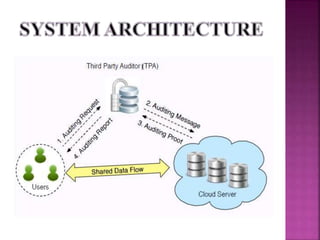
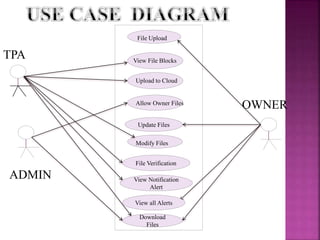
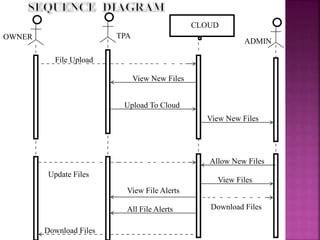
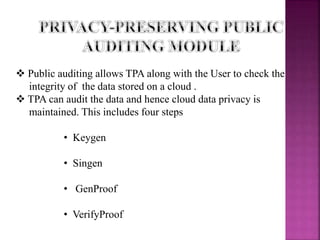
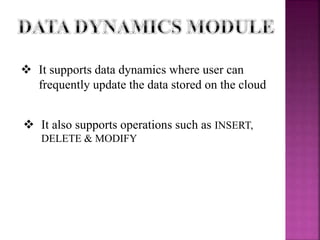
This document discusses privacy-preserving public auditing for shared data stored in the cloud. It proposes a mechanism called ORUTA that allows a third party auditor (TPA) to efficiently audit the integrity of shared data in the cloud while preserving the identity privacy of users. The mechanism has two phases - a setup phase and an audit phase. It also supports batch auditing which allows the TPA to concurrently handle multiple auditing tasks, improving efficiency. The mechanism further extends to allow for dynamic operations like insert, delete and modify on the outsourced data.