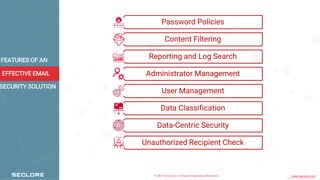
The document discusses the key features of an effective email security solution. It outlines eight important features: password policies, content filtering, reporting and log search, administrator management, user management, data classification, data-centric security, and unauthorized recipient check. Each feature is then discussed in more detail across multiple paragraphs. The conclusion states that while the outlined features are important, additional capabilities like anti-spam, anti-virus, outbound filtering, and email archiving further improve email security.