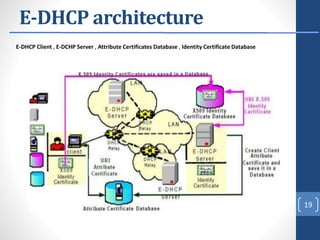
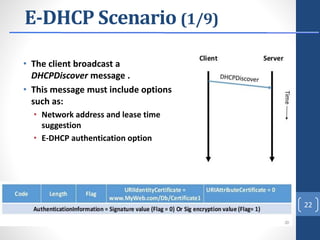
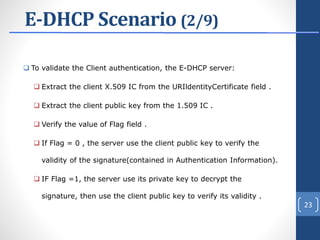
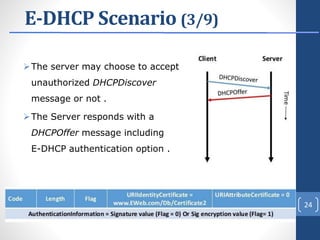
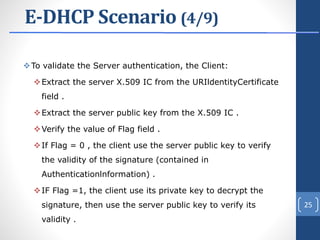
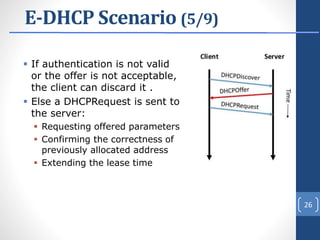
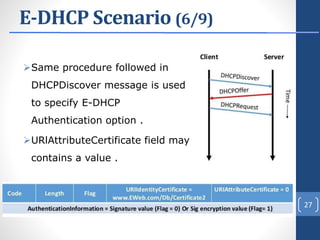
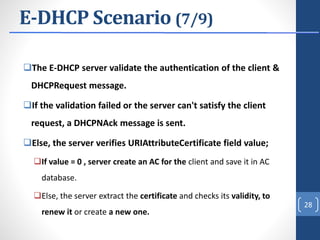
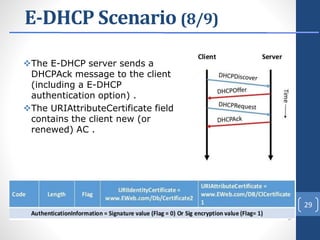
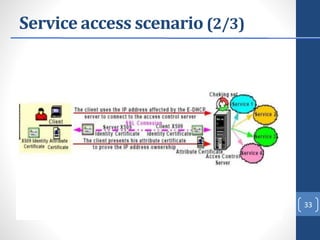
This document proposes E-DHCP, an extension to the DHCP protocol that adds authentication. E-DHCP uses X.509 certificates and attribute certificates to authenticate DHCP clients, servers, and messages. It introduces an Attribute Authority server that creates and manages attribute certificates linking a client's identity certificate to its allocated IP address. The architecture involves E-DHCP clients and servers possessing identity certificates. Attribute certificates are then used to grant clients access to authorized services based on validating the linkage between certificates and allocated IP address. E-DHCP aims to address DHCP security issues like lack of authentication and prevent denial of service attacks.