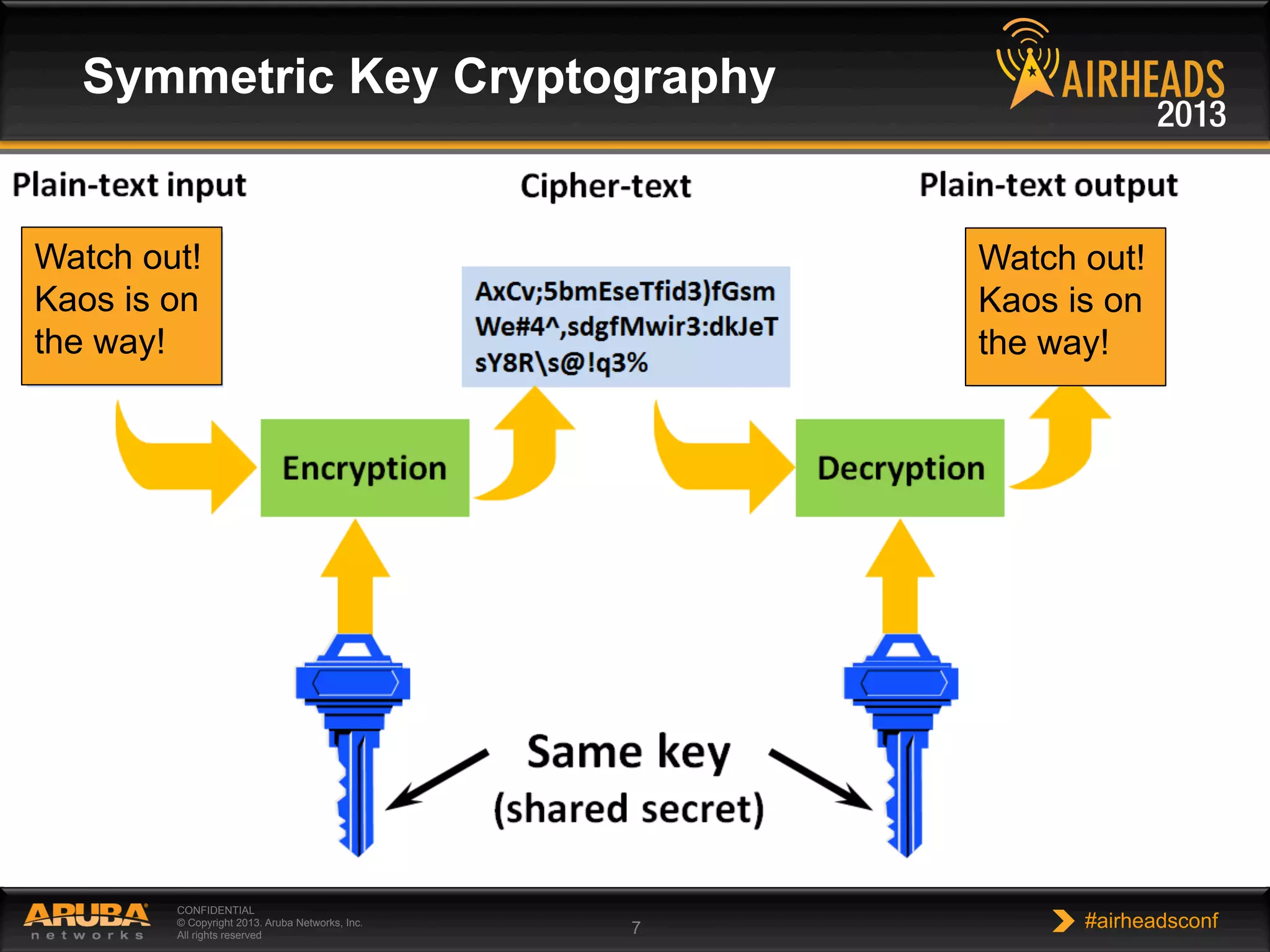
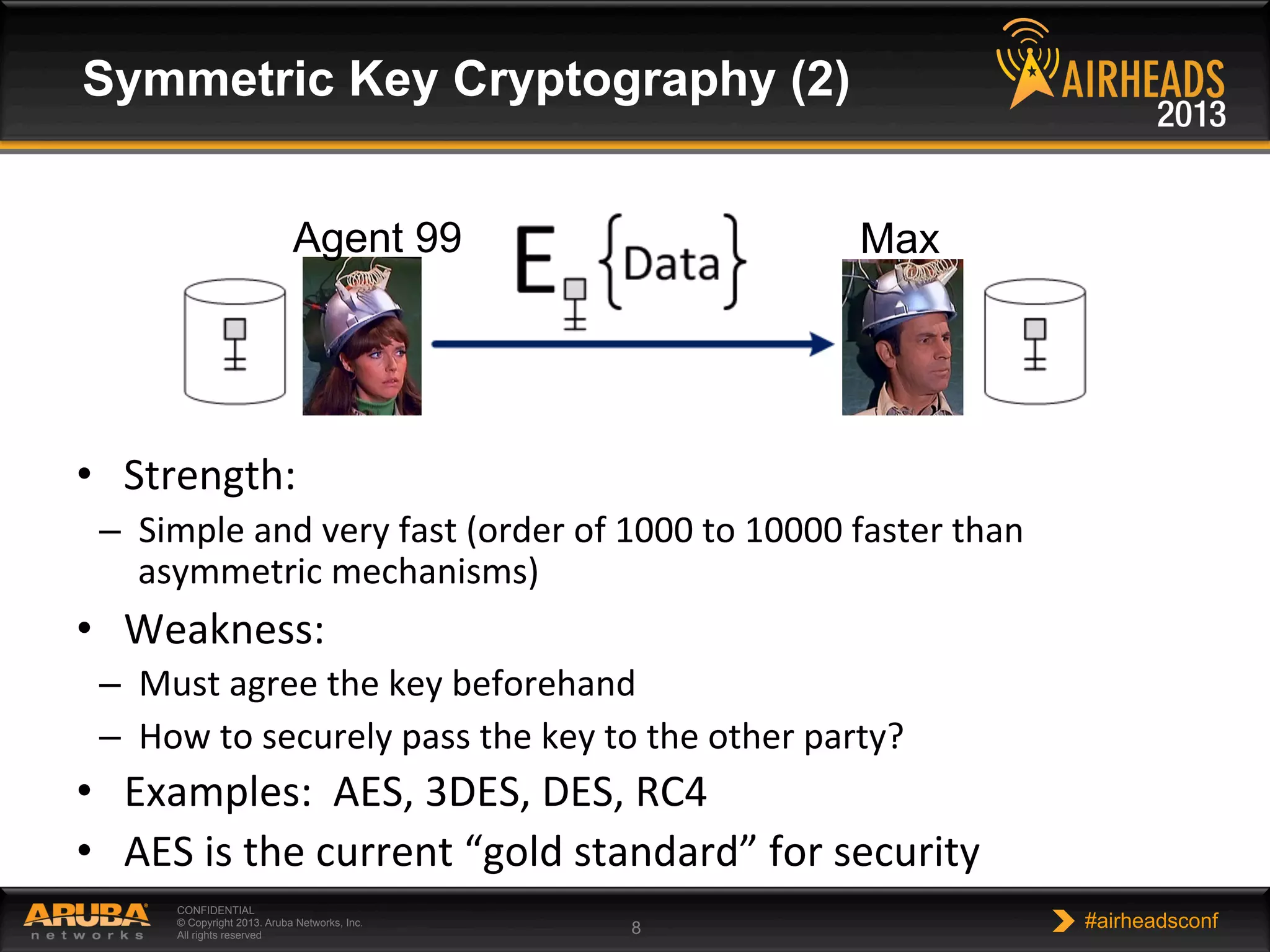
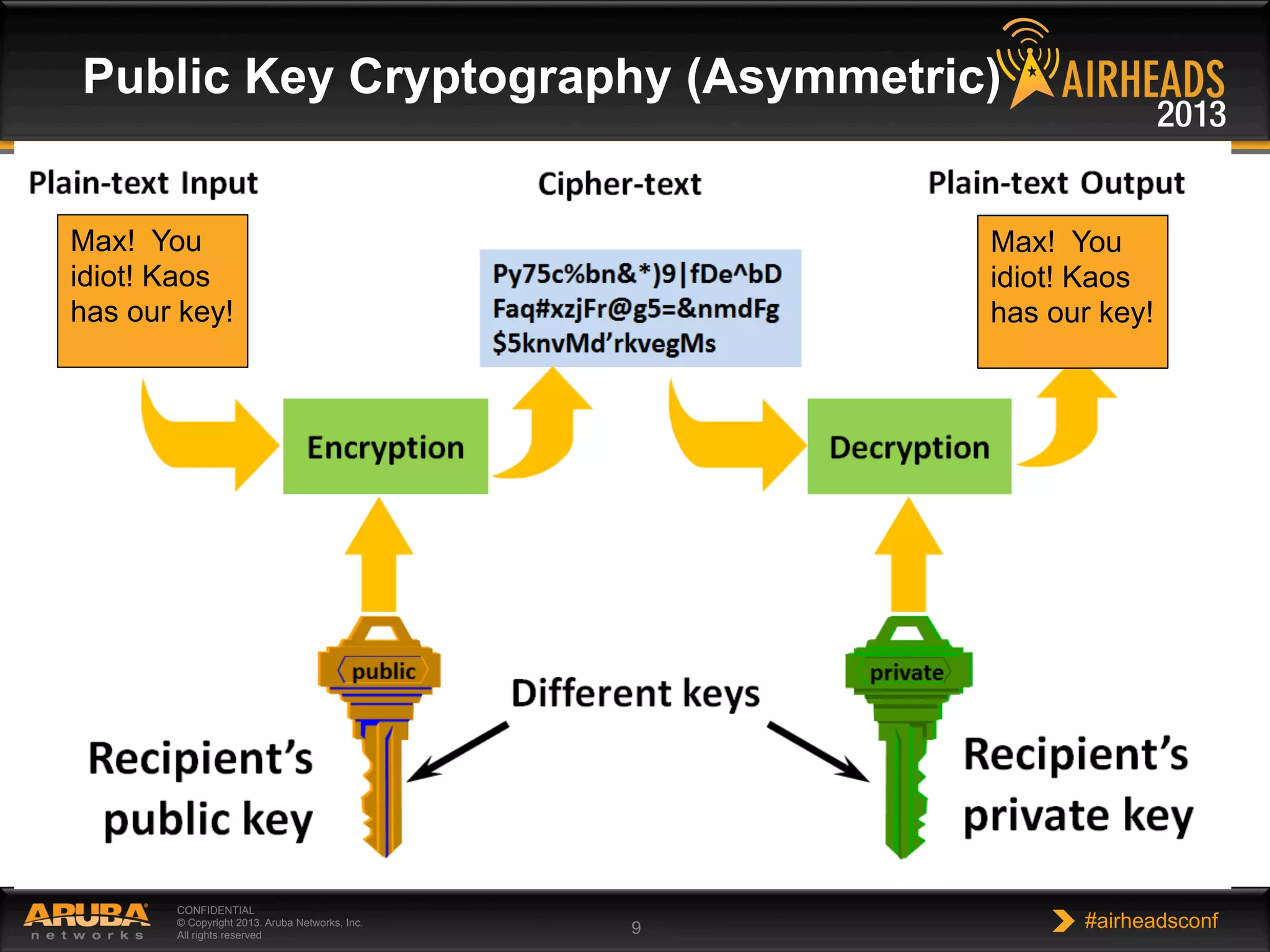
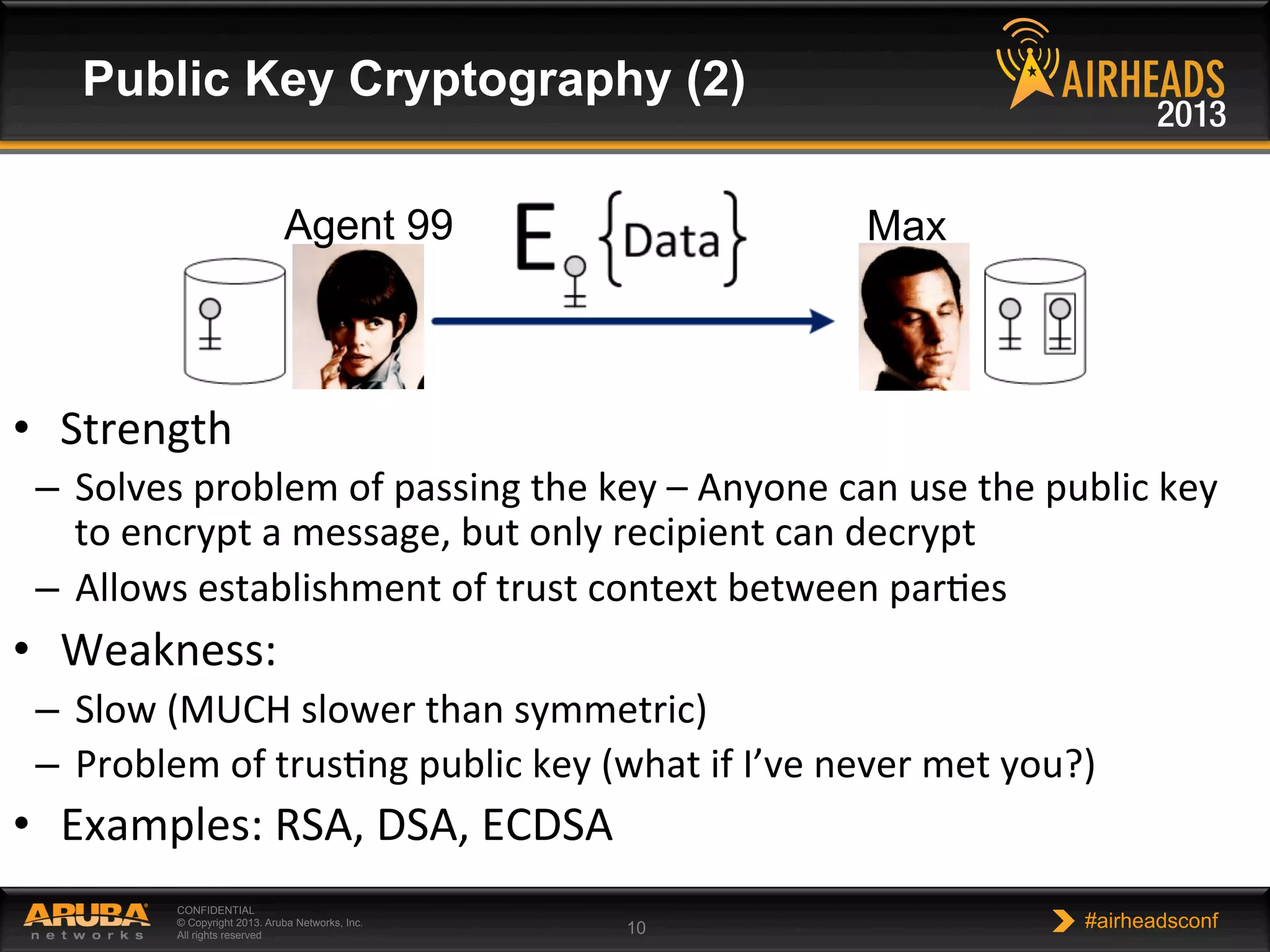
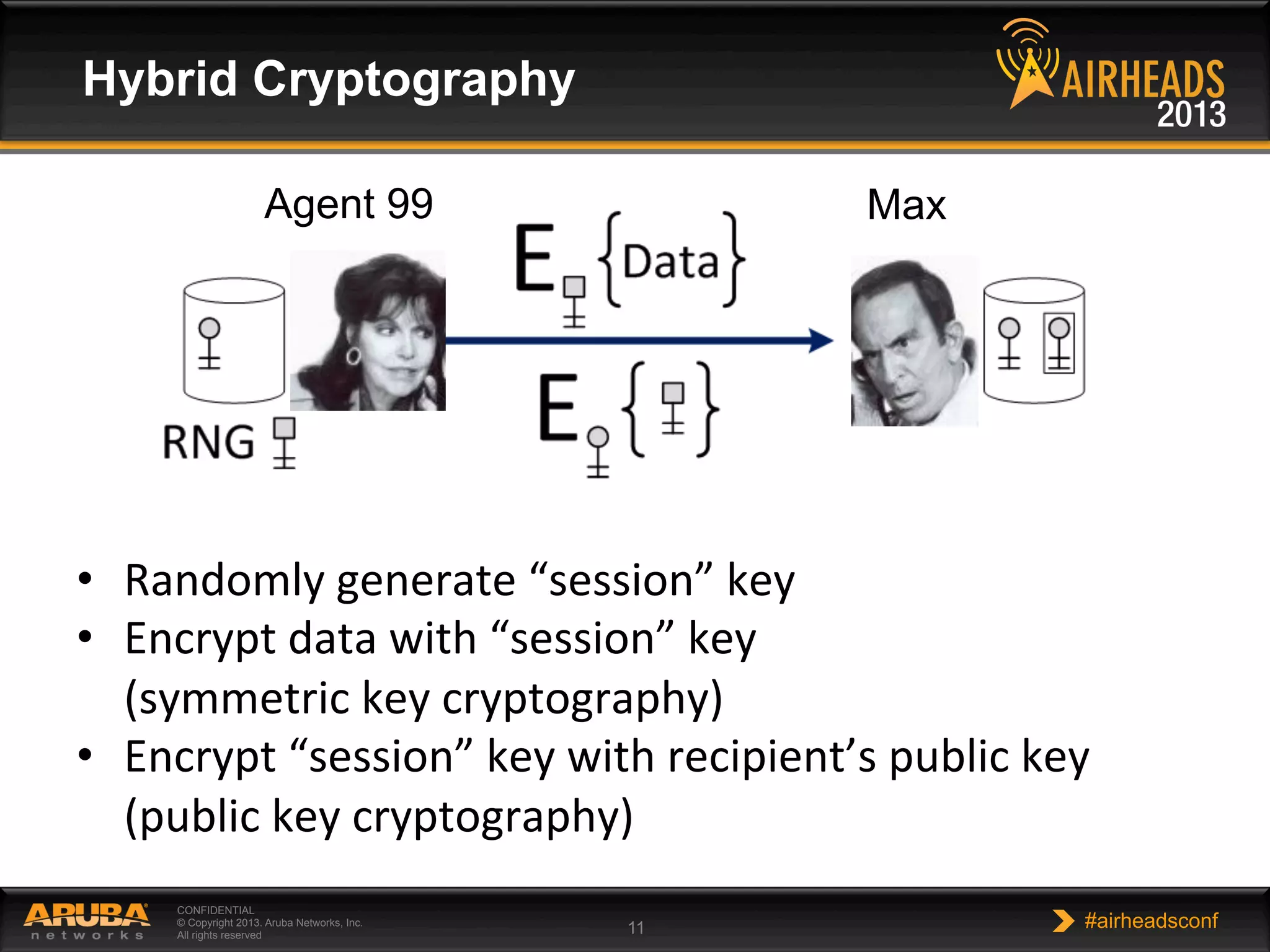
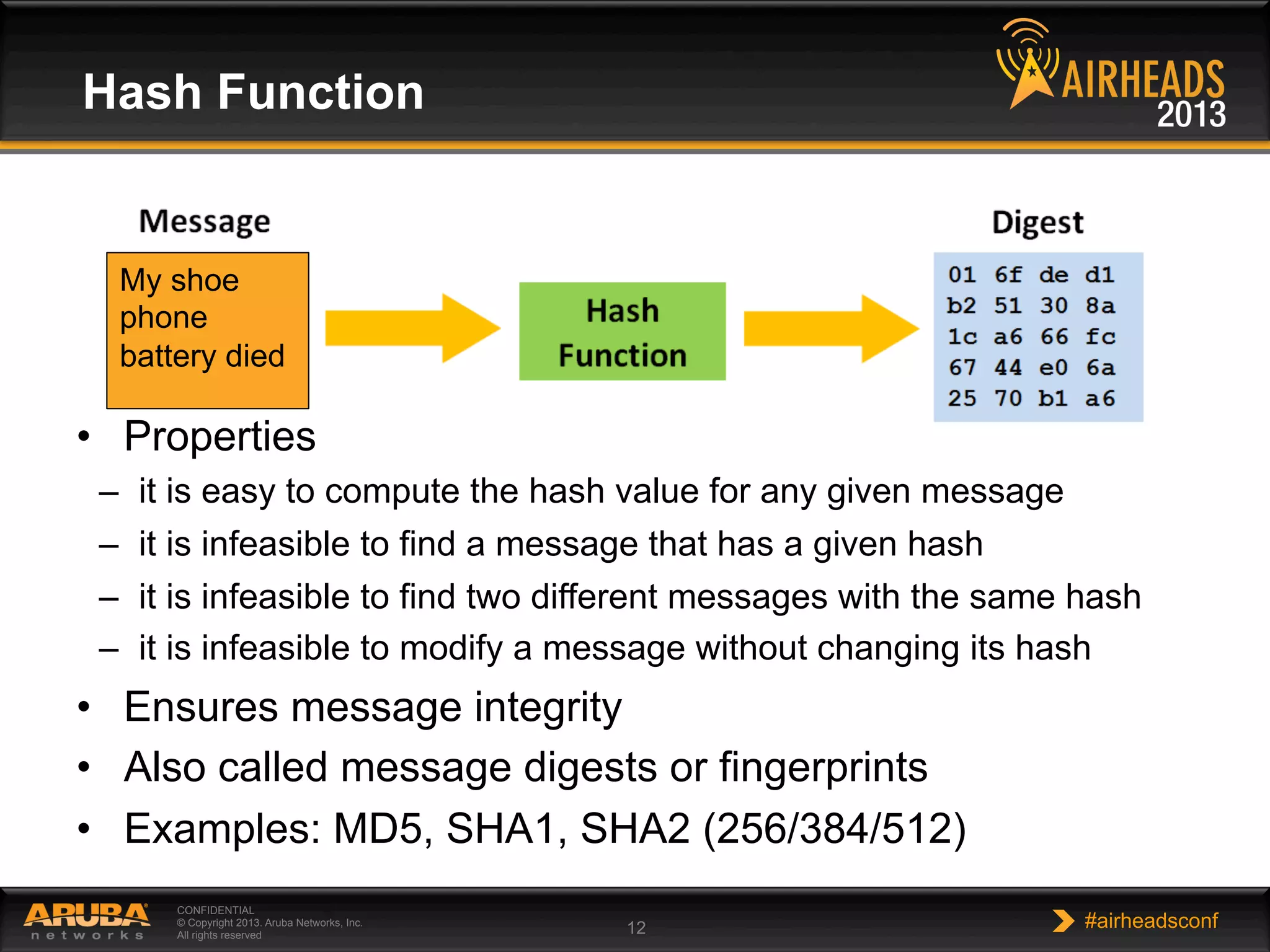
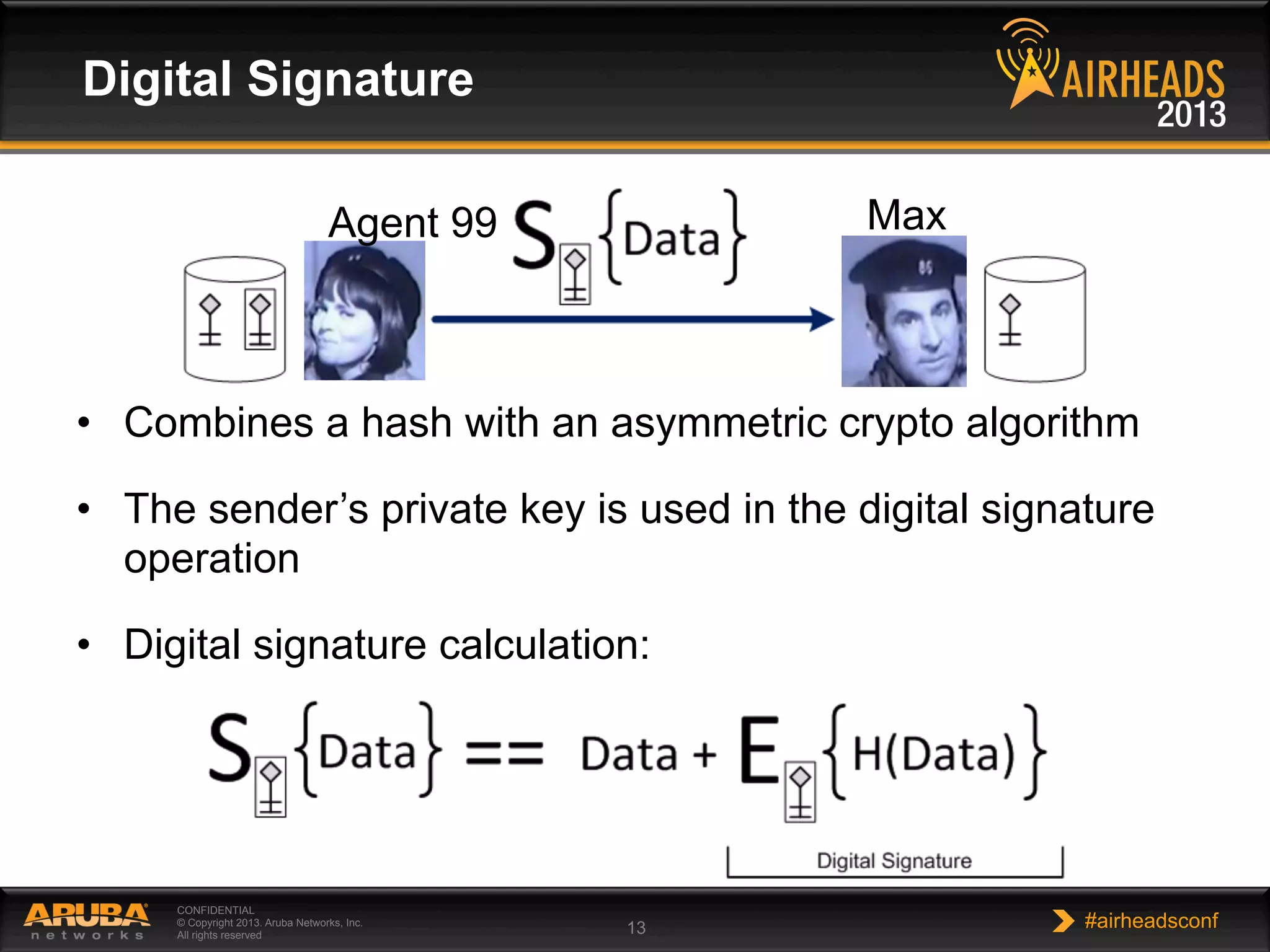
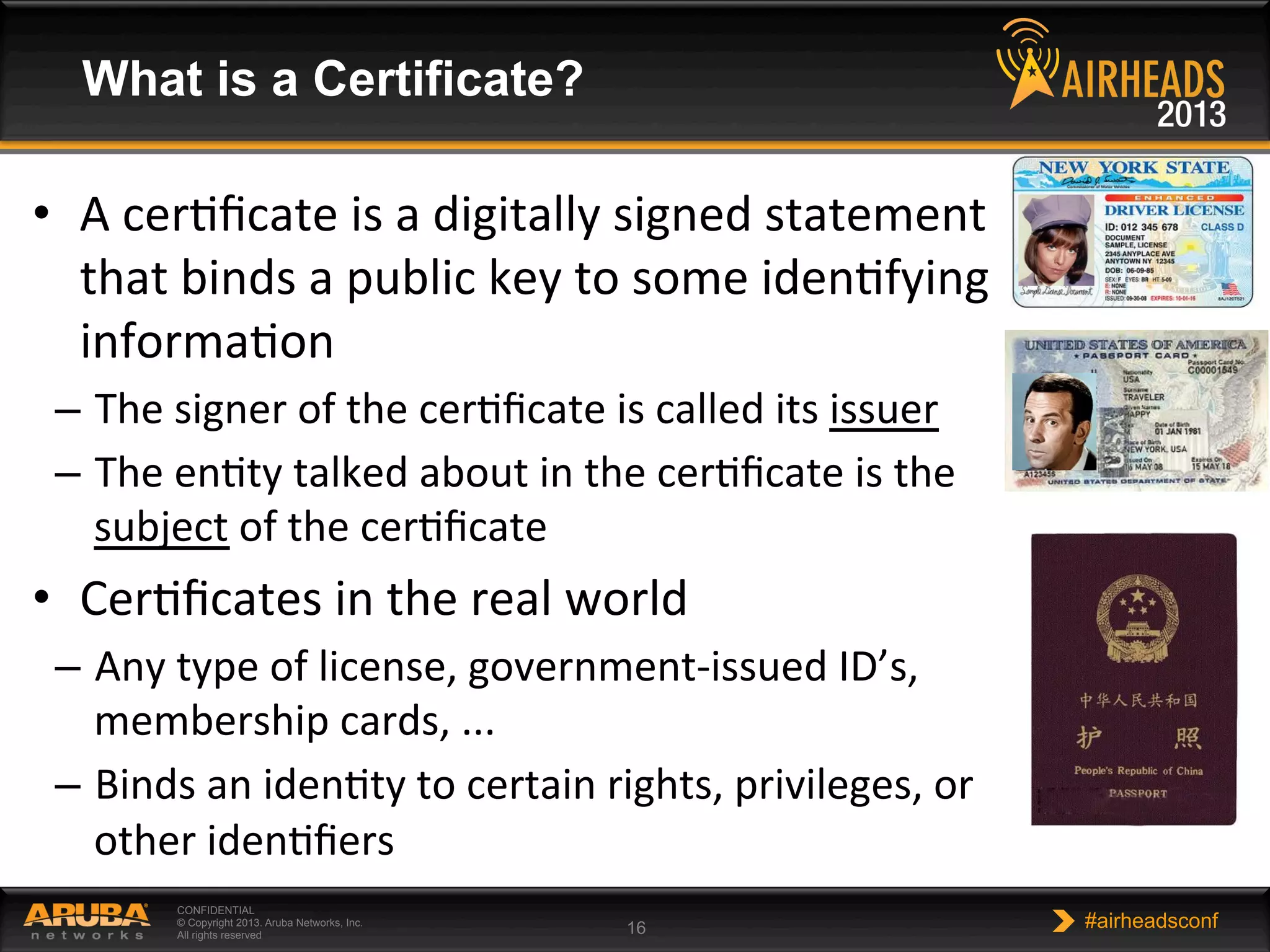
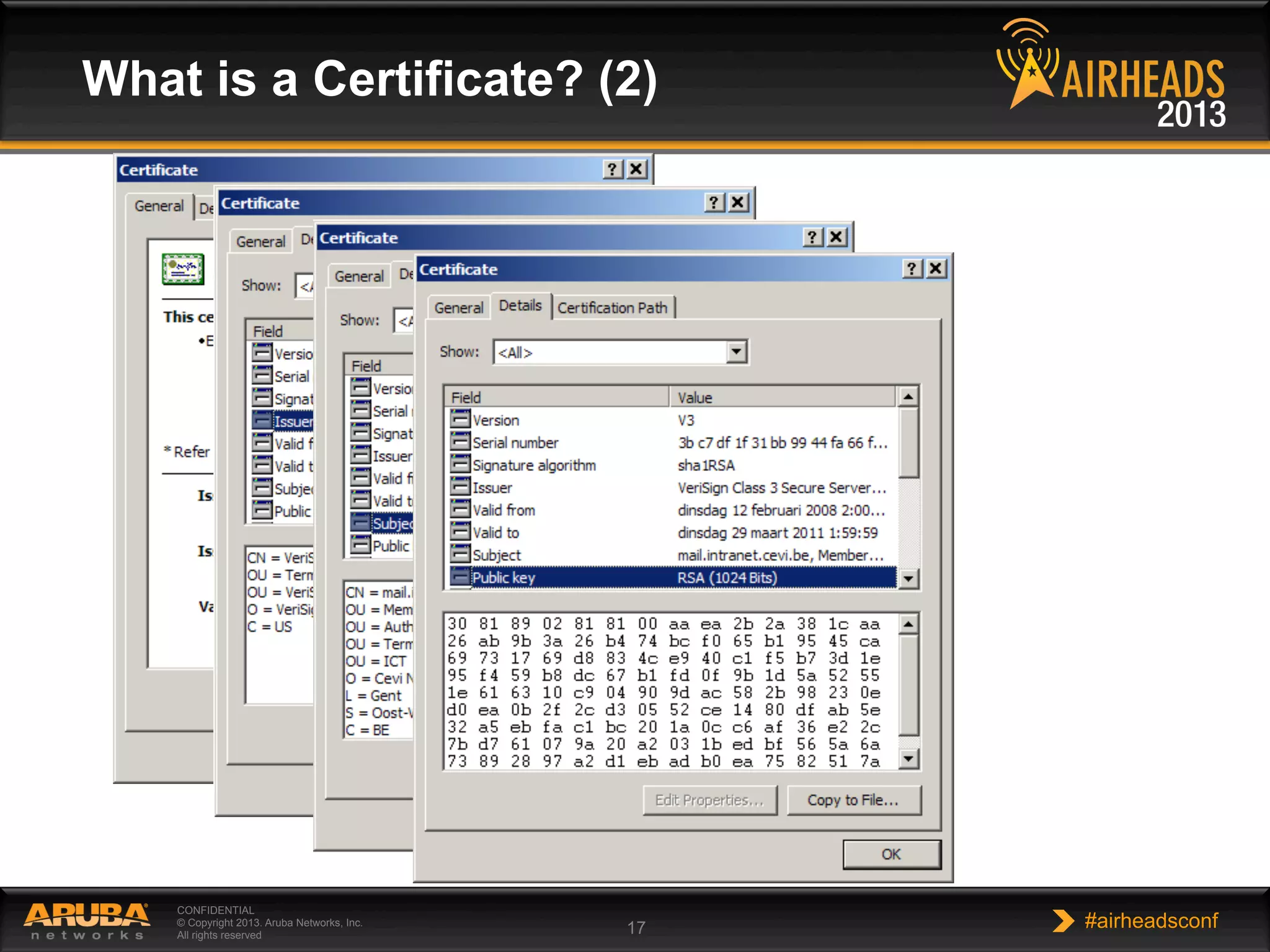
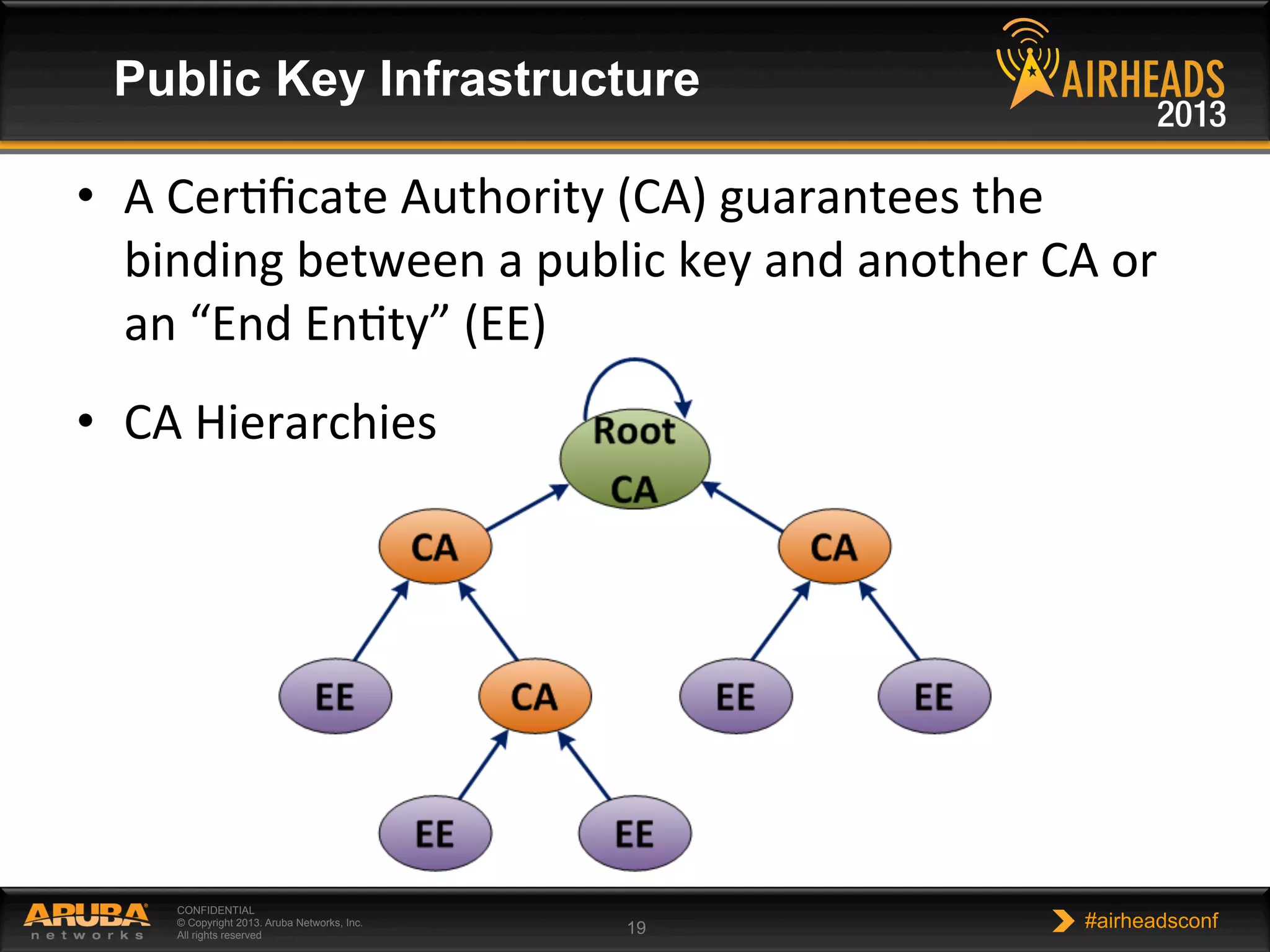
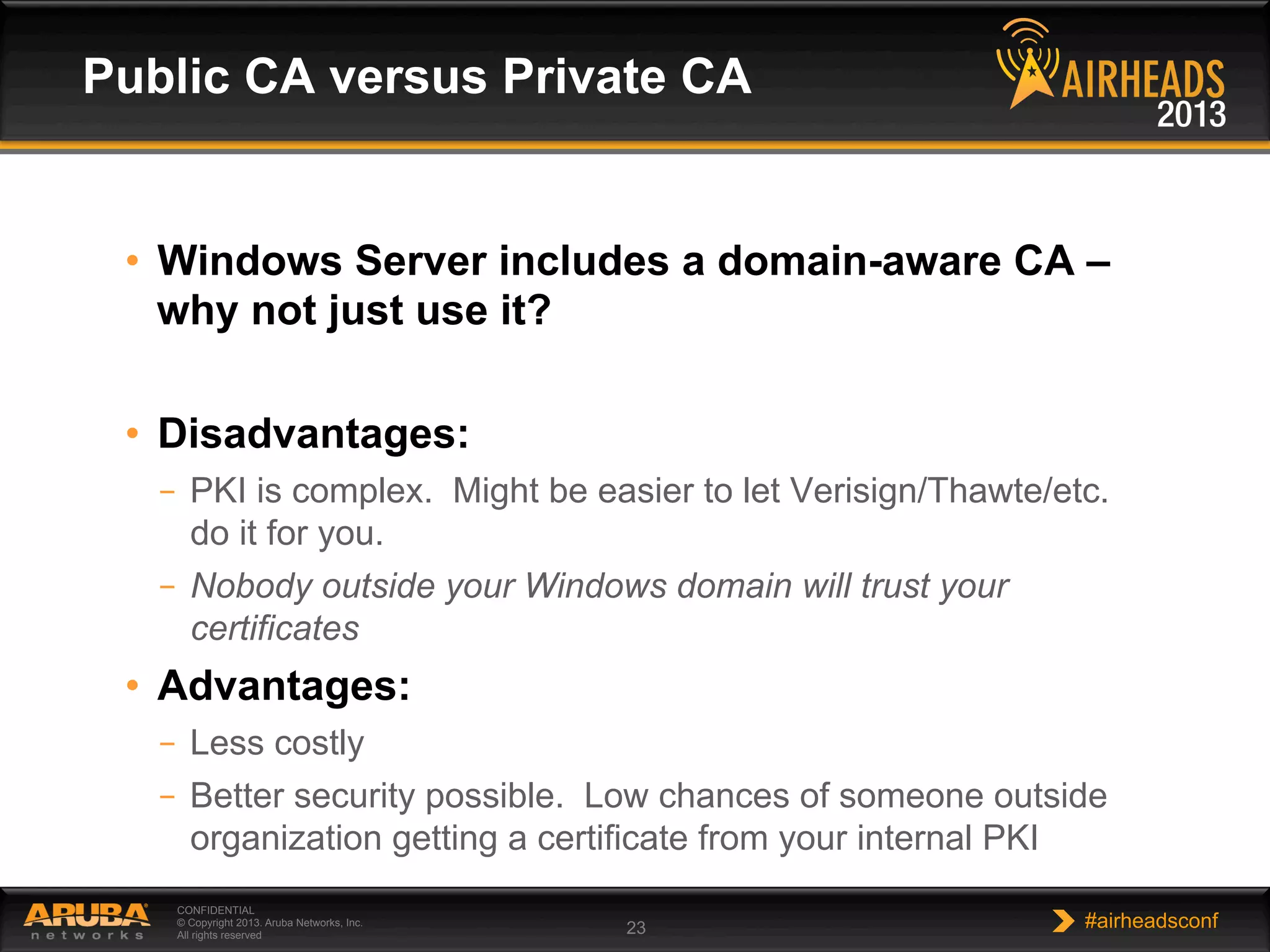
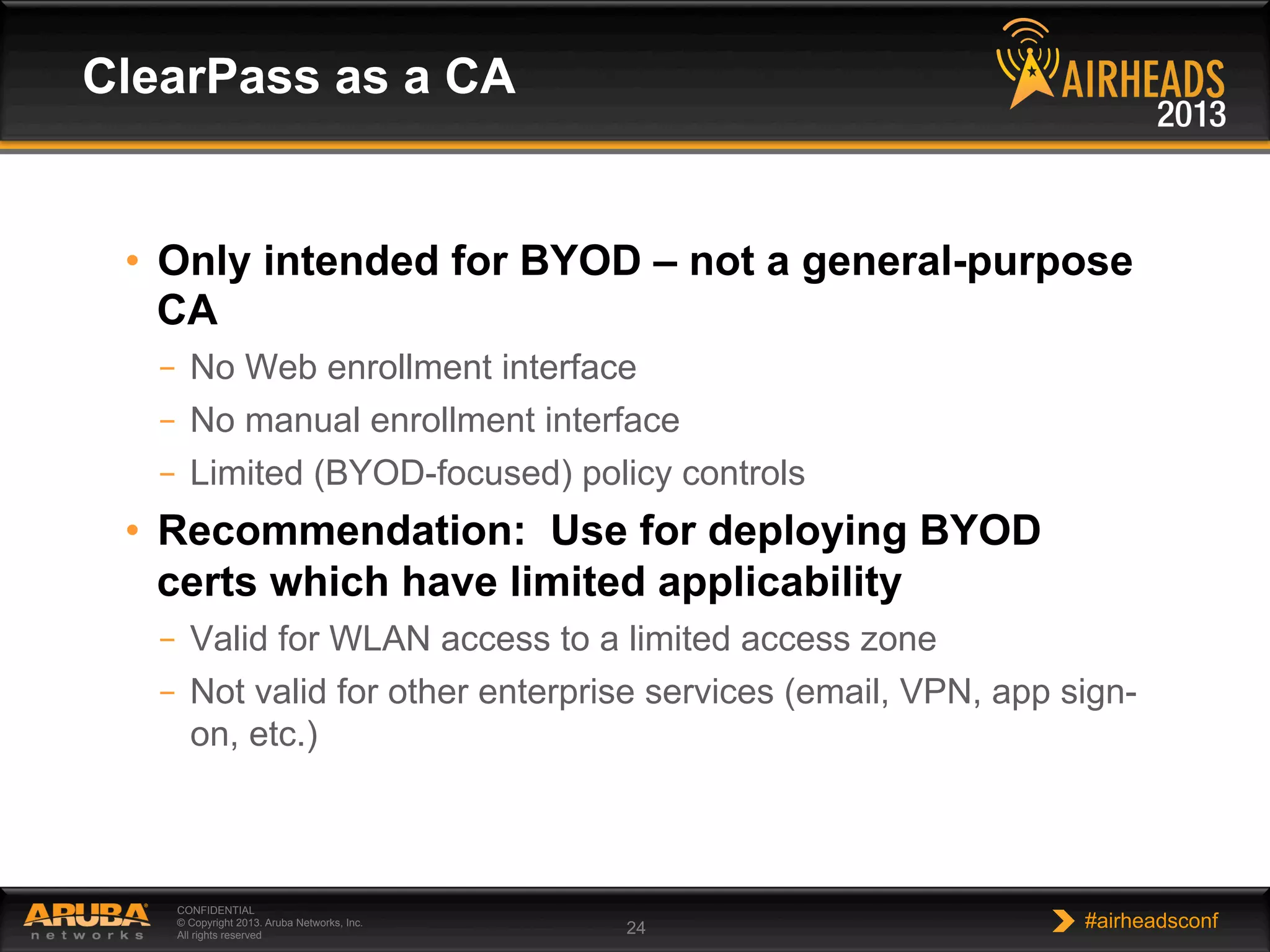
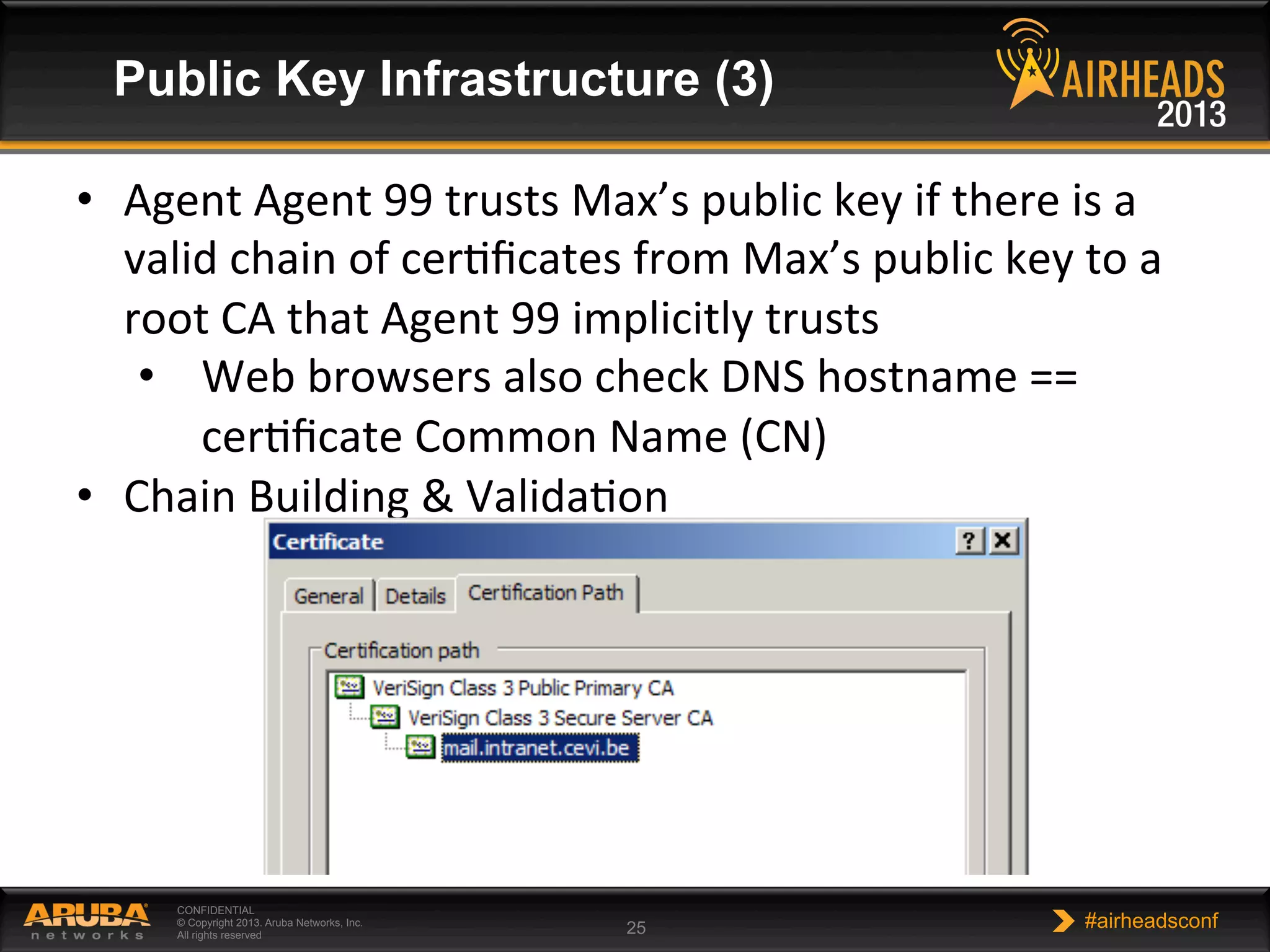
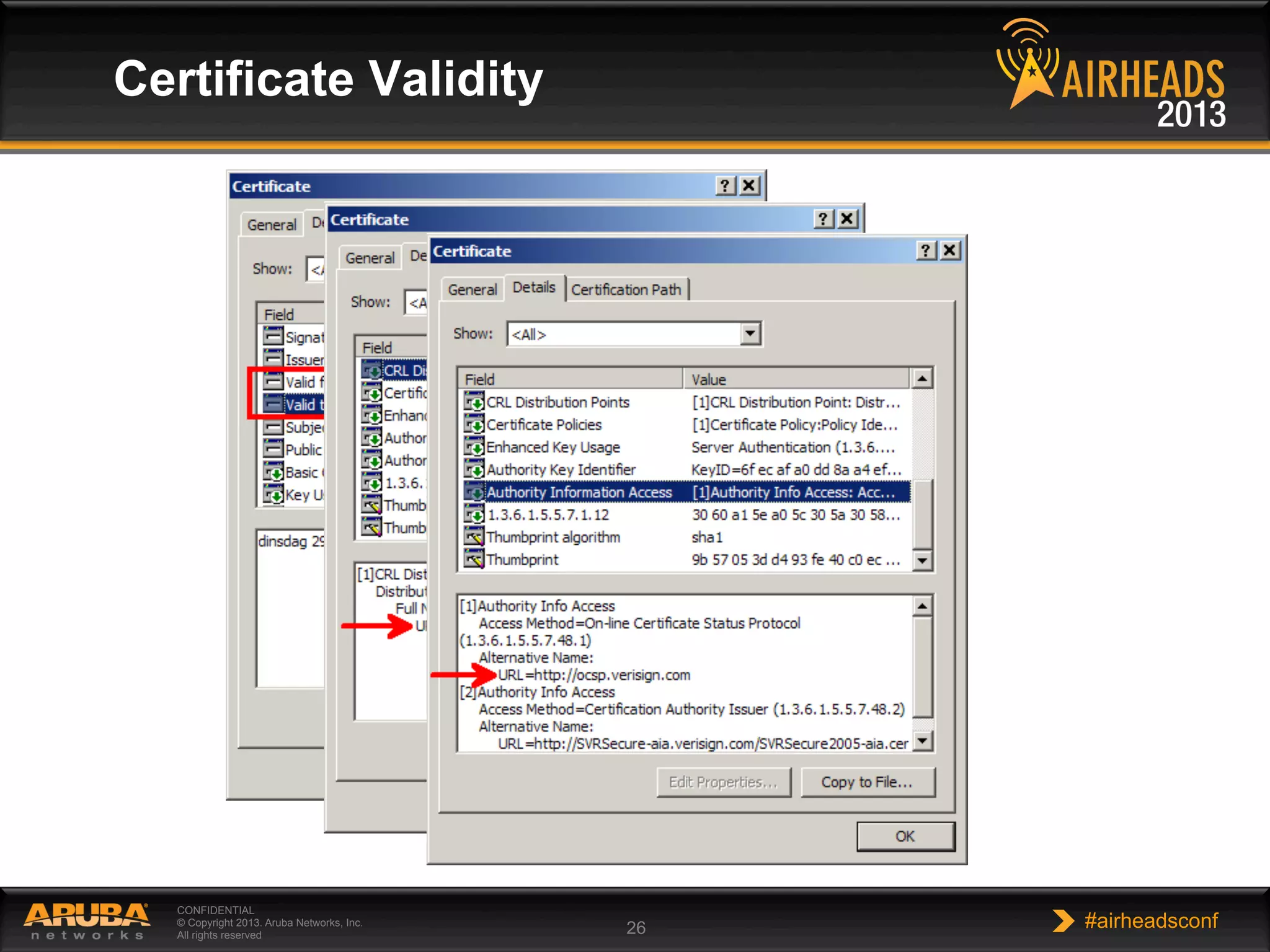
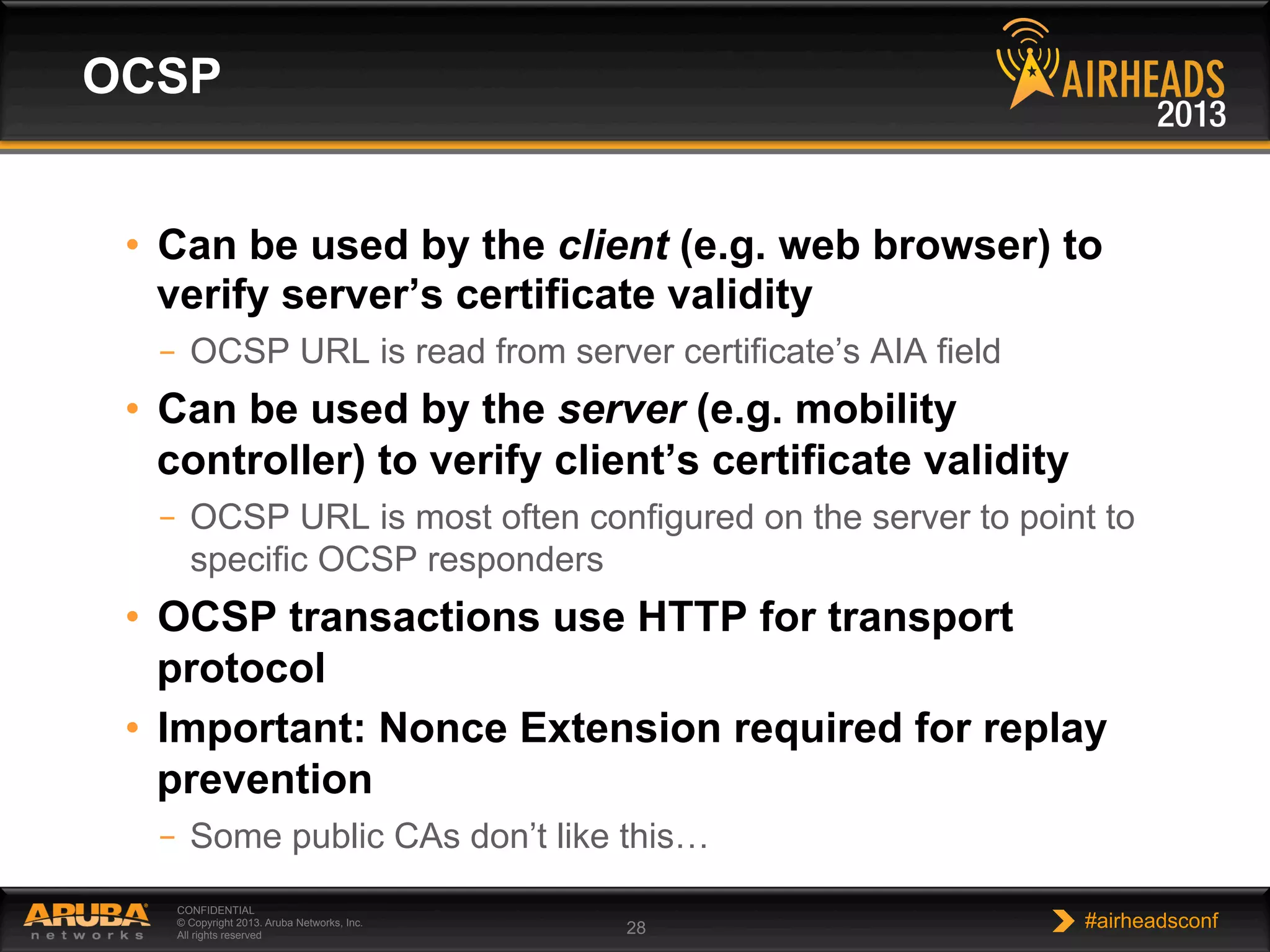
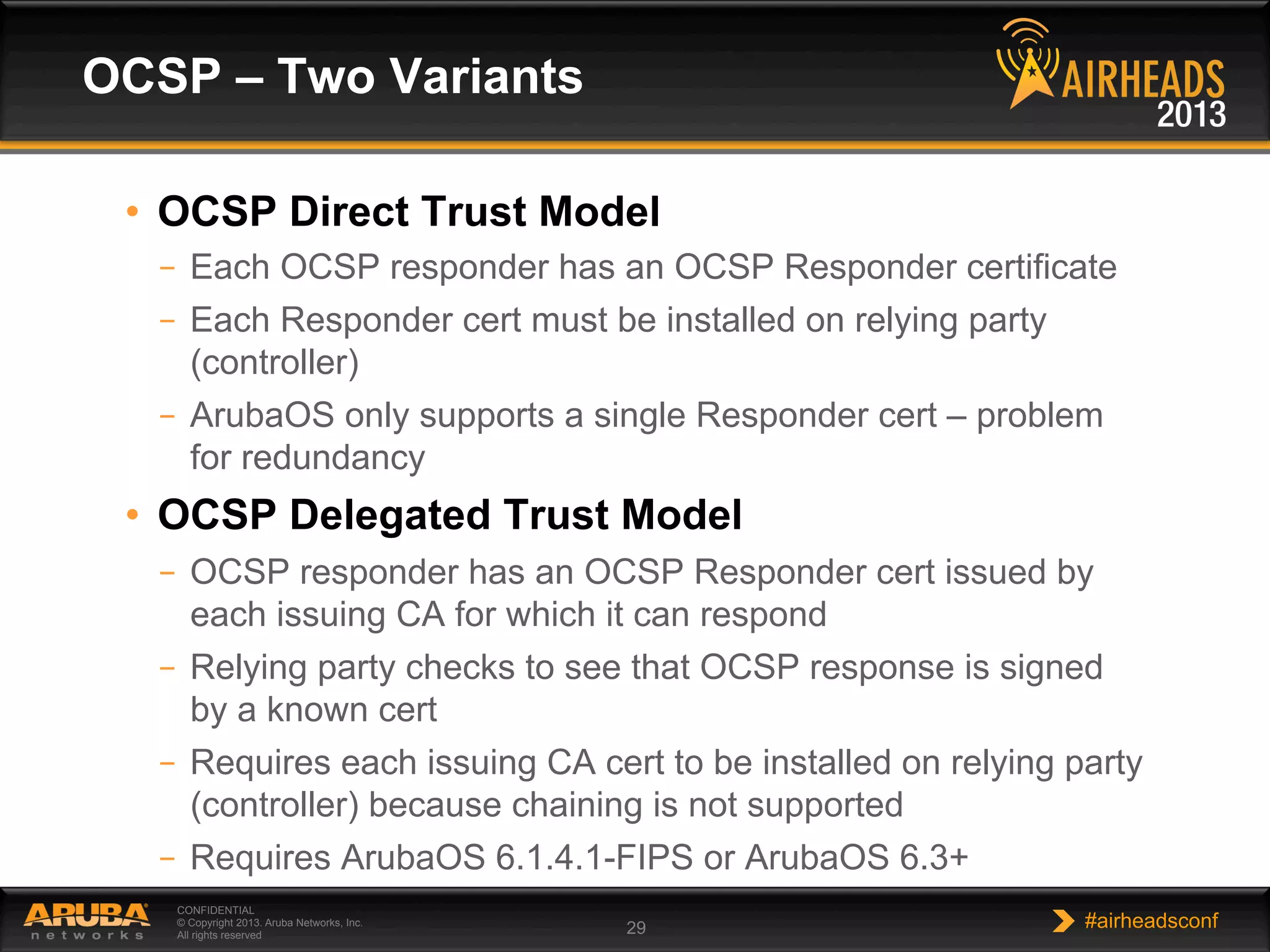
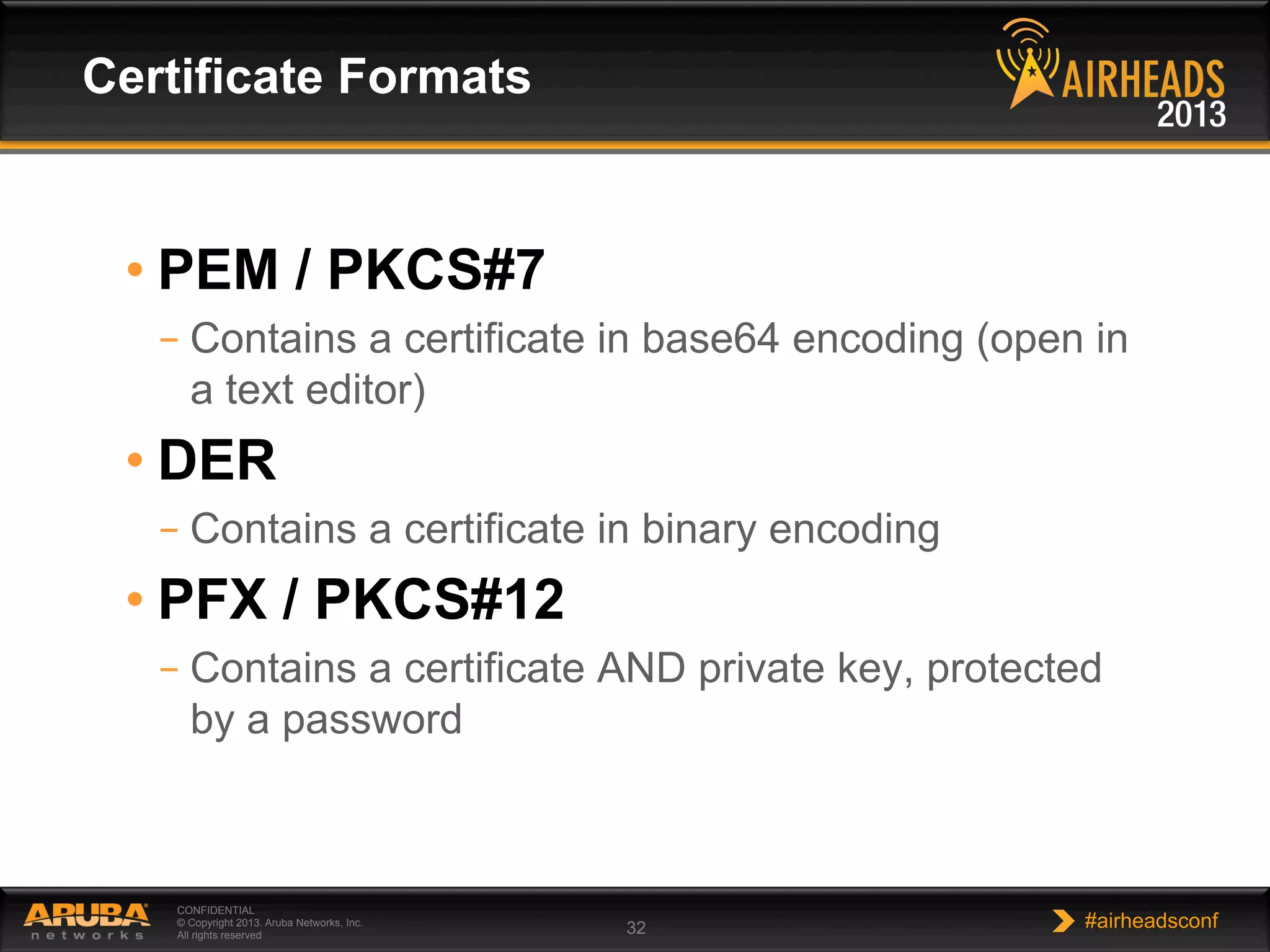
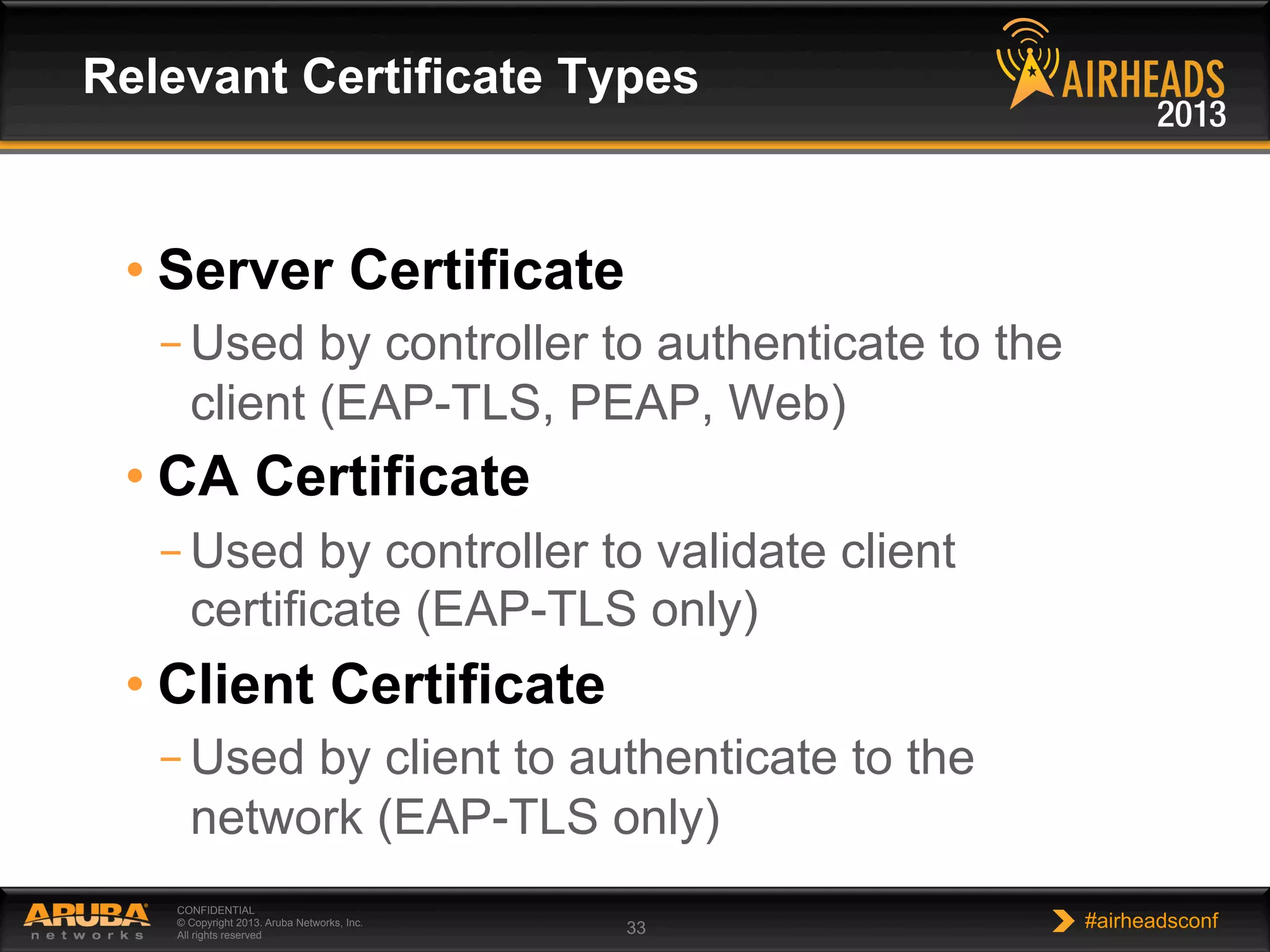
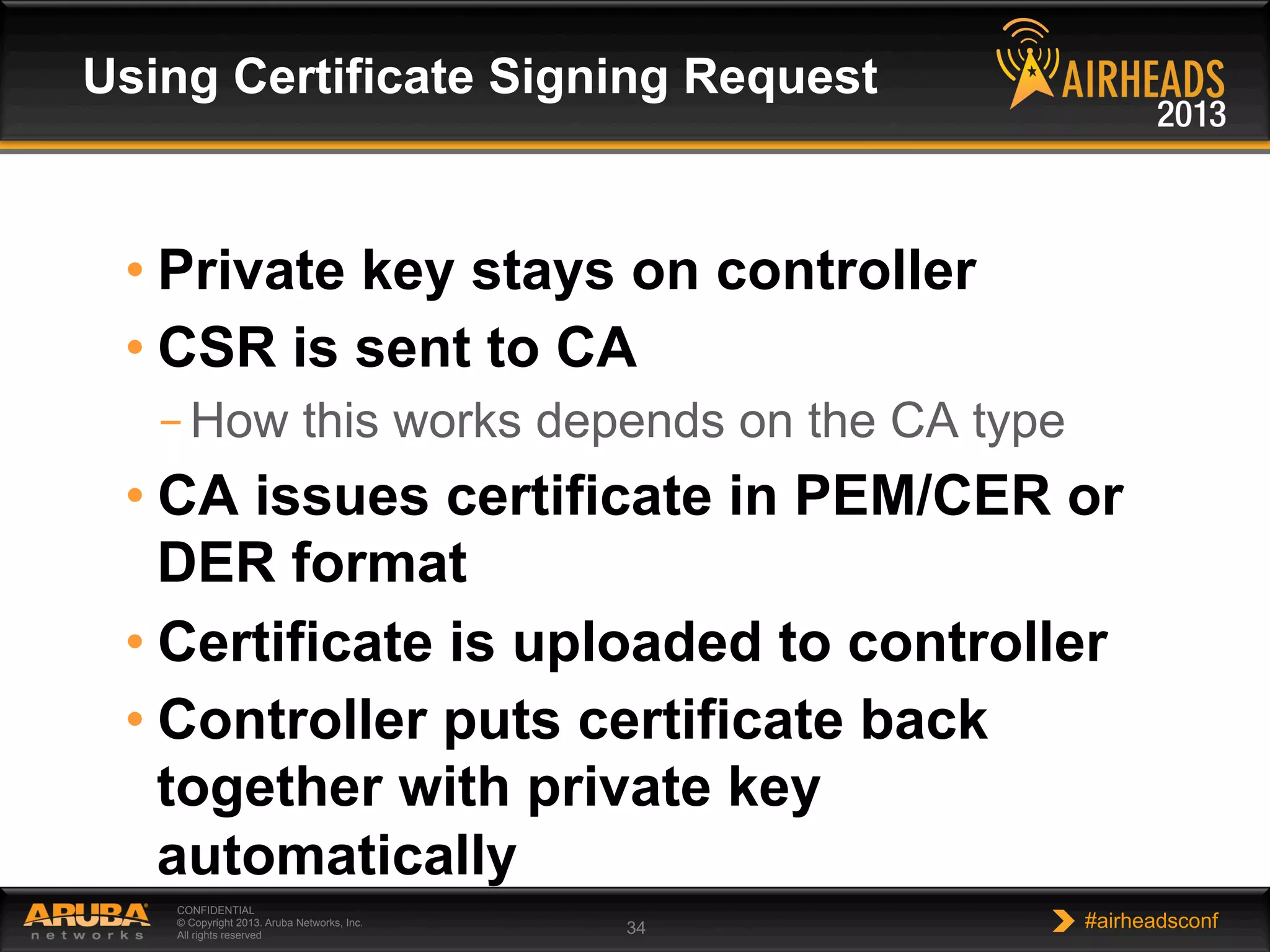
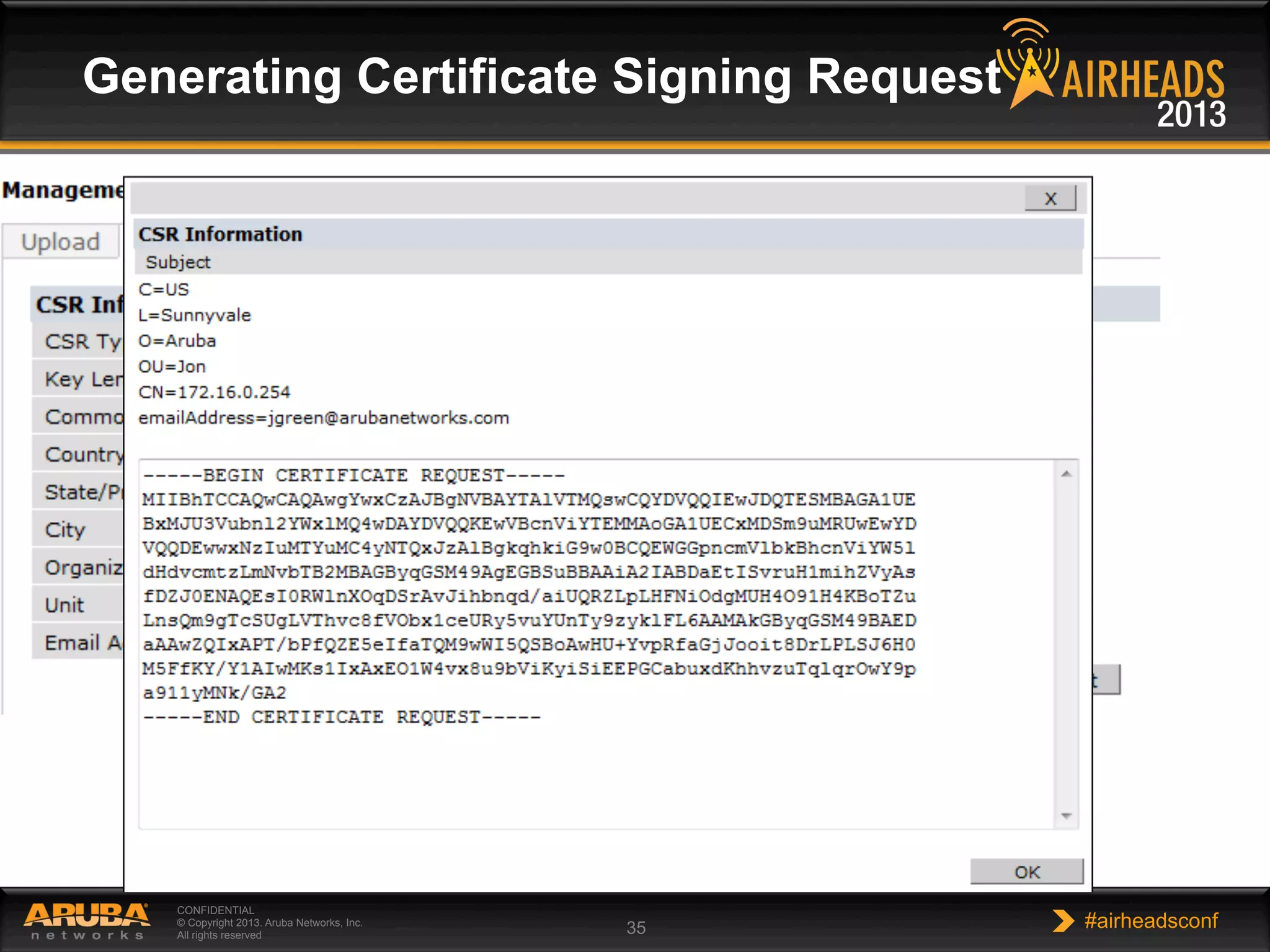
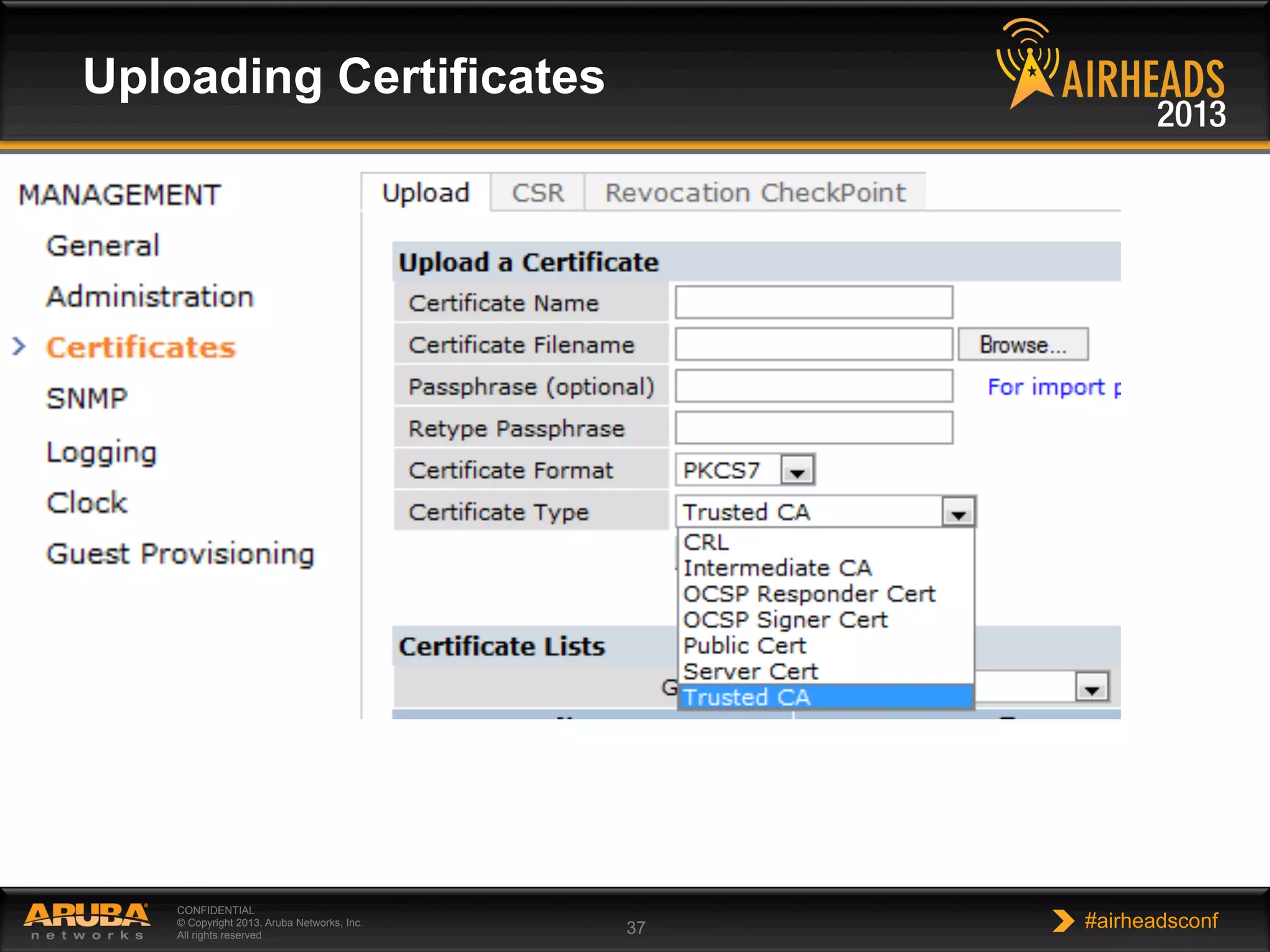
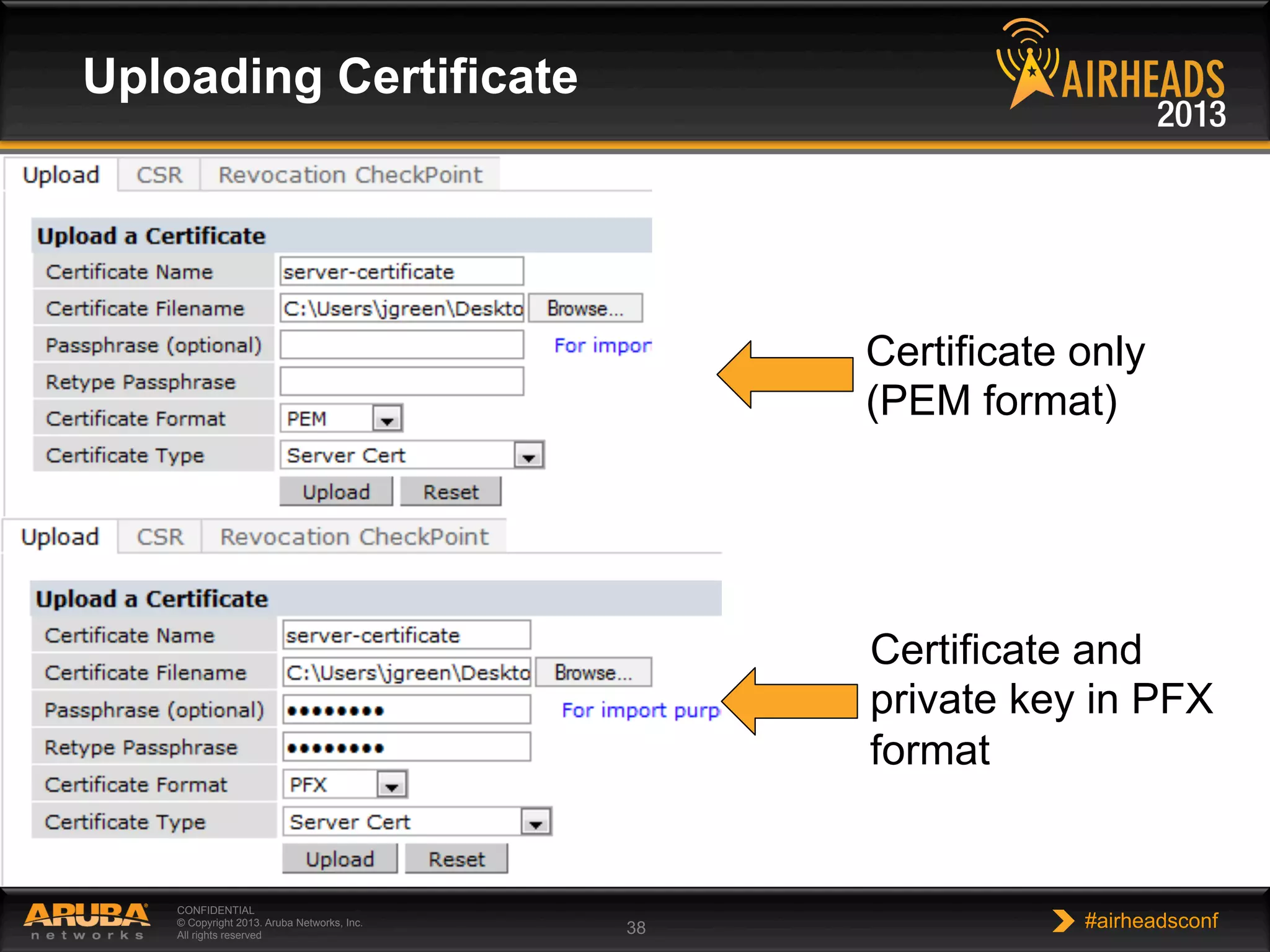
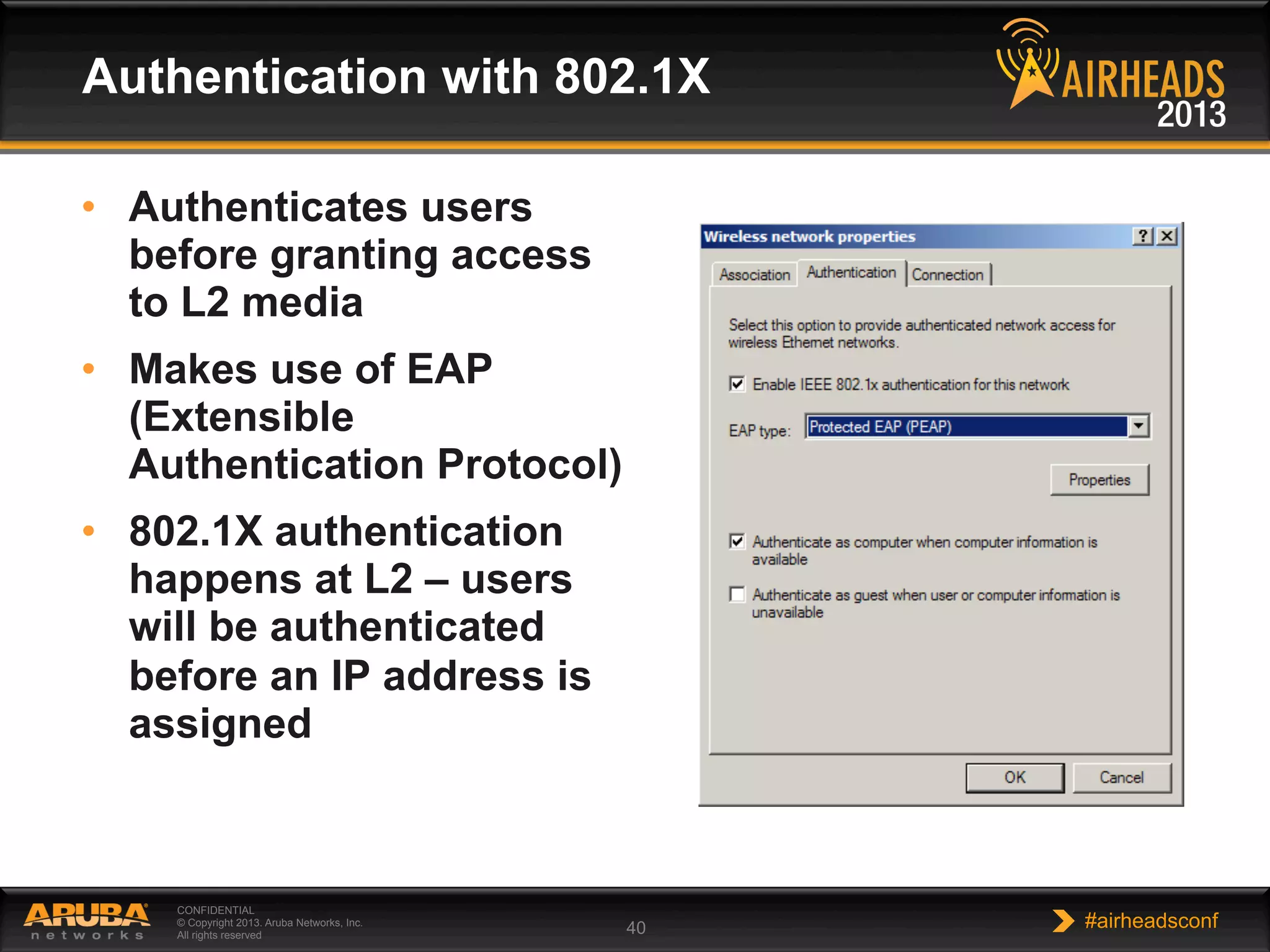
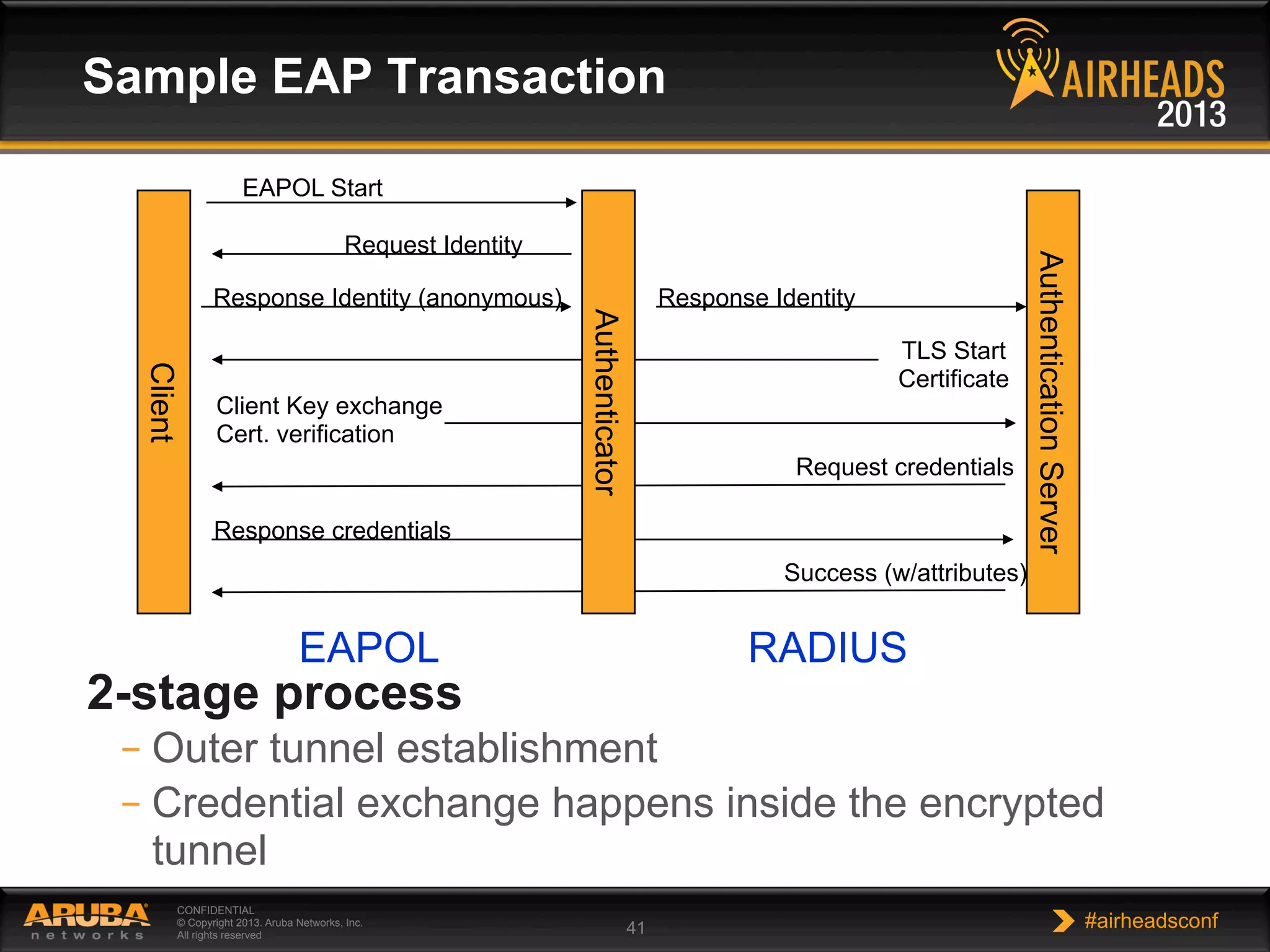
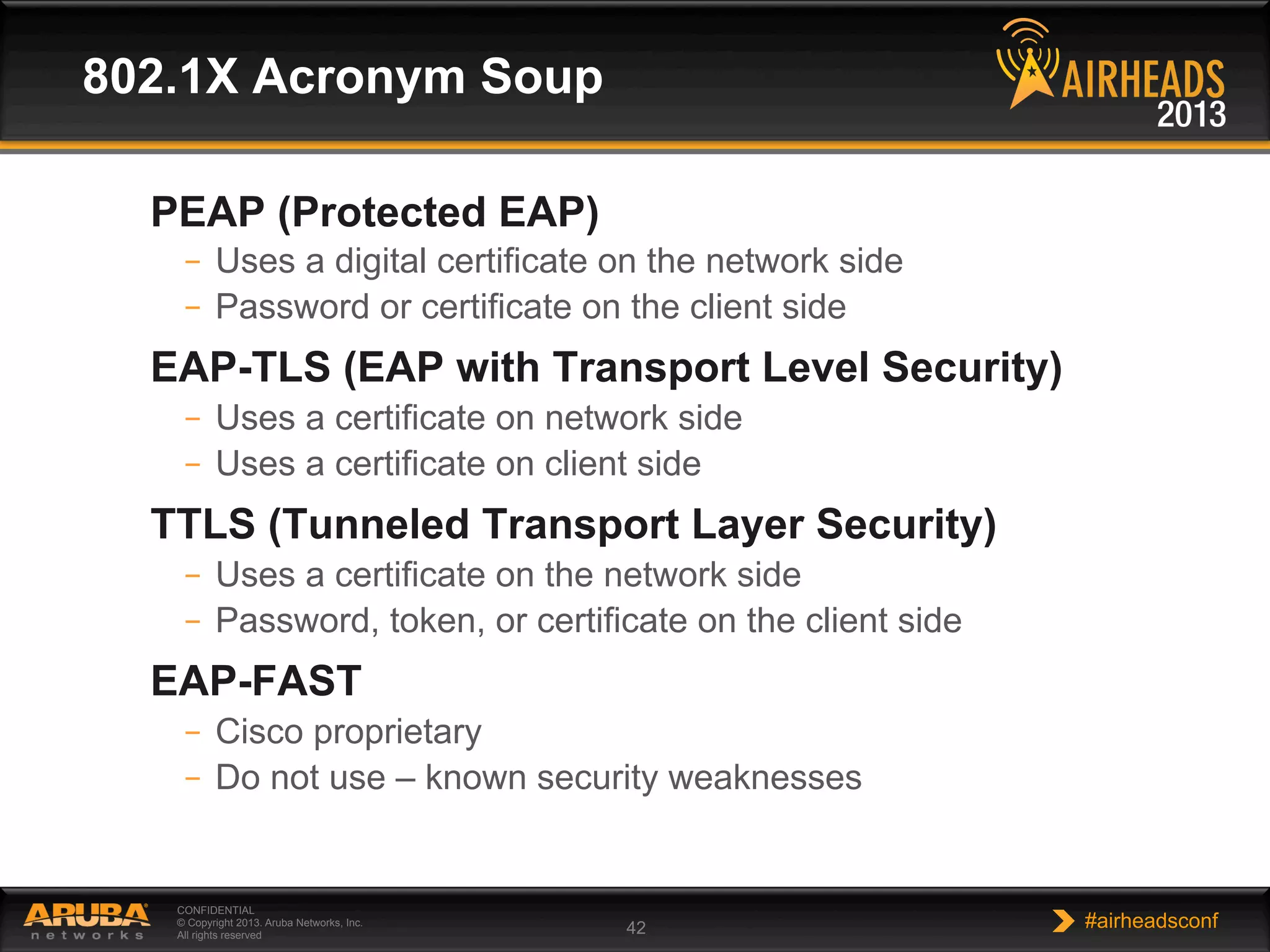
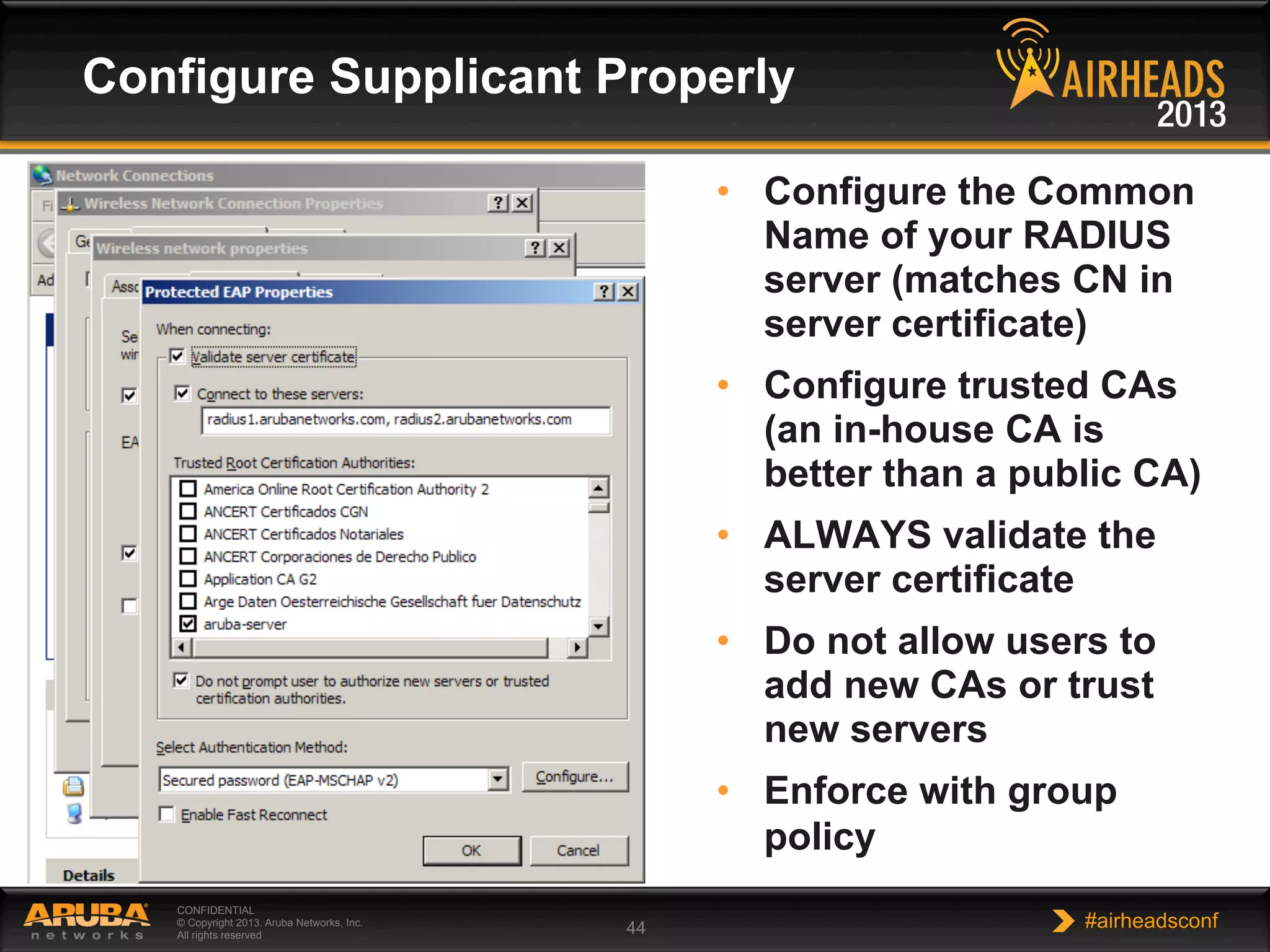
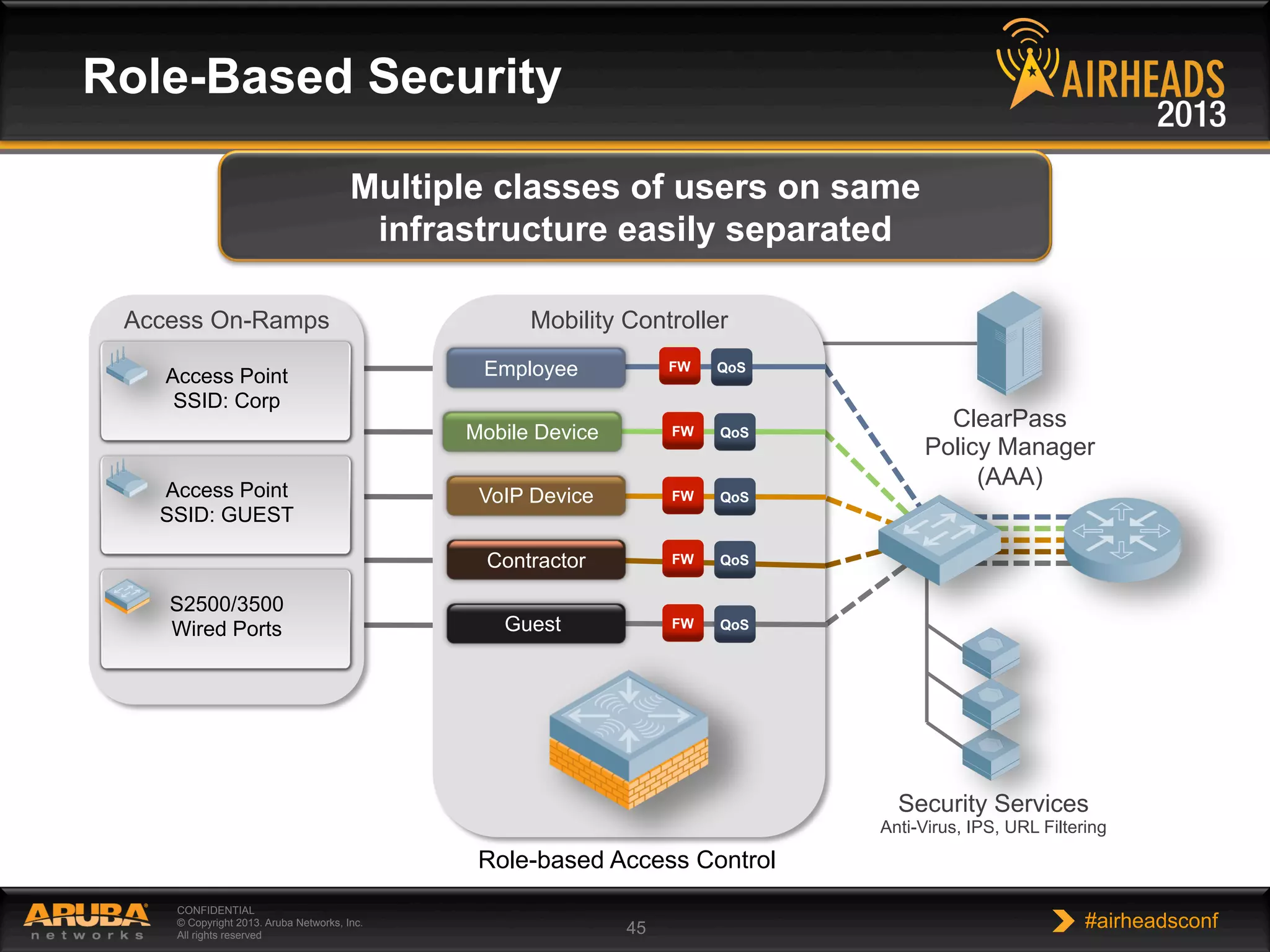
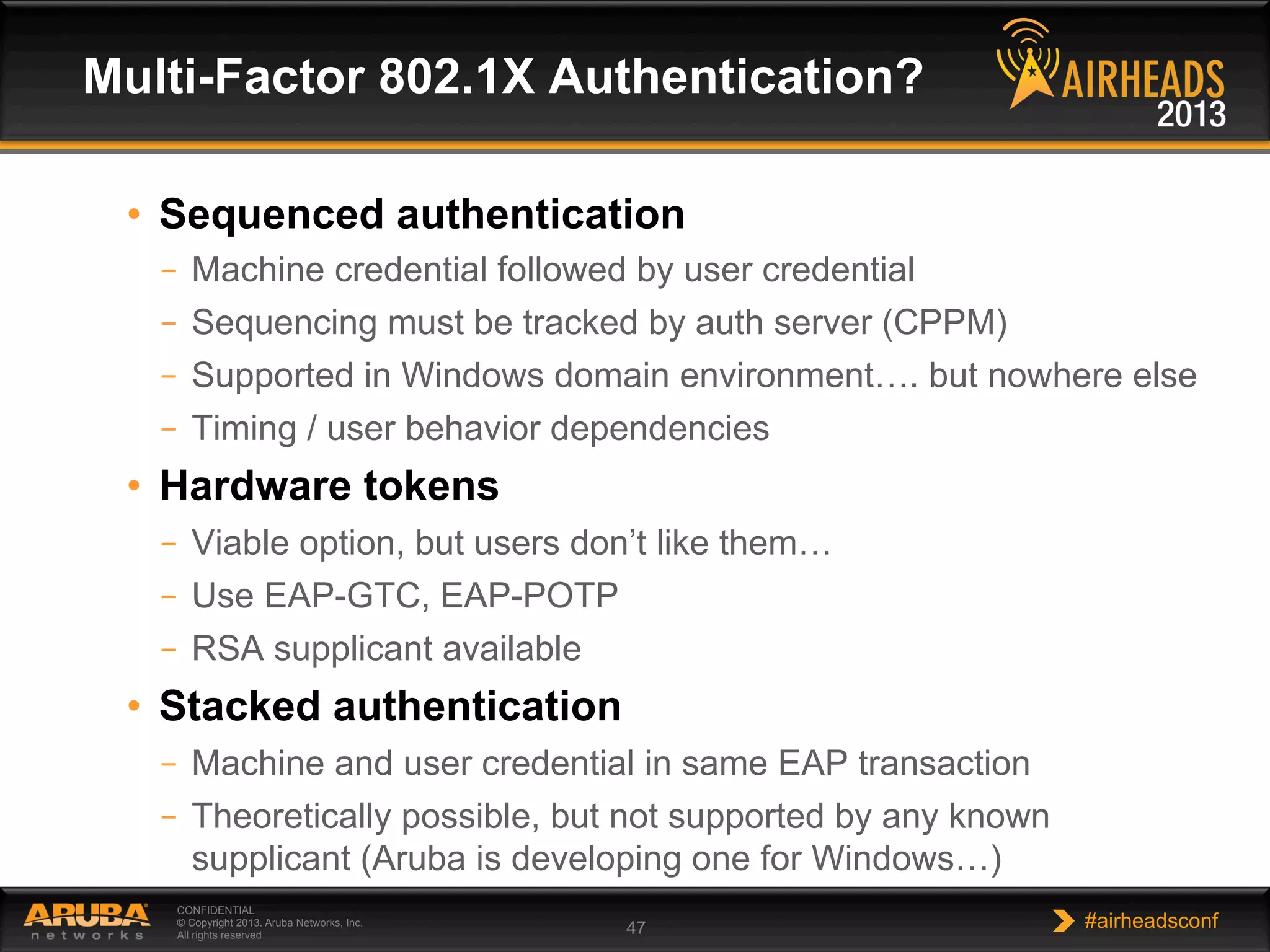
The document provides an overview of encryption, authentication, and access control topics. It begins with a cryptography primer covering symmetric and asymmetric encryption techniques. It then discusses public key infrastructure concepts like certificates, certificate authorities, and establishing trust chains. It concludes with recommendations around using a private certificate authority versus a public one and considerations for certificate validity and OCSP. The overall goal is to explain how public keys, certificates, and other cryptographic methods can be used together to create secure authentication methods like 802.1X.