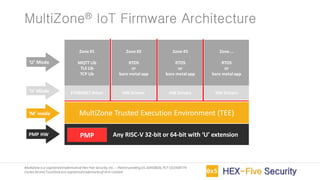
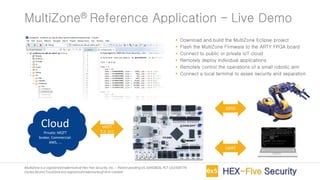
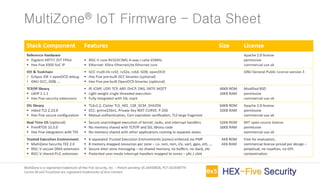
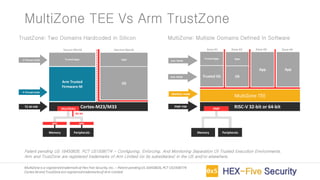
MultiZone is an IoT firmware that provides a trusted execution environment (TEE) for securing IoT applications on RISC-V processors. It includes pre-integrated libraries for TCP/IP, TLS, ECC and FreeRTOS to handle basic and advanced IoT requirements. MultiZone provides four separated execution environments called zones that are enforced by hardware to isolate trusted applications from untrusted third party code and libraries. It allows for building secure IoT devices, remote firmware updates, and real-time device monitoring and management without needing proprietary hardware extensions.