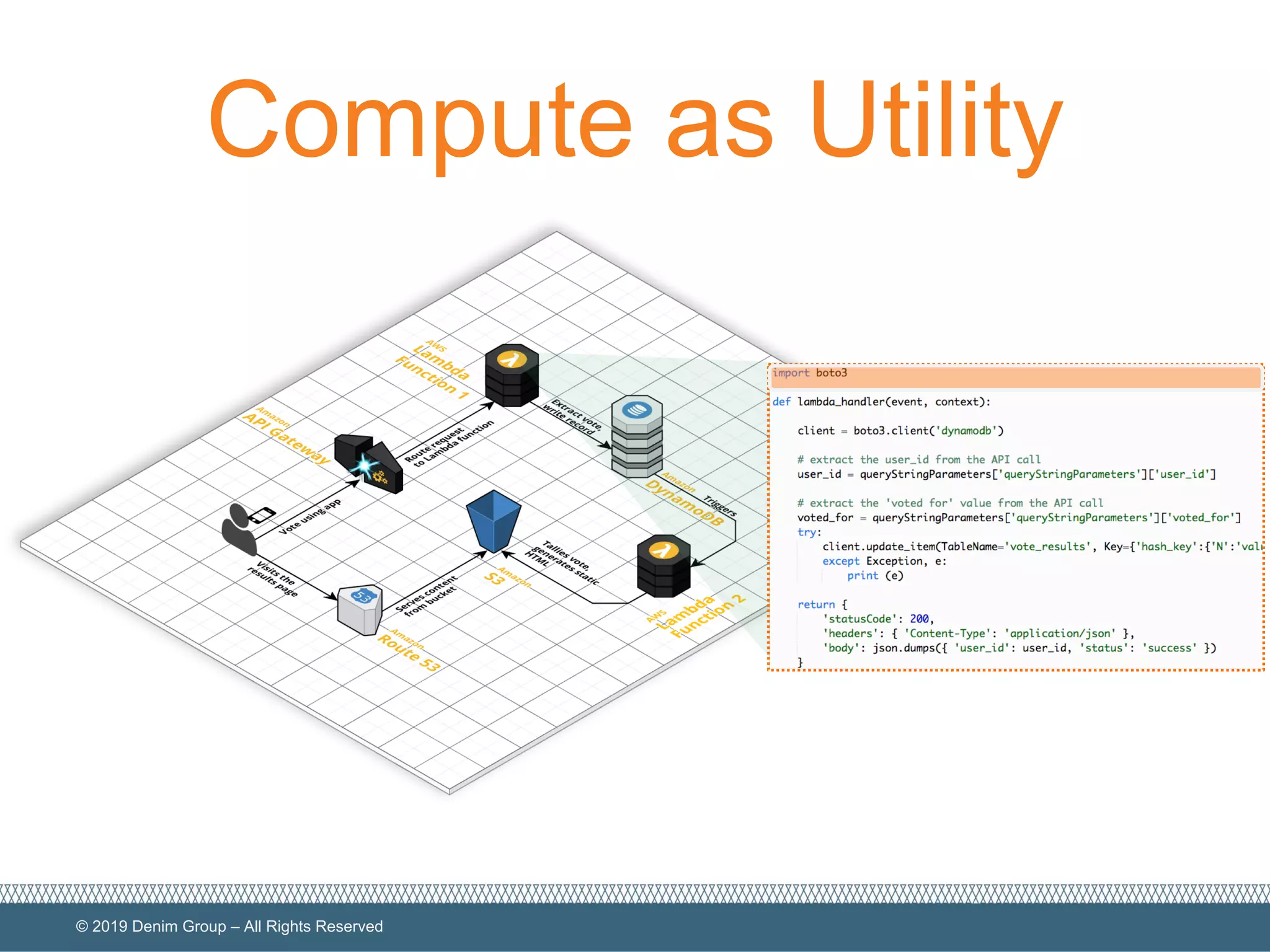
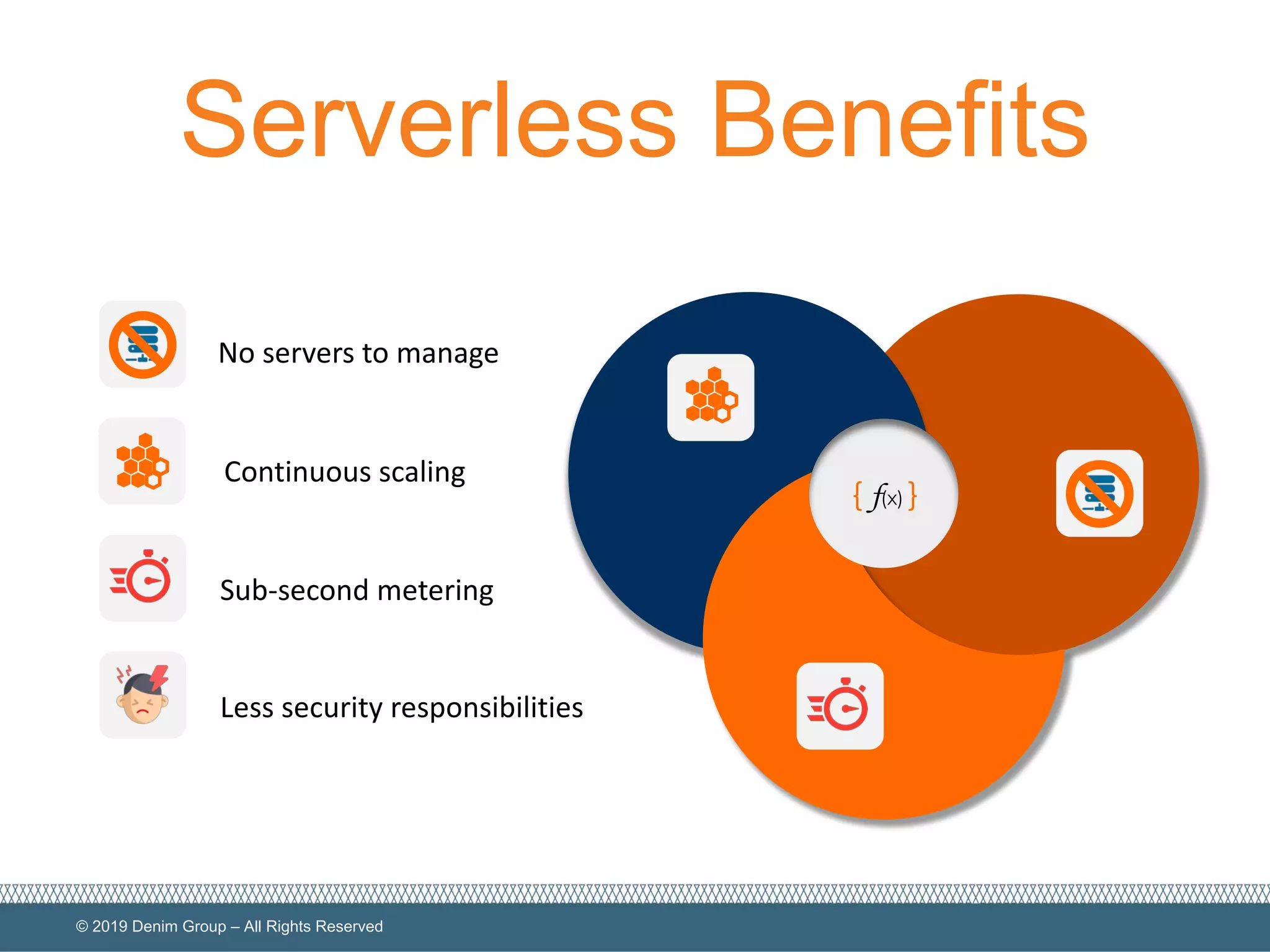
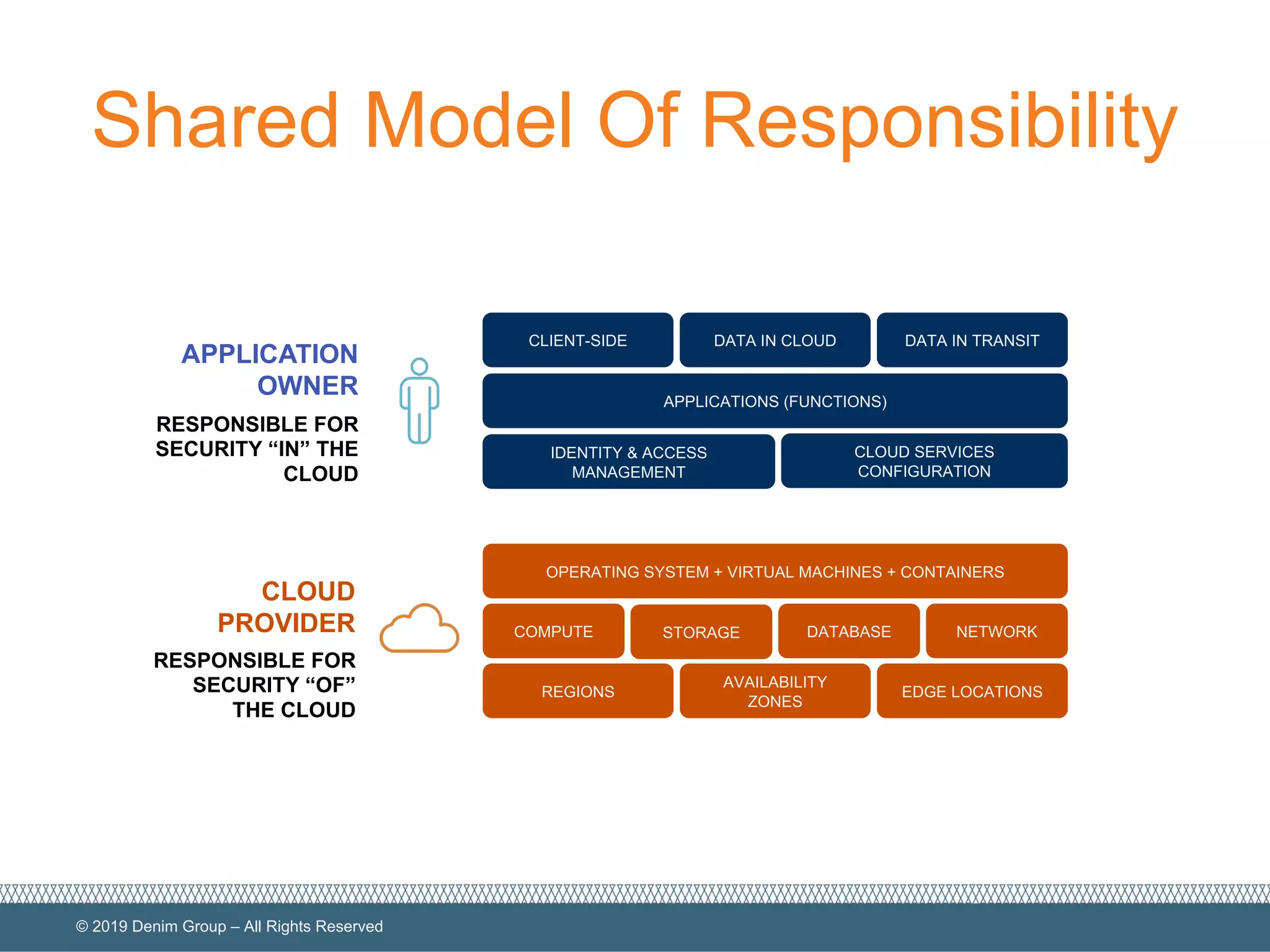
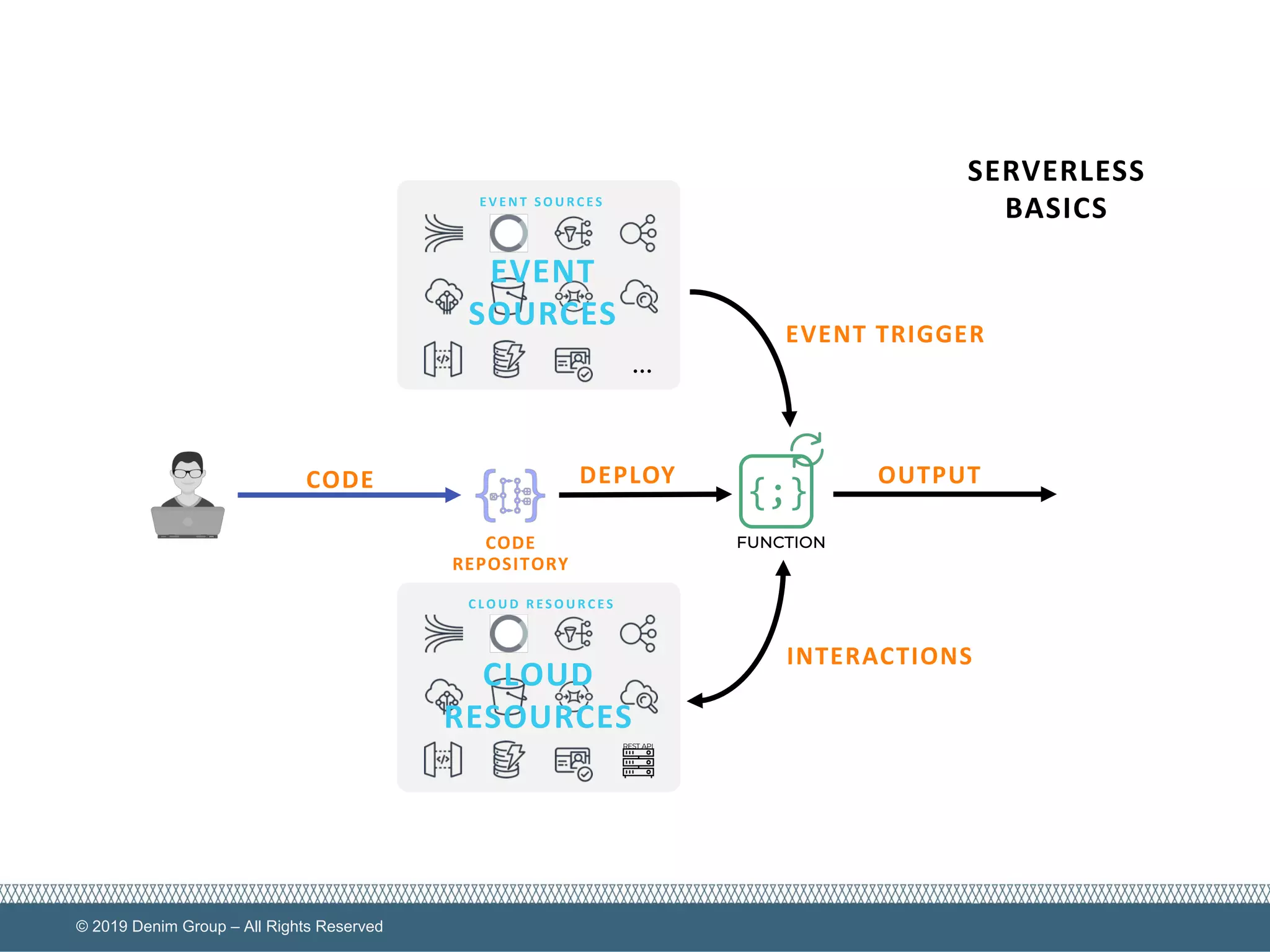
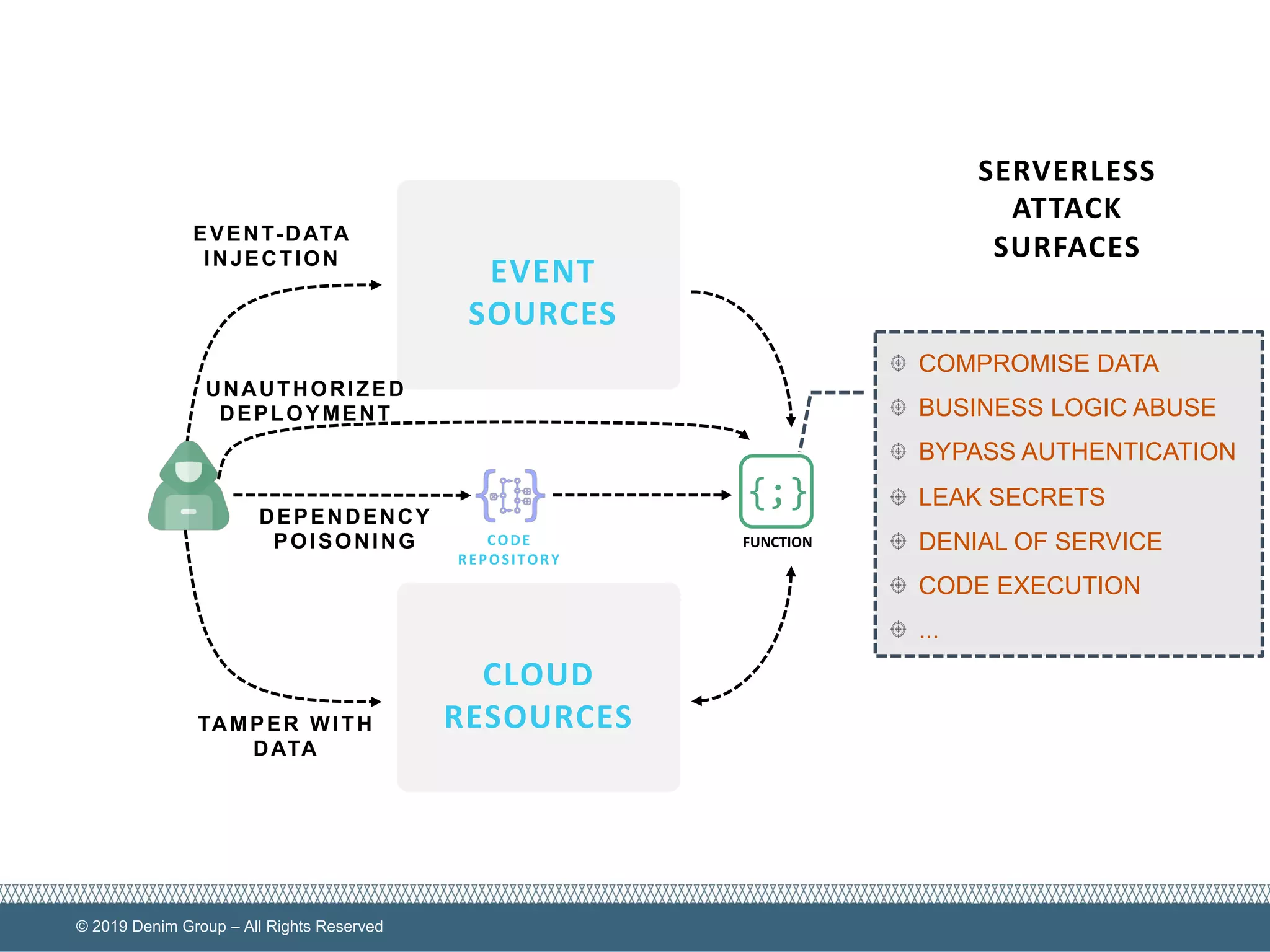
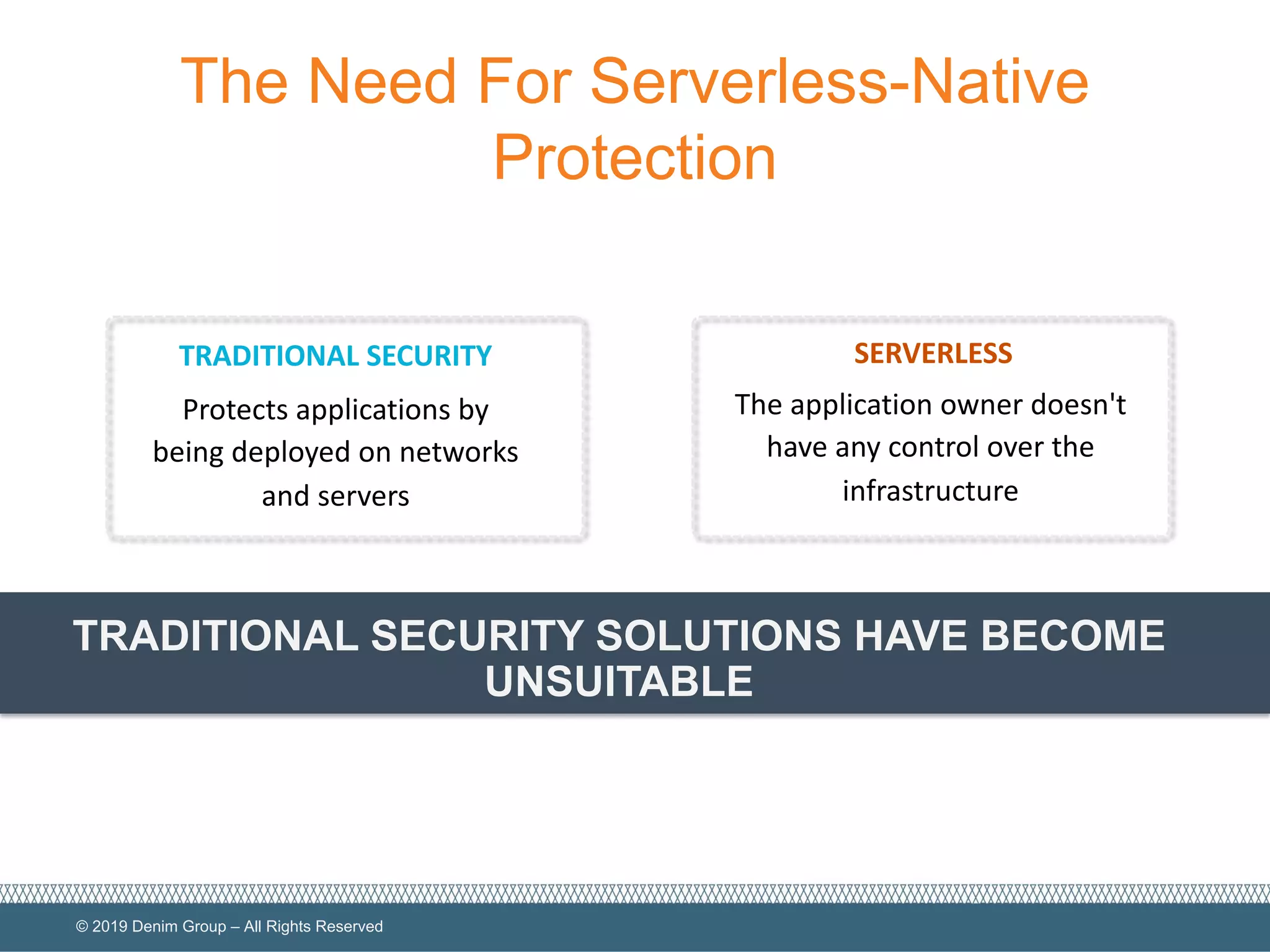
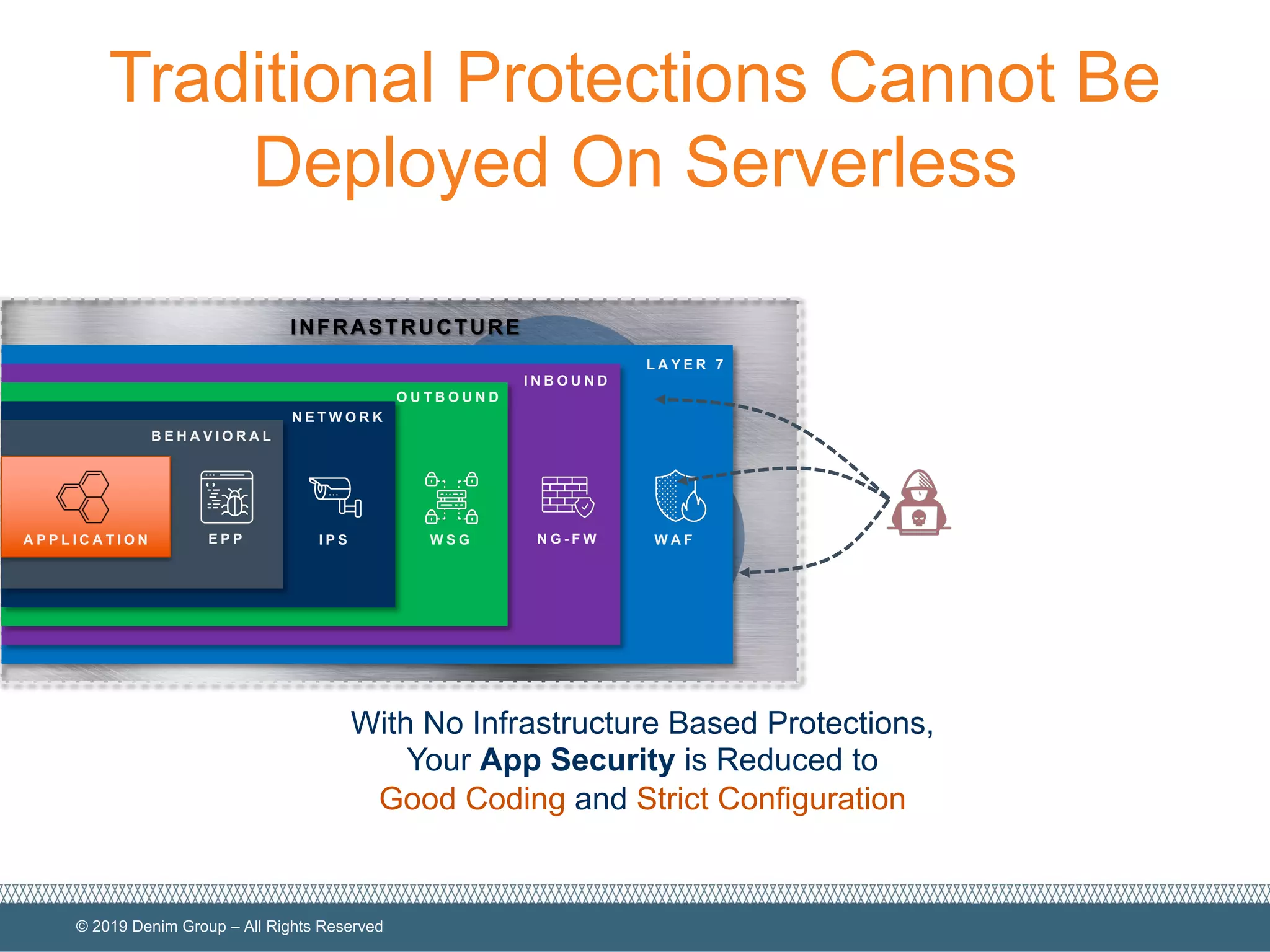
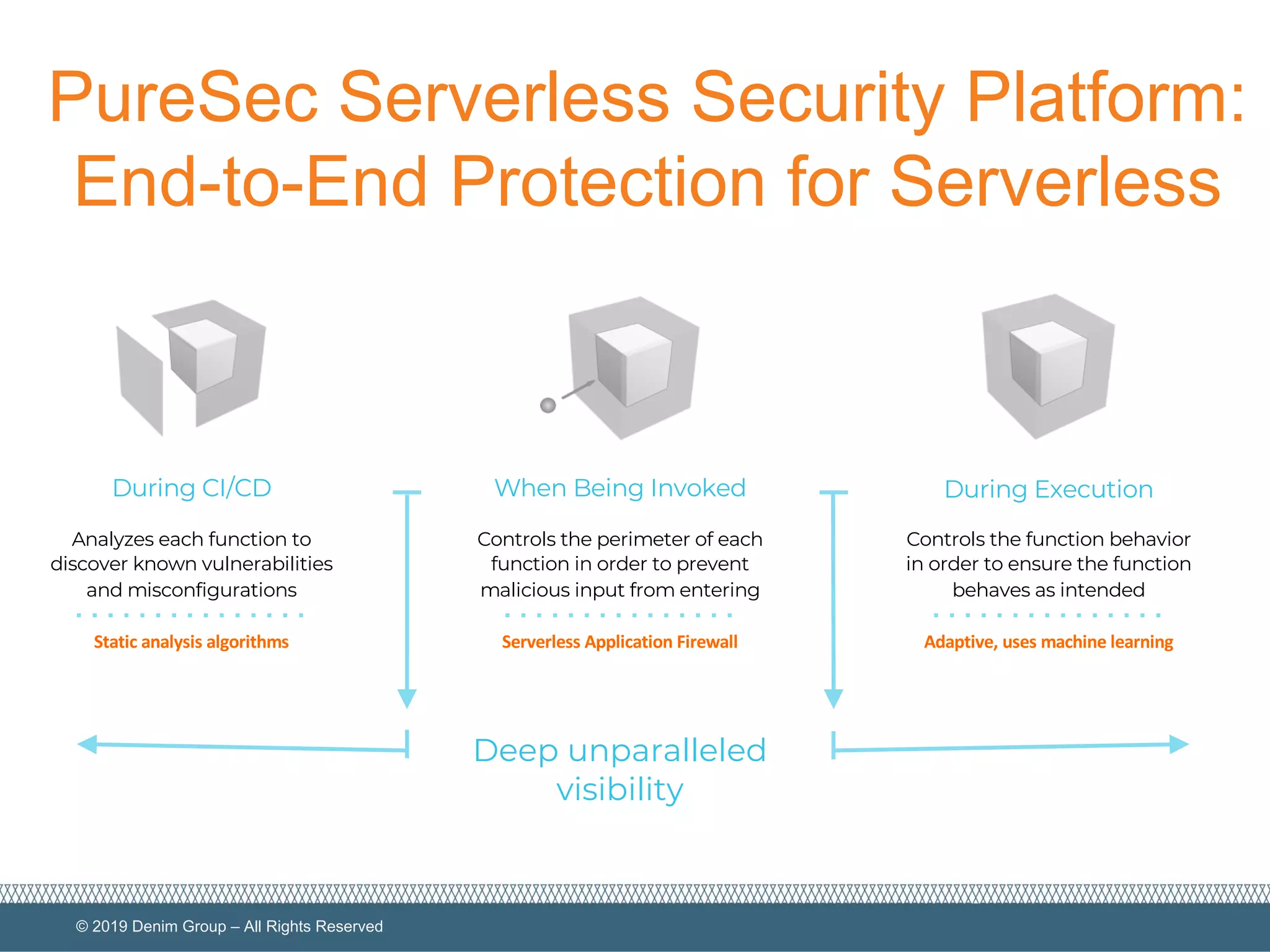
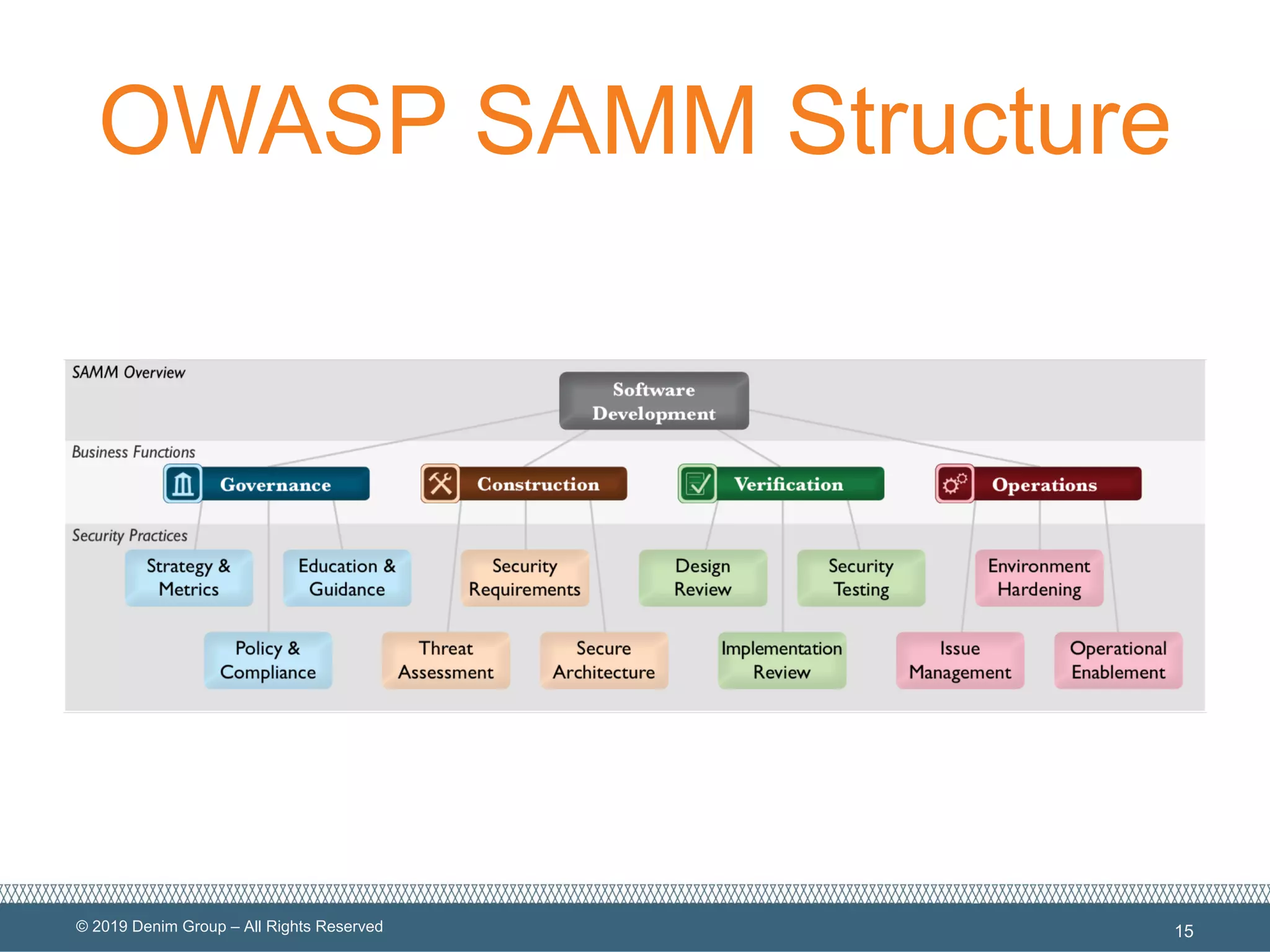
The document provides an overview of serverless computing security, highlighting the shared model of responsibility between cloud providers and application owners. It identifies top risks associated with serverless applications and emphasizes the need for serverless-native protection, as traditional security solutions are inadequate. Additionally, it discusses the integration of OWASP SAMM framework with serverless computing to enhance security governance, construction, verification, and operations.