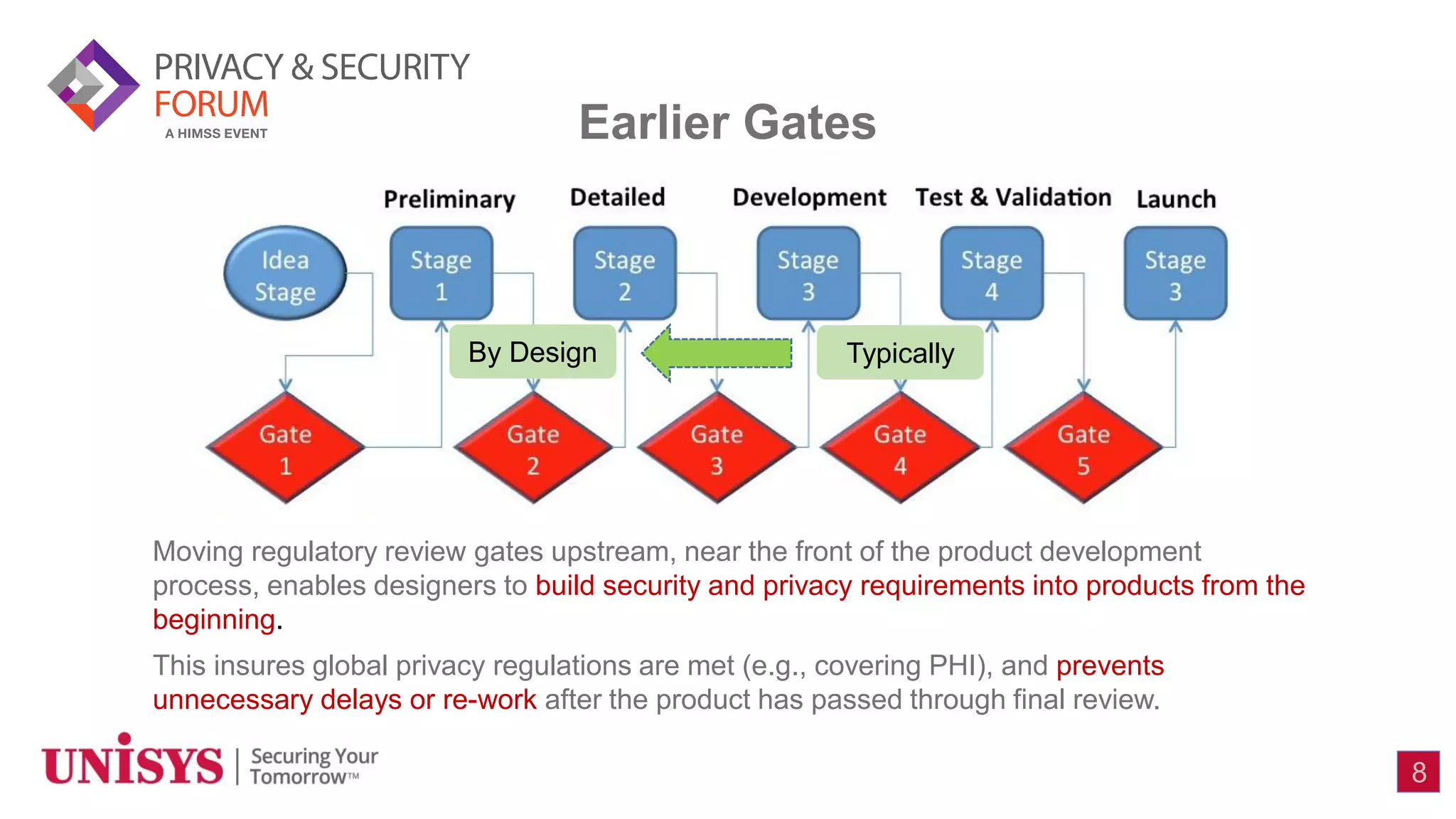
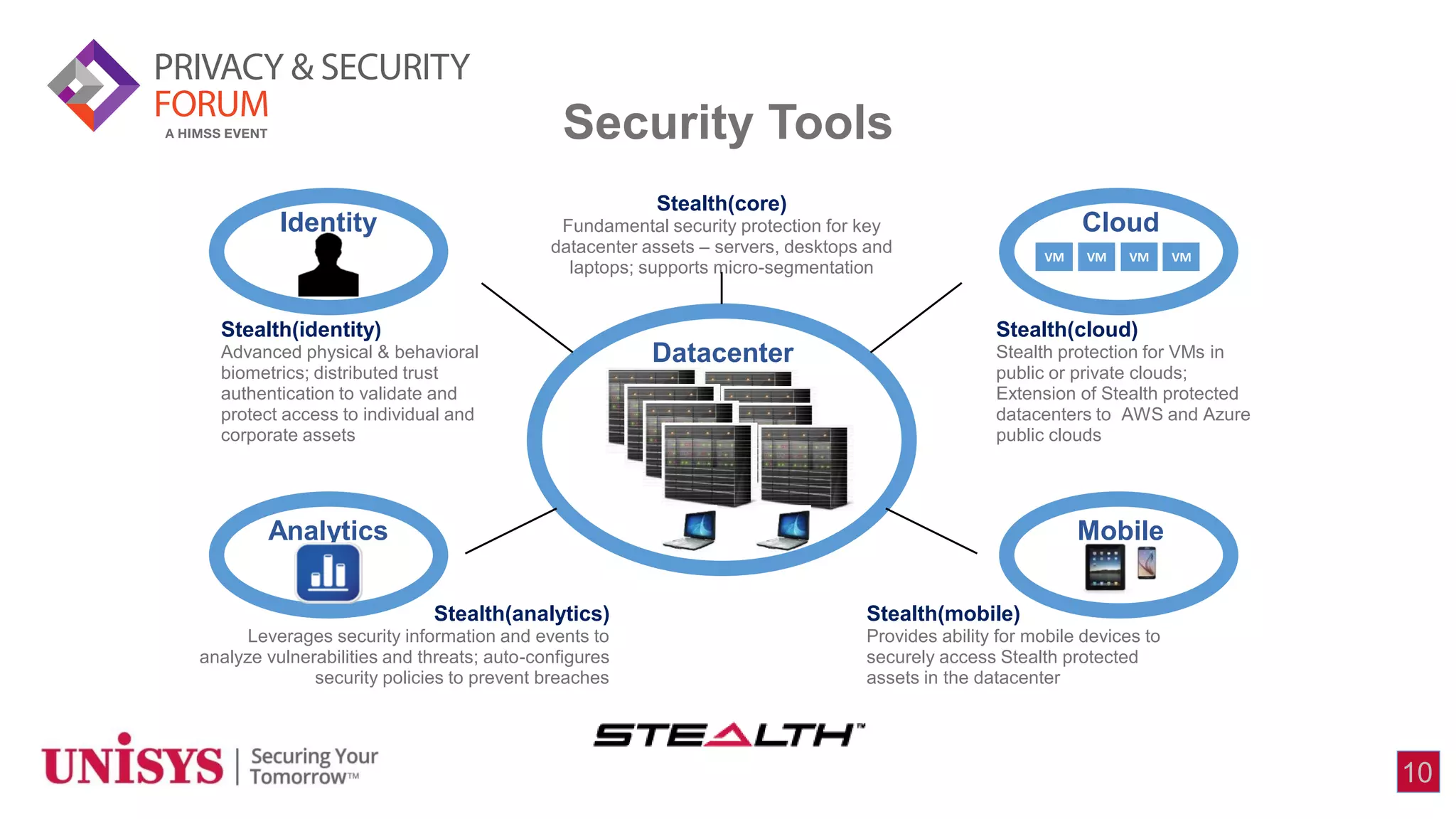
The document highlights the increasing security concerns surrounding medical devices and the healthcare industry's vulnerability to cyberattacks, particularly with the rise of IoT and mobile technologies. Despite significant investment in healthcare IT, only a small portion is allocated to securing medical devices, which are becoming prime targets for criminals. The author advocates for a 'privacy and security by design' initiative to integrate security measures early in the product development process to address these threats.







![Earlier this month Johnson & Johnson notified 114,000 patients of a
security hole in its Animas One Touch Ping connected insulin pump …
the flaw could permit hackers to take control, alter dosage levels and
disable the device altogether. It also exposed the weakness of health
care IOT networks.
Source: Markman, Jon, How Connected Medical Devices Can Cause
Cybersecurity Blues, Forbes Online, Nov 29, 2016.
“IOT is the new frontier of attack where we’re going to start seeing a
rapid increase in these attacks. Healthcare organizations have been
very focused on protecting traditional IT … but [leave] an open door with
IOT devices …”
- Pedro Abreu, Chief Strategy Officer, ForeScout
Increasing Complexity
7](https://image.slidesharecdn.com/livingstone-himsssecurityconferenceslides-v3-161205185007/75/Privacy-and-Security-by-Design-8-2048.jpg)