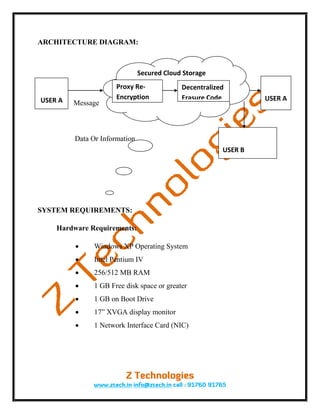
The document proposes a secure cloud storage system that uses a threshold proxy re-encryption scheme integrated with a decentralized erasure code. This allows the system to securely store and retrieve data, as well as securely forward data from one user to another without retrieving it directly. The system addresses limitations of traditional encryption for cloud storage by distributing keys and enabling storage servers to directly forward encrypted data between users.