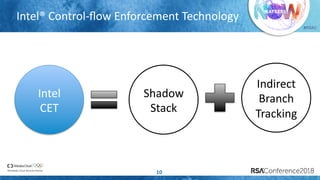
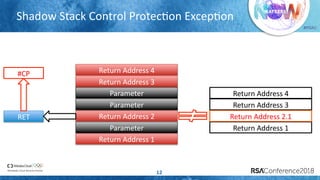
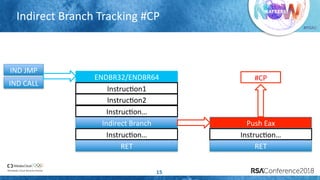
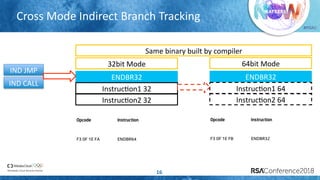
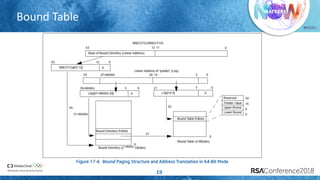
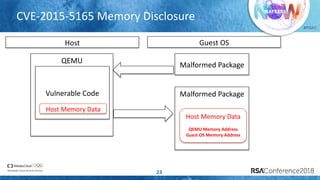
The document discusses enhancing virtualization security using Intel's Control-flow Enforcement Technology (CET) and Memory Protection Extensions (MPX) in the context of a full virtualization stack. It highlights vulnerabilities in QEMU, including specific CVEs, and presents a case study on VM escape exploits. The document concludes with recommendations for improving security measures against these vulnerabilities in cloud environments.



![#RSAC
Why Device EmulaLon?
4
Supports more guest devices with virtual devices
If physical devices number are not enough - limited GPU resource
If physical devices don’t support device virtualizaLon – Not every device
support SRIOV
If physical devices don’t exist – some outdated devices
Popular usage in cloud environment to support many VMs
QEMU can provide device emulaLon for KVM/XEN, but it brings new
a]ack surface on virtualizaLon stack](https://image.slidesharecdn.com/hta-f01enhancevirtualizationstackwithintelcetandmpx-180611061212/85/Enhance-Virtualization-Stack-with-Intel-CET-and-MPX-4-320.jpg)



















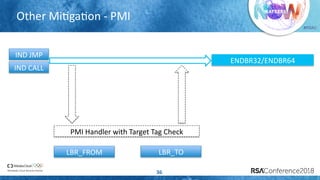
![#RSAC
CVE-2015-7504 – Out of Bound Read Defense
with MPX
31
Enable MPX on buffer[4096] memory access](https://image.slidesharecdn.com/hta-f01enhancevirtualizationstackwithintelcetandmpx-180611061212/85/Enhance-Virtualization-Stack-with-Intel-CET-and-MPX-31-320.jpg)