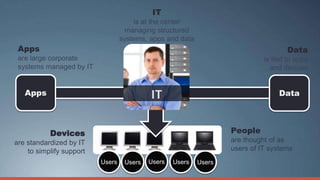
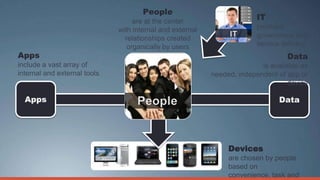
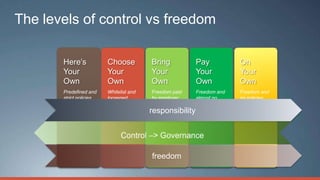
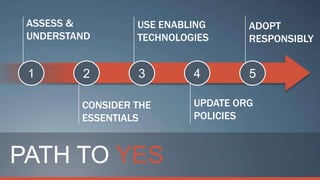
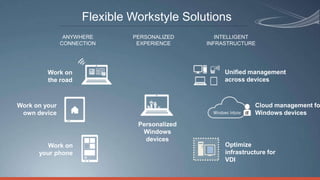
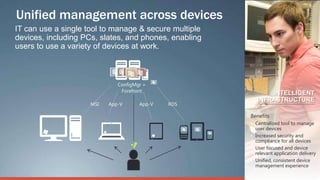
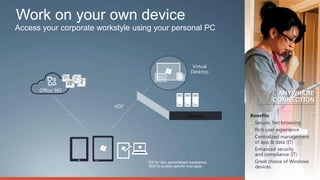
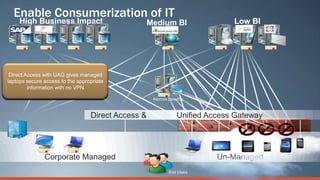
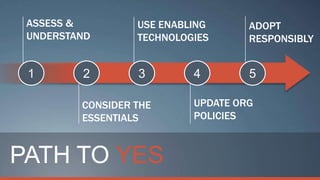
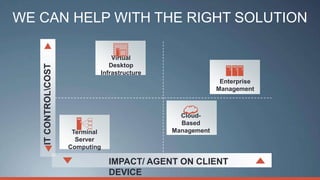
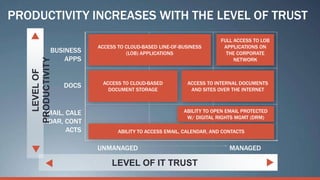
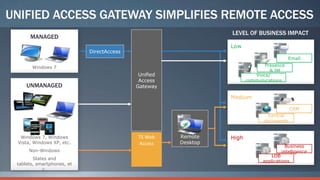
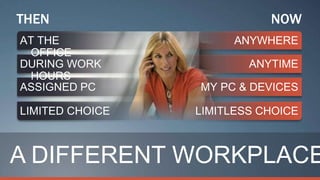
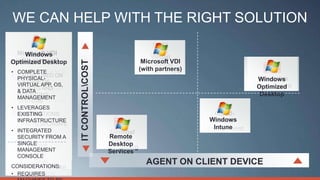
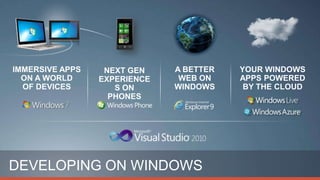
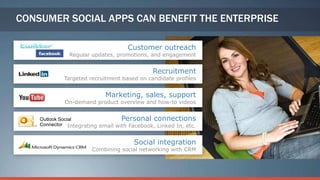
Consumerization refers to the trend of bringing consumer technologies into the workplace. As technology has become more mobile and apps have proliferated, the traditional model of IT tightly controlling all devices and apps is breaking down. Users now expect to use their own devices and apps for work. The document discusses how IT can embrace this trend by assessing user needs and behaviors, enabling technologies like virtualization and cloud computing, and updating policies to balance user choice with security and manageability. The goal is to empower users while still providing governance and service delivery. Microsoft offers solutions to help organizations adopt consumerization responsibly and drive business value.