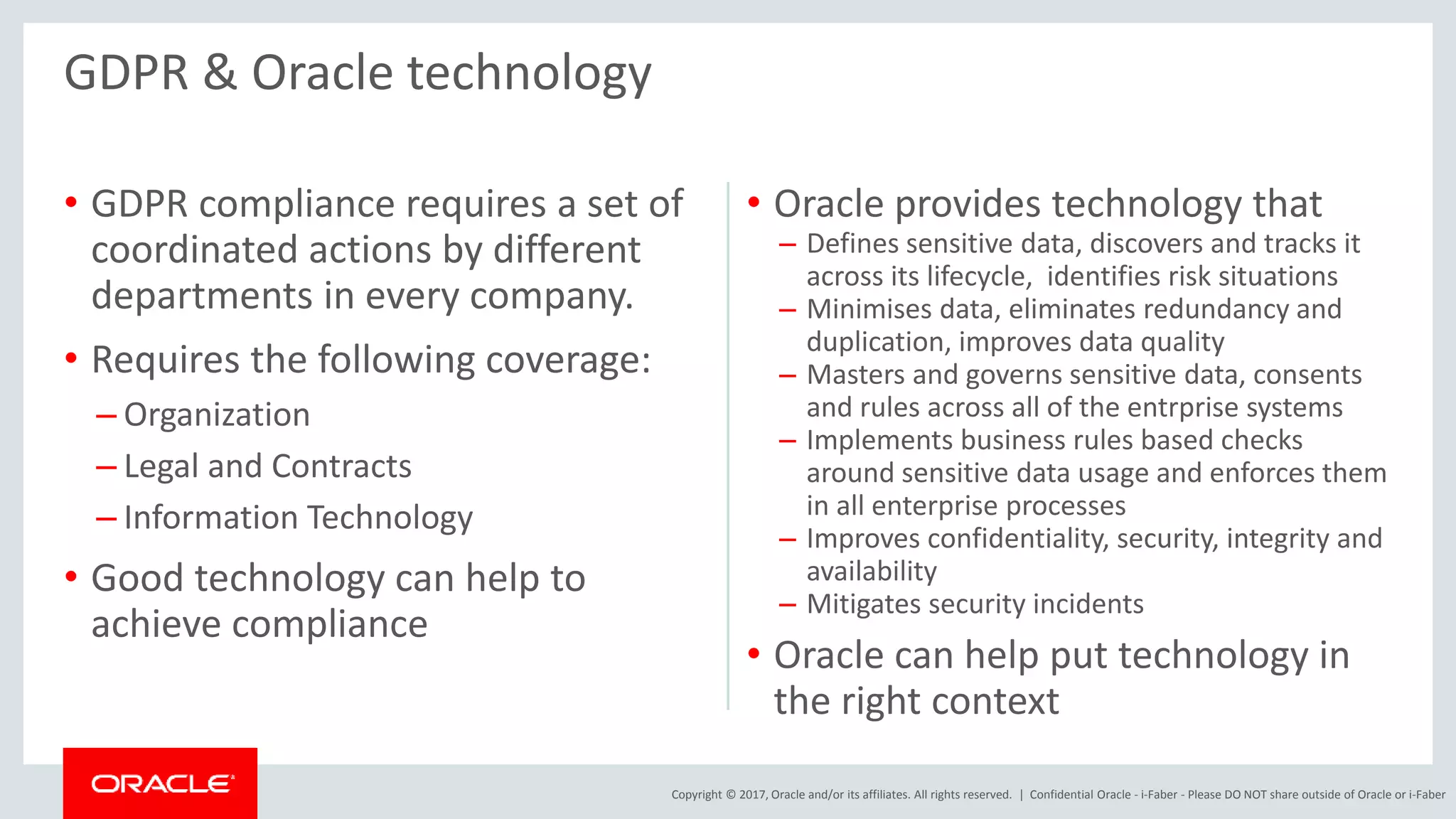
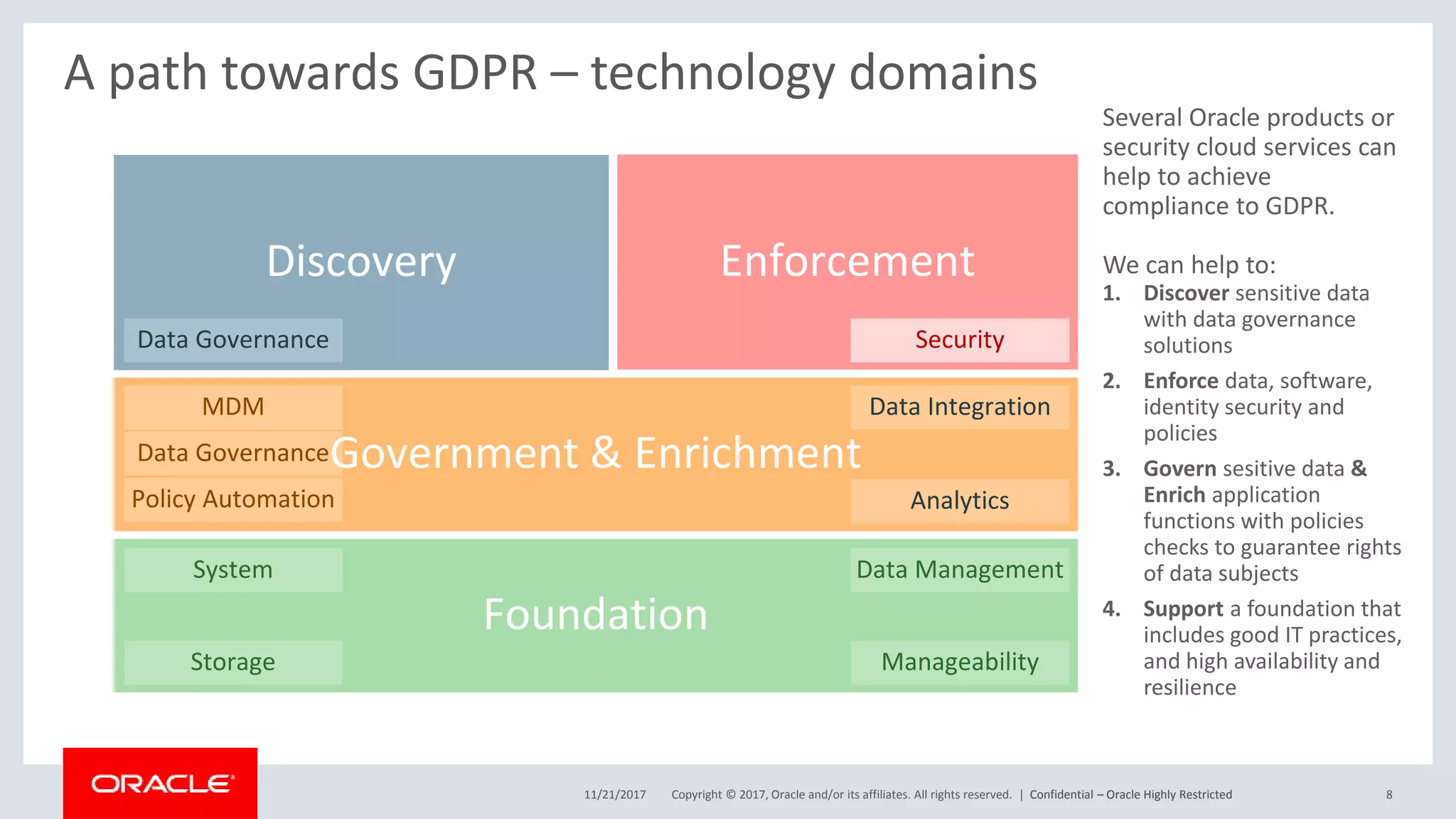
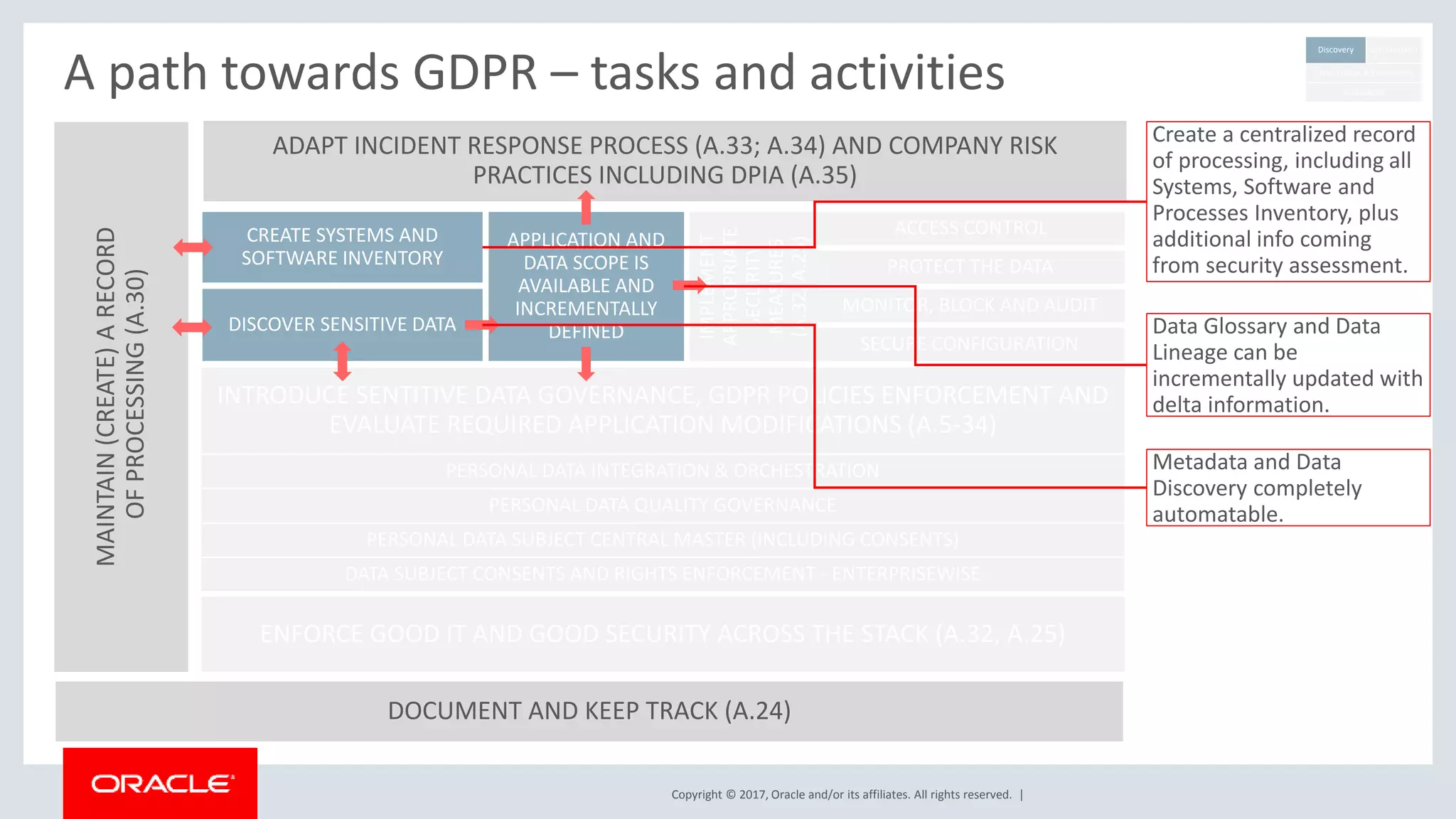
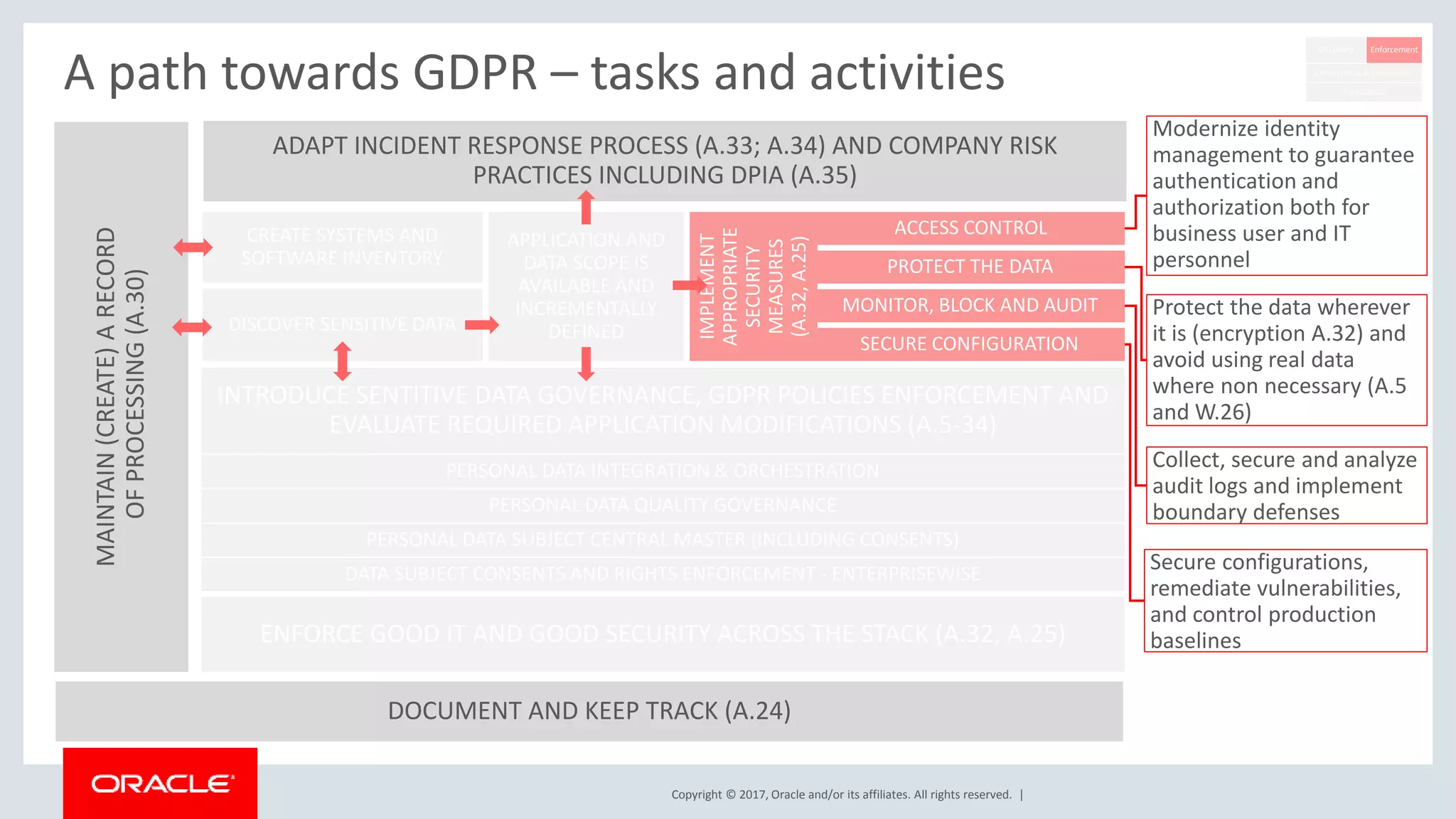
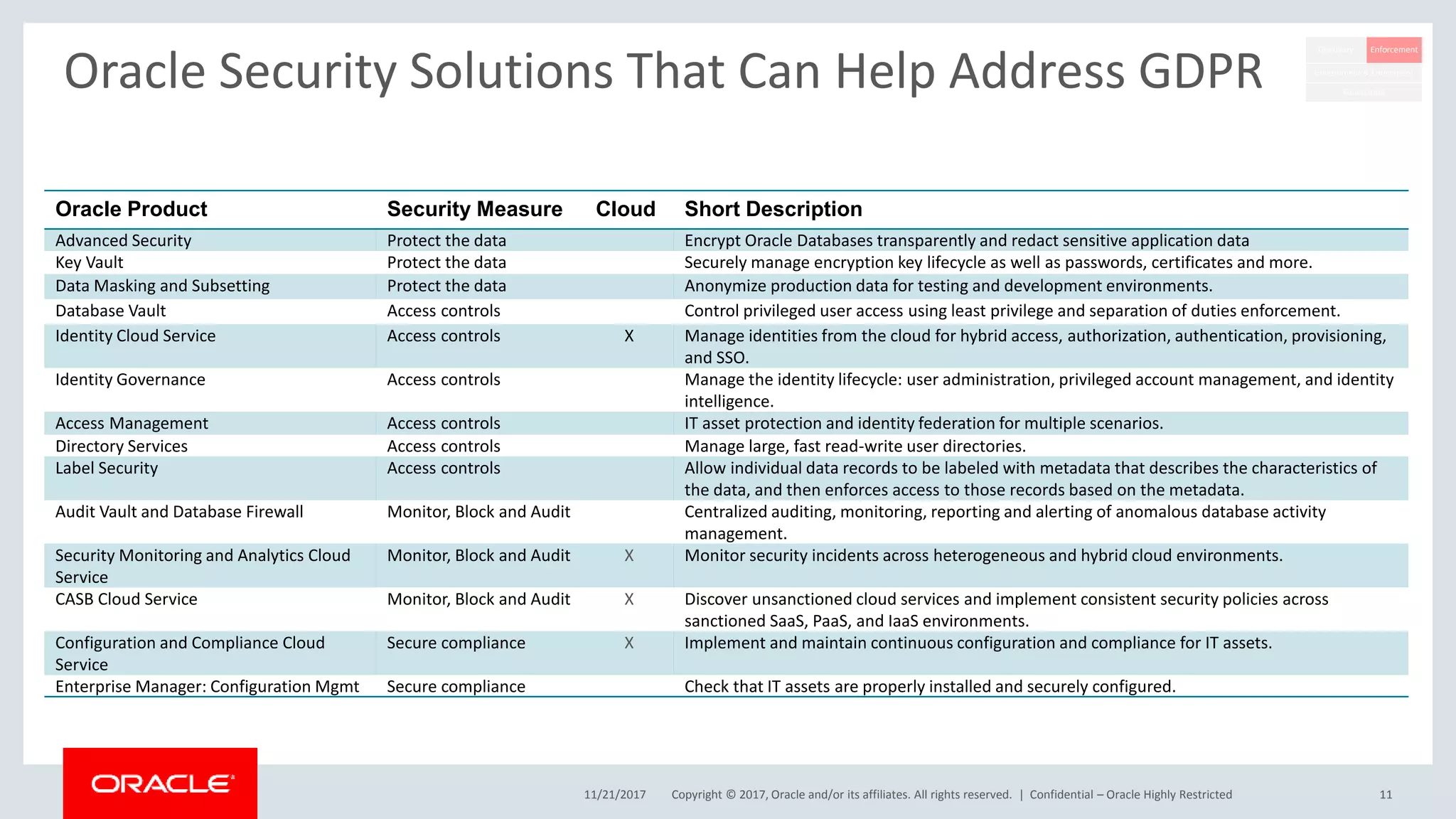
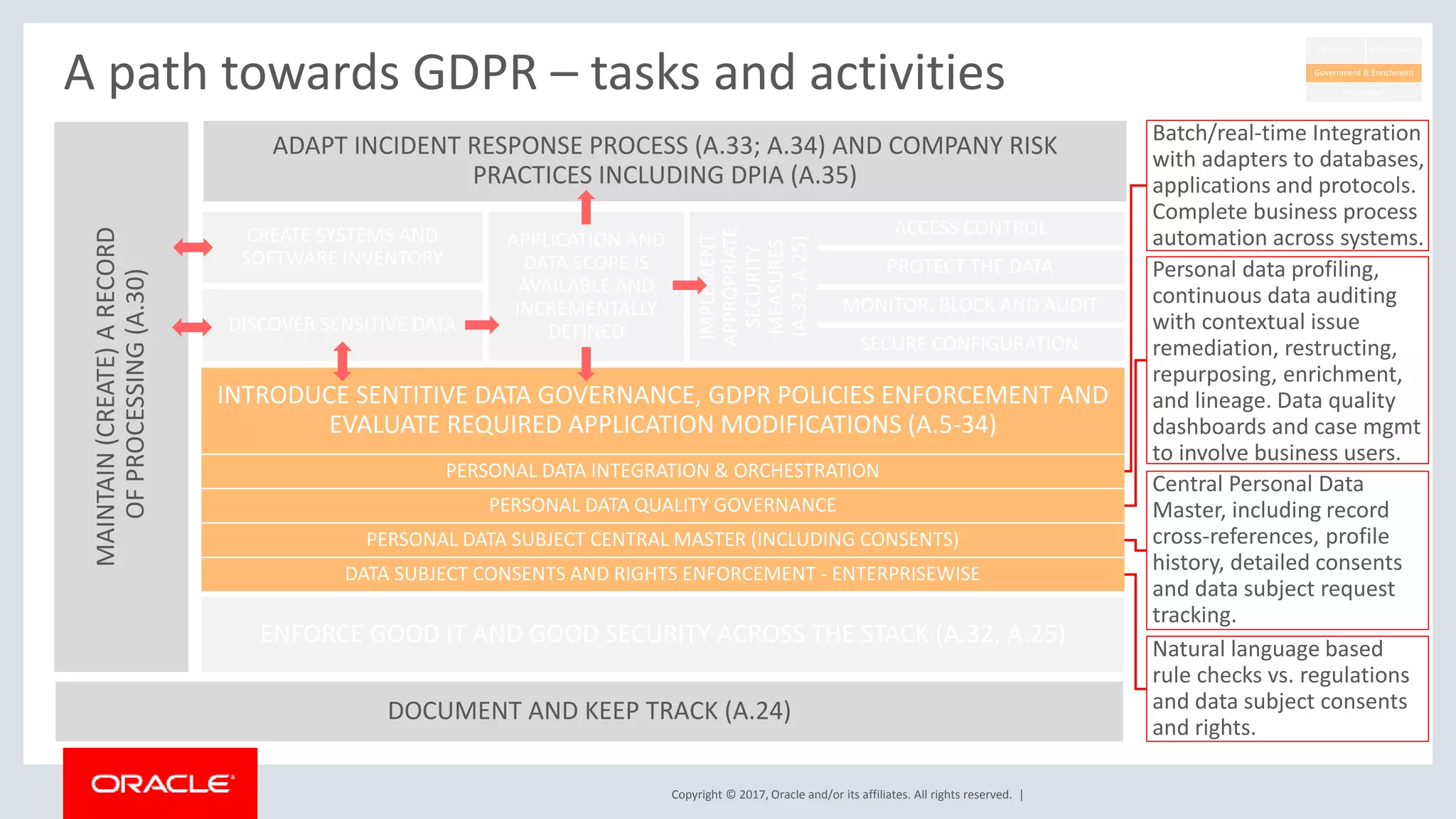
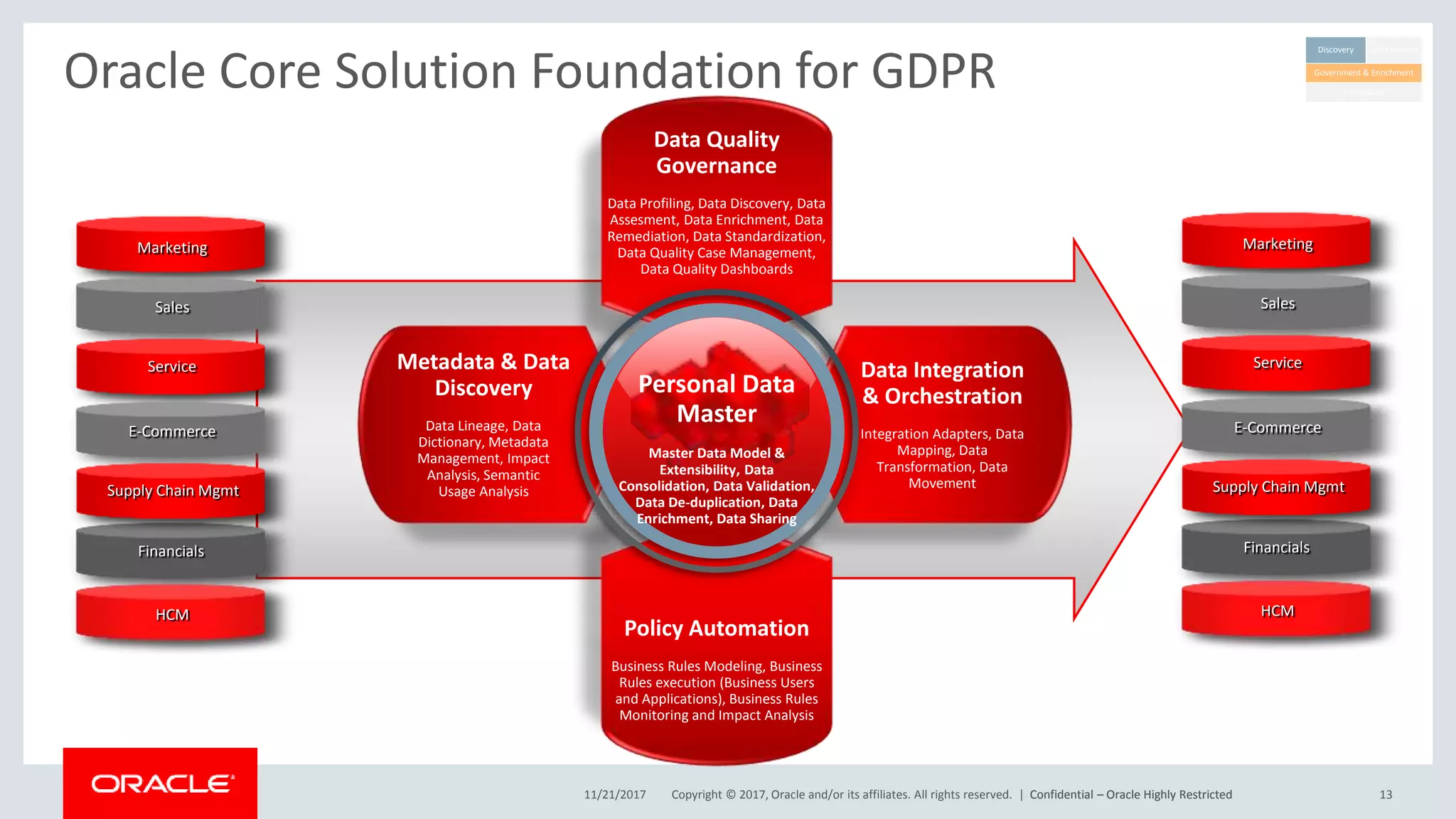
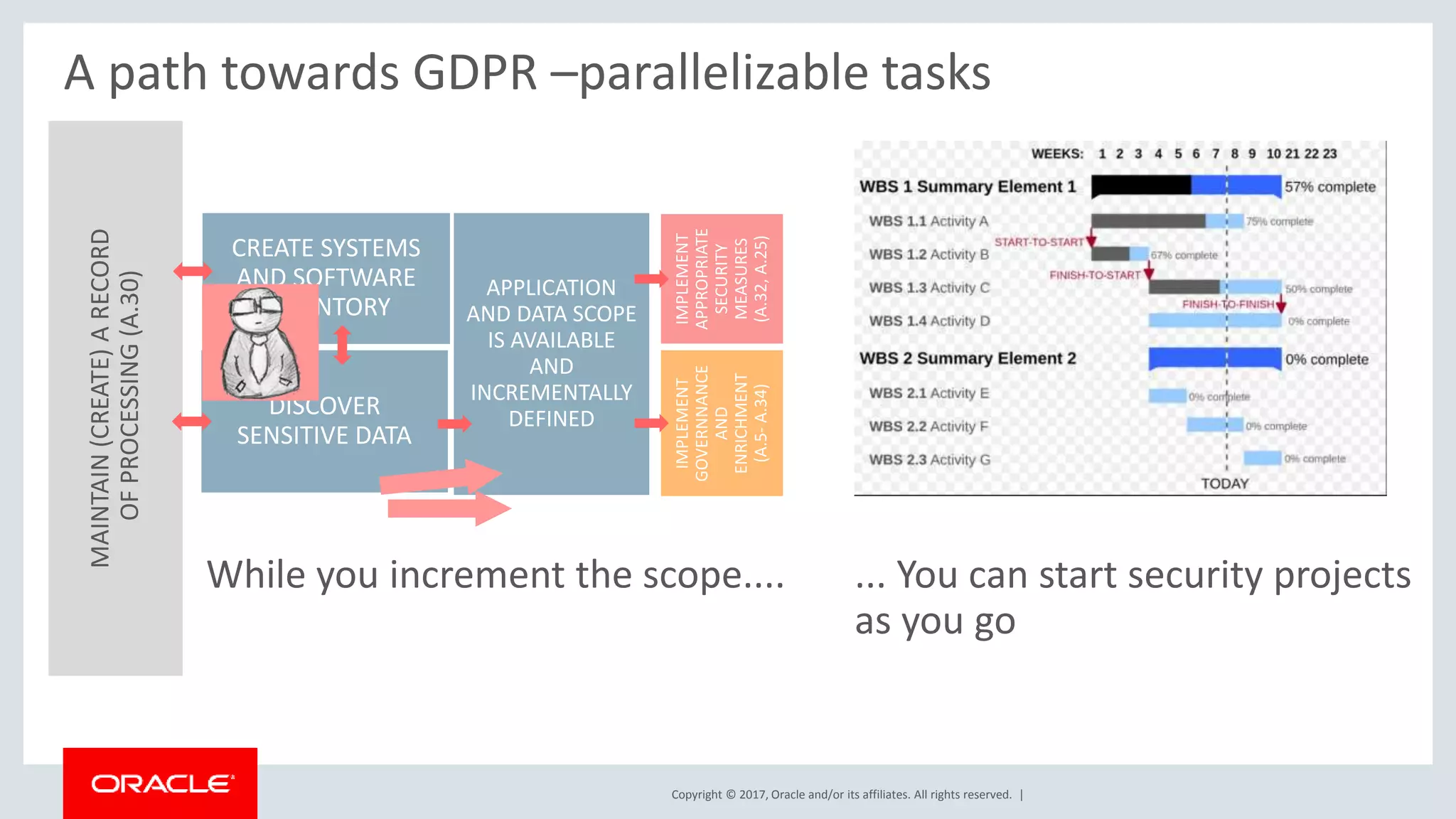
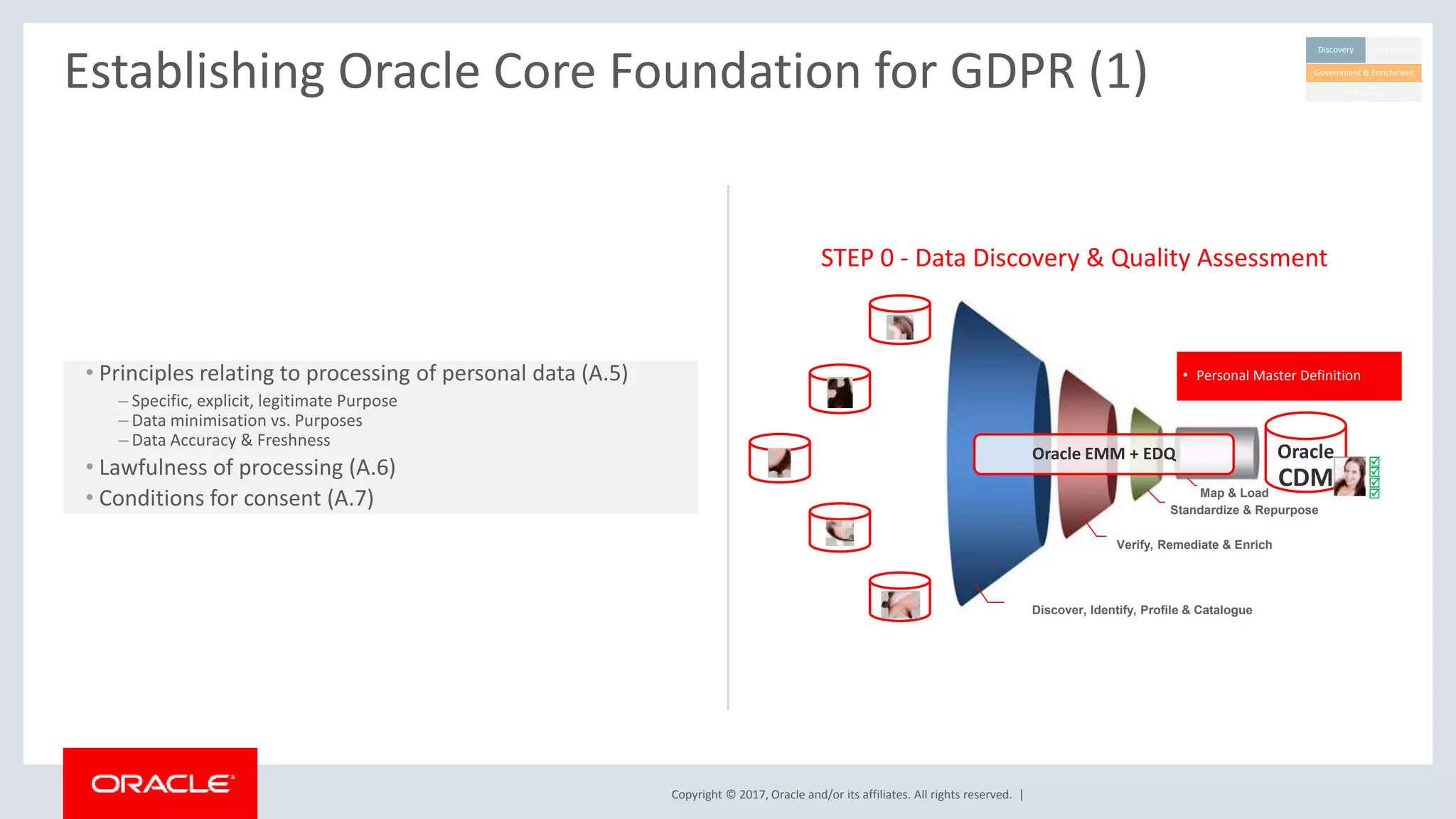
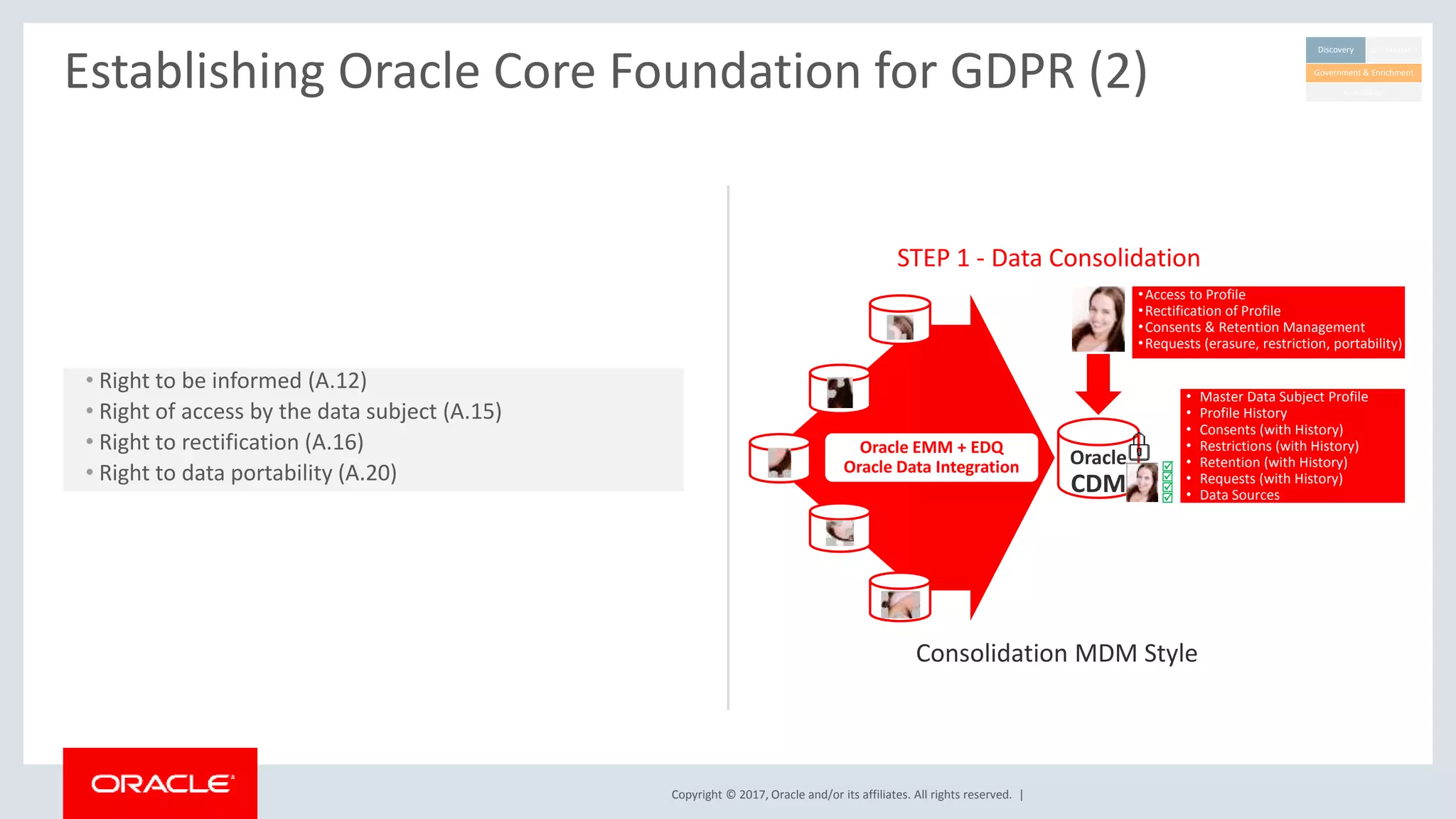
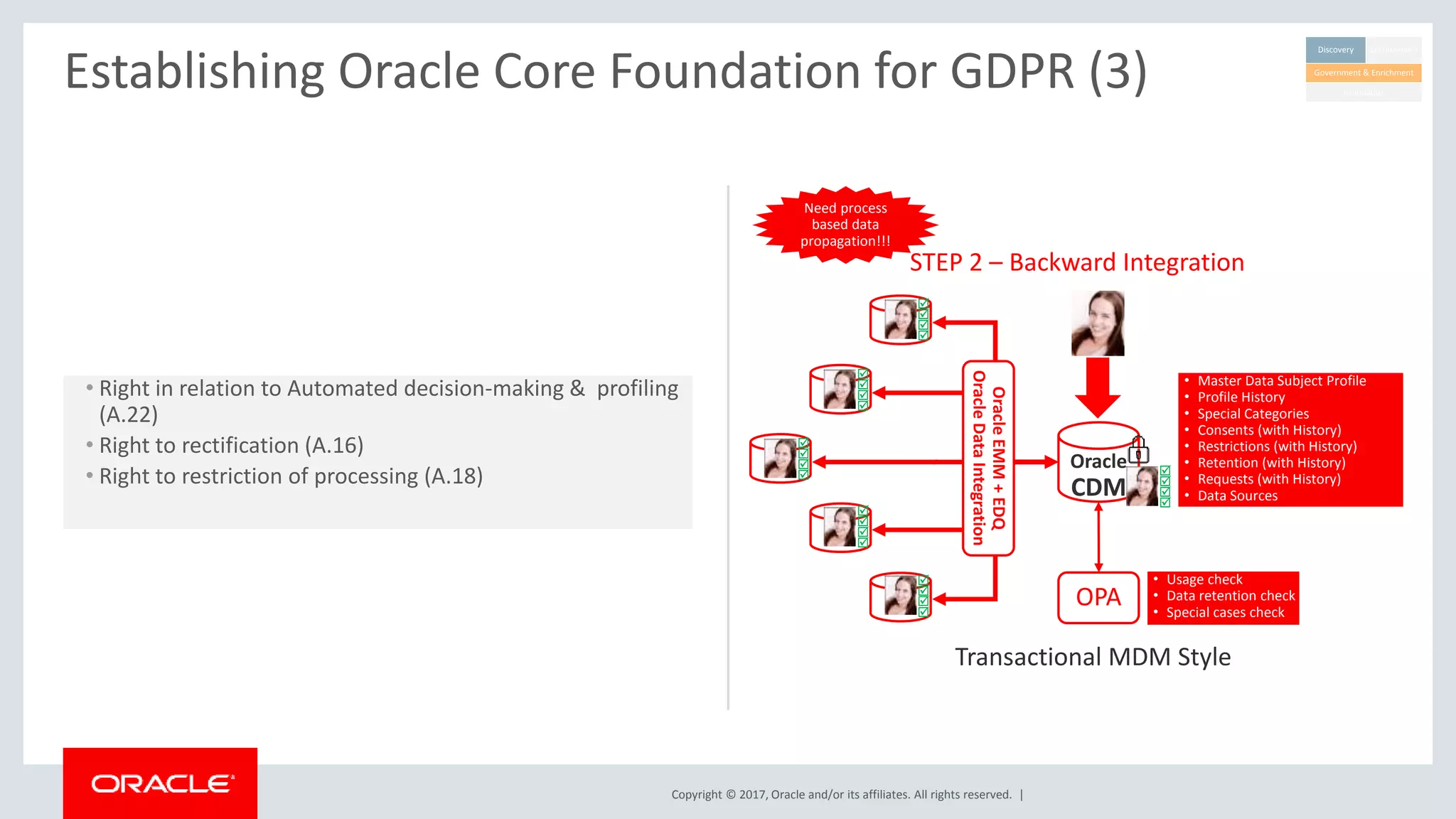
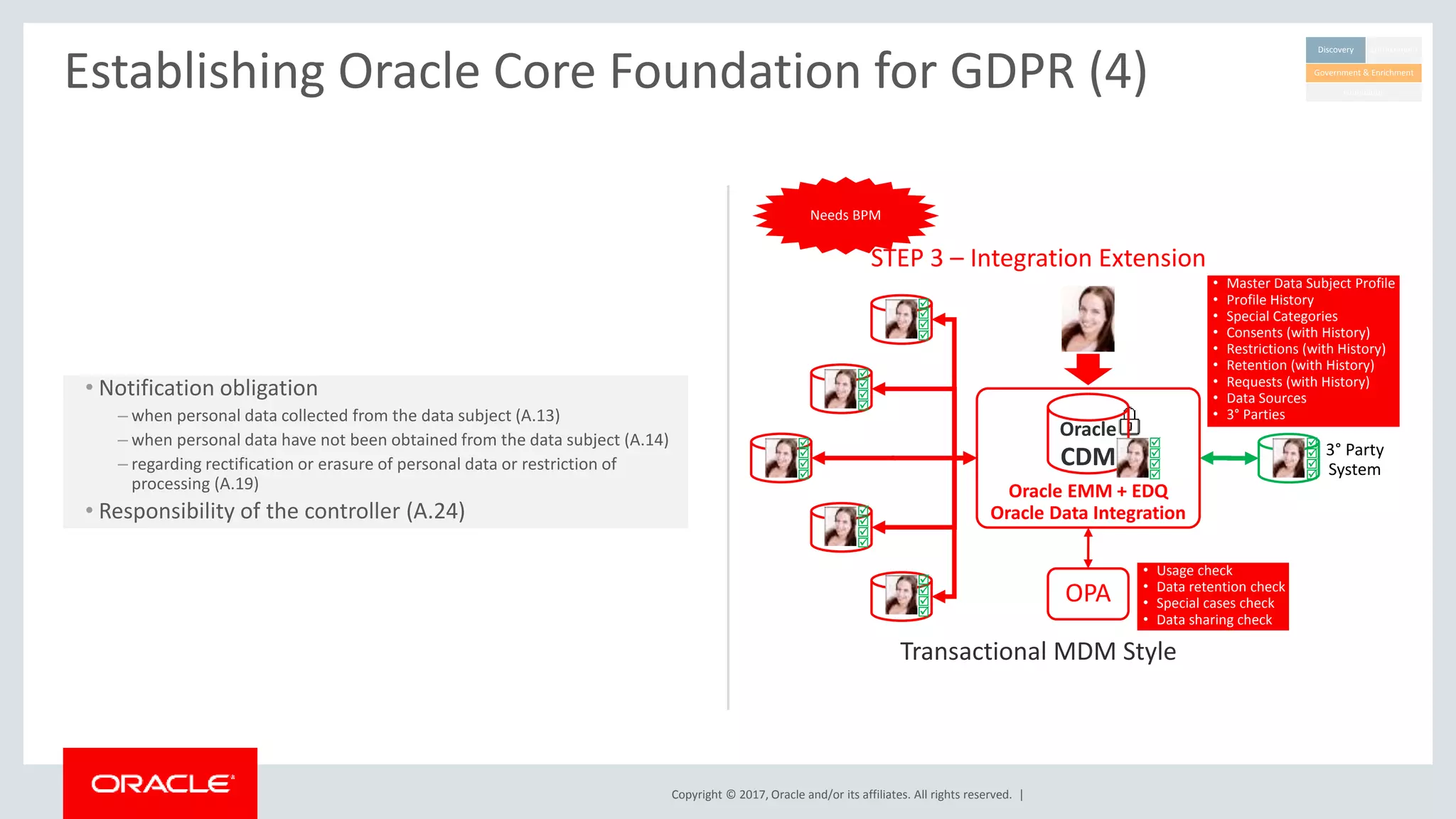
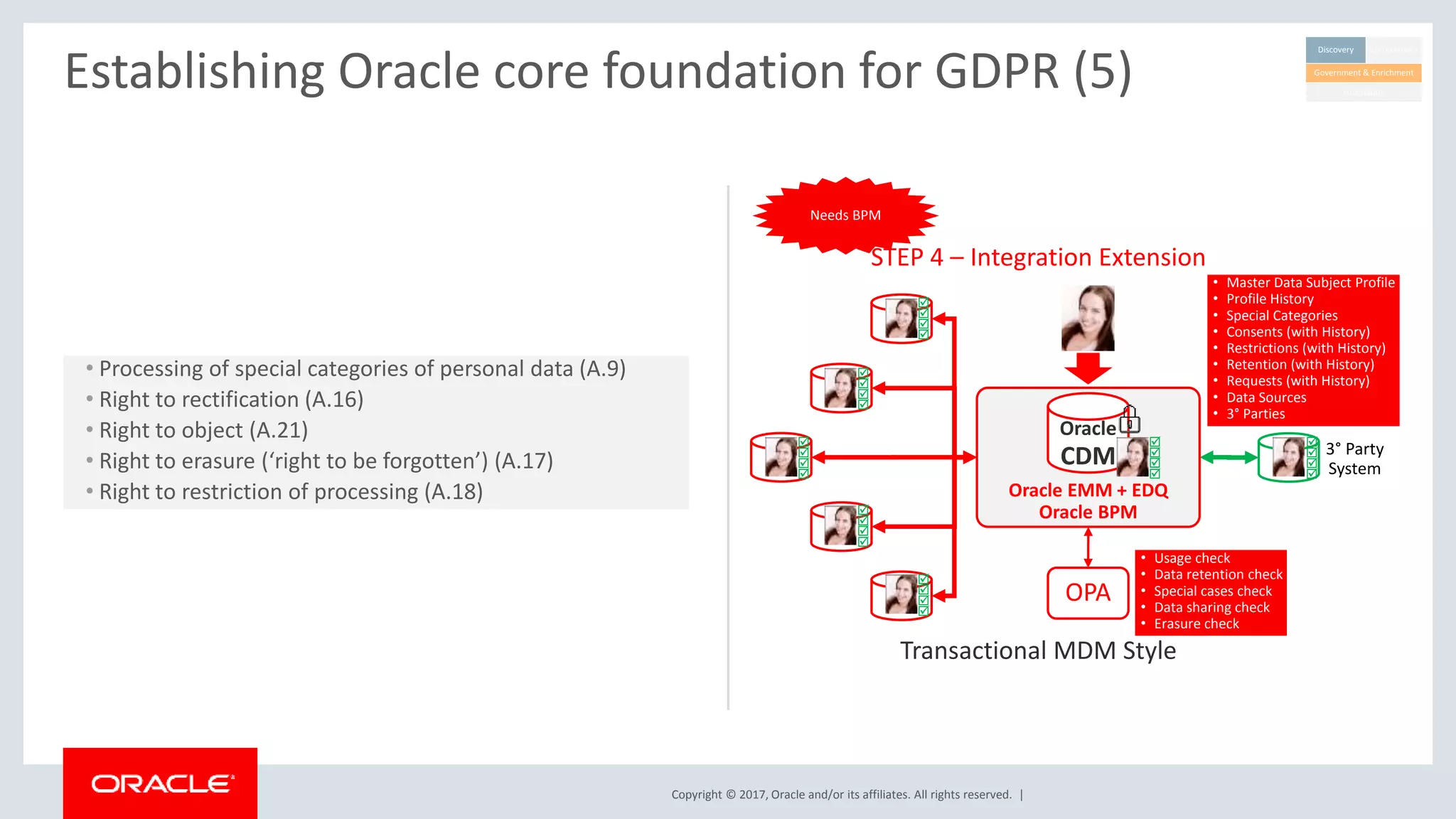
The document discusses Oracle's technology solutions that can help organizations comply with the EU General Data Protection Regulation (GDPR). It provides an overview of GDPR requirements and describes Oracle products that address key areas like data discovery, access controls, monitoring and auditing, and personal data management. It outlines a multi-step approach organizations can take using Oracle technologies to establish the necessary technical foundation and processes for GDPR compliance.