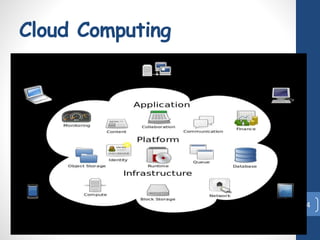
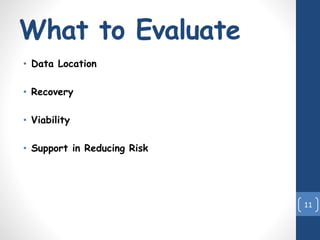
This document discusses risk assessment for cloud computing. It outlines the steps in risk assessment, which include threat identification, vulnerability identification, risk determination, and control recommendation. It also discusses assessing the security risks of cloud computing, including evaluating data location, recovery, viability, and support in reducing risk. Finally, it covers security and privacy challenges in cloud computing such as authentication, access control, secure service management, and privacy/data protection.