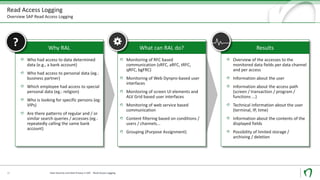
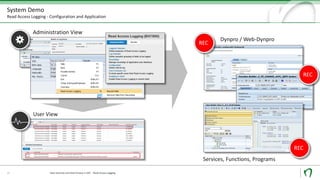
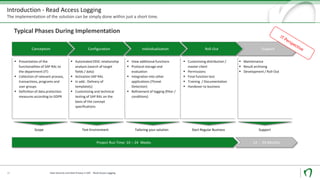
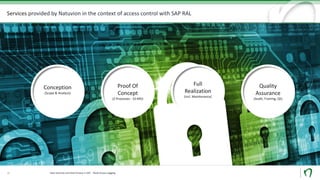
Natuvion is a consulting company specializing in SAP solutions for utilities and digital transformation. The presentation discusses SAP Read Access Logging (RAL), a tool that allows monitoring and logging of access to sensitive data fields within SAP systems. RAL can monitor access at different levels, including user interfaces, services, and programs. Logs show which users accessed what data and provide technical access details. Implementing RAL generally takes 10-24 weeks and involves conception, configuration, testing, and rollout phases. Natuvion's services include RAL concept development, proof of concept implementations, and full realization projects.