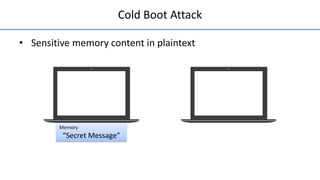
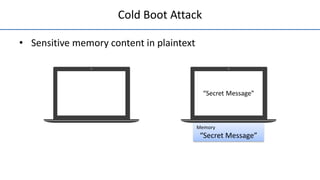
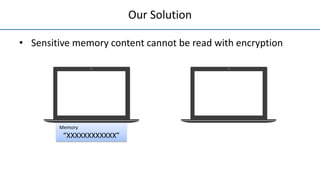
The document discusses a solution called 'encexec' designed to prevent sensitive data leaks during cold boot attacks by ensuring that sensitive memory content is only accessible in encrypted form. It details the design features such as spatial cache reservation and secure in-cache execution which aim to maintain data secrecy, application transparency, and performance isolation. Performance evaluations demonstrate the efficiency of the proposed methods in protecting data without significant overhead compared to other cryptographic measures.