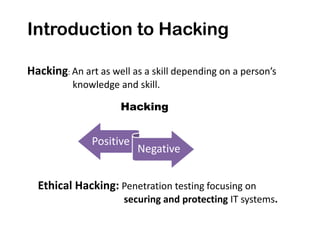
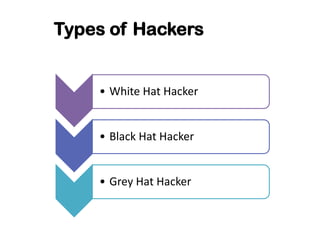
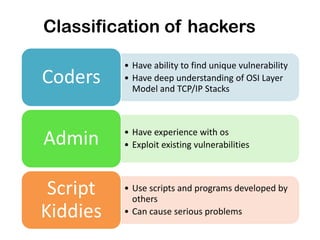
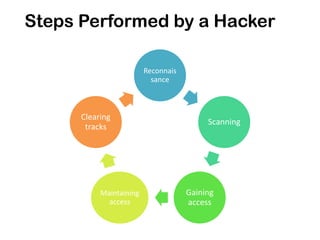
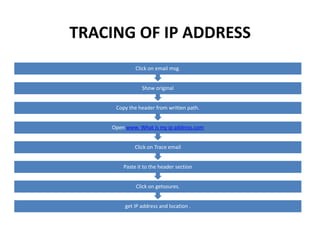
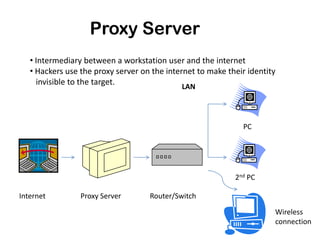
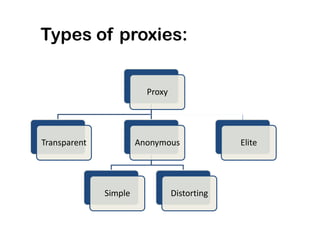
This document discusses ethical hacking and different types of hackers. It covers white hat hackers who perform ethical hacking and penetration testing to improve security, black hat hackers who conduct hacking for illegal purposes, and grey hat hackers who are in between. The document also outlines the steps hackers take including reconnaissance, scanning, gaining access, maintaining access, and clearing tracks. It provides information on IP address ranges, tracing IP addresses, email protocols, proxy servers, and security considerations.