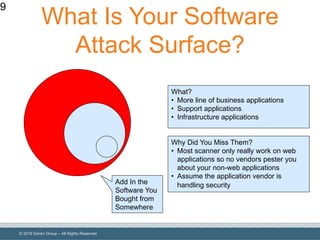
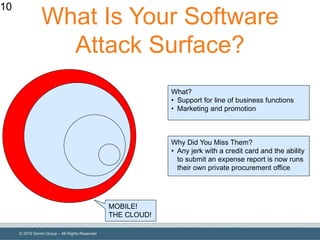
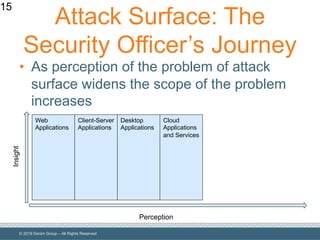
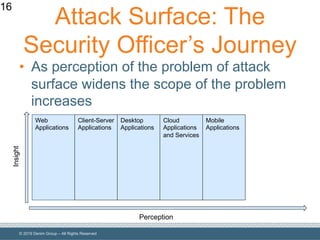
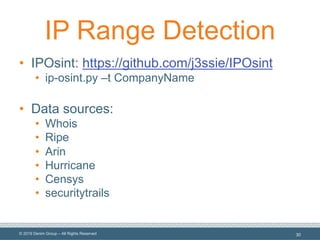
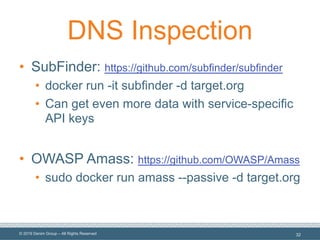
The document outlines the importance of understanding and enumerating an organization's software attack surface to effectively manage security vulnerabilities. It emphasizes the need for a software security program that encompasses people, processes, and tools, while also addressing challenges such as resource allocation and organizational resistance. The strategy involves identifying, categorizing, and continuously monitoring applications based on their significance to prioritize security efforts.






![© 2019 Denim Group – All Rights Reserved
[Translation]
Find out what applications you
have in your organization
Decide the relative importance of
applications and treat them
differently based on this
6](https://image.slidesharecdn.com/enumeratingenterpriseattacksurfacev3houseccon-190410211821/85/Enumerating-Enterprise-Attack-Surface-7-320.jpg)





























![© 2019 Denim Group – All Rights Reserved
[Translation]
Find out what applications you
have in your organization
Decide the relative importance of
applications and treat them
differently based on this
42](https://image.slidesharecdn.com/enumeratingenterpriseattacksurfacev3houseccon-190410211821/85/Enumerating-Enterprise-Attack-Surface-43-320.jpg)

