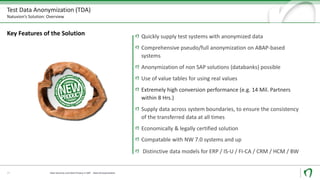
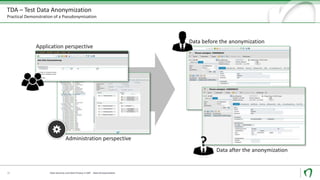
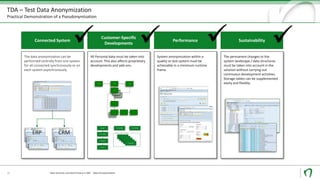
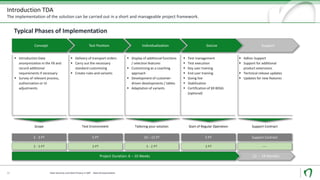
The document discusses challenges and solutions for anonymizing personal data in SAP systems to comply with the GDPR. It describes fields of action for anonymizing data in test, training, and production systems. The document also provides an overview of Natuvion's Test Data Anonymization solution for pseudonymizing data across connected SAP systems in a centralized and rule-based manner.










![Personal data may not be used for a test execution of IT software.
Data Security und Data Privacy in SAP - Data Anonymization
Comprehensive real data in project, test and training systems
"[..] Software and IT procedures are to be checked
with systematically developed case constellations
(test data, no personal data) according to a test plan,
from which the desired result emerges.
Mass tests can, if necessary, be carried out with
anonymized original data after approval and
specifications of the competent authority.
The approval of the responsible authority for the
anonymization of original data and all test results
must be documented in a revision-proof manner.
Source: https://www.bsi.bund.de/DE/Themen/ITGrundschutz/ITGrundschutzKataloge/
Inhalt/_content/m/m02/m02509.html
IT Baseline Protection Catalogs
13. EL on 2013, M 2.509):
13
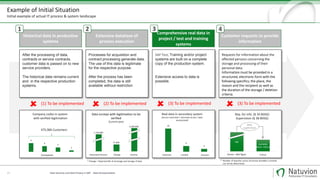
In SAP test- or project systems, no personal data may be held. All
test procedures must be carried out with anonymous data.
SAP CRM
Production
CRM
SAP
ERP / IS
Production
ERP
SAP CRM
Devel.
CRM
SAP
ERP / IS
Devel.
ERP
SAP CRM
Test
CRM
SAP
ERP / IS
Test
ERP
Project-
system
CRM
Training-
system
CRM
Project-
system
ERP
Training-
system
IS-
UER
P
Sandbox-
system
CRM
Sandbox-
system
ERP
Sample of SAP System Landscape](https://image.slidesharecdn.com/webcastsecurityno4anonymizationen-eugdpr-170728142811/85/GDPR-compliant-data-anonymization-pseudonymization-13-320.jpg)