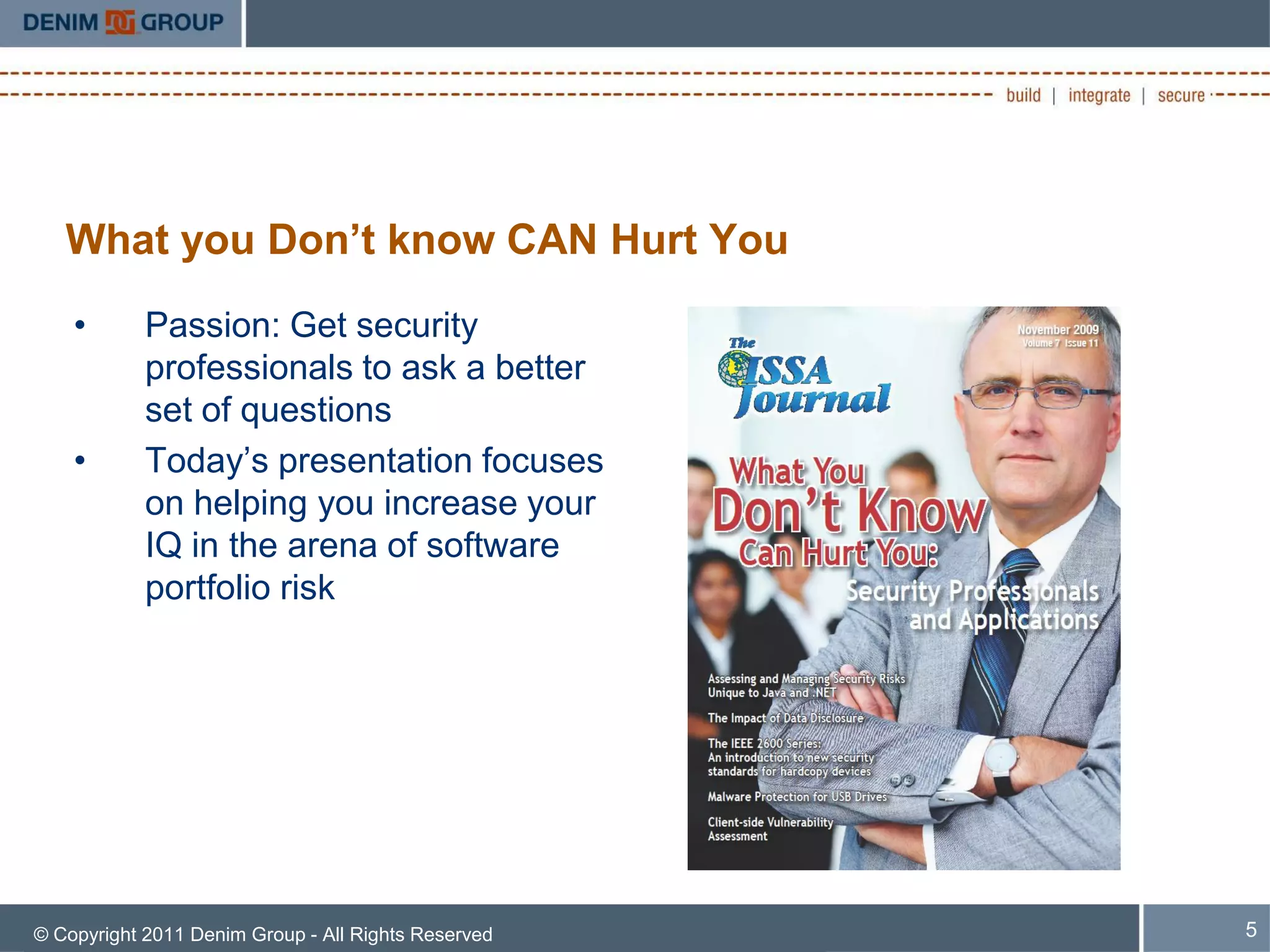
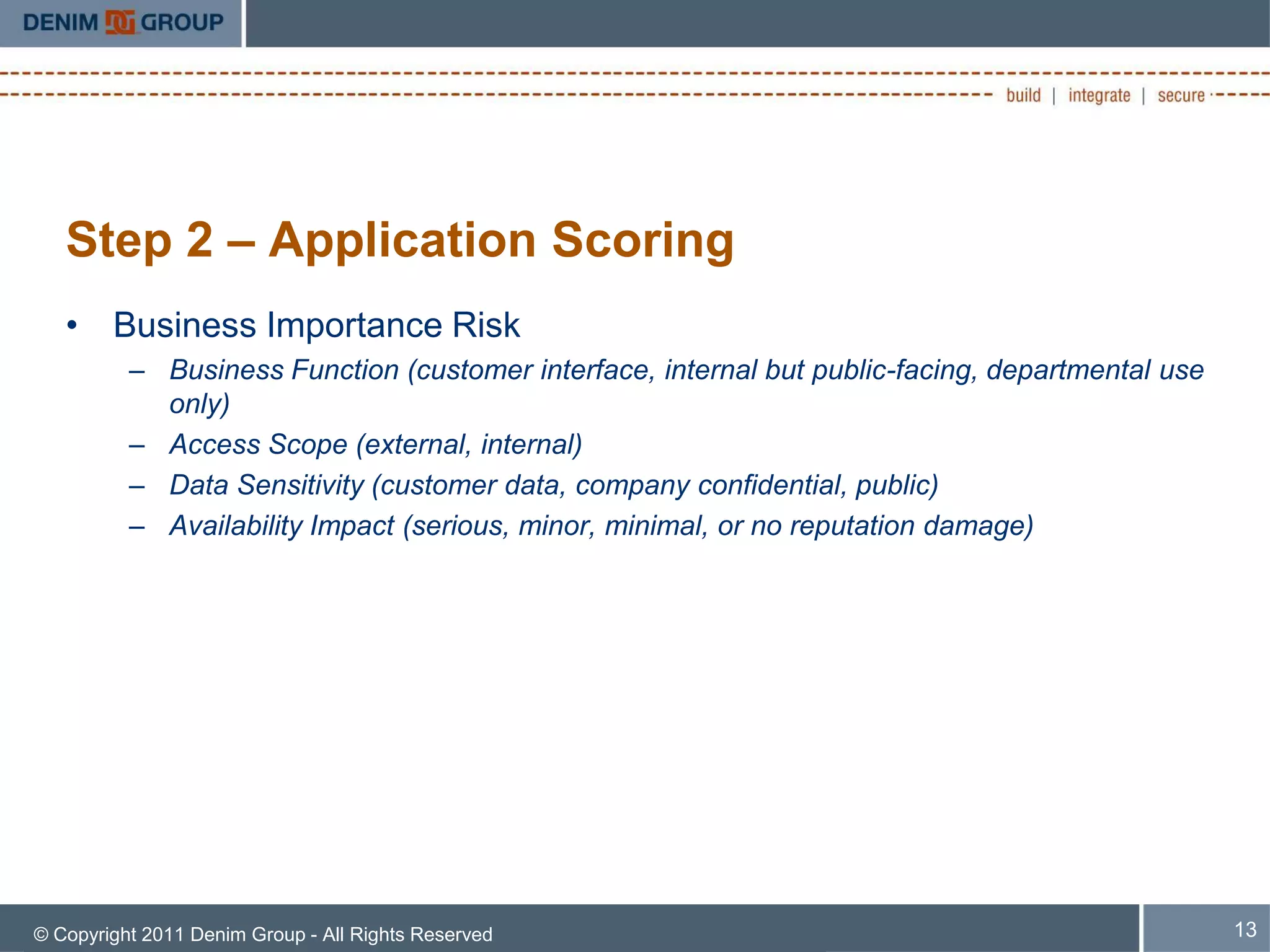
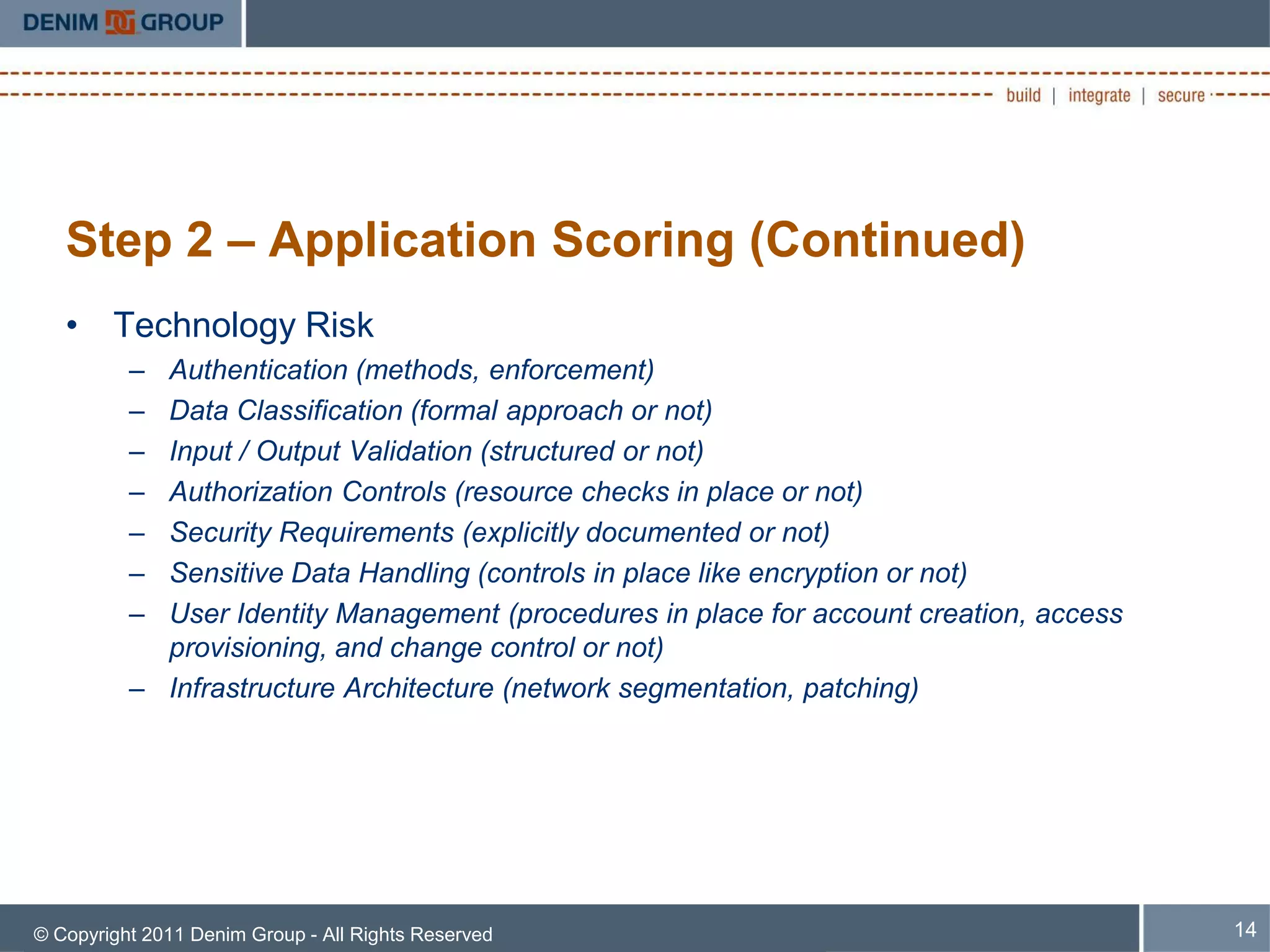
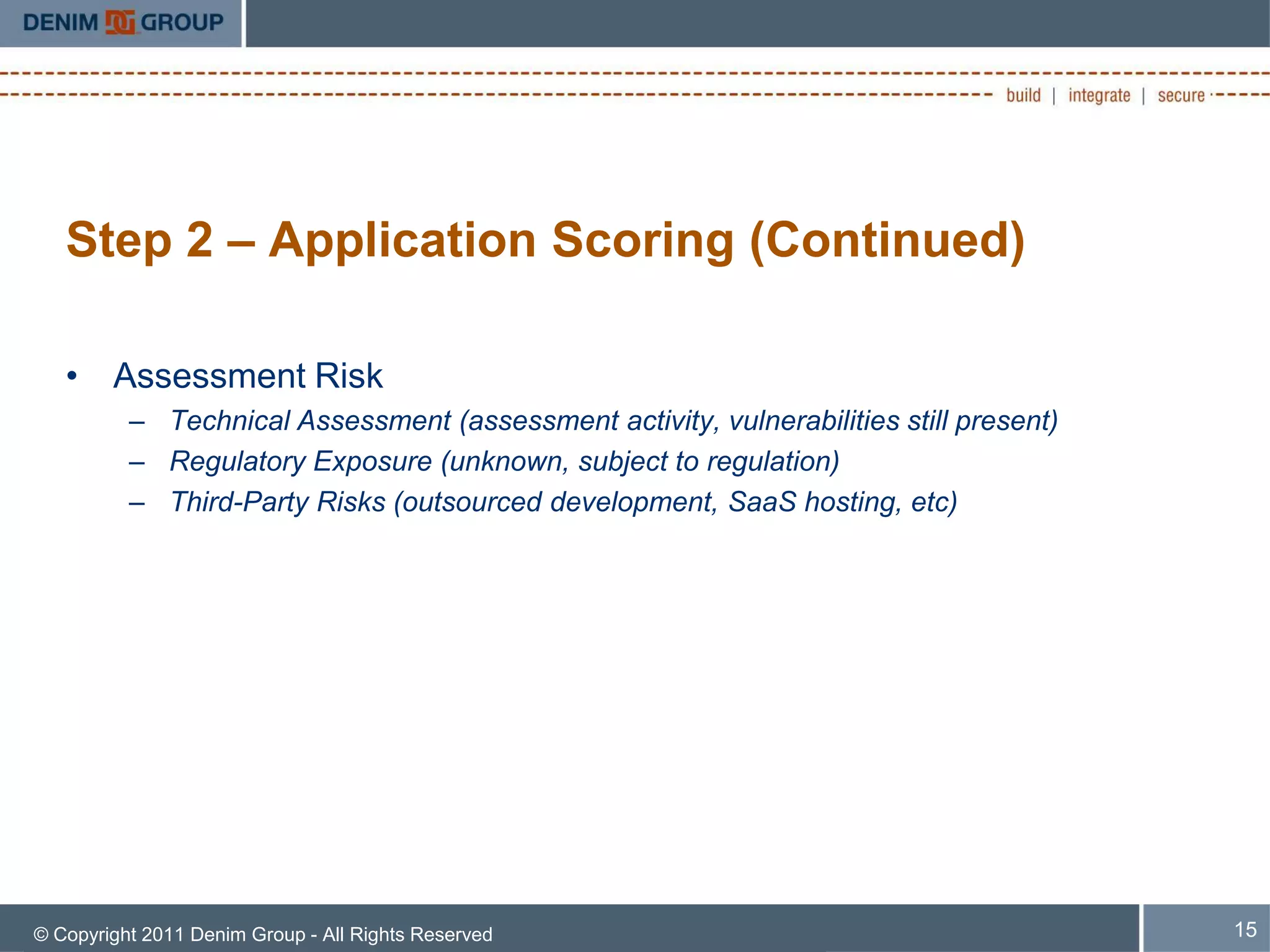
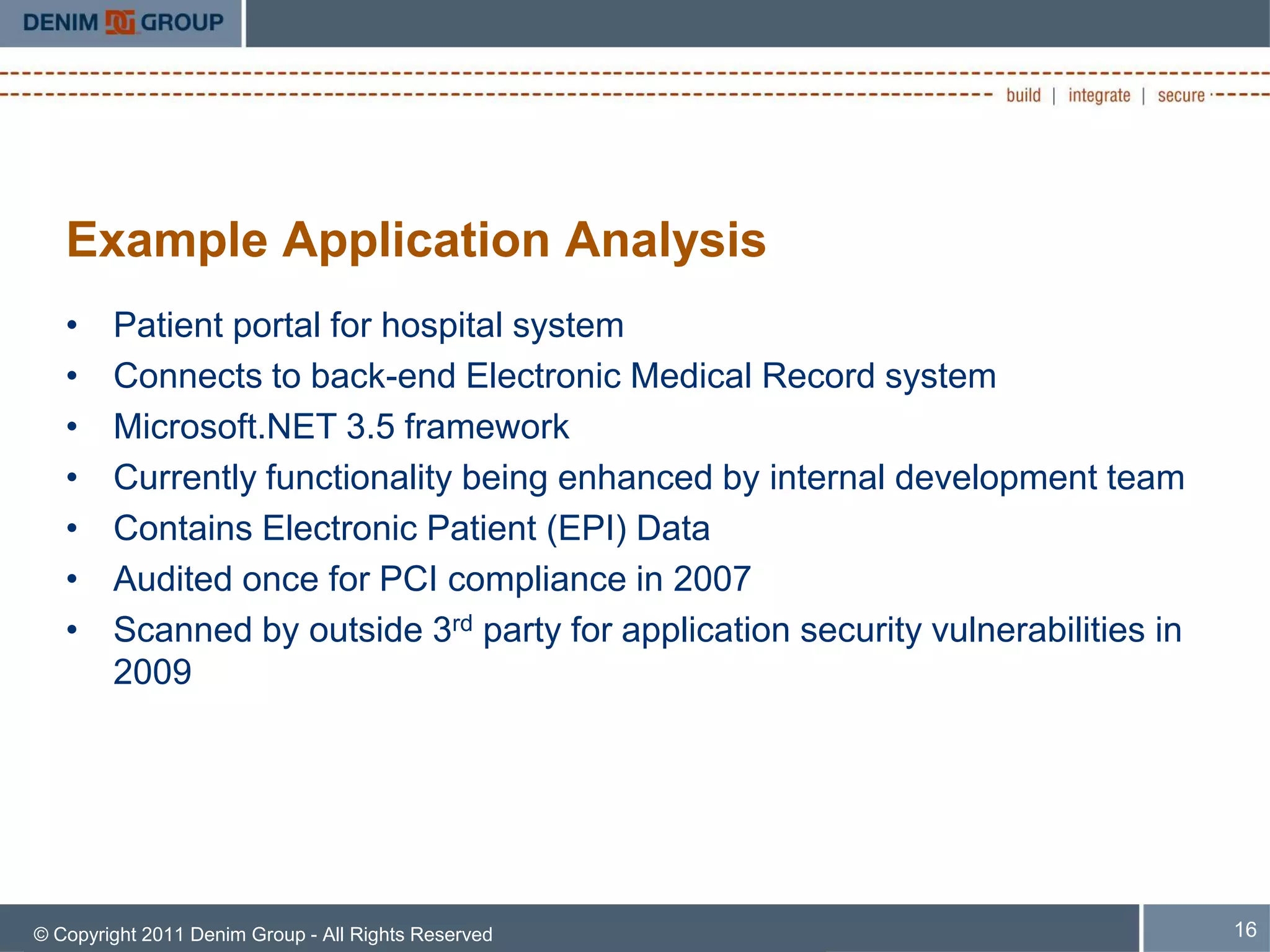
The document discusses managing the security of inherited applications, highlighting the need for a risk-based approach to identify and prioritize vulnerabilities in legacy software. It outlines steps for information gathering, application scoring, and risk analysis to assist organizations in understanding their software portfolio's security state. Key goals include enhancing decision-making in application security and applying learned tactics for better risk management.