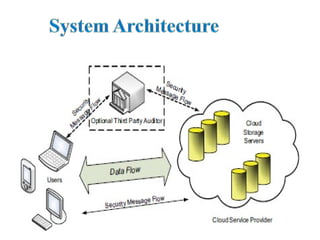
Cloud computing moves application software and databases to large data centers where management may not be fully trustworthy, posing security challenges. The article focuses on cloud data storage security and proposes a scheme using erasure-coded data with distributed verification and error localization to identify misbehaving servers. Unlike prior works, the scheme supports secure dynamic operations like update, delete and append. Extensive analysis shows it efficiently protects against attacks while supporting data dependencies and dynamics.