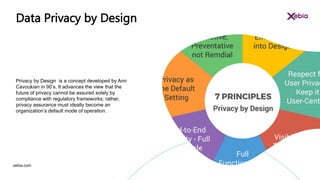
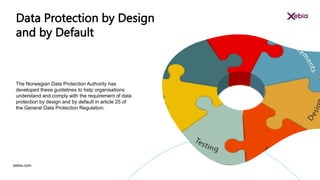
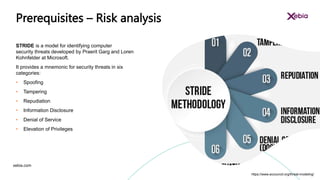
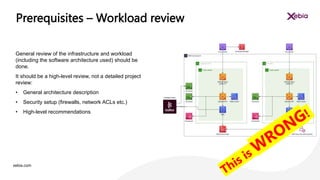
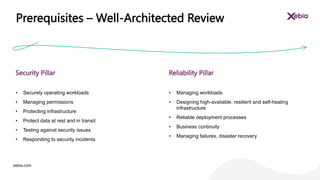
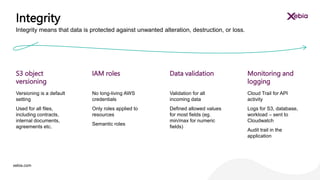
The document discusses the importance of designing for privacy in AWS cloud environments, emphasizing 'privacy by design' as a proactive approach to ensure data protection and compliance. It outlines key practices for implementing privacy measures, including secure coding, testing, and incident response planning. Additionally, it highlights the need for thorough documentation and periodic reviews to maintain security and reliability across cloud workloads.