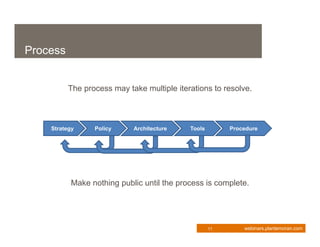
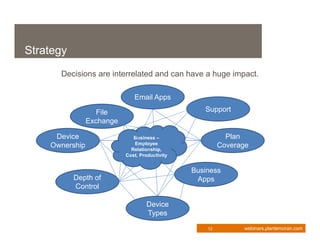
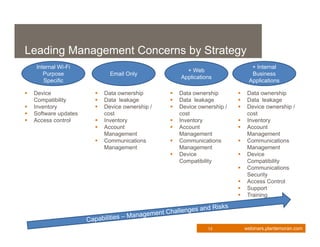
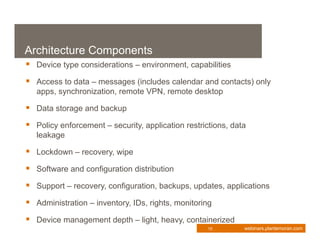
This document provides an overview of enterprise mobility management. It discusses the importance of developing a strategic approach and comprehensive plan for managing mobile devices, applications, and services. The presentation covers key considerations like device ownership, security best practices, and total cost of ownership. It also outlines the components of an effective mobility management process, including policy, architecture, tools, and procedures. Managing security risks associated with mobile access is a major focus. The webinar aims to help organizations transform their business through mobilization while maintaining appropriate controls.