their structure, operators (selection, crossover, mutation), and advantages over traditional optimization methods. Additionally, it briefly covers the history of GAs and provides an overview of reactive routing protocols, specifically the AODV and DSR protocols used in ad-hoc networks.
![For More Info Https://www.ThesisScientist.com
CHAPTER 3
BACKGROUND
3.1 GENETIC ALGORITHM
GA is a search technique that depends on the natural selection and genetics principles and
which determines a optimal solution for even a hard issue.
Genetic algorithms are normally a family of computational models which are
motivated by the biological evolution. These algorithms encode a powerful
solution to a particular problem on a simple chromosome i.e. data structure and use
genetic operators to these structures so as to preserve severe information.
Genetic algorithms are usually viewed as a function optimizer.
Genetic algorithms can be used to a broad range of problems.
For solving the issue by genetic algorithm the first step is to generate the
chromosomes population (random). Then these chromosomes are estimated in
such a manner that the chromosome which shows a better solution for the problem
will be provided more opportunities than the poorer solution.
The genetic algorithms are part of the evolutionary algorithms family, which are
computational models, motivated in the Nature.
GAs are more reliable as compared to other most search techniques because they need
only information related to the quality of the solution created by every parameter set
(objective function values) and not like other optimization techniques which needs
derivative information, or worse yet, entire knowledge of the parameters and problem
structure[9].There are some difference between GA’s and other optimization/conventional
searching algorithms [14] . They are briefly explained as follows
1) GAs work with a coding of the parameter set, not the parameters themselves. Thus GAs
can easily manage the discrete or integer variables.
2) GAs search within a points population, not a single point. Thus GAs can offer a
globally optimal solution.](https://image.slidesharecdn.com/chapter3thesisscientist-170507034241/75/Genetic-algorithm-fitness-function-1-2048.jpg)
![For More Info Https://www.ThesisScientist.com
3) GAs employ only objective function information, not derivatives or other auxiliary
knowledge. Thus GAs can manage the non-continuous, non-smooth and non-
differentiable functions which are actually available in a practical optimization issue. 4)
GAs employ probabilistic transition rules, not deterministic rules, Although GAs appear to
be a good mechanism to solve optimization issue, sometimes the solution achieved from
GAs is only a near global optimal solution.
3.2 BASIC FEATURES OF GA
GA is a sub division of artificial intelligence.
AI (Artificial intelligence) is a computer science branch by which researchers
implement an intelligent computer system that has intelligence same as human
being.
GA comes in the category of search algorithms that are based on computer and are
random in nature. These algorithms are obtained from the natural theory of
“survival of the fittest” being specified by Darwin.
The mechanization of intelligent nature is a pre concern of this branch.
GA is also appropriate for complicated problems.
It generates the best of the best solutions.
The aim of GA is to increase the candidate solutions payoff in the population against an
objective function from problem domain. The scheme for the GA is to repeatedly use
surrogates for the mutation and recombination genetic processes on the population of
candidate solutions, where the objective function used to a decoded representation of a
candidate governs the probabilistic contributions a provided candidate solution can build
the subsequent generation of candidate solutions.
3.3 HISTORY OF GENETIC ALGORITHM
John Holland is assumed as the father of Genetic Algorithm. He discovered it in the early
1970's.and after that he and his students contribute much to the growth of this field.
Holland research was not concentrated on domain and optimization specific practical
problem but was on the adaptation concept as viewed in nature [6] and [7]. Other](https://image.slidesharecdn.com/chapter3thesisscientist-170507034241/85/Genetic-algorithm-fitness-function-2-320.jpg)
![For More Info Https://www.ThesisScientist.com
significant contributions were performed by Frantz in 1972 who inquired what were
known as Genetic Algorithm for Search and in 1971 Holstein inquired genetic plans for
adaptive control and function optimization. Several people involved biologists, are
amazed that life at the level of complexity that we realize could have emerged in the
relatively short time proposed by the fossil record [20].
Several human inventions were motivated by the natural selection. Genetic algorithm is
one of them. The main concept of this is the fittest survival or in other words it is called
natural selection. As evidently in nature the individual that has better chances for survival
will survive for a larger period of time. This in turn offers a better chance to create
offspring with its genetic material. In other words They can say that the fittest candidate
will survive and unfit will not. This force of nature is as known natural selection and on
this principle GA operates for solving optimization problems.
3.4BASICTERMINOLOGYofGA
Before beginning a discussion on Genetic Algorithms, it is essential to be familiar with
some basic terminology which will be used throughout this tutorial.
Population − It is a subset of all the possible (encoded) solutions to the given
problem. The population for a GA is analogous to the population for human
beings except that instead of human beings, we have Candidate Solutions
representing human beings.
Chromosomes − A chromosome is one such solution to the given problem.
Gene − A gene is one element position of a chromosome.
Allele − It is the value a gene takes for a particular chromosome.
Genotype − Genotype is the population in the computation space. In the
computation space, the solutions are represented in a way which can be easily
understood and manipulated using a computing system.
Phenotype − Phenotype is the population in the actual real world solution space in
which solutions are represented in a way they are represented in real world
situations.
Decoding and Encoding − For simple problems, the phenotype and
genotype spaces are the same. However, in most of the cases, the phenotype and
genotype spaces are different. Decoding is a process of transforming a solution](https://image.slidesharecdn.com/chapter3thesisscientist-170507034241/85/Genetic-algorithm-fitness-function-3-320.jpg)
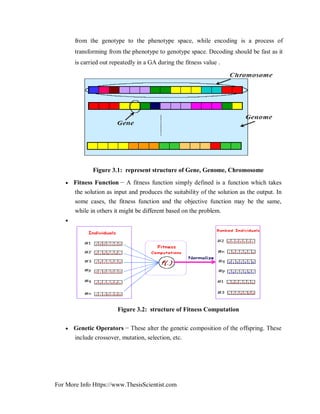
![For More Info Https://www.ThesisScientist.com
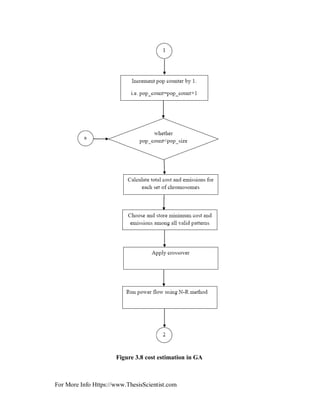
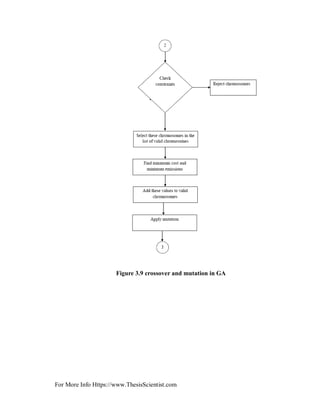
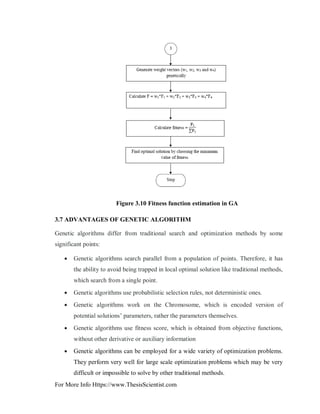
3.5 OPERATORS OF GA
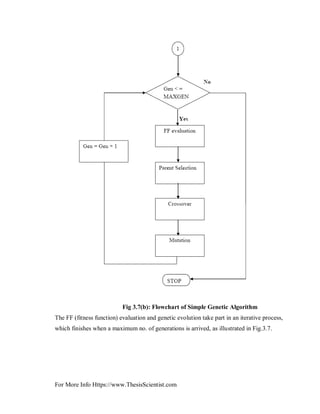
GA begins with random creation of initial population and then the selection, crossover and
mutation operations are conducted until best population is determined. Gas are practical
and simple algorithm and easy to be implemented in power system.
In other words, considering an initial random population generated and measured, genetic
evolution happens by means of three basic genetic operators [22].
1) Parent selection.
2) Crossover.
3) Mutation.
The descriptions of these genetic operators are provided below [23]:
1. Parent Selection/Selection Strategy:
The selection of parents to generate successive generations plays a significant role in the
GA. This permits the fitter individuals to be chosen more usually to reproduce. There is a
no. of selection techniques introduced in the literature [24].
In this technique, n individuals are copied from the population randomly and the best of
the n is introduced into population for further genetic processing. This process is repeated
until the mating pool is filled.
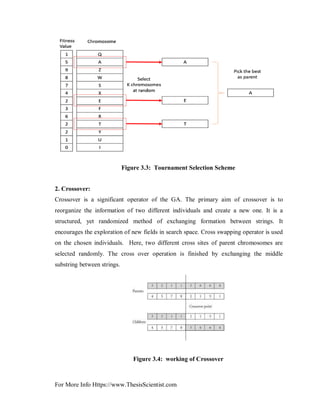
TournamentSelection
In K-Way tournament selection, It select K individuals from the population at random
and select the best out of these to become a parent. The same process is repeated for
selecting the next parent. Tournament Selection is also extremely popular in literature as
it can even work with negative fitness values.](https://image.slidesharecdn.com/chapter3thesisscientist-170507034241/85/Genetic-algorithm-fitness-function-5-320.jpg)


![For More Info Https://www.ThesisScientist.com
3.8 VANET Routing Protocols
Routing is a mechanism to establish and to select a specific path in order to send data from
source to destination [14, 16]. There are various routing algorithm designed for ad-hoc
networks. Classification of various VANET routing protocols can be divided in two broad
categories: proactive or Table Driven Routing Protocols (DSDV, OLSR, FSR) and
reactive or On-demand routing protocols (AODV, DSR, TORA) that shown in figure 3.11.
In the next section describes a detail overview of various reactive routing protocols
(AODV, DSR).
Figure 3.11 VANET Routing Protocols
3.9 Reactive/On Demand Routing Protocols
Reactive routing protocols were designed to reduce the overheads by maintaining
information for active routes at each node [8]. This means that each node determined and
maintained routes only when it requires sending data to a particular destination. It using
two main mechanisms for route establishment: Route discovery and Route maintenance
[17, 25]. Route discovery mechanism uses two messages: Route Request (RREQ) and
Route Reply (RREP).](https://image.slidesharecdn.com/chapter3thesisscientist-170507034241/85/Genetic-algorithm-fitness-function-13-320.jpg)
![For More Info Https://www.ThesisScientist.com
Figure 3.12: Route Request Propagation in Reactive Routing Protocols
The basic approach is when a node needs to send a message to a particular destination, it
broadcasts the RREQ message in the network that shown in figure 3.12 When RREQ
message found a destination node then destination node send a RREP message to source
node that shown in figure 3.13.
Figure 3.13: Route Reply Propagation in Reactive Routing Protocols
Ad hoc On Demand Distance Vector (AODV): Ad hoc On Demand Distance Vector
(AODV) is a pure reactive routing protocol which is capable of both unicasting and
multicasting. In Ad hoc On Demand Distance Vector (AODV), like all reactive protocols,
it works on demand basis when it is required by the nodes within the network [8, 14].
When source node has to send some data to destination node then initially it propagates
Route Request (RREQ) message which is forwarded by intermediate nodes until](https://image.slidesharecdn.com/chapter3thesisscientist-170507034241/85/Genetic-algorithm-fitness-function-14-320.jpg)
![For More Info Https://www.ThesisScientist.com
destination is reached. A route reply message is unicasted back to the source node if the
receiver is either the node using the requested address, or it has a valid route to the
requested address that is shown is figure 3.14.
(a) (b)
Figure 3.14: AODV Route Discovery Process. (a) Propagation of the RREQ.
(b) Path of the RREP to the source.
Working of Ad Hoc On Demand Distance Vector Routing (AODV): In this type of routing
[14, 16] allows the communication between two nodes via intermediated nodes, if those
two nodes are not within the range of each other. To establish a route between source to
the destination, AODV using route discovery phase, along which Route Request message
(RREQ) messages are broadcasted to all its neighbouring nodes. This phase makes sure
that these routes do not forms any loops and find only the shortest possible route to the
destination node. It also uses destination sequence number for each route entry, which
ensures the loop free route, this is the one of the main benefit of AODV routing protocol.
For example if two different sources send two different requests to a same destination
node, then a requesting node selects the one with greatest sequence number. In the route
discovery phase several control messages are defined in AODV that are defined as
follows.
a) RREQ (Route Request): When any node wants to communicate with other node
then it broadcast route request message (RREQ) to its neighbouring nodes [14, 16].
This message is forwarded by all intermediate nodes until destination is reached.](https://image.slidesharecdn.com/chapter3thesisscientist-170507034241/85/Genetic-algorithm-fitness-function-15-320.jpg)
![For More Info Https://www.ThesisScientist.com
The route request messages (RREQ) contains the some information such as RREQ
id or broadcast id, source and destination IP address, source and destination
sequence number and a counter.
b) RREP (Route Reply): When any intermediate nodes received Route Request
(RREQ) message then it unicast the route reply message (RREP) to source node
either it is valid destination or it has path to destination and reverse path is
constructed between source and destination [14, 16]. Each route reply message
(RREP) packet consist of some information such as hop count, destination
sequence number, source and destination IP address.
c) RERR (Route Error): Whenever there is any link failure arises in the routing
process then route error message (RERR) is used for link failure notifications. The
route error message (RERR) consist of some information such as Unreachable
Destination node IP Address, Unreachable Destination node Sequence Number.
Routing in AODV: There are various mechanisms which are followed in AODV routing
approach:
a) AODV Route Discovery phase: To establish a route between source node to the
destination node, AODV using route discovery phase, along which the Route
Request message (RREQ) messages are broadcasted to all its neighbouring nodes
[14]. This phase makes sure that these routes do not forms any loops and find only
the shortest possible path to the destination node. It also uses destination sequence
number for each route entry that ensures the loop free route, this is the one of the
main benefit of AODV routing protocol. For example if two different sources
sends two different request to a same destination node, then a destination node
selects only that node having largest sequence number. In the route discovery
phase several control messages are defined in AODV protocol.
b) AODV Route Table Management: In AODV, Routing table management is
required to avoid those entities of nodes that do not exist or having invalid route
from source to destination. The need for routing table management is important to](https://image.slidesharecdn.com/chapter3thesisscientist-170507034241/85/Genetic-algorithm-fitness-function-16-320.jpg)
![For More Info Https://www.ThesisScientist.com
make communication loop free. It consists of following characteristics to maintain
the route table for each node.
• Destination IP address
• Total number of hops to the destination
• Destination sequence numbers
• Number of active neighbours
• Route expiration time
c) AODV Route Maintenance: In AODV, when any node in the network detects that a
route is not valid anymore for communication it delete all the related entries from
the routing table .And it sends the Route reply message (RREP) to all current
active neighbouring nodes to inform that the route is not valid anymore for
communication purpose.
Dynamic Source Routing Protocol (DSR)
Dynamic Source Routing is a reactive routing protocol that is based on the concept of
source routing [8, 16]. Source routing means source has the complete knowledge of entire
route to the destination before transmitting data. In DSR each node maintains a route
cache where it records all possible learned routes. It using two main mechanisms: Route
discovery and Route maintenance.
Route Discovery: Whenever a source node wants to send a data packet to destination node
in the network, it first looks in its Route Cache to find a valid hop sequence to the
destination [1].](https://image.slidesharecdn.com/chapter3thesisscientist-170507034241/85/Genetic-algorithm-fitness-function-17-320.jpg)
![For More Info Https://www.ThesisScientist.com
Figure 3.15: Route Request Propagation in DSR
If such a route exists, the source node attaches to the packet header the complete route to
the destination and forwards the packet to the next node. The next node checks the packet
header and forwards the packet to the next node. The process terminates when the packet
reaches the destination. If the source node cannot find a valid hop sequence to the
destination in its Route Cache then it initiates a route discovery process [17].
In route discovery process a route request (RREQ) message is broadcasts to all its
neighbouring nodes, adding a unique request ID to each request to prevent
Figure 3.16: Route Reply Propagation in DSR](https://image.slidesharecdn.com/chapter3thesisscientist-170507034241/85/Genetic-algorithm-fitness-function-18-320.jpg)
![For More Info Https://www.ThesisScientist.com
Figure 3.15 shows the RREQ message propagation in the network. And figure 3.16
shows the propagation of RREP message that carries the entire hop sequence.
a) Route Maintenance: Route Maintenance is done by the propagation of route error
message (RERR). Whenever any active node sees or detects the link failure, it
propagates the route error message to its upstream neighbours along the reverse
path till it reaches the source node. To verify the correct operation of the router
links, HELLO messages and acknowledgement messages can be used.
3.10 Classification of the VANET Applications:
The applications of Vehicular Ad hoc Networks (VANET) are classified into three major
groups: 1)comfort oriented applications 2) convenience-oriented applications and 3)safety
oriented applications [11]. Safety oriented related applications look for the increasing
security of passengers by exchanging relevant information through vehicle-to-
infrastructure and vehicle-to-vehicle. And comfort and convenience applications improve
passenger’s comfort and traffic efficiency.
3.10.1 Safety-Oriented Applications: These types of applications help the driver to avoid
potential dangers through the exchange of information among vehicles. They are the
important applications because they serve to avoid accidents [11].
Figure 3.17: Safety Applications provided by VANET](https://image.slidesharecdn.com/chapter3thesisscientist-170507034241/85/Genetic-algorithm-fitness-function-19-320.jpg)
![For More Info Https://www.ThesisScientist.com
They can take control of the vehicle in case of hazardous conditions, as in the case of the
automatic braking and only send warning/emergency messages to drivers. Some safety
oriented application shown in Table 3.1[11].
Table 3.1: Examples of Safety-Oriented Applications
Name Description
Intersection violation warning Intersection violation warns drivers when they are
going to pass over a traffic red light .
On-coming traffic warning It assists the driver during over taking manoeuvres
Electronic brake warning It alerts to the driver that a preceding vehicle has
performed a emergent braking.
Vehicle stability warning It reports drivers that they should activate the vehicle
stability control system.
Post-crash notification A vehicle involved in an accident sends warning
/emergency messages in broadcast to approaching
vehicles.
Traffic signal violation warning A roadside unit (RSU) sends messages in broadcast to
warn drivers of potential violations of traffic signals.
Lane change warning It assists drivers to perform a safe lane change
3.10.2 Convenience-Oriented Applications: These types of applications improve the
efficiency of the roads and to save drivers time . Various Convenience oriented
application shown in Table 3.2[11]. Some examples of Convenience Oriented
Applications in VANET as shown in table 3.2.
Table 3.2: Examples of Convenience-Oriented Applications
Name Description
Intersection management Vehicle to vehicle and Vehicle to RSU
communications allow a better intersections
management](https://image.slidesharecdn.com/chapter3thesisscientist-170507034241/85/Genetic-algorithm-fitness-function-20-320.jpg)
![For More Info Https://www.ThesisScientist.com
Limited access and detour warning A roadside unit (RSU) sends information in
broadcast about limited access network areas or
detours.
Electronic toll collection A vehicle founds unicast communication with a
toll gate road side unit( RSU) and pays the toll
without stopping vehicle.
Parking availability notification A vehicle asks to a roadside unit (RSU) for a list of
available parking areas or parking spaces, and the
roadside unit (RSU) sends the list to the vehicle.
Congested road notification A vehicle in a congested road forwards
information to other vehicles.
Figure 3.18: Convenience Oriented Application Provided by VANET
3.10.3 Commercial-Oriented Applications: These types of applications serve to make
the travelling more comfortable for example, by means of the internet connection. Few
Commercial oriented application shown in Table 3.3[11].
Table 3.3: Examples of Commercial-Oriented Applications](https://image.slidesharecdn.com/chapter3thesisscientist-170507034241/85/Genetic-algorithm-fitness-function-21-320.jpg)