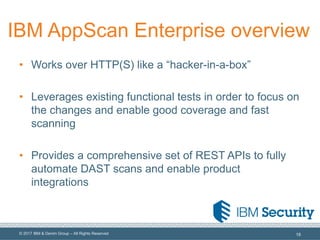
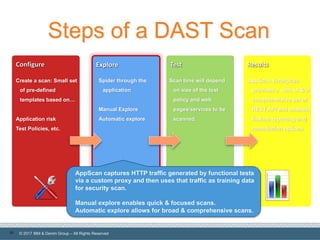
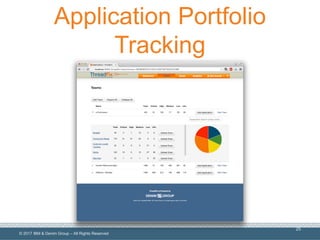
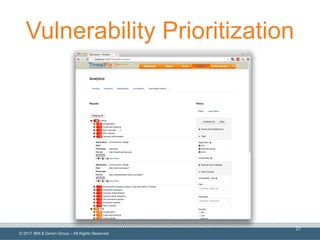
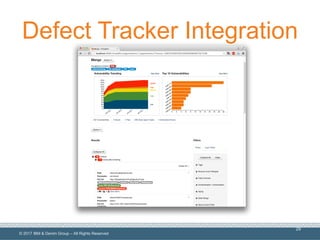
The document discusses integrating application security (AppSec) testing into DevOps processes to reduce risk and vulnerabilities. It emphasizes the importance of automating dynamic analysis security testing (DAST) within CI/CD pipelines and balancing testing coverage with speed. Additionally, it outlines approaches for effective vulnerability management, including the use of tools like IBM AppScan Enterprise and ThreadFix.