Our techniques provide fast wavelet tree construction in practice based on recent theoretical work. Experiments on real datasets show our methods using the PEXT and PSHUFB CPU instructions outperform previous approaches. For wavelet trees, our methods are 1.9x faster than naive construction on average and competitive with state-of-the-art. For wavelet matrices, we achieve speedups of 1.1-1.9x over the state-of-the-art. This work provides the first practical implementation of the fastest known wavelet tree construction algorithms.

![2
Background
§ Wavelet tree [Grossi+,SODA’03] / Wavele matrix [Claude+,SPIRE’12]
• Fundamentaltoolsinmodernstringprocessing.
• Fastaccess,rank,andselectonanarrayofnintegersin[0,σ).
10 1 1 0 1 1 000 10 10 01
11 0 01 1 0100 11 00 0 1
1 0 100 01 1 00 0 11 1 10
00 101 10 1 10 1 01 00 1
Awavelettreeson[6,8,9,4,14,11,1,0,5,7,12,13,15,2,3,10]](https://image.slidesharecdn.com/20181010spire18kanetausakufinal-181030035559/75/Fast-Wavelet-Tree-Construction-in-Practice-2-2048.jpg)
![3
Fast WT construction has attracted much attension!!
Papers
Sequential?
Parallel?
Impl.?
[Fuentes-Sepúlveda+,SEA’14] P Yes
[Shun+,DCC’15] P Yes
[Labeit+,DCC’16] P Yes
[Fischer+,ALENEX’18] S+P Yes
[Munro+,SPIRE’14][Babenko+,SODA’15](Bestupperbound) S No
[Shun+,DCC’17](Bestupperbound) P No
§ Gap between theory and practice:
• Nopracticalimplementationof[Munro+,SPIRE’14][Babenko+,
SODA’15]:Thecurrentfastestwavelettreeconstructionalgorithm.](https://image.slidesharecdn.com/20181010spire18kanetausakufinal-181030035559/75/Fast-Wavelet-Tree-Construction-in-Practice-3-2048.jpg)
![4
First* practical implementation of wavelet tree construction
based on [Munro+, SPIRE’14][Babenko+, SODA’15]
Main result
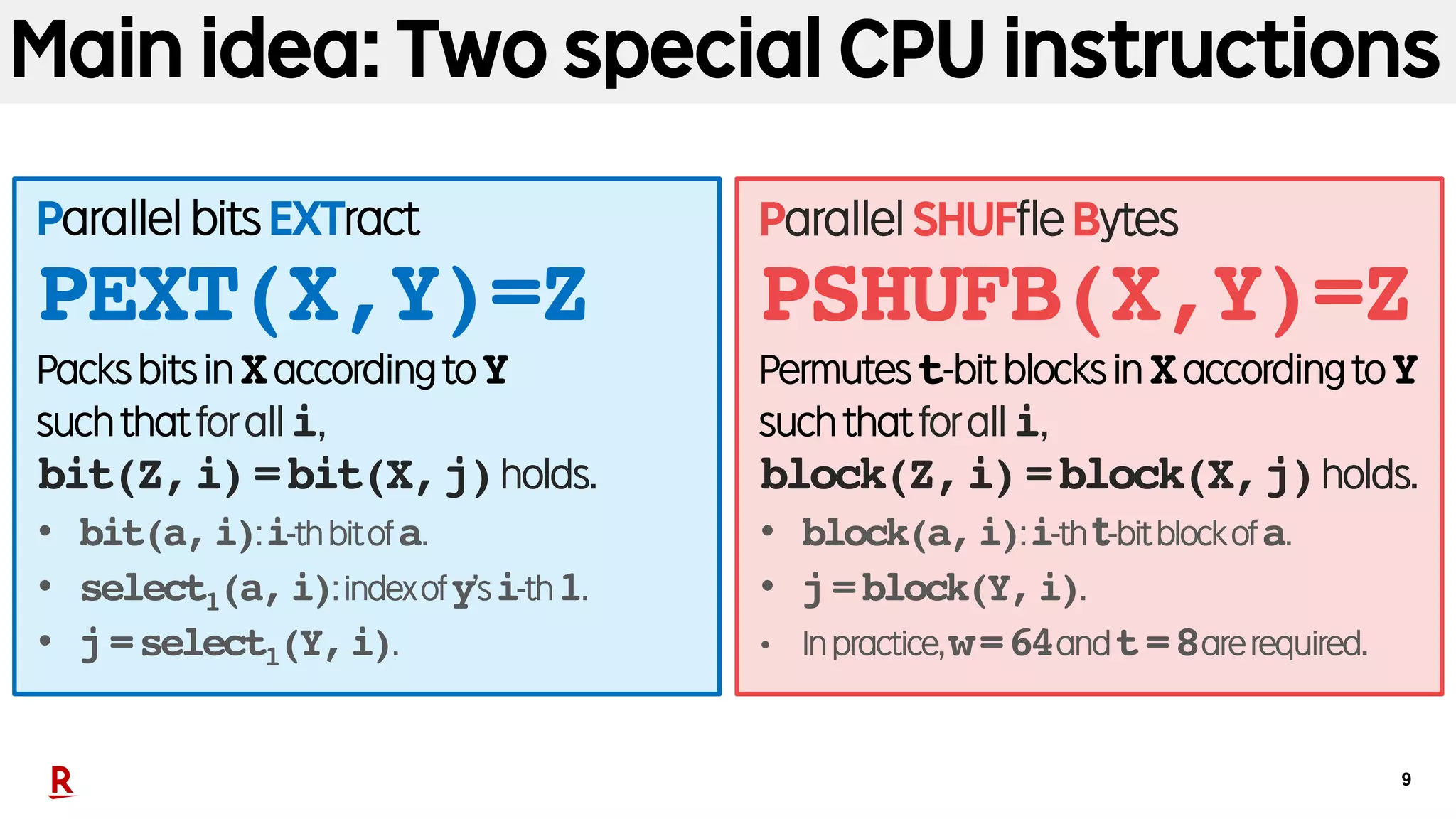
§ Our idea: Replace precomputed tables w/
• SpecialCPUinstruction:PEXTin(BMI2)orPSHUFB(inSSSE3).
• Broadwordcomputation(omitted).
§ Experiments on real datasets:
• Wavelettree:ourswerecompetitivetoSOTA[Fischer+,ALENEX'18]
• Waveletmatrix:ourswere1.1–1.9xfasterthanSOTA.
*SzymonGrabowskikindlypointedthatTuukkaNorrialsotriedsimilarapproaches:
github.com/tsnorri/wt-construct-gn](https://image.slidesharecdn.com/20181010spire18kanetausakufinal-181030035559/75/Fast-Wavelet-Tree-Construction-in-Practice-4-2048.jpg)

![8
6
0110
8
1000
9
1001
4
0100
14
1110
11
1011
1
0001
0
0000
5
0101
7
0111
12
1100
15
1111
13
1101
2
0010
3
0011
10
1010
6
0110
8
1000
9
1001
4
0100
14
1110
11
1011
1
0001
0
0000
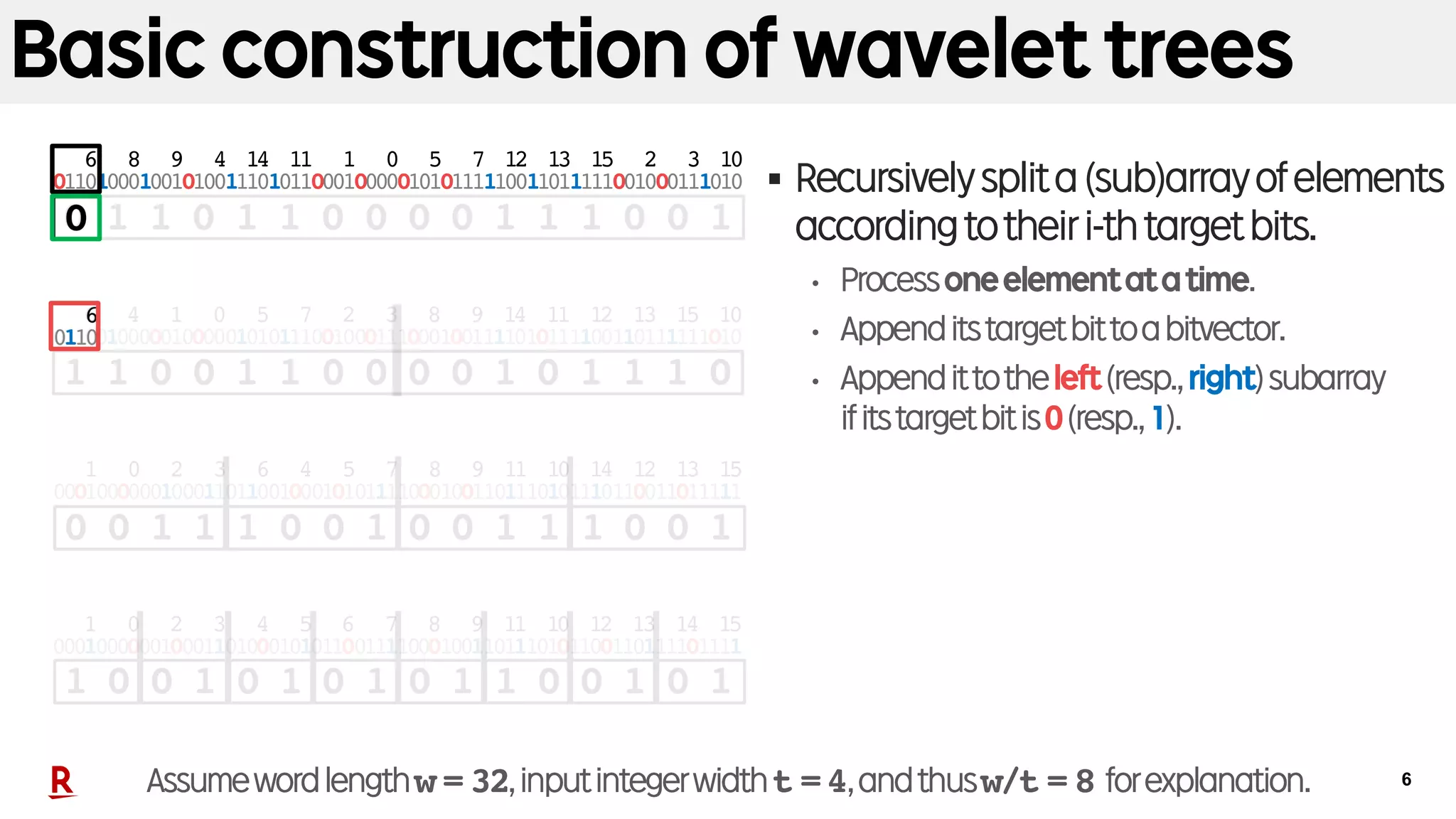
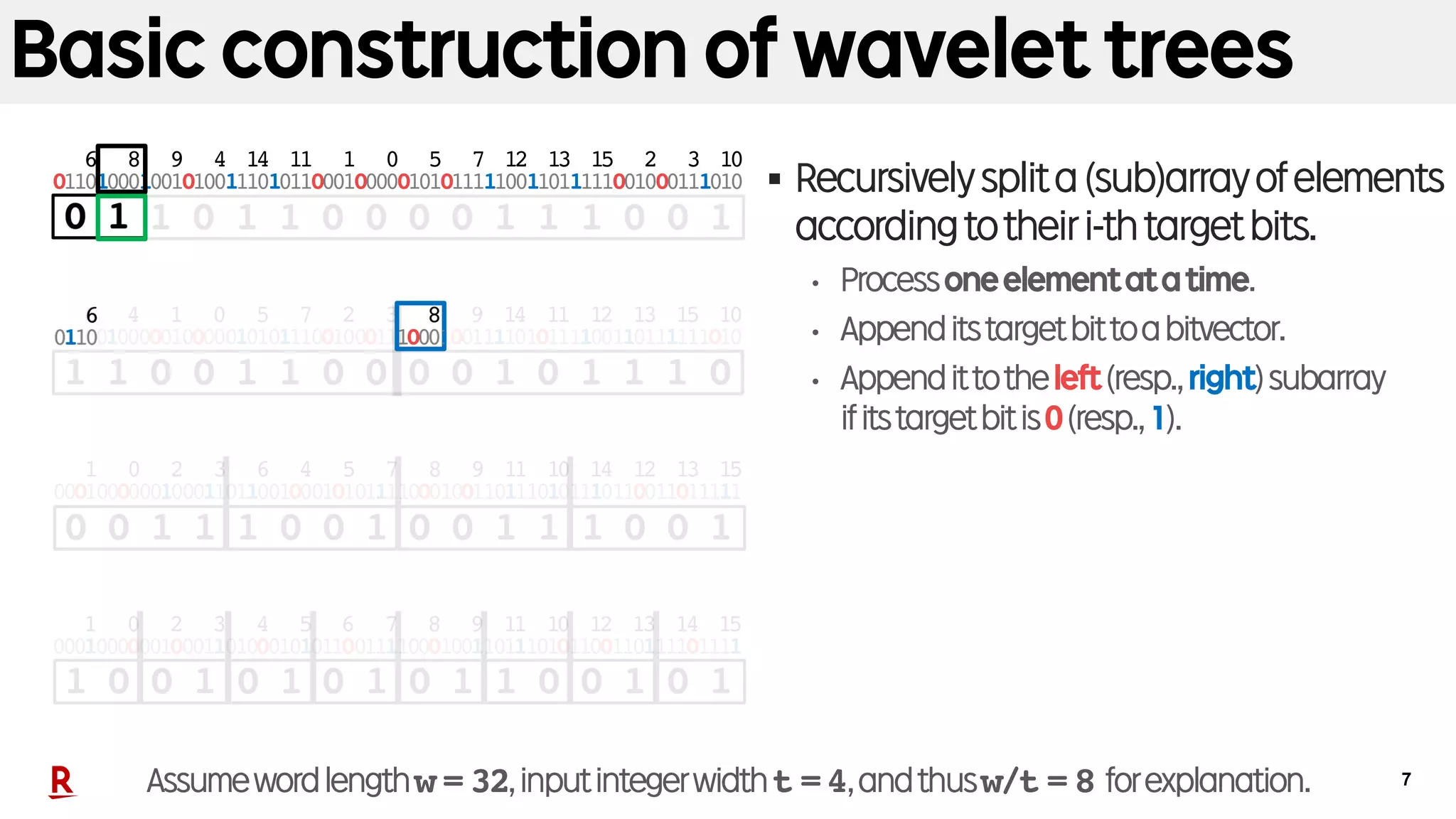
Fast construction of wavelet trees
§ Fastwavelettreeconstruction
[Munro+, SPIRE’14][Babenko+,SODA’15]
• Processmultipleelementsatatime.
• w/toft-bitelementscanbereadtogether.
§ Primitiveoperations:
X Bbitpack ( ,i)=
X X0listsplit( ,i)=( , )X1
X1
A subarray consisting of
X’s elements whose 0th bit 1
A subarray consisting of
X’s elements whose 0th bit 0
X0
First w/t elements in a word of w bits (e.g., w = 32 and t = 4)
X
Packed 0th bits of elements contained in X.
B
Assumewordlengthw = 32,inputintegerwidtht =4,andthusw/t = 8 forexplanation.
Assumption:
• ThestandardwordRAM
• w:wordlength(inbits)
• t:inputintegerwidth(inbits)
• t≤w justforexplanation.
(Thisconditioncanbeeliminated.)](https://image.slidesharecdn.com/20181010spire18kanetausakufinal-181030035559/75/Fast-Wavelet-Tree-Construction-in-Practice-8-2048.jpg)
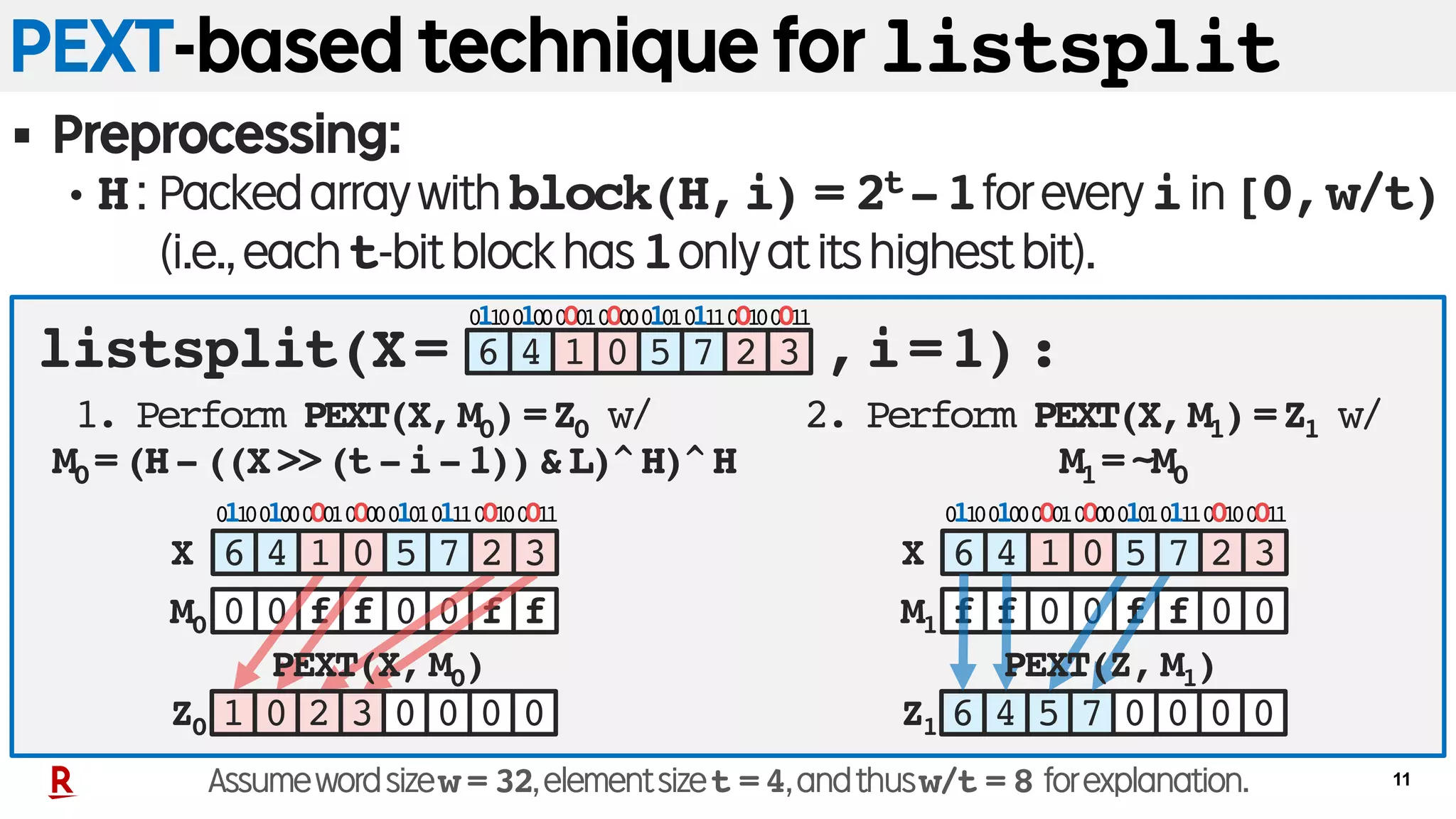
![12
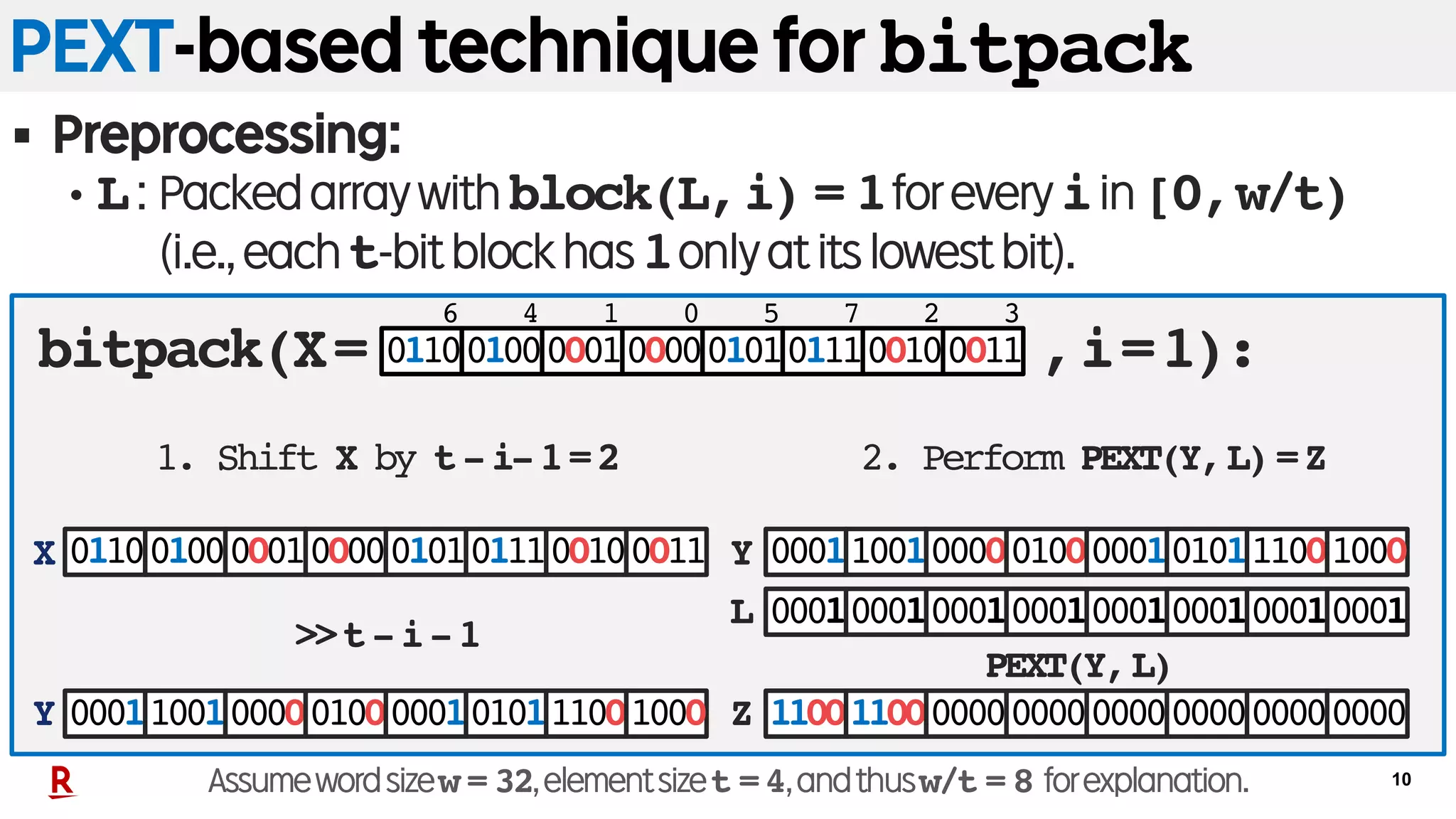
PSHUFB-based technique for listsplit
§ Preprocessing: Let m=2w/t be # of blocks in a word.
• T[a]forallain[0,m):Packedarraycontaininginascendingorder
(1)allindexesof0’sfollowedby(2)allindexesof1’sin a.
2. Extract each part from Y.
|a|1: Number of ones in a.
<<t|a|1
6 4 701 52 3
0 0 001 02 3Z0
Y 6 4 701 52 3
0 0 046 05 7Z1
Y
00010000001000110110010001010111 00010000001000110110010001010111
1. Perform PSHUFB(X,T[a]) w/
a=bitpack(X,i)=11001100
0 1 532 46 7
01100100000100000101011100100011
6 4 701 5 2 3
6 4 701 52 3
T[a]
Y
X
Assumewordsizew = 32,elementsizet =4,andthusw/t = 8 forexplanation.
>>t|a|1
<<w-t|a|1PSHUFB(X,T[a])
6 4 701 5 2 3
01100100000100000101011100100011
listsplit(X= ,i=1):](https://image.slidesharecdn.com/20181010spire18kanetausakufinal-181030035559/75/Fast-Wavelet-Tree-Construction-in-Practice-12-2048.jpg)
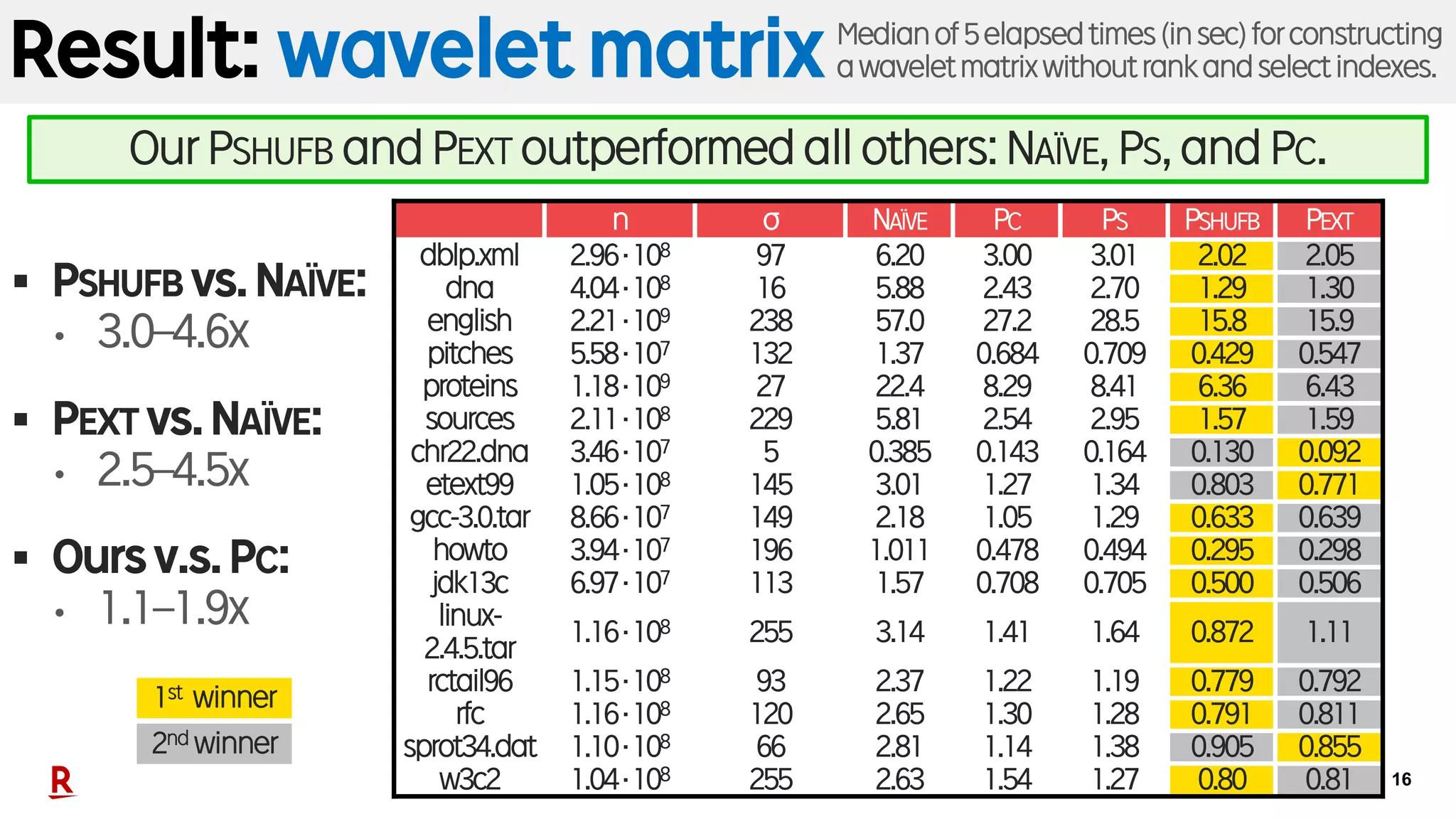
![17
Conclusion
§ Practical wavelet tree construction using PEXT/PSHUFB.
• Based on [Munro+, SPIRE’14] and [Babenko+, SODA’15]
§ Experiments on real datasets:
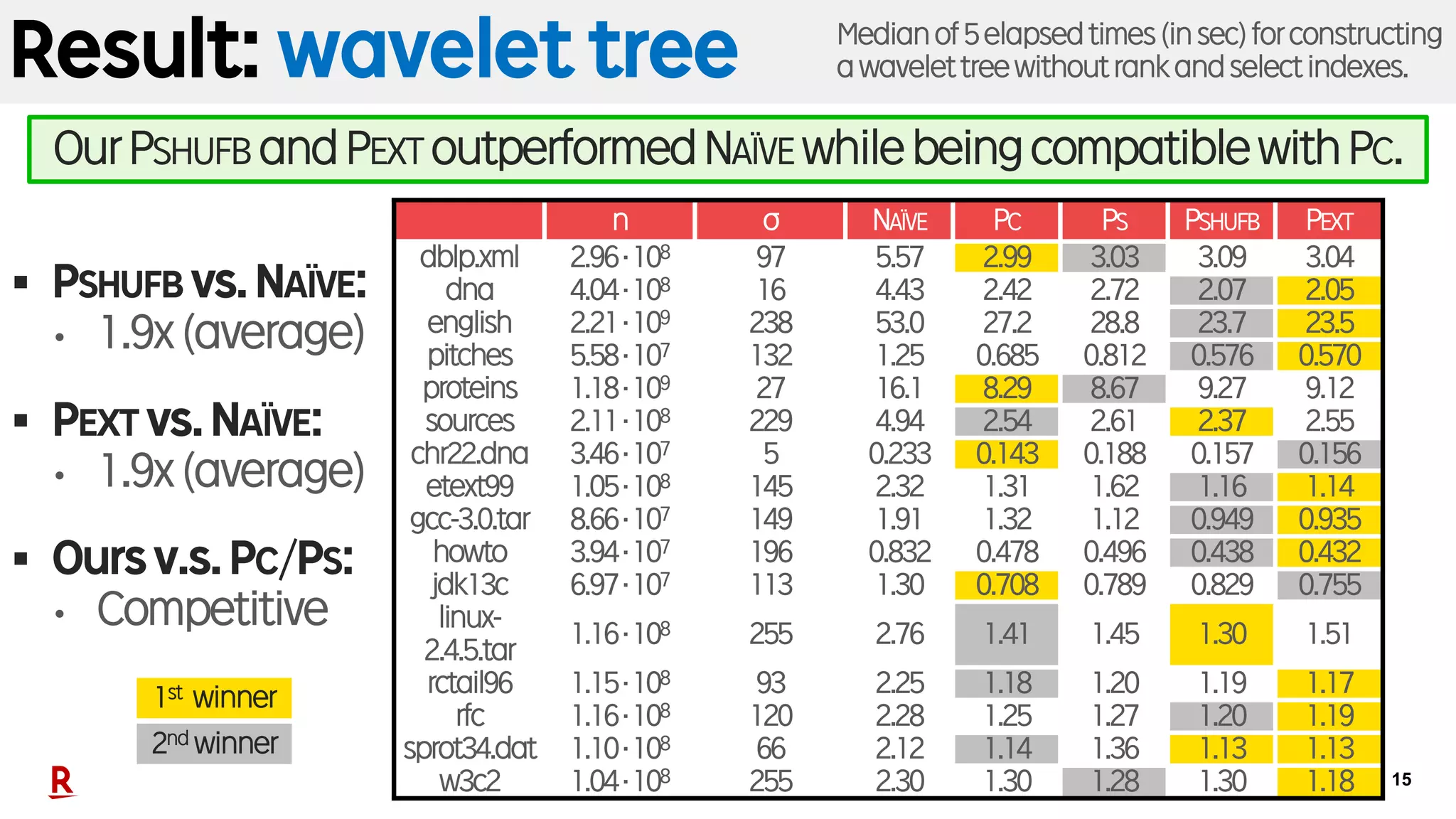
• Wavelet tree: Faster than NAÏVE and competitive w/ SOTA:
prefix sorting (PS) and prefix counting (PC).
• Wavelet matrix: Faster than NAÏVE, PS, and PC.
§ Future work
• Exploit moreparallelismin CPUcoresand/orSIMD registers.](https://image.slidesharecdn.com/20181010spire18kanetausakufinal-181030035559/75/Fast-Wavelet-Tree-Construction-in-Practice-17-2048.jpg)
