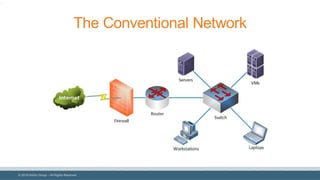
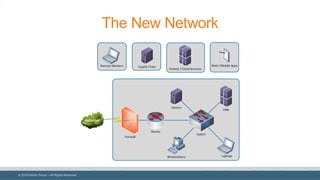
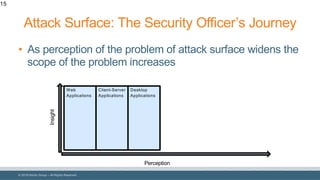
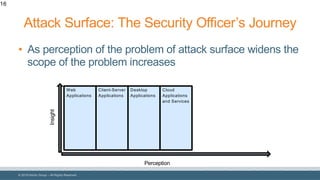
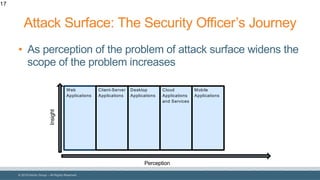
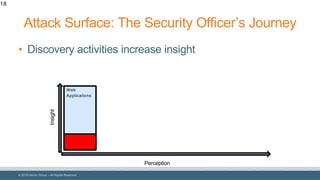
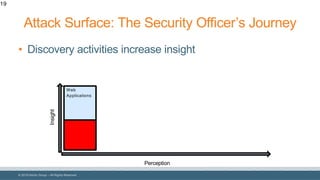
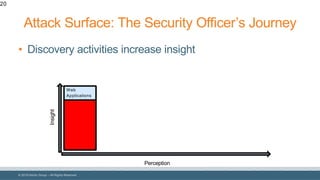
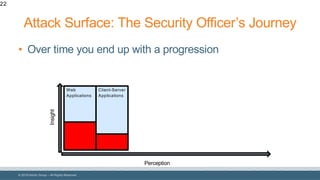
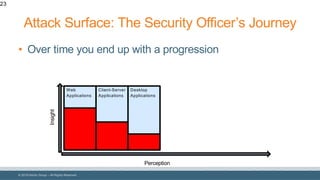
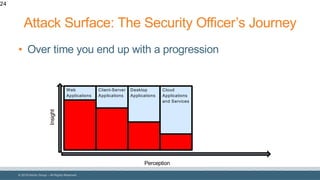
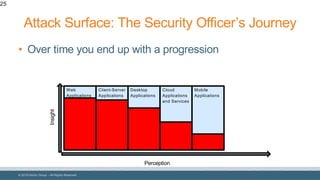
The document discusses strategies for reducing attack surfaces in budget-constrained environments and highlights the evolving nature of cyber threats. It emphasizes the importance of understanding and managing security budgets, conducting regular vulnerability assessments, and maintaining relationships with trusted security partners. The overall goal is to enhance organizational security posture amidst increasing external pressures and sophisticated attacks.