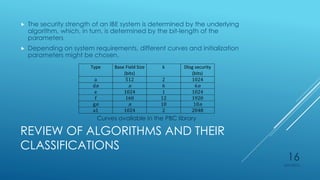
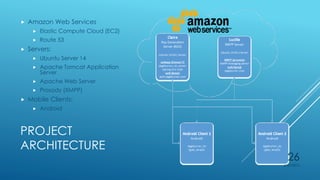
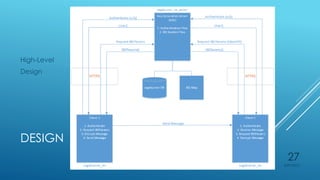
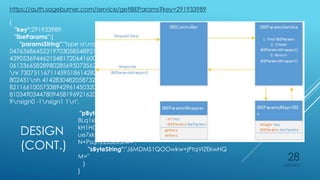
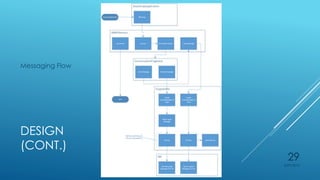
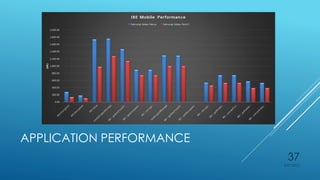
Ryan Holt presents a master's thesis on developing a secure mobile messaging application using identity-based encryption. The presentation includes an introduction outlining privacy and security concerns with existing messaging apps and cloud services. It then covers the background concepts of identity-based encryption, elliptic curve cryptography, and the PBC library. Finally, it details the design, implementation, and user experience of the proof-of-concept mobile messaging app created for the thesis project.