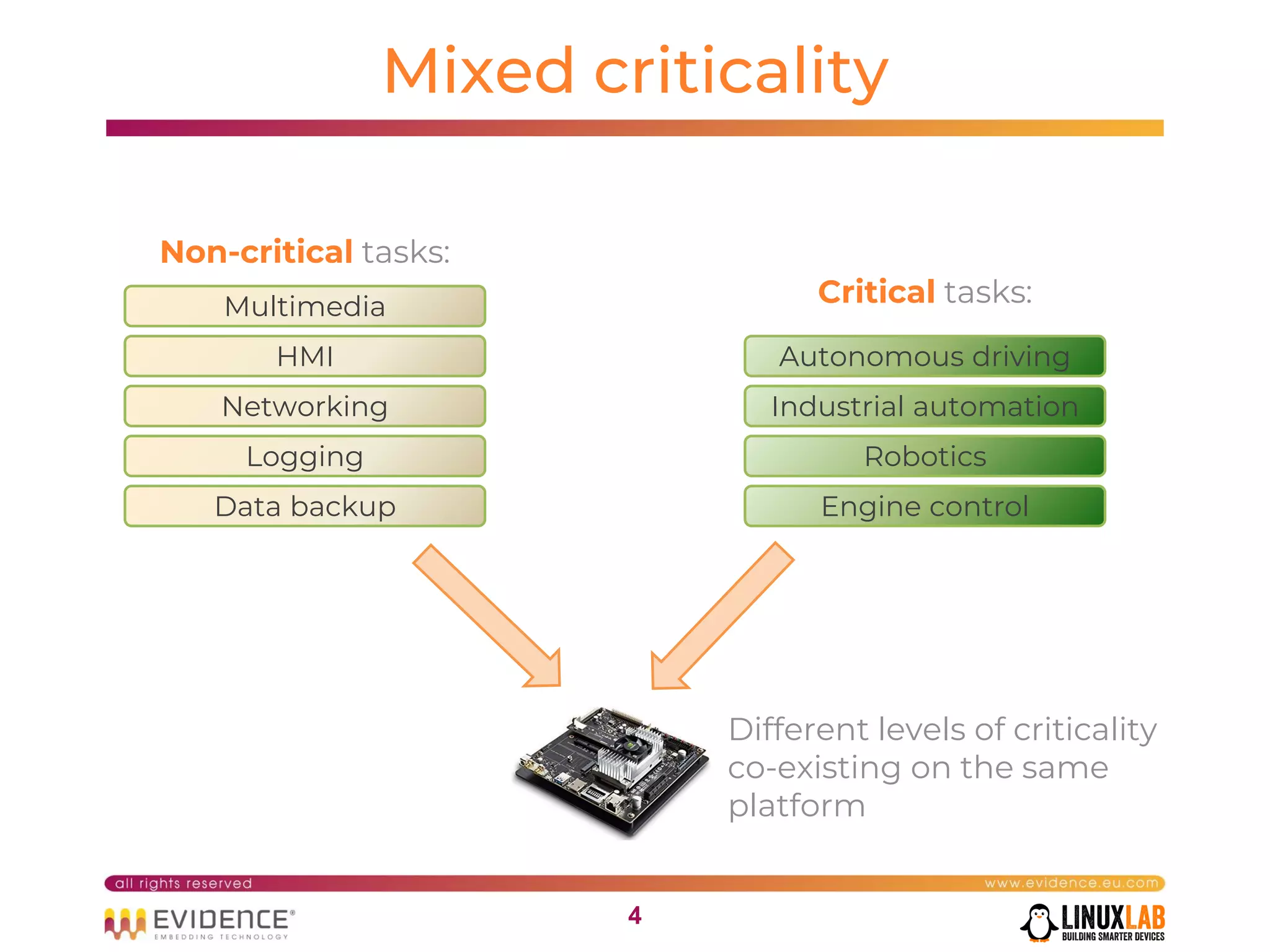
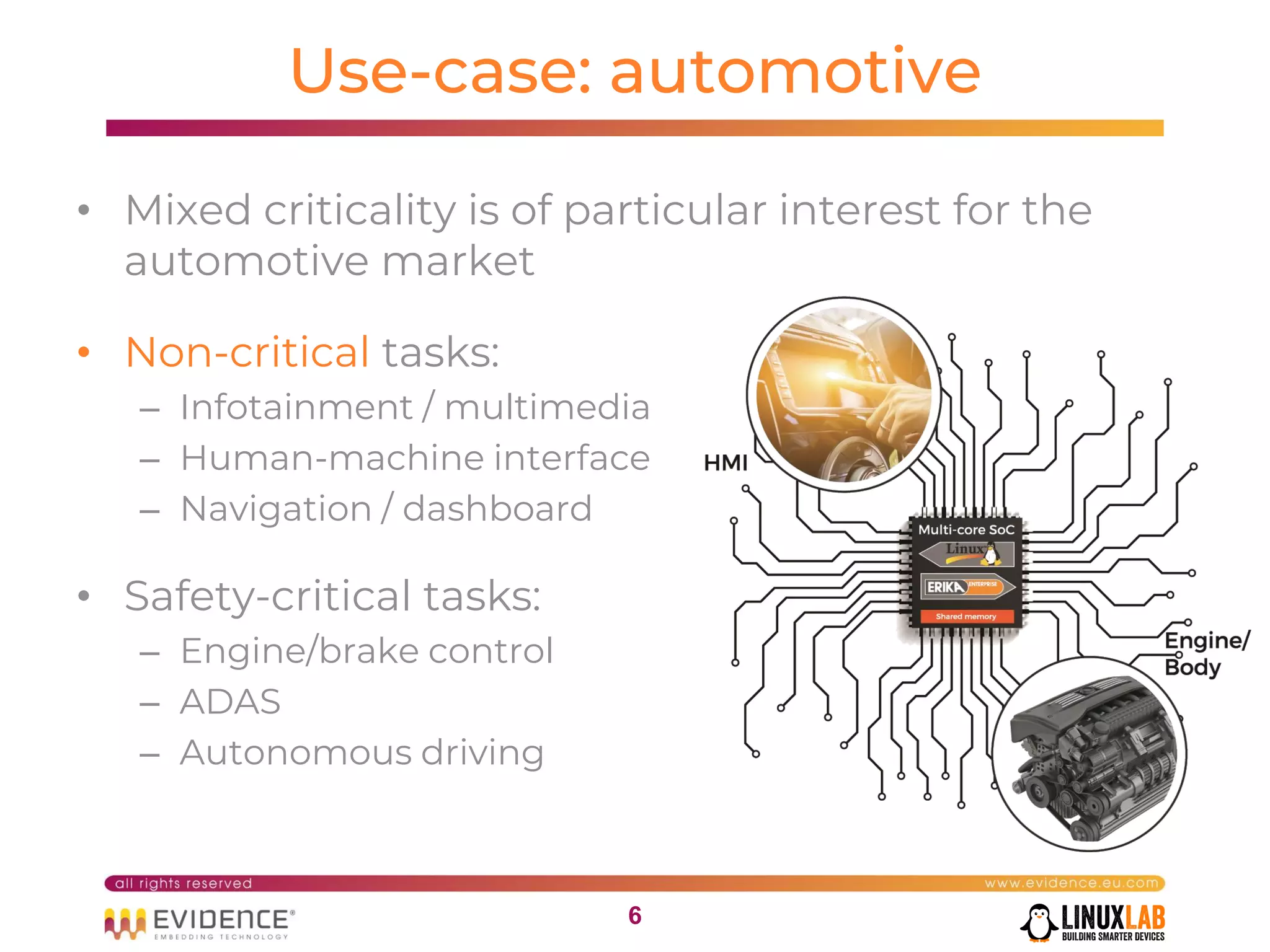
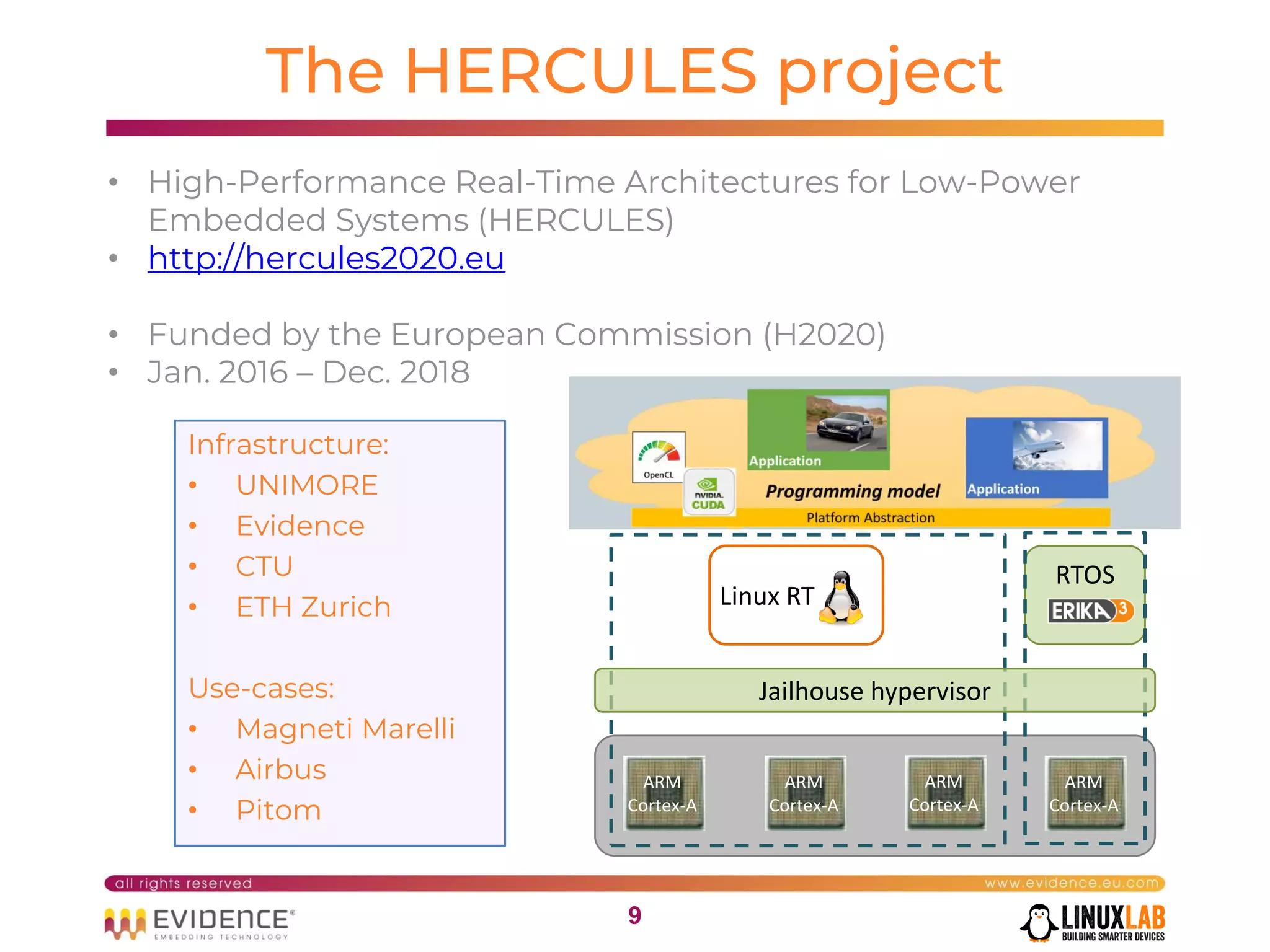
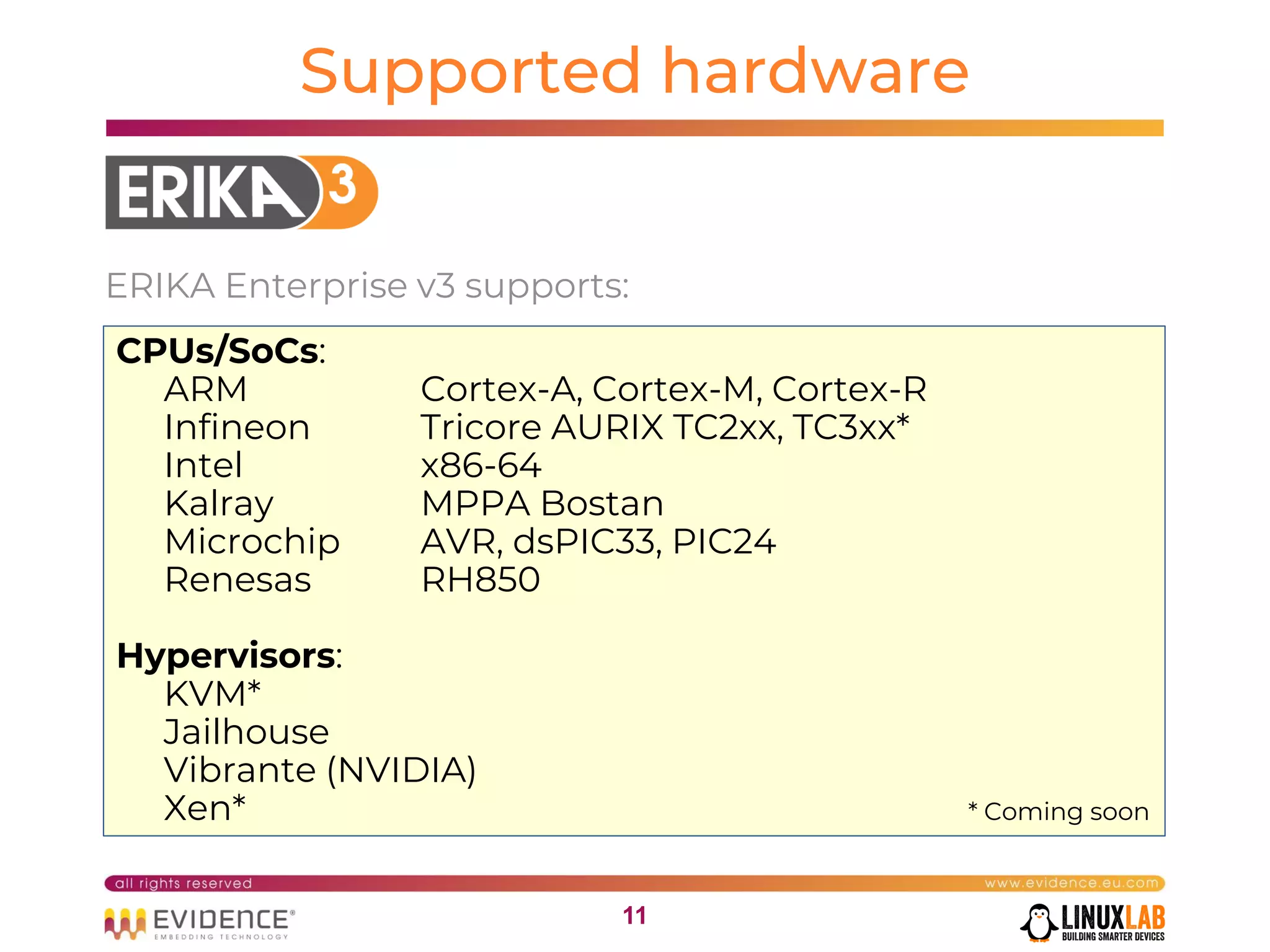
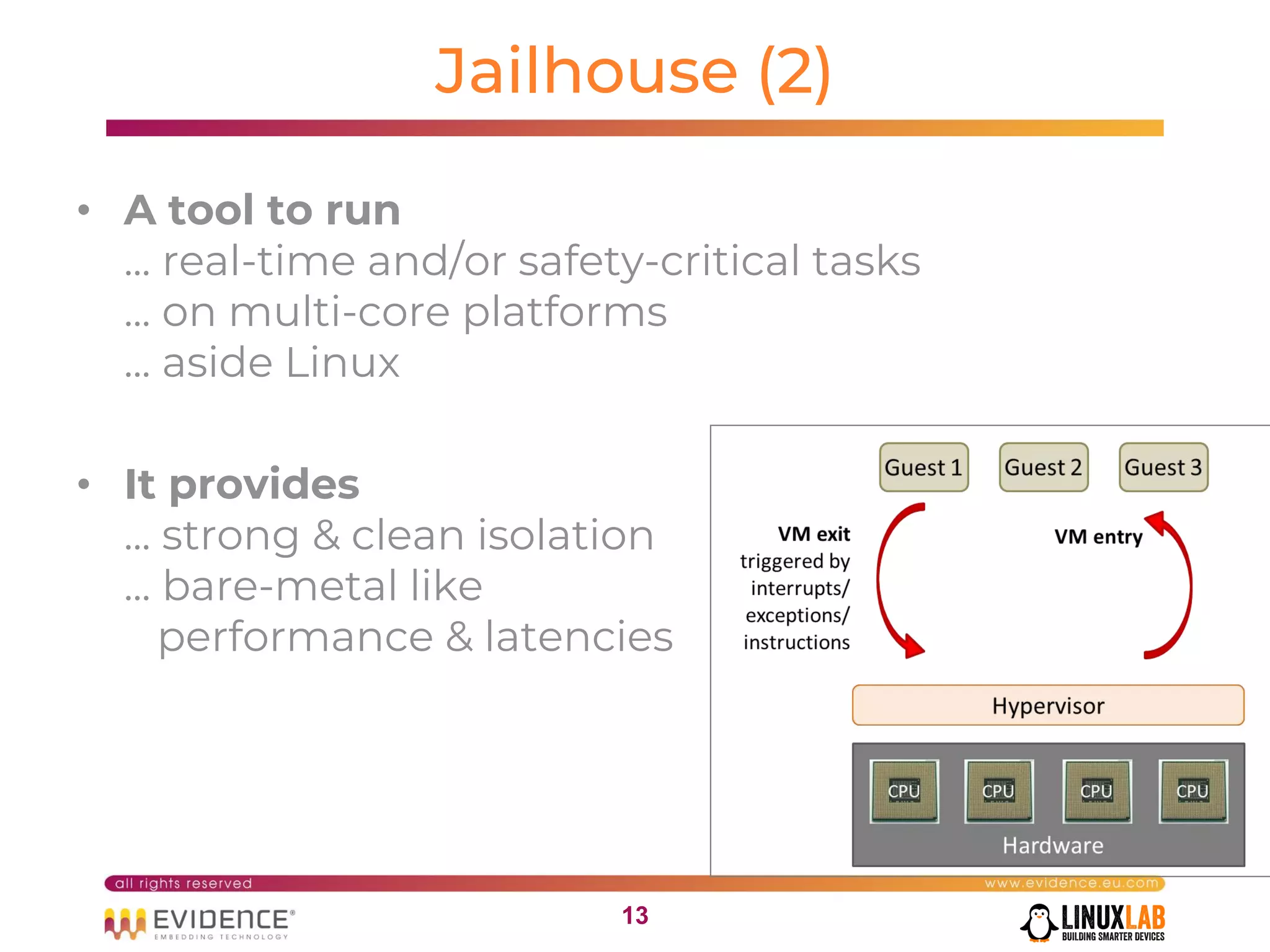
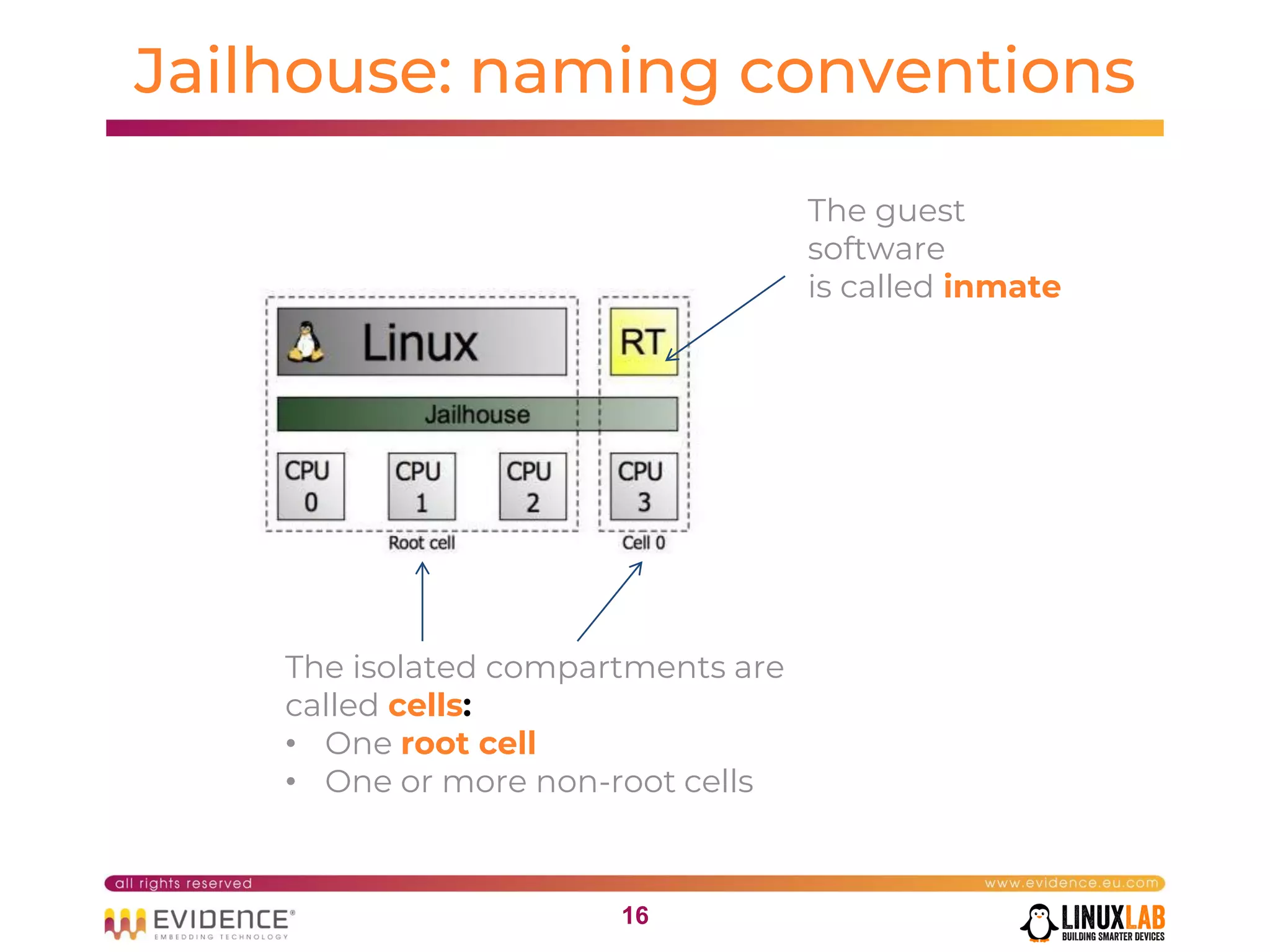
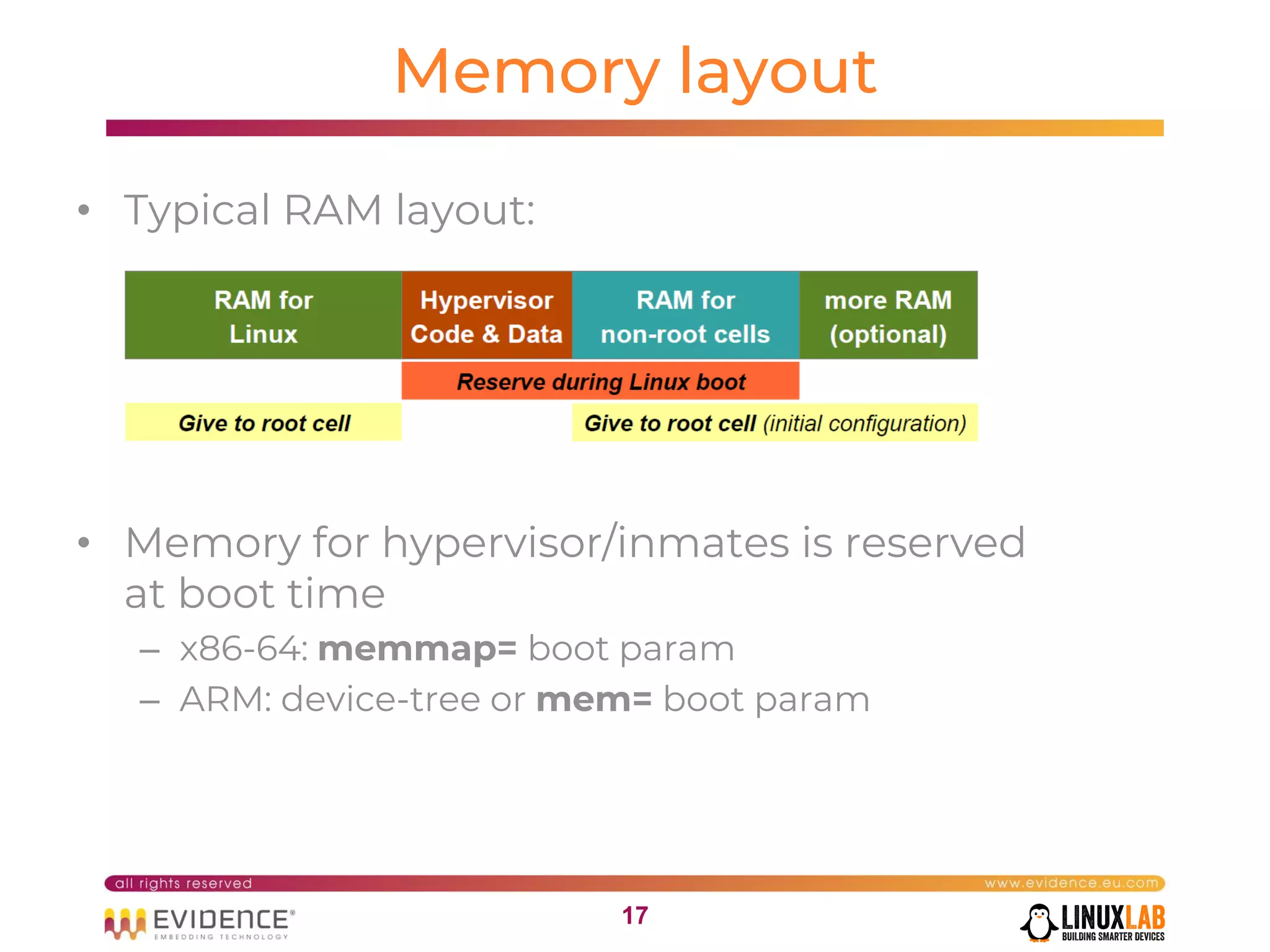
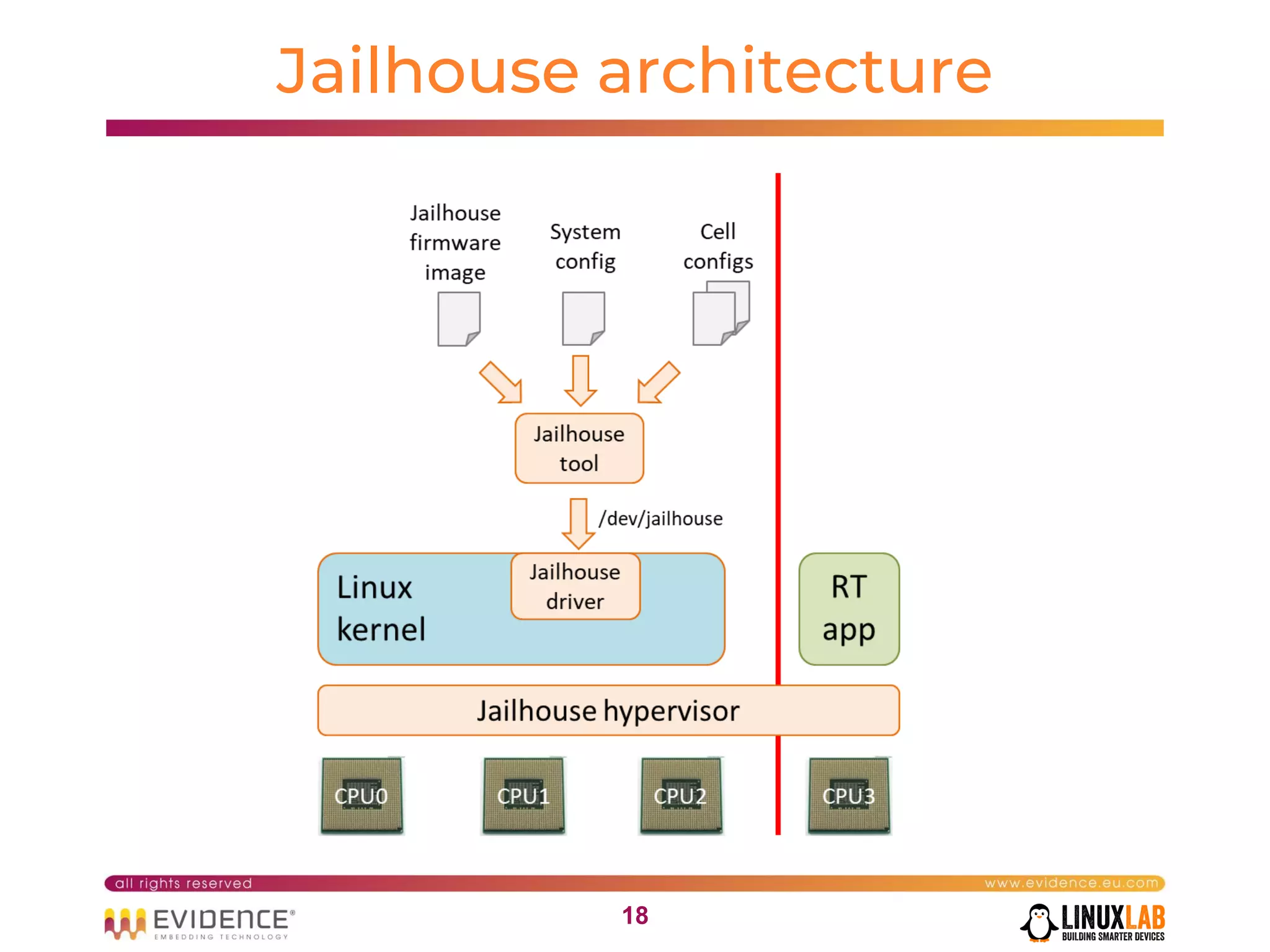
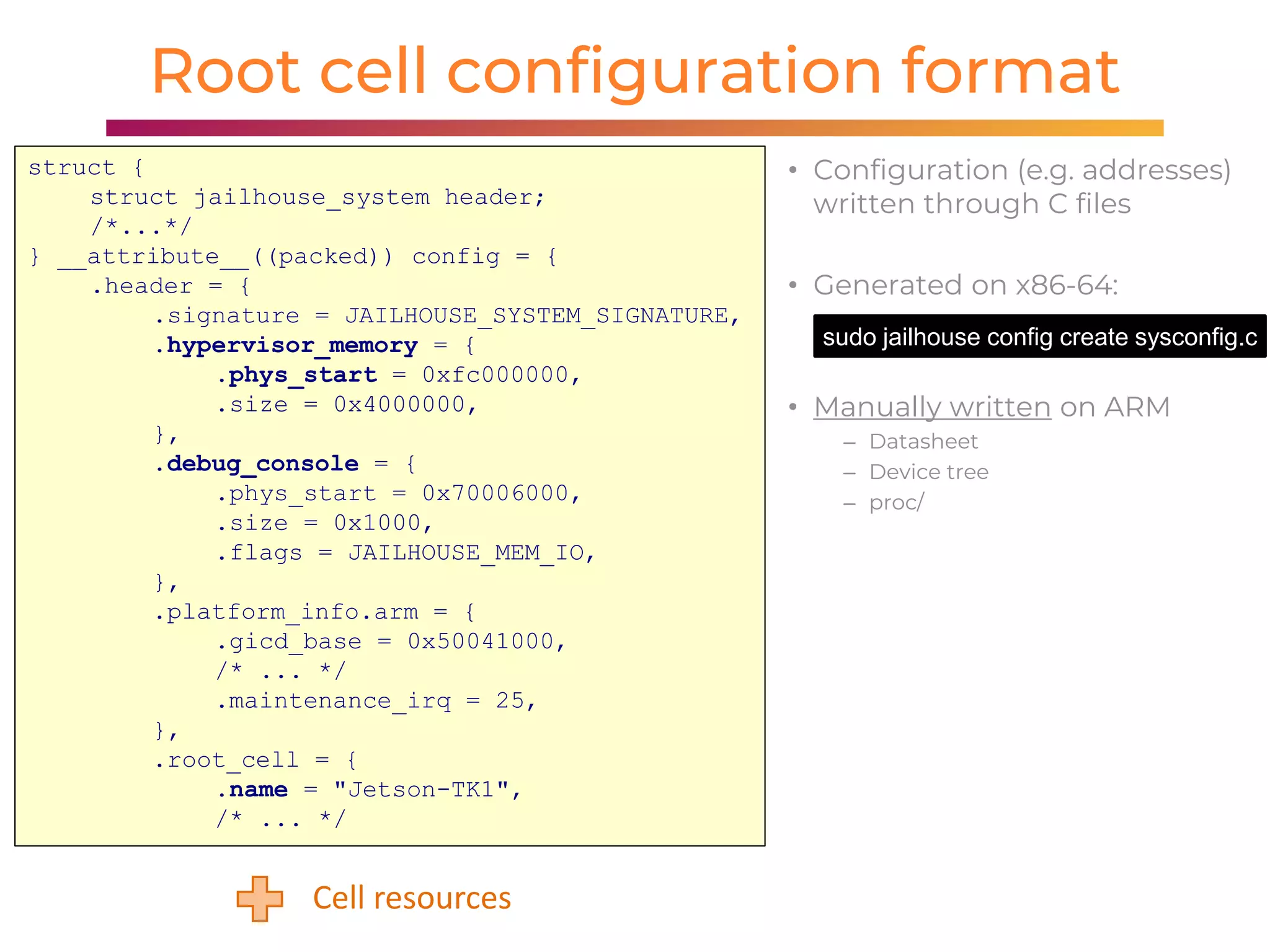
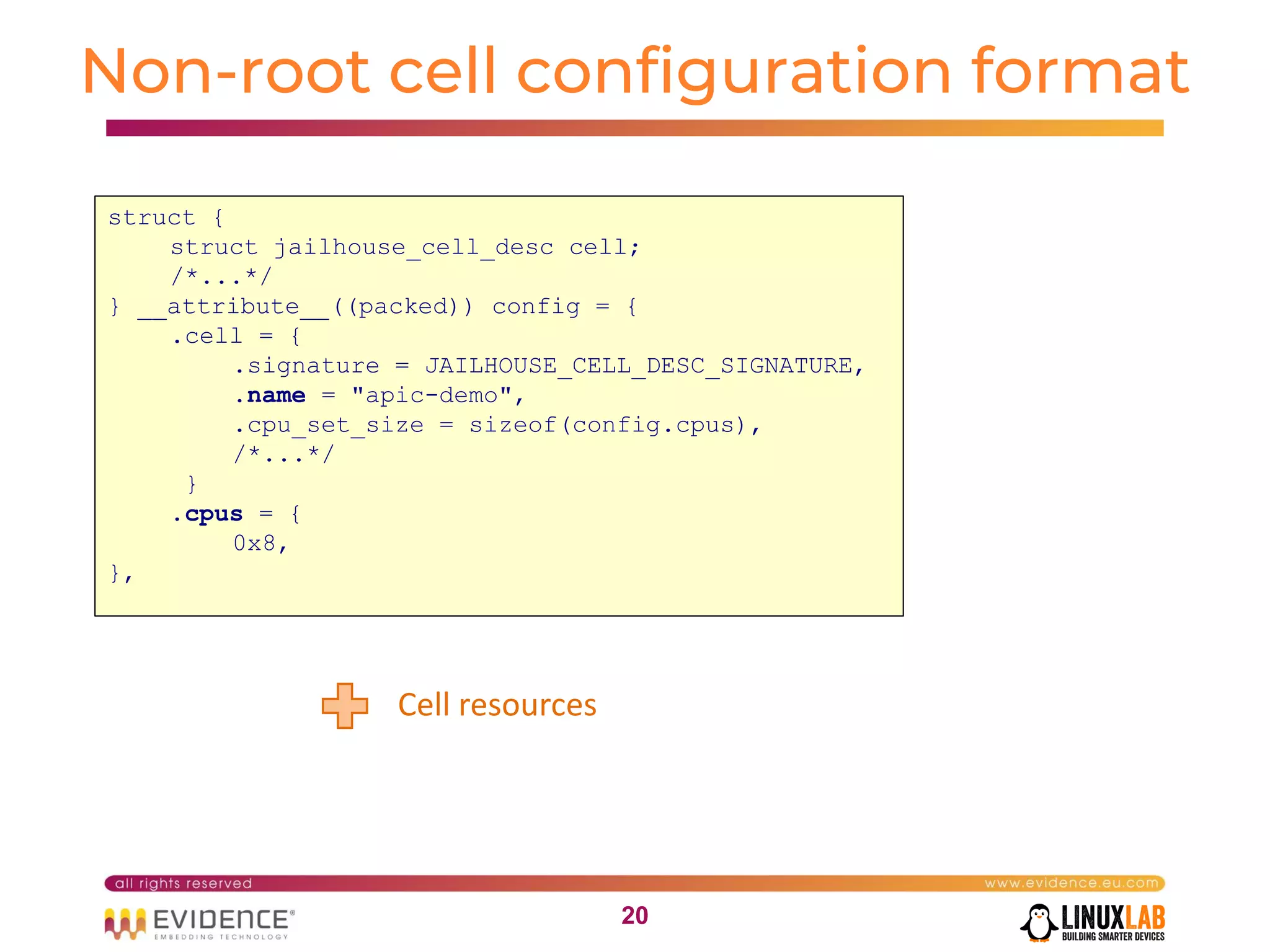
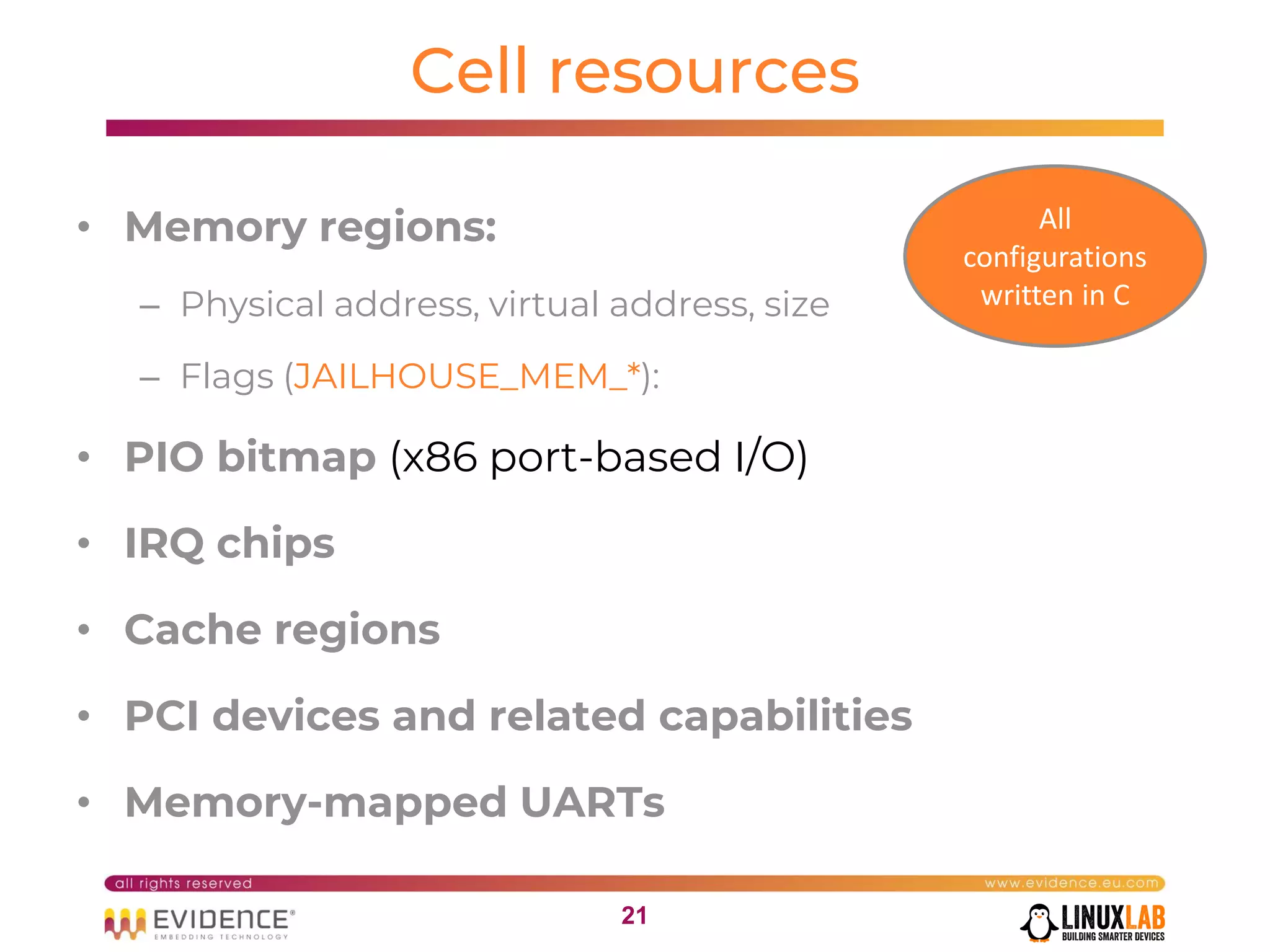
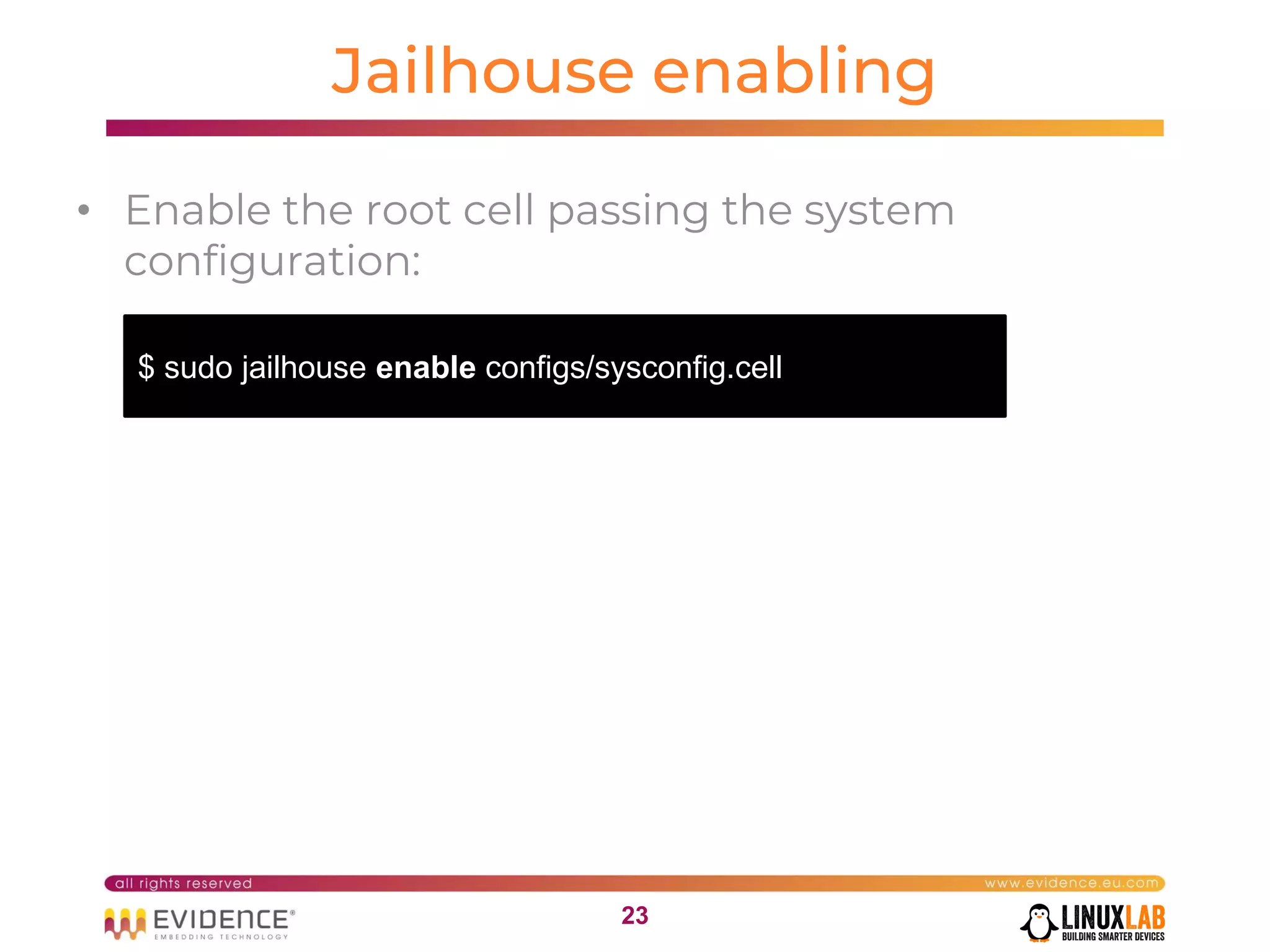
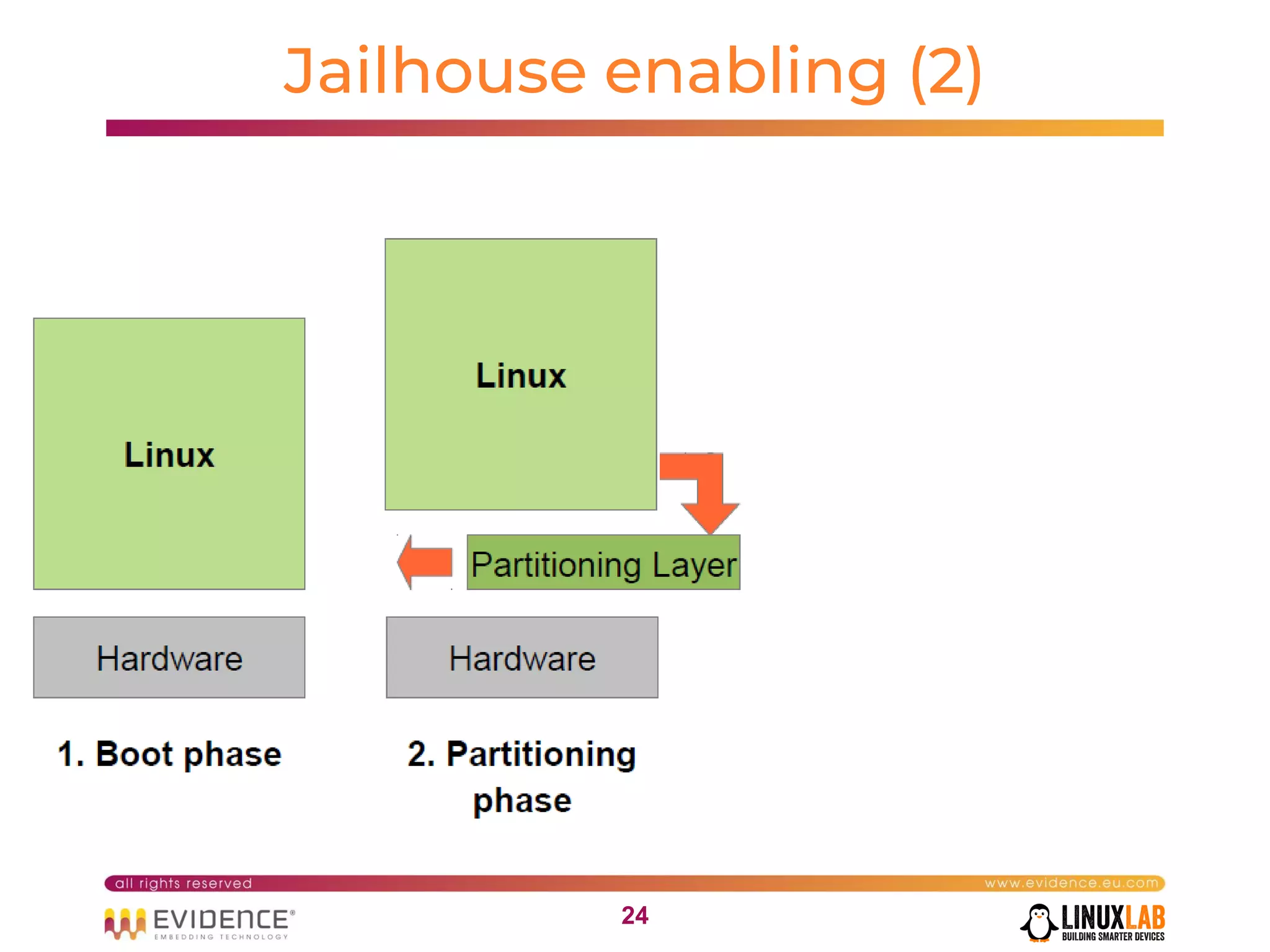
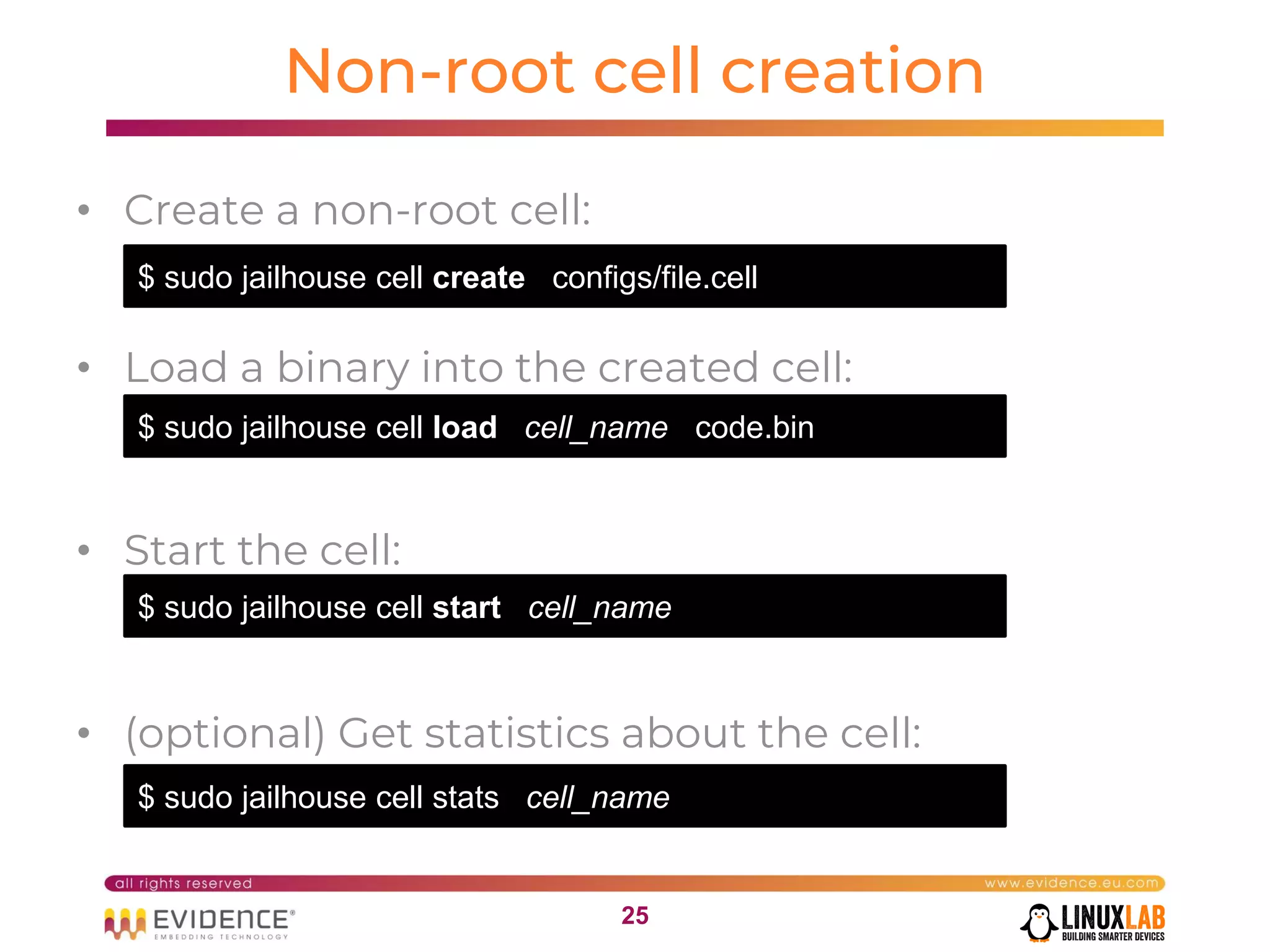
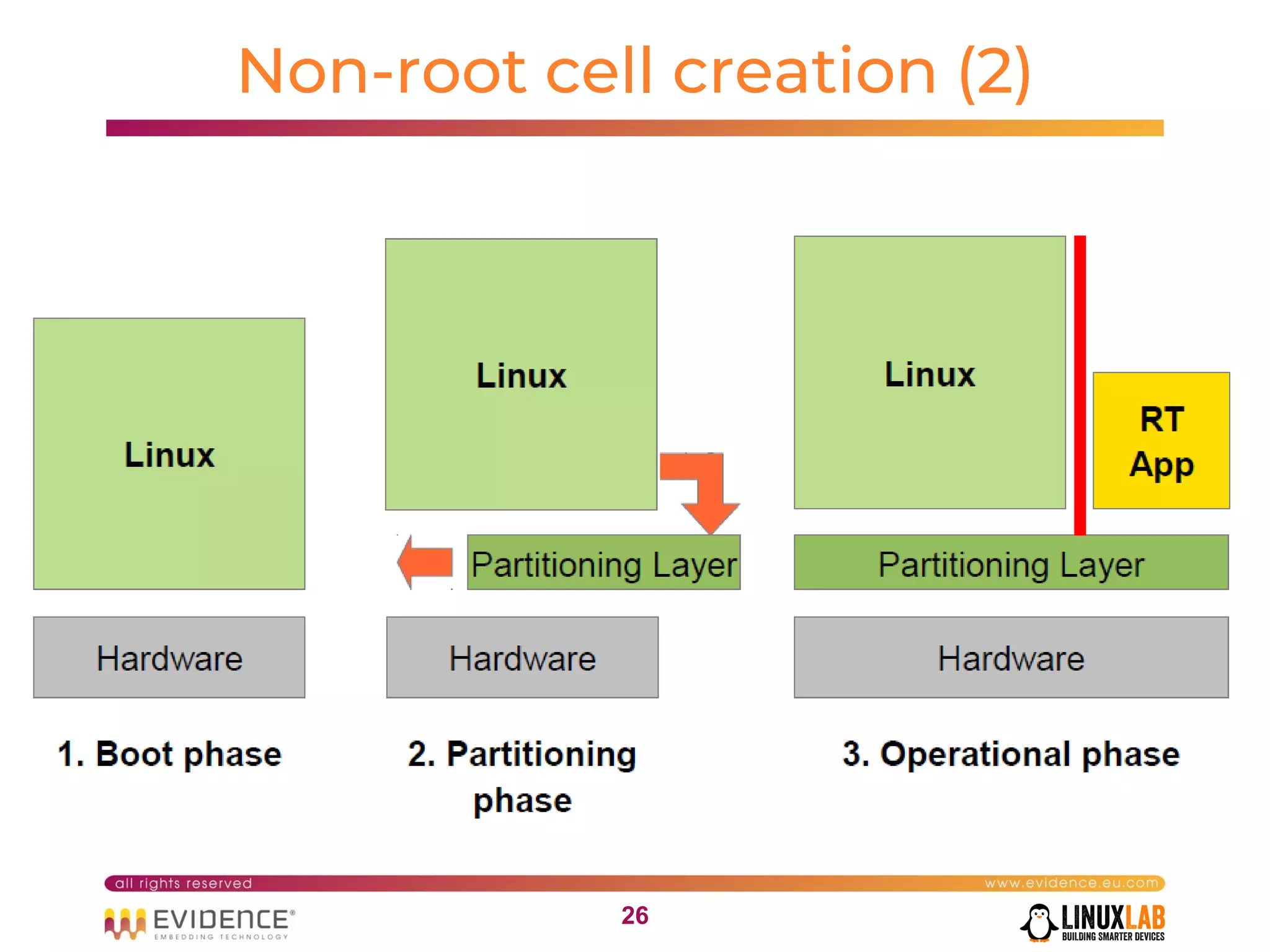
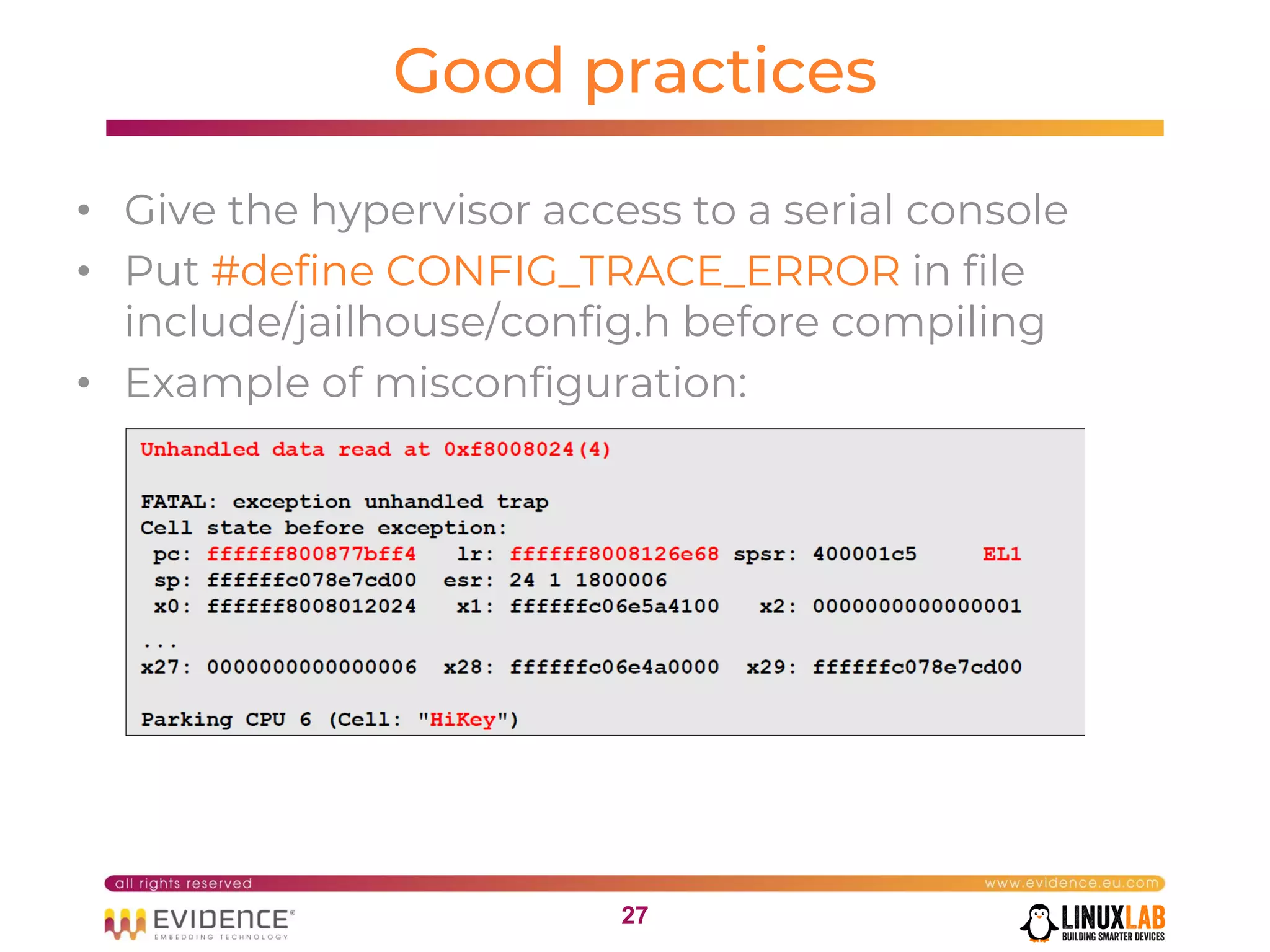
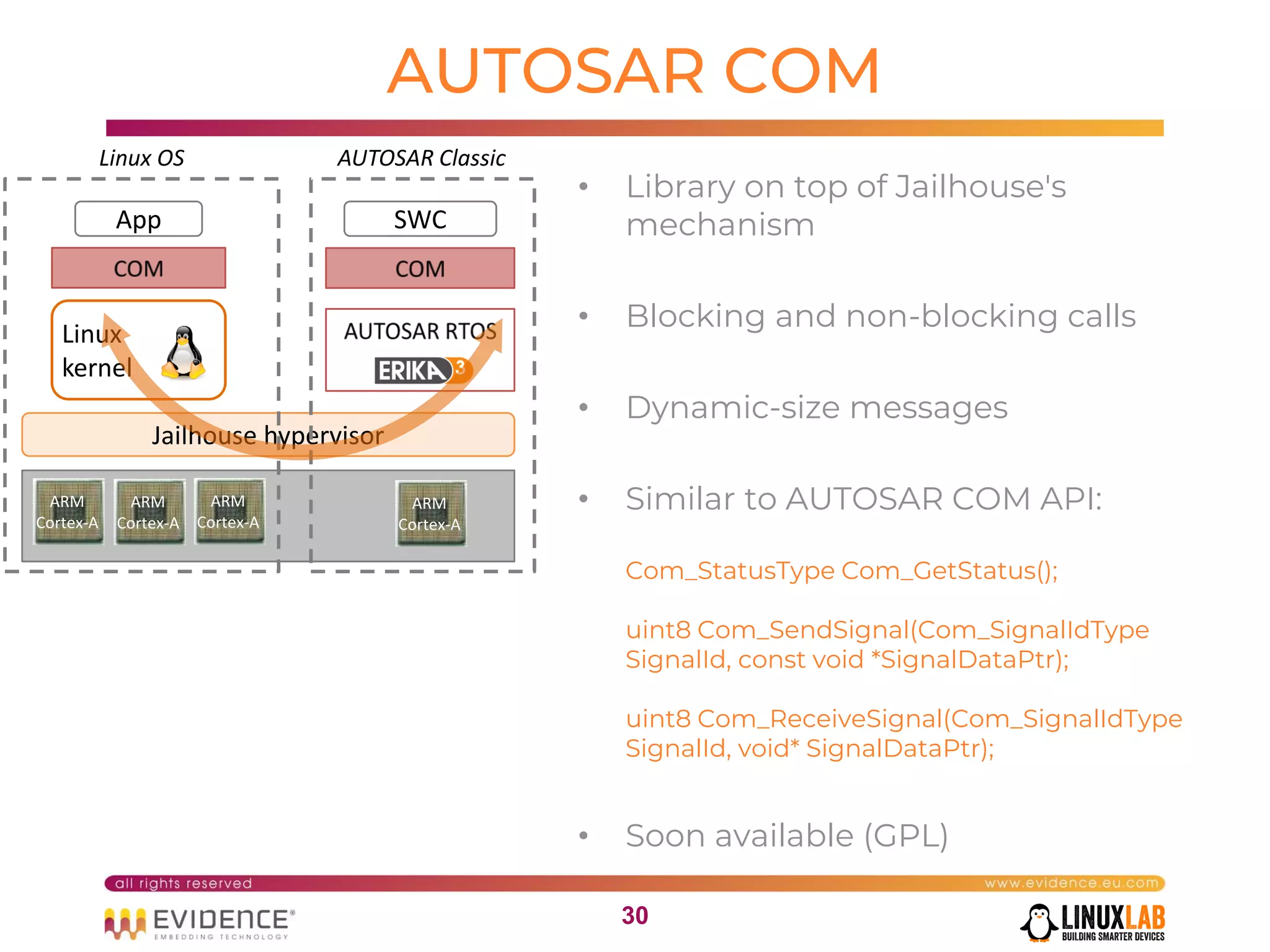
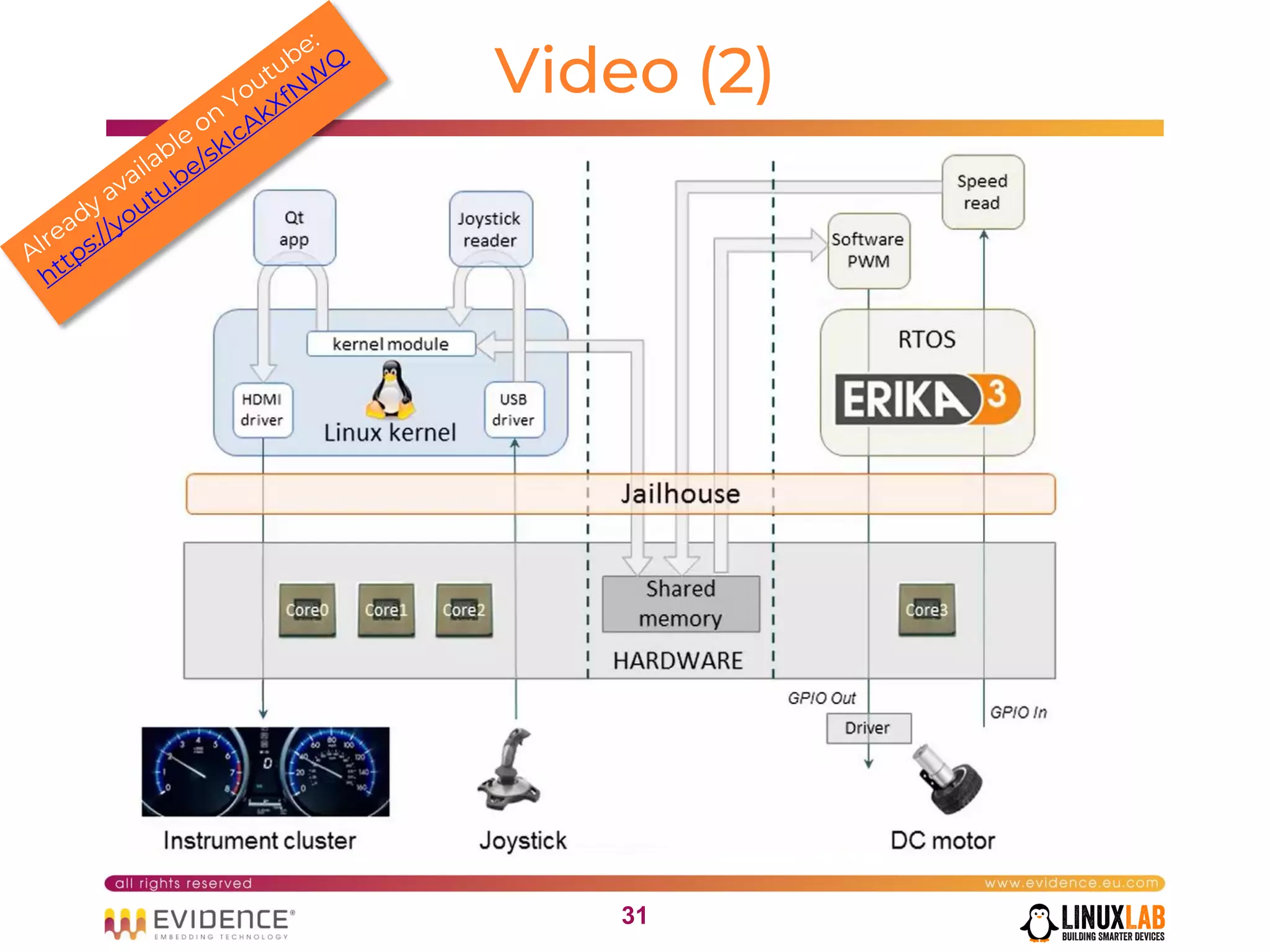
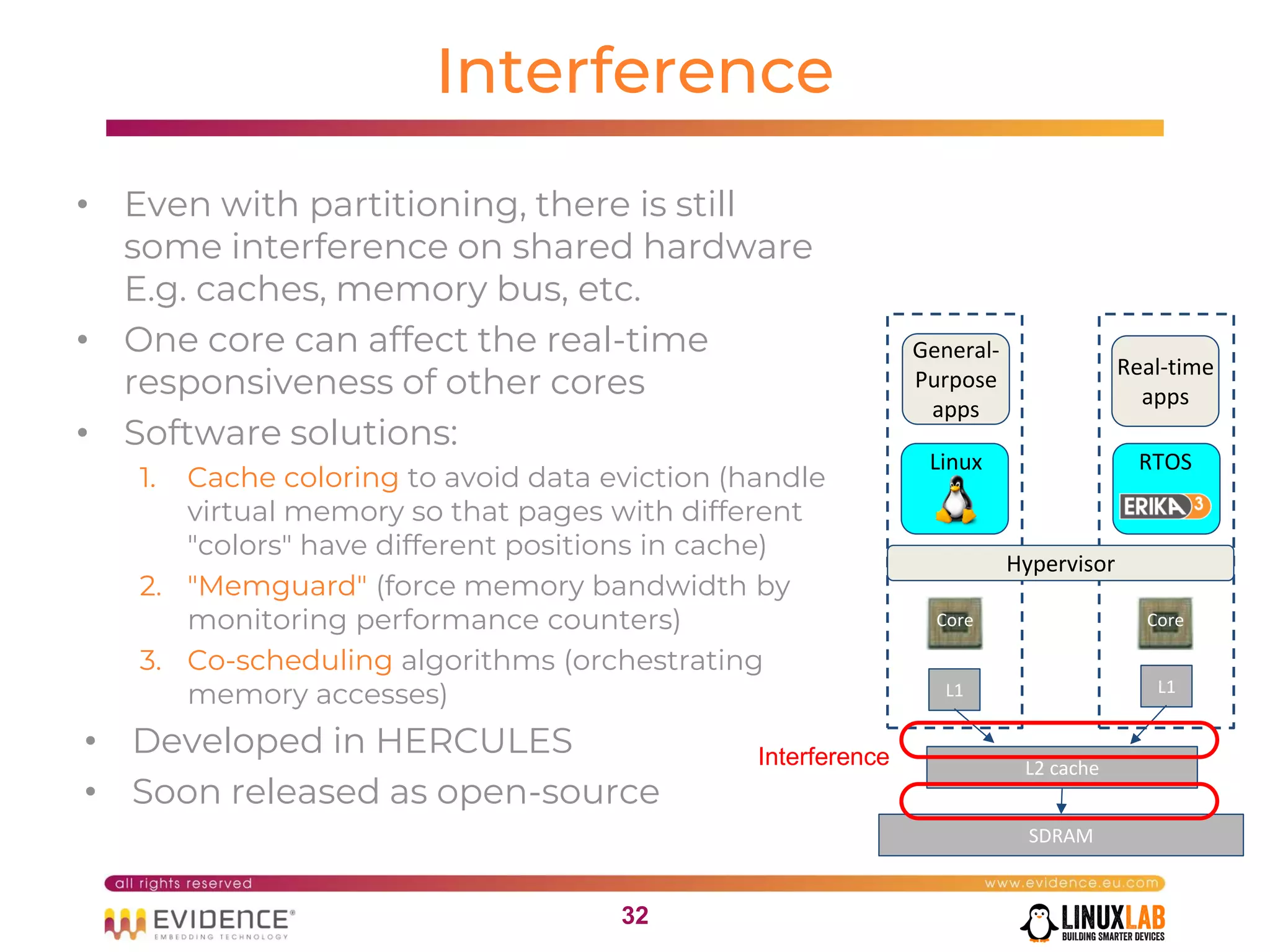
The document discusses handling mixed criticality on embedded multi-core systems, particularly in the automotive sector. It highlights technologies like the Hercules project, Erika Enterprise RTOS, and the Jailhouse hypervisor, which are aimed at improving safety and performance by allowing critical and non-critical tasks to coexist. It also addresses challenges such as certification, resource partitioning, and interference management in shared hardware environments.